GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
To provide the level of data protection required by the EU’s General Data Protection Regulation (GDPR), your organization must continuously detect vulnerabilities, and prioritize their remediation.
Why? An InfoSec team that’s chronically overwhelmed by its IT environment’s vulnerabilities and unable to pinpoint the critical ones that must be remediated immediately is at a high risk for data breaches, and, consequently, for GDPR non-compliance.
The Center for Internet Security (CIS) ranks “Continuous Vulnerability Assessment and Remediation” as the fourth most important practice in its 20 Critical Security Controls. “Organizations that do not scan for vulnerabilities and proactively address discovered flaws face a significant likelihood of having their computer systems compromised,” CIS states.
In fact, hackers constantly exploit common vulnerabilities and exposures (CVEs) for which patches have been available for weeks, months and even years. The reason: Many organizations fail to detect and remediate critical bugs on a timely basis, leaving them like low-hanging fruit for cyber data thieves to feast on.
In this second installment of our GDPR compliance blog series, we’ll explain the importance of vulnerability management and threat prioritization, and how Qualys can help you solidify these practices so you can slash your risk of data breaches.
Managing vulnerabilities effectively
When you continuously detect, assess and remediate vulnerabilities, whether through patching or mitigation, you eliminate entry points for cyber criminals and consistently lower your risk of breaches.
With proper vulnerability management, you “immunize” your IT assets against opportunistic attacks designed to exploit common, well-known bugs. You also must make sure you’re as quick as possible in your remediation work.
SANS Institute’s second survey on continuous monitoring programs found that only 10% of respondents could remediate critical vulnerabilities in 24 hours or less. According to SANS, breach risk reaches moderate levels at the one-week mark and becomes high after a month.
For example, most organizations should have prioritized patching the vulnerability that was exploited by the WannaCry ransomware, way before the attack was unleashed. Instead, the WannaCry attack infected 300,000-plus systems and disrupted critical operations globally.
Microsoft disclosed the Windows vulnerability (MS17-010) exploited by WannaCry in mid-March 2017 and made a patch available. At the time, Microsoft rated the vulnerability as “Critical” due to the potential for attackers to execute remote code in affected systems.
The vulnerability also had a number of other red flags that made it stand out as a particularly concerning one. In mid-April, the vulnerability became even more dangerous when the Shadow Brokers hacker group released an exploit for it called EternalBlue.
So organizations had a window of about two months to install the patch before WannaCry was unleashed in mid-May. Had most affected systems been patched, WannaCry’s impact would have been minor.
The Threat Prioritization Challenge
Thousands of vulnerabilities are disclosed annually. Organizations can’t patch every single one in their environment.
In addition, vulnerabilities disclosed months or even years before can suddenly become more dangerous if, for example, they’re targeted by exploit kits that make them easier to compromise by a much larger universe of hackers. Meanwhile, your IT asset inventory also changes frequently.
In other words, the threats posed by vulnerabilities in your IT environment change constantly, forcing you to continually reassess your remediation plans. But you can’t continuously pinpoint which IT assets must be patched with the greatest urgency at any given time by doing manual calculations or using informed guesswork.
To prioritize remediation, you must continuously correlate vulnerability disclosures with your organization’s IT asset inventory. This gives you a clear picture of each asset’s vulnerabilities. Then you must weigh detailed criteria about impacted IT assets and their vulnerabilities. CIS recommends rating vulnerabilities’ risk based on their “exploitability” and their potential impact.
Regarding IT assets, you should consider factors such as their role in business operations, their interconnectedness with other assets, their Internet exposure, and their user base. For vulnerabilities, you should consider, for example, whether they are “zero day,” are being actively exploited, threaten data integrity, lead to “lateral movement” attacks, and are conduits for DDoS attacks.
Out of this type of in-depth analysis will emerge a clear picture of your threat landscape, and based on it, you’ll come up with an accurate remediation plan.
Qualys Vulnerability Management
Qualys’ Vulnerability Management (VM) continuously identifies exposures so you can defend your organization against attacks anytime, anywhere.
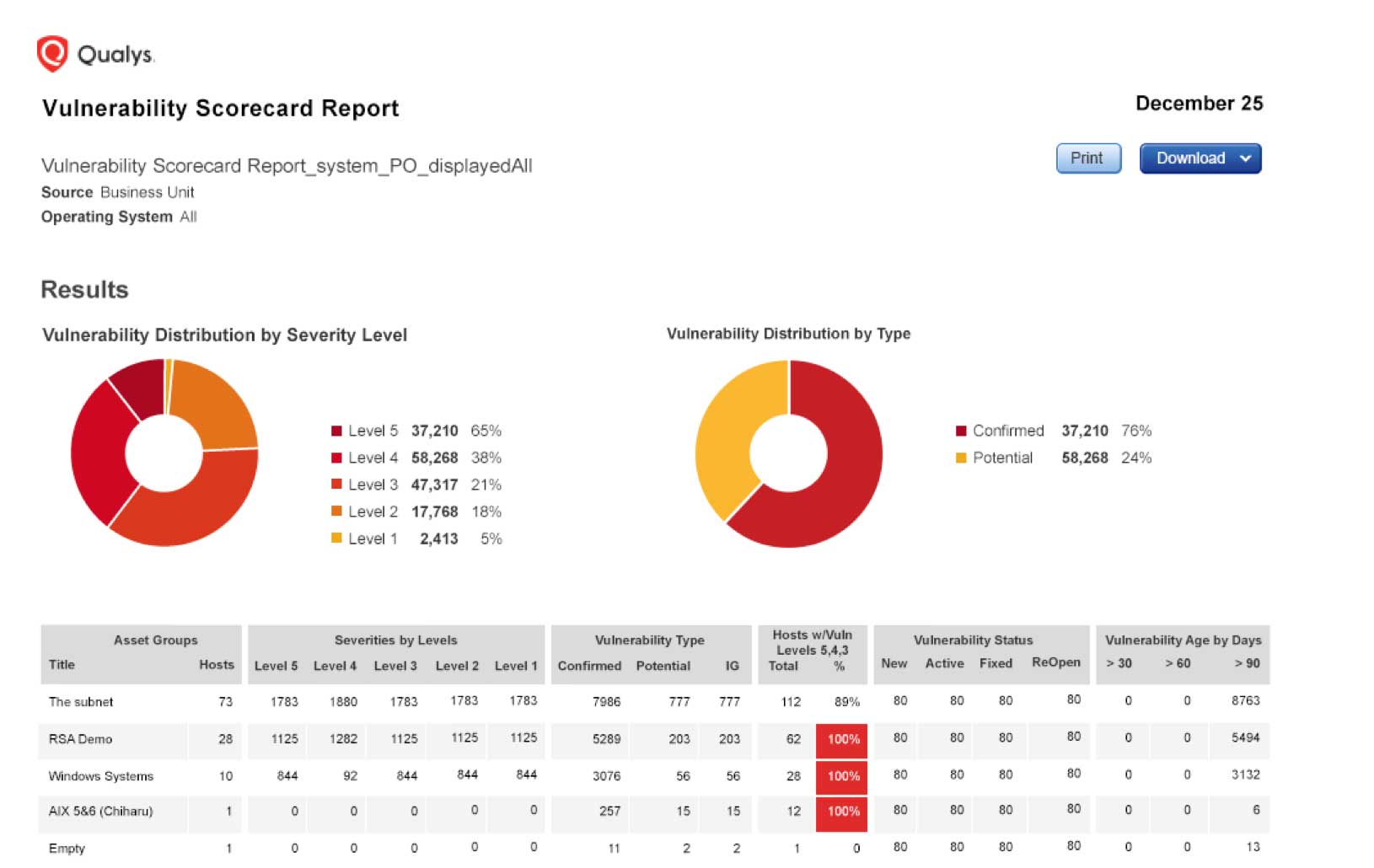
VM maps all network assets, detailing their OS, ports, services and certificates, and scans them for vulnerabilities with Six Sigma (99.99966 %) accuracy. It assigns remediation tickets, manages exceptions, lists patches for each host and integrates with IT ticketing systems.
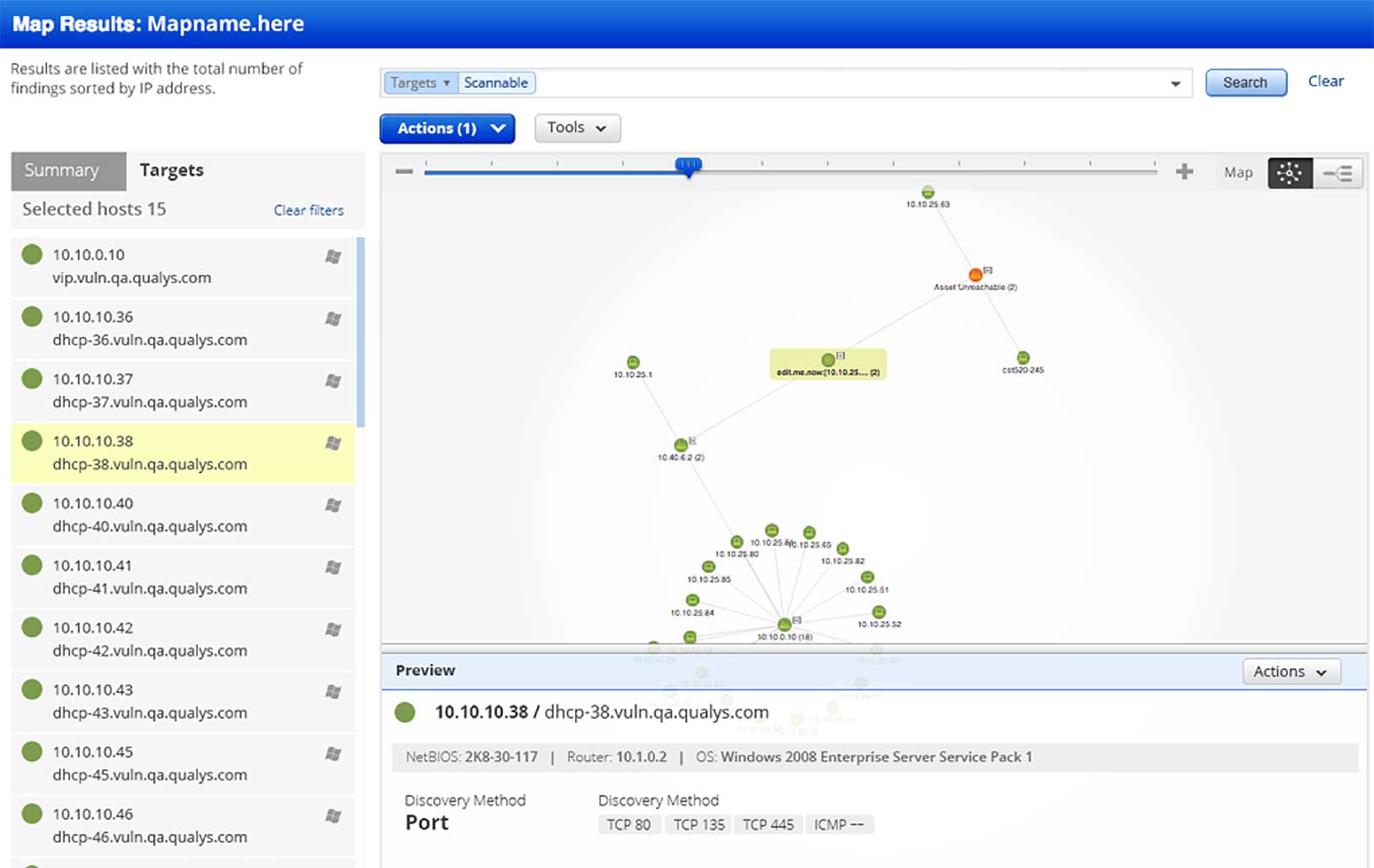
In addition, VM generates comprehensive reports customized for different recipients — like IT pros, business executives or auditors — and incorporates context and insight, including progress against goals. Via VM’s APIs, the reporting data can be integrated with other security and compliance systems.
When VM is paired with Qualys Continuous Monitoring, you’ll be alerted about potential threats — such as new hosts/OSes, expiring certificates, unexpected open ports and unauthorized software.
With Qualys CM, you can monitor your global network from the cloud, like hackers do, and alert the appropriate people to critical security issues.
In addition to Qualys scanners, VM also works with the Qualys Cloud Agents, extending its network coverage to assets that can’t be scanned. These lightweight, all-purpose, self-updating agents reside on the assets they monitor — no scan windows, credentials or firewall changes needed — so vulnerabilities are found faster with minimal network impact.
Prioritize Remediation with Qualys Threat Protection
To conduct these assessments of IT assets and vulnerabilities continuously and prioritize accordingly, the process must be automated. Qualys Threat Protection was designed to do just that.
Qualys TP, working in tandem with Qualys Asset Inventory and Qualys Vulnerability Management, helps you to proactively and continuously identify, prioritize, patch and mitigate the most critical vulnerabilities in your IT environment.
Qualys TP will also give you the necessary data to know which things are most likely to be exploited, so you can show auditors that you’re doing due diligence and reducing risk in the areas that are most likely to affect data privacy..
With Qualys TP you take full control of evolving threats and identify what to remediate first, with features including:
Robust Data Analysis
Qualys TP continuously correlates external threat information against your internal vulnerabilities and IT asset inventory, leveraging Qualys Cloud Platform’s robust back-end engine to automate this large-scale and intensive data analysis process.
Live Threat Intelligence Feed
As Qualys engineers continuously validate and rate new threats from internal and external sources, Qualys TP’s Live Threat Intelligence Feed displays the latest vulnerability disclosures and maps them to your impacted IT assets. You can see the number of assets affected by each threat, and drill down into asset details.
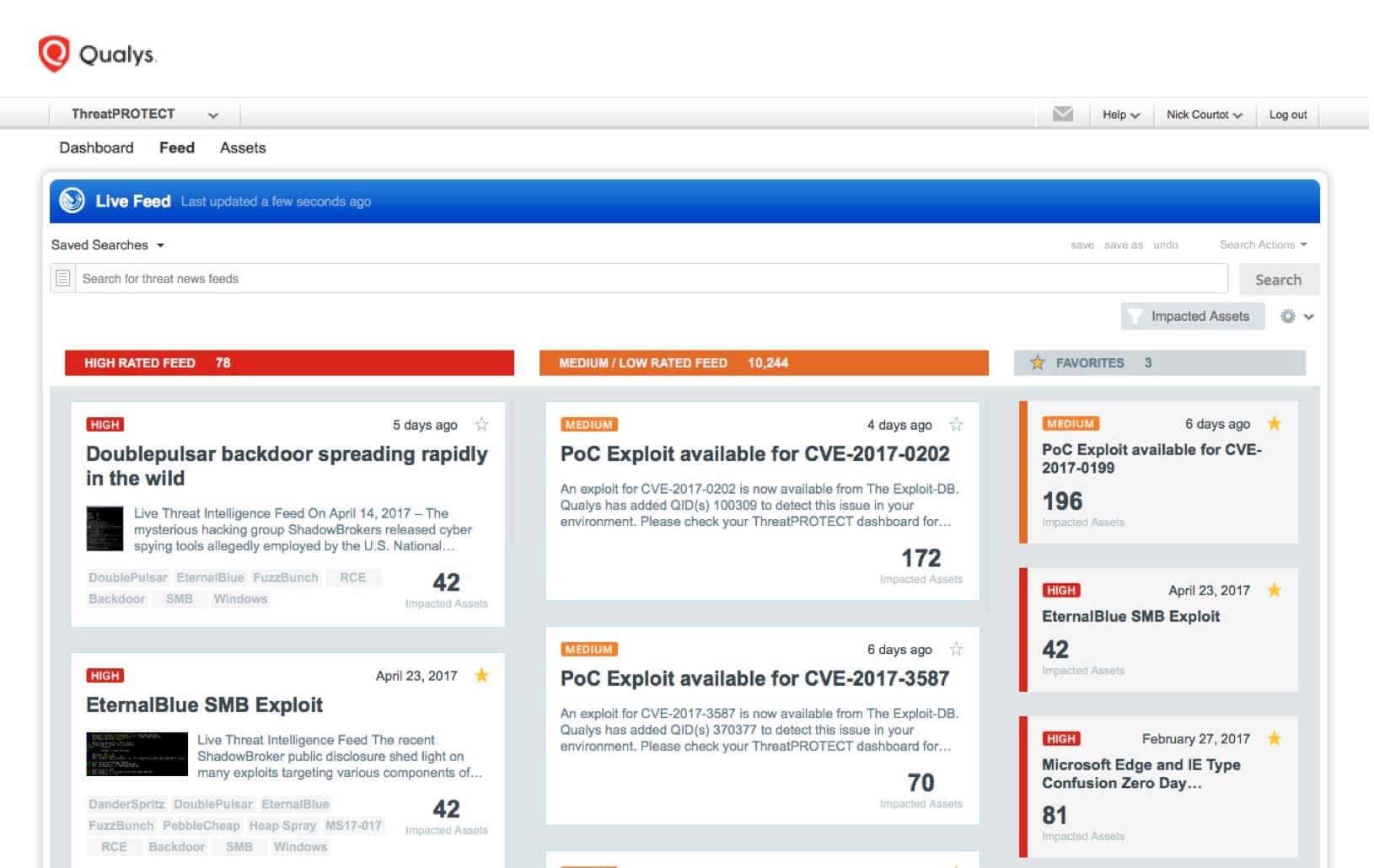
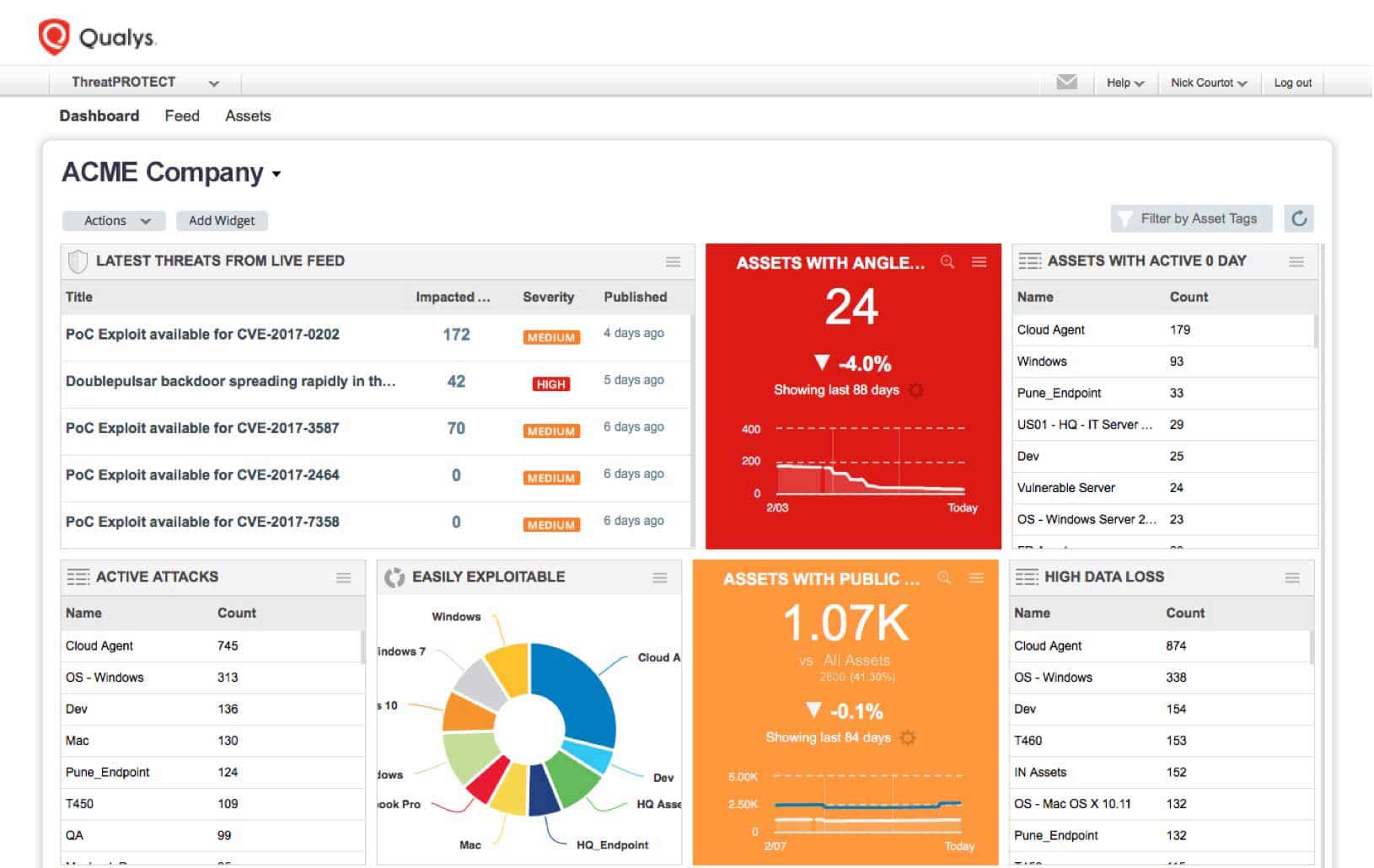
Centralized Control and Visualization Panel
A single, dynamic dashboard includes customizable views, graphs and charts, giving you a clear and comprehensive view of your threat landscape at a glance in real time. You can create multiple dashboard views, and break down vulnerabilities by real-time threat indicator (RTI) types, such as zero-day exploits.
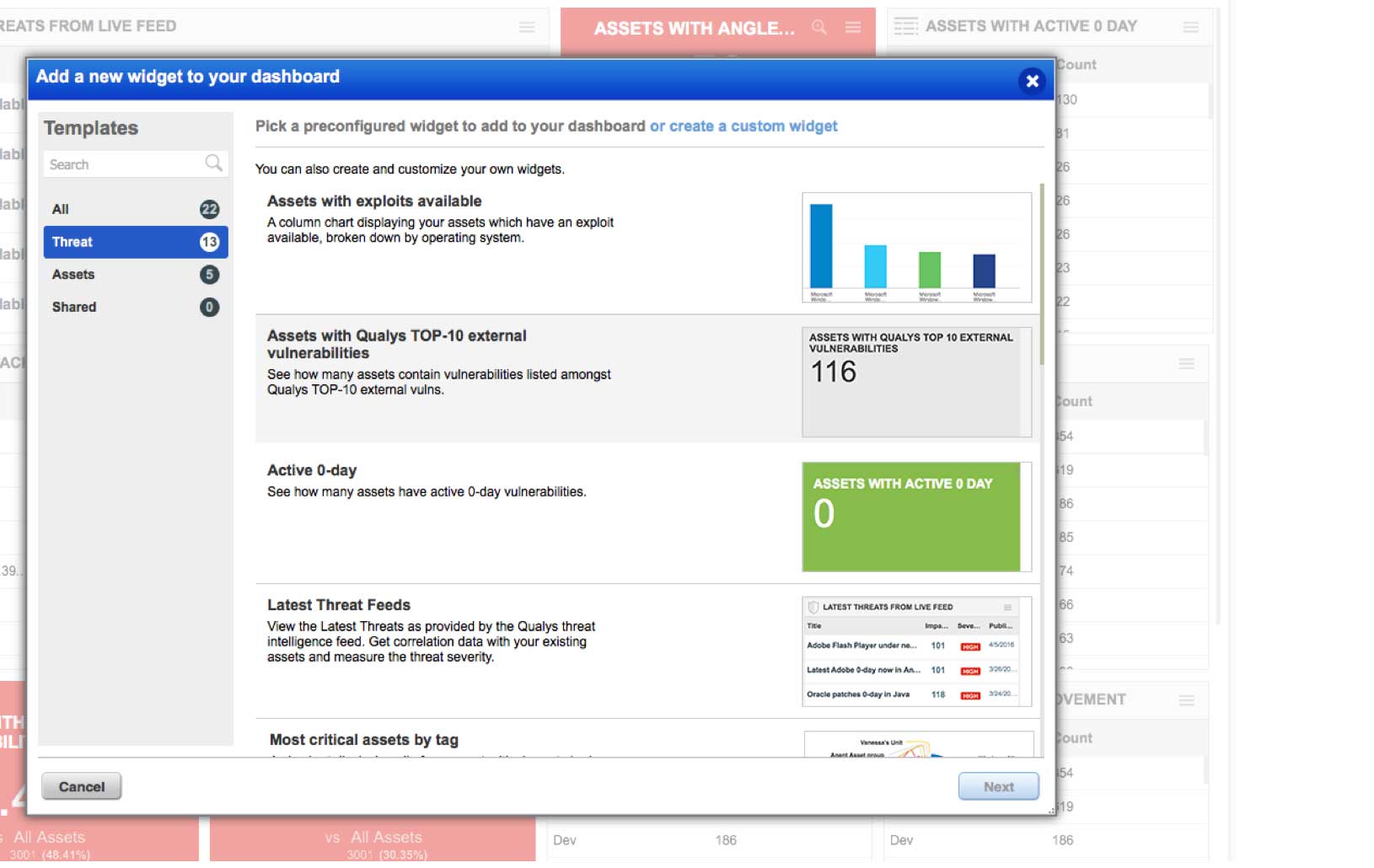
Powerful Search Function
Qualys TP’s search engine lets you look for specific assets and vulnerabilities by crafting ad-hoc queries with multiple variables and criteria. You can sort, filter, drill down and fine-tune results. Queries can be saved and turned into dashboard widgets, which can display trend graphs.
Stay on the Right Side of GDPR with Qualys VM and Qualys TP
Organizations must know at all times which vulnerabilities are present in their IT assets; understand the level of risk each one carries; and plan remediation of affected IT assets accordingly.
If an InfoSec team remediates the right vulnerabilities at the right time, its organization will avoid falling prey to most cyber attacks, and slash its risk of data breaches and non-compliance with GDPR.
In this blog series’ next installment, we’ll explain the importance of managing vendor risk for GDPR compliance, and how Qualys can help you solidify this essential security practice.
(Jimmy Graham is a Director of Product Management at Qualys.)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
GDPR Is Here: Assess Risk from Vendors and from Internal Teams