SSL Pulse Now Tracking Forward Secrecy and RC4
Table of Contents
In October we made several changes to how we produce our monthly SSL Pulse reports. They include starting tracking Forward Secrecy and RC4, and removing the requirement to mitigate BEAST server side.
Forward Secrecy
Given the increased importance of Forward Secrecy (FS) in SSL/TLS server configuration, SSL Pulse now tracks support for it among the servers in our data sample.
Just before the October SSL Pulse scan began, we made some tweaks to the way we test, moving away from a simple binary test (Yes or No for Forward Secrecy support) to something more granular and more useful. Now, there are several possible outcomes:
- Not supported – there are no FS suites in the server configuration.
- Some FS Suites enabled – the server negotiates FS with some browsers.
- Used with modern browsers – all modern browsers negotiate a FS suite. This will typically happen with a server that has support for ECDHE suites.
- Used with most browsers – most browsers negotiate a FS suite. This will typically happen with a server that supports ECDHE suites, but falls back to DHE for clients that do not support Elliptic Curve cryptography.
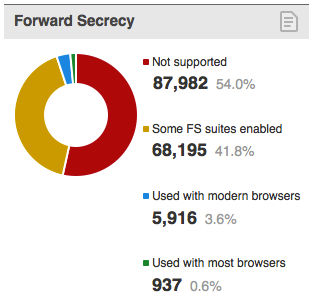
You can see the October results in the following screen capture:
The results show that a large chunk of the servers (54%) does not use Forward Secrecy with any of the desktop browsers. However, a pretty large chunk (41.8%) does use it with some of the browsers. Only a small number support Forward Secrecy with modern browsers (3.6%), and an even smaller number (0.6%) support robust Forward Secrecy across most browsers.
RC4
We took this opportunity to also start tracking support for RC4 suites. As you may remember, earlier this year we learned that RC4 is much weaker than previously thought. In SSL Labs we now categorise RC4 support as follows:
- Not supported – no RC4 suites supported.
- Some RC4 suites enabled – server configuration contains RC4 suites, but they might not be actually used. For example, some servers will keep them around to use as a last resort.
- Used with modern browsers – RC4 is used with at least one modern browser. This shows the servers where RC4 is not used as backup.
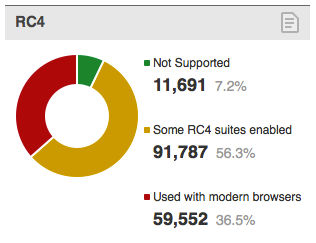
And the results are as follows:
As you can see, the green area is very small; only 7.2% servers do not support RC4. This is not very surprising, as RC4 is one of the most popular ciphers in SSL. Most servers (56.3%) have at least one RC4 suite enabled, but they are not always used. But more than a third of servers (36.5%) actually use RC4 with at least one modern browser. This is the number we need to bring down.
BEAST
This month we stopped requiring server-side mitigation for the BEAST vulnerability. Even though BEAST can still be a problem for some, the impending threat of RC4 means that we must give up on BEAST so that we can start phasing RC4 out.
Given that we are not yet penalizing servers that support RC4, the change in our rating means that there is a much higher number of servers that we consider secure:
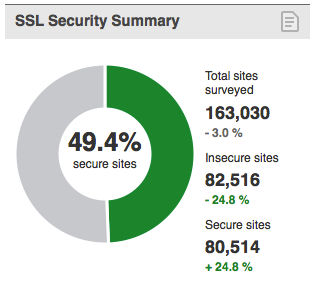
But, with more than 50% of the servers supporting RC4, the number of secure sites will most definitely fall again in the following months.