GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
Turned into law in 2016, the EU’s General Data Protection Regulation (GDPR) finally goes into effect this week, slapping strict requirements on millions of businesses and subjecting violators to severe penalties. The complex regulation applies to any organization worldwide — not just in Europe — that controls and processes personal data of EU residents, whose security and privacy GDPR fiercely protects.
GDPR calls this data’s protection a “fundamental right” essential for “freedom, security and justice” and for creating the “trust” needed for the “digital economy” to flourish. Its requirements amount to what some have called zero-tolerance on mishandling EU residents’ personal data.

A PwC survey found that more than half of U.S. multinationals say GDPR is their main data-protection priority, with 77% planning to spend $1 million or more on GDPR readiness. “Data protection has been a thing organizations know about, but GDPR has brought it all to the forefront,” Richard Sisson, Senior Policy Officer at the U.K.’s Information Commissioner’s Office (ICO) said during a recent GDPR roundtable.
Penalties can be stiff. One possible fine: Up to 4% of your company’s annual revenue, or up to €20 million, whichever is higher. GDPR also gives leeway to EU countries to impose heavier fines and stricter requirements. Still, Gartner estimates that about half of organizations will not be in full compliance with GDPR requirements by the end of 2018.
Regardless of where you are in your GDPR preparedness journey, Qualys can help you. To that end, today we begin a blog series in which we’ll highlight how Qualys can assist you by solidifying the security and compliance foundations of your organization, thus slashing your risk of data breaches that could land you in GDPR hot water.
We’ll address IT asset visibility, vulnerability management, threat prioritization, web application security, file integrity monitoring, vendor risk management, public cloud protection, and other essential elements of a rock-solid security and compliance posture.
GDPR scope and requirements
As regulations go, GDPR is as demanding as they come. Organizations must know what personal data of EU residents they have, where it’s stored, with whom they’re sharing it, how they’re protecting it, and what they’re using it for.
“The core approach is information governance, knowing what personal data sits in an organization and getting it under management,” wrote IDC analyst Duncan Brown. “Most companies have a very loose understanding of this concept, and need assistance.”
Organizations must have technology and processes in place to quickly respond to requests from EU residents, including deleting (“right to be forgotten”), disclosing, correcting or transferring their personal information, and to report data breaches within 72 hours — or less.
Organizations must also prove they obtained unequivocal consent from each EU resident whose data they collect, and protect this data, in part by adopting the principle of “privacy by design” when developing new services and systems.

Organizations also have to ensure that the third parties they share this data with — vendors, contractors, partners, suppliers — are compliant with GDPR.
What organizations won’t find in GDPR’s text are detailed prescriptions for technology adoption, as few InfoSec technologies and practices are mentioned by name.
Both data “controllers” (organizations that collect data) and “processors” (those with whom it’s shared) must protect this information by implementing “appropriate technical and organisational measures”, a phrase repeated multiple times in the GDPR document.
Several references are made to organizations’ need to have secure IT networks and systems that can “resist, at a given level of confidence, accidental events or unlawful or malicious actions.”
“This could, for example, include preventing unauthorised access to electronic communications networks and malicious code distribution and stopping ‘denial of service’ attacks and damage to computer and electronic communication systems,” reads the document.
What does this all mean? You must do everything in your power to prevent accidental and malicious incidents that compromise the “availability, authenticity, integrity and confidentiality of stored or transmitted personal data.”
In short, while GDPR compliance requires implementation of new business processes and technical controls, information security and compliance are a significant subset of the regulation. For security and compliance professionals, the bottom line is clear: Organizations must have solid InfoSec foundations in place to comply with GDPR.
Let’s look at the first foundational security practice that your organization must have solidly in place for GDPR compliance: IT asset visibility. The section below was authored by our expert in this area — Pablo Quiroga, a Director of Product Management at Qualys.
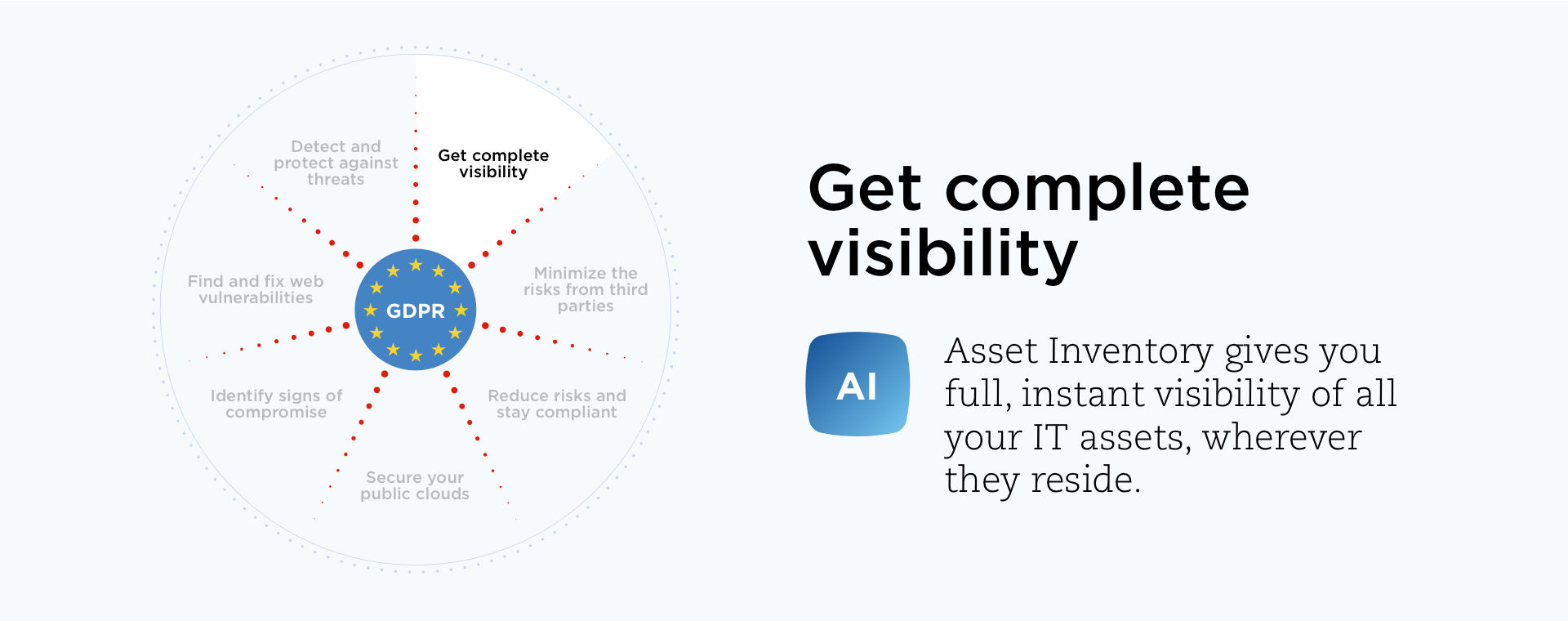
Visibility into your IT assets
Full visibility and a detailed inventory of all IT resources are key to a strong security and compliance position: Every device, software installation, and user should be counted and correlated.
In the case of an IT breach, for example, you must answer these questions:
- What are your IT assets? Which software is installed on your devices?
- Who has access to devices and applications? Who is assigned to the devices?
- Where are these devices? How have they “moved” over time?
- How are they related to each other?
Thus for GDPR compliance, organizations need full visibility into all hardware and software involved in processing, transmission, analysis and storage of EU residents’ personal data, so they can protect it and account for it according to regulation requirements.
Stringent regulations like GDPR, combined with hybrid, distributed and decentralized IT environments, create a perfect storm for IT and InfoSec teams: While security and compliance challenges get thornier, the visibility of their organizations’ IT assets becomes fuzzier.
Flying blind exponentially increases the risk of getting hacked and of running afoul of regulations, because you can’t secure — nor defend yourself from — what you can’t see. So it’s key to have complete visibility of your IT environment and a detailed inventory of all your assets.
Regain IT Asset Visibility with Qualys
Qualys Asset Inventory (AI) automates collection and categorization of IT, compliance, and security data, which is fed into the Qualys Cloud Platform for aggregation, indexing, correlation, and analysis.
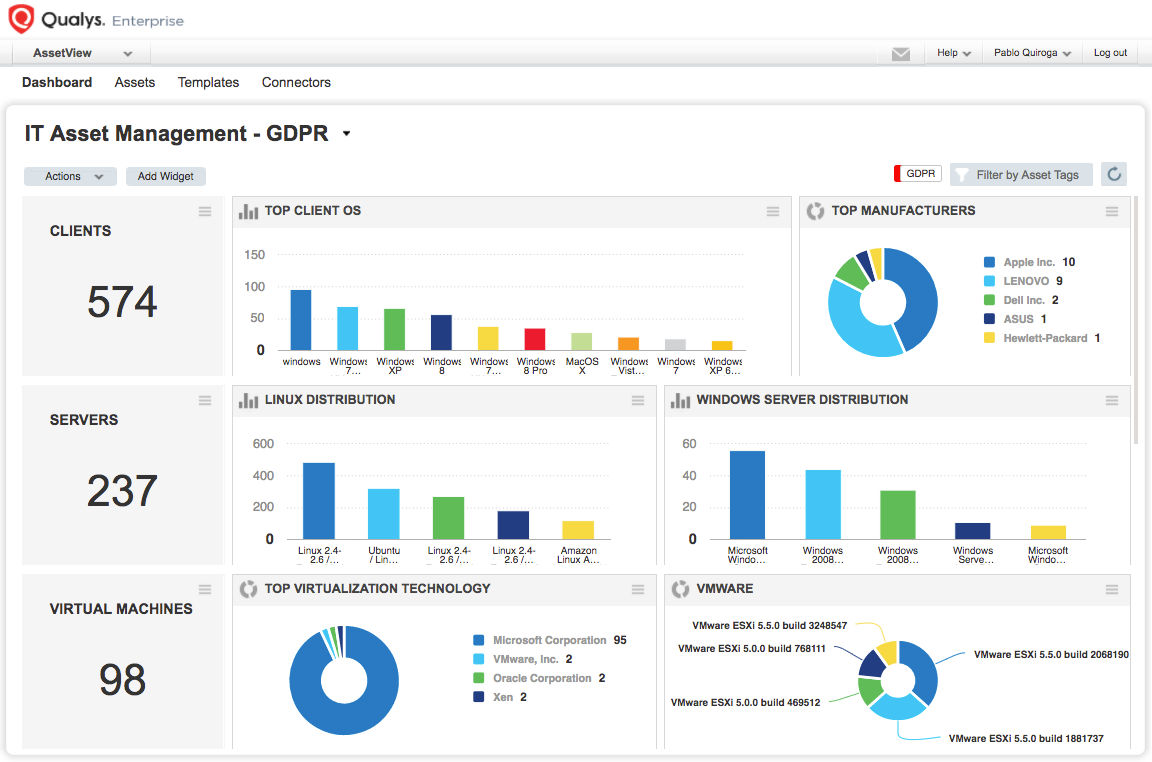
To continuously collect and update this data, Qualys uses a variety of sensors, including:
- Physical and virtual appliances that scan IT assets located on-premises, in private clouds, or in virtualized environments
- Cloud appliances that remotely scan your infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) instances in commercial cloud computing platforms
- Lightweight, all-purpose cloud agents that are installed on IT assets and continuously monitor them
Qualys AI’s capabilities include:
- Complete visibility of your IT environment
Qualys gives you full horizontal visibility of all hardware and software, scaling up to millions of assets — on-premises, in cloud instances, and on mobile endpoints. It also provides the last seen geolocation of devices as well as which users are assigned to them.
- Deep visibility into assets
You get a detailed, multidimensional view of each IT asset that includes both its IT and security data, so you can flag issues such as configuration problems, security risks, IT policy violations and regulatory non-compliance.
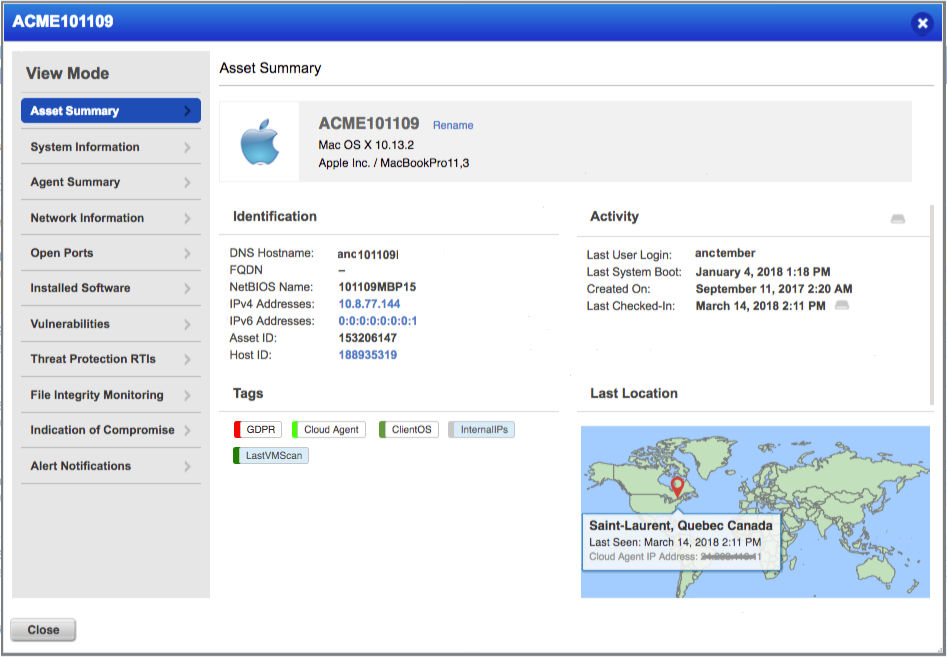
- Continuous and automatic updates
An IT asset inventory loses its value if its data gets stale: New vulnerabilities are disclosed. Old ones become more dangerous. Laptops go from secure to compromised. Qualys continuously updates asset data.
- Asset criticality rankings
Qualys lets you tag your assets, so you can put relevant labels on them and organize them in multiple ways. If a device contains data governed by GDPR, it can be tagged and managed accordingly. If the device reaches its lifecycle’s end, all appropriate processes can be followed to ensure there’s no GDPR violation.
- Interactive, customizable dashboarding and reporting
Interactive, customizable dashboards and powerful reporting capabilities let you visualize and share the security, configuration and compliance status of IT assets. Search capabilities let you fire off ad hoc queries against the inventory database.
- Integration with your CMDB
IT asset inventory solutions must link up with your CMDB (configuration management database) and continuously feed it fresh, detailed data, so the CMDB can better map the relationships, hierarchies and dependencies among IT assets. The Qualys app for ServiceNow CMDB automatically syncs data from Qualys with the ServiceNow configuration management system.
In summary, Qualys gives you a comprehensive, detailed and continually updated inventory of all your IT assets, so you can see the internal IT asset landscape where all your customers’ data is stored, processed, accessed and transmitted.
Given this foundation, you can start to get clarity and understanding into the many moving parts involved in collecting and processing personal data. As you identify, document and map these data flows, you can further develop your GDPR readiness efforts accordingly.
In our next post in this blog series, we’ll look into the importance of vulnerability management and threat prioritization within the realm of your GDPR readiness efforts.
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
GDPR Is Here: Assess Risk from Vendors and from Internal Teams