Heartbleed Remediation Report Now Available in QualysGuard
Update2: It seems the focus for many organizations has shifted from patching the OpenSSL code to finding and replacing SSL certificates that might have been exposed. We will host a webinar on Thursday, April 24, 2014 at 10am PDT entitled "A Post-Mortem on Heartbleed – What Worked and What Didn’t" in which Jonathan Trull, the CISO for the State of Colorado, and I will cover the technical aspects of the bug, testing for its presence, how to exploit (with live examples) and some recovery strategies, both in theory and practice.
Update: We have added another Filter to this report. We now have "Heartbleed – All" and "Heartbleed – Active" that help you in your reporting around this vulnerability.
Original: The Heartbleed OpenSSL bug (CVE-20-14-0160) caught everybody by surprise last week, and the scope and impact of the issue can’t be overstated. Mitigating the impact of Heartbleed is a daunting process since it has been in the wild since March 2012 and because attacks that use it leave no footprints.
When Heartbleed was discovered, Qualys added detection capabilities to QualysGuard within 24 hours. We then added new Heartbleed reporting to the Certificates Dashboard in QualysGuard that helps organizations move efficiently through the patching and certificate cleanup process. Now, you can use the following selections in the Filters menu to quickly identify which certificates might have been affected by Heartbleed:
- Heartbleed – All: lists all certificates that have been used on systems that were (or still are) vulnerable to Heartbleed.
- Heartbleed – Active: lists all certificates currently in use on systems that are still vulnerable to Heartbleed.
In addition, administrators can search for certificates that were issued any time before the systems were patched to determine which certificates are "at risk" and should be revoked or replaced.
Our ability to deliver detection and reporting to our entire QualysGuard customer so quickly after the discovery of Heartbleed demonstrates the flexibility of our cloud-based platform. We will continue to iterate and improve our capabilities to make the recovery from Heartbleed as painless as possible for our customers.
Heartbleed Remediation Reporting Step-by-Step
- Navigate to the Assets section of QualysGuard.
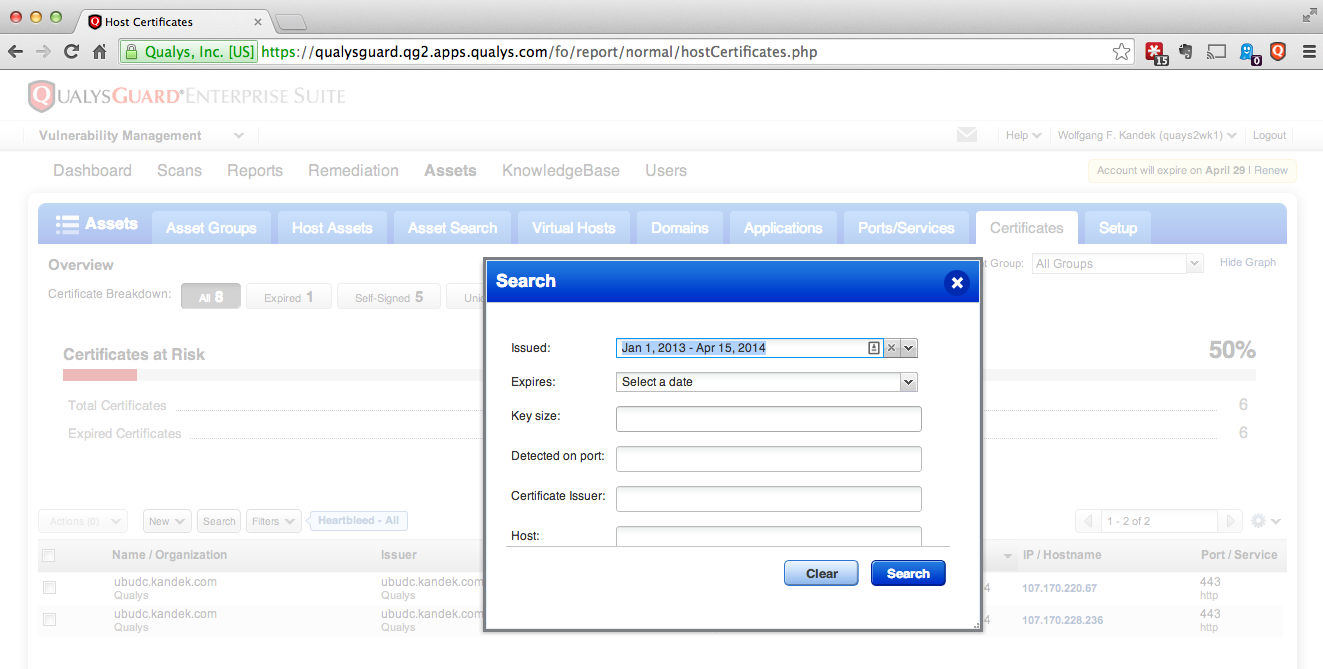
- Select the Certificates tab, click the Filters dropdown and choose "Heartbleed – All" to see all affected hosts.
- After you have patched some or all of the affected hosts, click Search and select Fixed to list only remediated hosts that can be issued new certificates.
- Search for all certificates issued before the patch date to identify certificates that may need to be replaced (in this example 14 April 2014).
- To share with others, export the data in the format of your choice.

Nice report!
I would like to see an option to filter/select specific asset groups for this report.
Sridhar – there is a "Select Asset Group" drop down at the top right corner that might meet your needs.
I’d like the ability to:
We had a number of Entrust Intermediate certs show up as vulnerable, however, it doesn’t appear they’re at risk.
https://www.entrust.com/openssl-heartbleed-bug/
Matthew, The TrustForce software from Venafi will allow you to do all those things and can also replace the certificates on the affected systems.
Is it based on old scan result?
DO I need to run the scan again before run this report?
Yes it is based on existing results.
It should work immediately, one condition though if you only scanned for the Heartbleed QIDs then you will not need to rescan and also include the QID for certificates 86002.
see our updated instructions: https://community.qualys.com/docs/DOC-4739
Hi,
I filter the data in "Heartbleed-Active", but while i click into 1 object, the vulnerability detail is empty. How can I understand this situation of the certificate report? the site is in vulnerable or not?
Thanks.