How To Prioritize Vulnerabilities in a Modern IT Environment

Here’s a stat that shows the importance of prioritizing vulnerability remediation: Almost 30% of the CVEs disclosed in 2017 had a CVSS score of “High” or “Critical.” That works out to about 3,000 such vulnerabilities, or about 58 every week.
Given this large number of severe vulnerabilities, it’s critical for IT and security teams to make a deeper assessment of the risk they represent in the context of their organizations’ IT environment.
If they identify the vulnerabilities that pose the highest risk to their organization’s most critical assets, they’ll be able to prioritize remediation accordingly and eliminate the most serious and pressing threats to their IT environment.
However, as evidenced by the long list of major breaches caused by unpatched vulnerabilities, it’s hard for many businesses, government agencies and not-for-profit organizations to prioritize remediation consistently and accurately.
“One of the big challenges that we have as security professionals is trying to stay on top of our vulnerability management,” Josh Zelonis, a Forrester Research analyst, said during a recent webcast.
Zelonis, who cited the CVE stat during the webcast, said that, according to a 2017 Forrester survey of global businesses, 58% of them experienced at least one breach in the previous 12 months. Among those, 41% of the breaches were carried out by exploiting a vulnerability.
“This is really representative of the problems we’re seeing in the industry with prioritization and getting patches deployed, and this is only increasing,” he said.
“In a post-Equifax world, VM is coming under increased scrutiny,” Zelonis added, alluding to the massive data breach suffered by the credit reporting agency in 2017 after hackers exploited the Apache Struts vulnerability (CVE-2017-5638), which had been disclosed about six months before.
Read on to learn valuable best practices for prioritizing remediation, and how Qualys can help your organization overcome this critical challenge.
Vulnerability management and prioritization tips
According to Zelonis, the vulnerability risk management process has four main steps:
- Asset identification
- Enumeration of assets
- Prioritization of patching
- Remediation
When assigning remediation priorities, it’s key to examine the severity of the vulnerabilities in the context of each asset.
For example, it should be a top priority to remediate a critical vulnerability in an asset that’s highly important. However, remediating that same vulnerability may not be a top priority when it’s present in an asset of medium or low importance.
In vulnerability management, it’s also helpful to use threat intelligence not just to detect threats, but to also preemptively patch using threat landscape trends as a guide.
“It’s important to understand how a vulnerability can be exploited so you can take a look at at the assets within your organization to figure out where patches need to be prioritized and applied,” Zelonis said.
Threat intelligence is also essential for security teams to be able to communicate effectively with C-level executives and board members, who are increasingly interested in staying informed about the organization’s security posture and strategy.
“Once you’ve made it relevant to them, they’re going to need to understand what you’re doing to mitigate the situations and perhaps allocate additional budget where necessary,” he said.
It’s also important to communicate this information not just to the higher-ups, but also horizontally across other IT teams such as operations, and across business units, because vulnerability remediation requires cross-functional collaboration.
“This is a major gap we see with organizations who are struggling to get items patched: The security team’s priorities aren’t echoed nor understood outside of the security team,” he said.
The goal here is to make these other teams aware of the real risk and potential business impact of particular vulnerabilities.
Ultimately, organizations should evolve from vulnerability management to vulnerability risk management. That way, the focus isn’t just on reducing false positives, but rather on assessing critical data points and metrics to attain an understanding of risk, according to Zelonis.
Qualys: Asset visibility, vulnerability management and threat prioritization
With Qualys, you’ll get complete visibility of your IT assets wherever they reside — on premises, in clouds or at remote endpoints — and you’ll be able to continuously detect and asses all your vulnerabilities, and precisely prioritize remediation.
With proper vulnerability management, you “immunize” your IT assets against opportunistic attacks which are designed to exploit common, well-known bugs and which are the most likely to hit your network.
Let’s look at three Qualys products that work in tandem to provide you with this asset visibility, vulnerability detection and remediation prioritization.
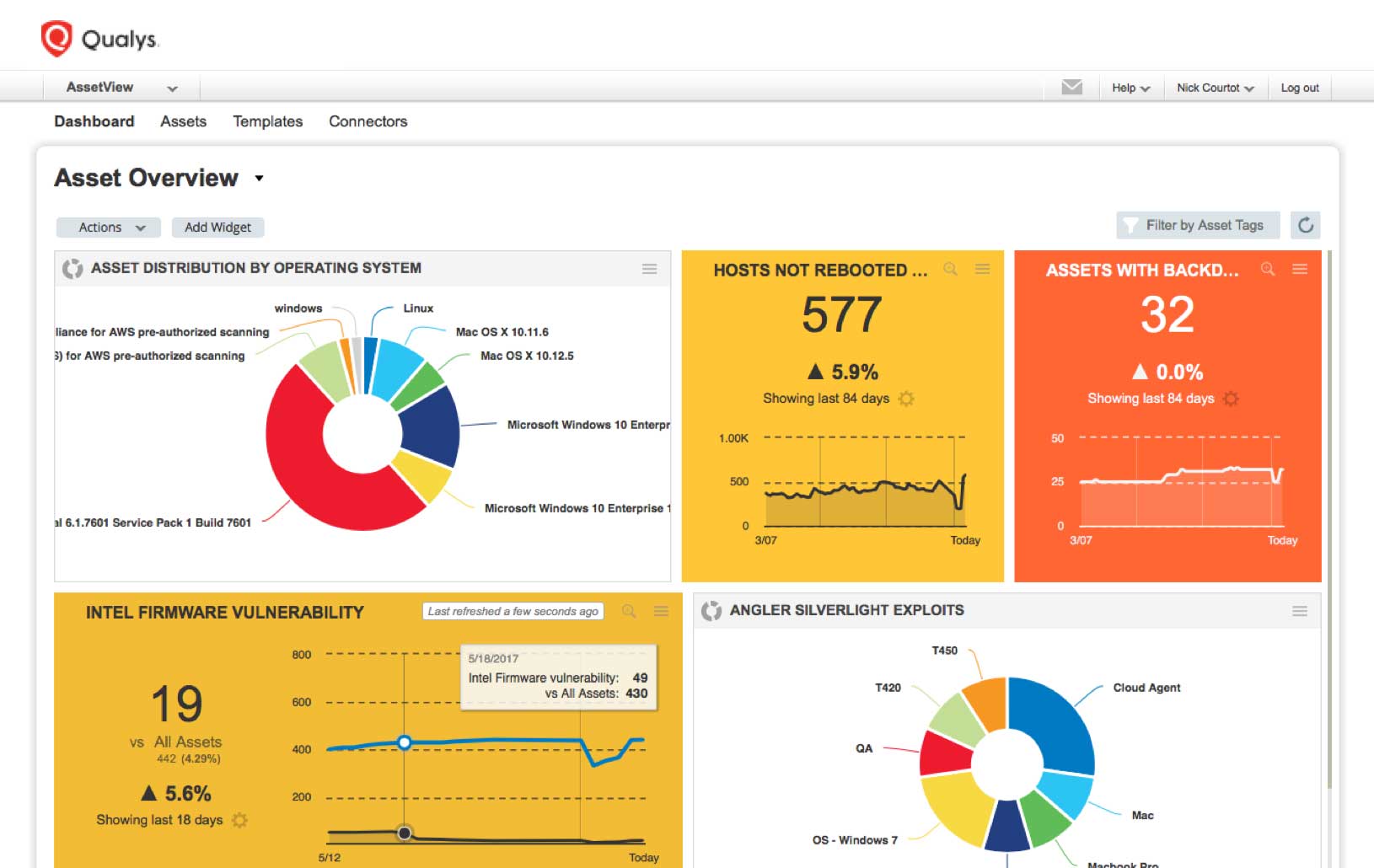
Qualys AssetView
Qualys AssetView automates collection and categorization of IT and security information, and provides a unified view of this data.
“It brings IT and security data together,” Qualys Product Management Director Jimmy Graham said during the webcast, titled “Prioritization of Vulnerabilities in a Modern IT Environment.”
The data, which is fed into the Qualys Cloud Platform for aggregation, indexing, correlation, and analysis, is continuously collected and updated using a variety of sensors, including:
- Physical and virtual appliances that scan IT assets located on-premises, in private clouds, or in virtualized environments
- Cloud appliances that remotely scan your infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) instances in commercial cloud computing platforms
- Lightweight, all-purpose cloud agents installed on IT assets that continuously monitor them
The data is made searchable via AssetView’s search engine using ad-hoc queries. In addition, any query can be turned into interactive, continuously updated widgets in AssetView’s customizable and dynamic dashboards. You can also generate detailed and custom-tailored reports.
This inventory provides both a complete “horizontal” list of IT assets as well as deep “vertical” details for each asset, including hardware specs, installed software, network connections, approved users, applied patches, and open vulnerabilities.
In addition, Qualys AssetView lets you assign criticality rankings to assets, since not all assets carry the same weight within your organization. Qualys lets you tag your assets, so you put relevant labels on them in the inventory and organize them in multiple ways.
Qualys Vulnerability Management
Qualys Vulnerability Management provides continuous, comprehensive coverage and visibility, as well as constant monitoring and alerts, in a way that makes vulnerability assessment effective in a “perimeter-less world,” according to Graham.
“We call that ‘perimeter-less world’ because we collect vulnerabilities from on premises devices, and from private and public clouds. Through the agent, we can collect vulnerability information from roaming devices like laptops that employees may be using in a coffee shop or at home,” he said.
Qualys VM maps all assets on the network, detailing their OS, ports, services and certificates, and scans them for vulnerabilities with Six Sigma 99.99966 percent accuracy. It assigns remediation tickets, manages exceptions, lists patches for each host, and integrates with existing IT ticketing systems.
In addition, VM generates comprehensive reports customized for different recipients — like IT pros, business executives or auditors — and incorporates context and insight, including progress against goals. Via VM’s APIs, the reporting data can be integrated with other security and compliance systems.
When VM is paired with the Qualys Continuous Monitoring (CM) app, you’ll be alerted about potential threats — such as new hosts/OSes, expiring certificates, unexpected open ports and unauthorized software — so problems can be tackled before turning into breaches.
Qualys Threat Protection
To prioritize remediation work, you must continuously correlate vulnerability disclosures with your organization’s IT asset inventory, so that you get a clear picture of the vulnerabilities that exist in each IT asset.
This is what Qualys Threat Protection (TP) does, and more.
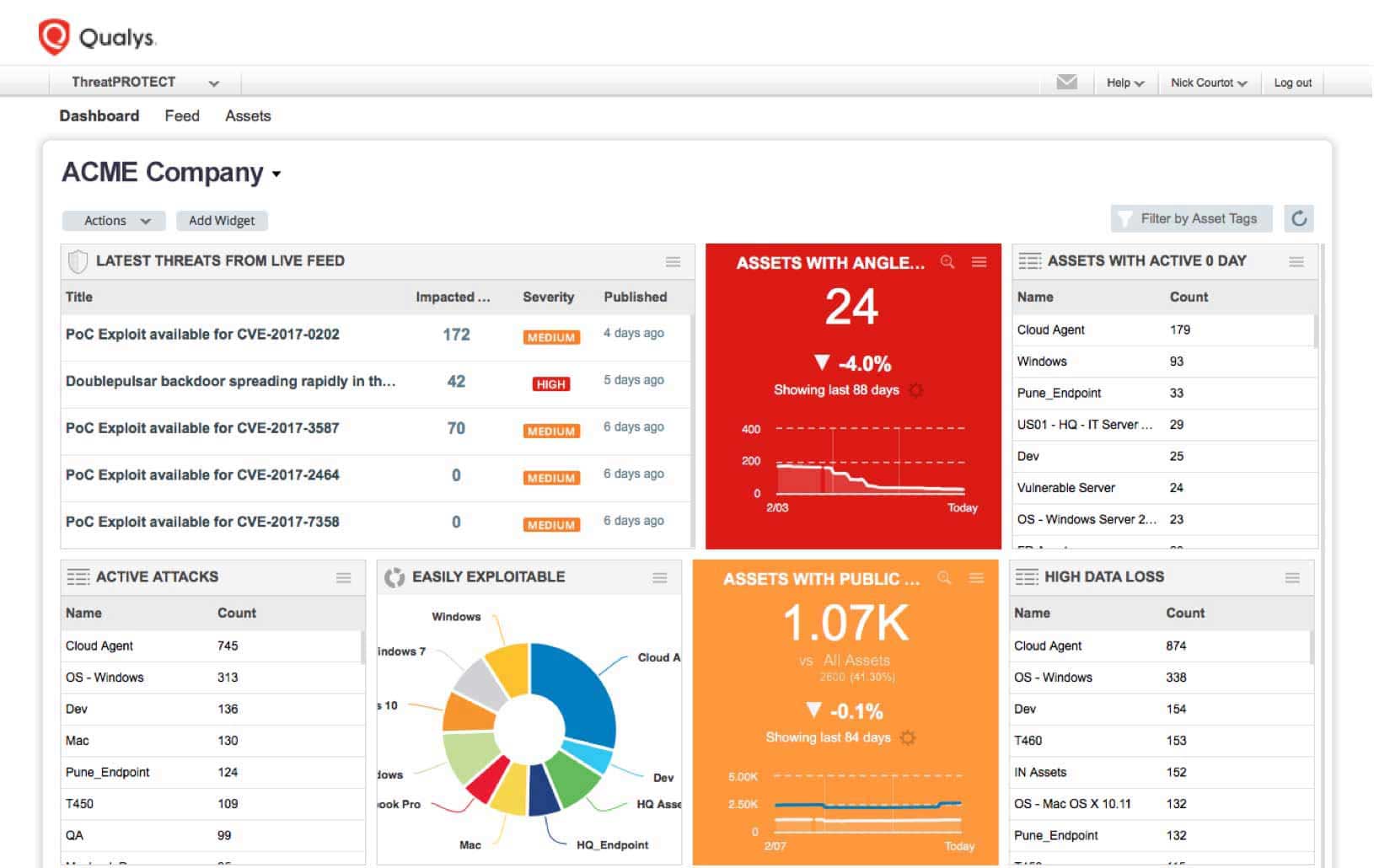
Qualys TP continuously correlates external real-time threat indicators (RTIs) against your internal vulnerabilities and IT asset data, so you can take full control of evolving threats and identify what to remediate first.
“What ties this all together is Qualys Threat Protection,” Graham said.
RTIs add valuable context to a vulnerability, such as whether:
- It’s being actively attacked in the wild
- There’s an exploit kit available for it
- It can lead to high data loss or to a denial of service attack
- It’s a “zero day” with no patch available
Regarding IT assets, you should consider factors such as their role in business operations, their interconnectedness with other assets, their Internet exposure and their user base.
Out of this type of in-depth analysis will emerge a clear picture of your threat landscape, and based on it, you’ll be able to come up with an accurate remediation plan.
Qualys TP features include:
- Robust Data Analysis
Qualys TP continuously correlates external threat information against your vulnerabilities and IT asset inventory, leveraging Qualys Cloud Platform’s robust back-end engine to automate this large-scale and intensive data analysis process.
- Live Threat Intelligence Feed
As Qualys engineers continuously validate and rate new threats from internal and external sources, Qualys TP’s Live Threat Intelligence Feed displays the latest vulnerability disclosures and maps them to your impacted IT assets. You can see the number of assets affected by each threat, and drill down into asset details.
Qualys Threat Protection, working in tandem with Qualys AssetView and Qualys Vulnerability Management, helps you to proactively and continuously detect assets and vulnerabilities, and prioritize remediation in your IT environment.
Watch a recording of the webcast, which has a lot more details, a demo of Qualys Threat Protection, and a Q&A session with the audience.