Qualys and BMC Join Forces to Close the SecOps Gap
In recent years cybercrime has gone from an array of independent hackers to a global industrialized operation that utilizes collaboration, worldwide coordination and advanced criminal techniques to evade detection. One would expect this increased organization and sophistication would improve the speed at which “hackers hack.” And you would be correct: according to a recently released report, the time between an exploit announcement and the first attack is typically just 7.5 days, down from just under 10 days in 2008.
Your organization is likely already struggling with meeting internal and regulatory requirements for patch times. In addition, vulnerabilities and their risk to the organization are increasing each day, as hackers are now able to weaponize new vulnerabilities faster than ever.
It turns out that more than 80% [1] of attacks target known vulnerabilities and that 79% [2] of vulnerabilities have fixes available on the day of disclosure. So why is it taking so long for enterprises to remediate vulnerabilties in a timely manner once they are detected?
The issue in most enterprises is that there is a gap between the team that is responsible for compliance (the IT Security team), and the team that remediates the issues that are discovered (the IT Operations team), i.e., the “SecOps Gap.” The Security and Operations teams must better collaborate to accelerate vulnerability resolution and lower the costs of audit and remediation while simultaneously increasing security.
Closing the SecOps Gap
To close the SecOps Gap, enterprises need to implement end-to-end automation of discovery, audit, remediation, and governance. This enables them to fix problems fast, reduce risk, improve enforcement, and free IT personnel to focus on achieving the strategic goals of the business.
Qualys and BMC have joined forces to close the SecOps Gap by integrating their respective technologies in the SecOps Portal.
How the SecOps Portal Integrates BMC and Qualys
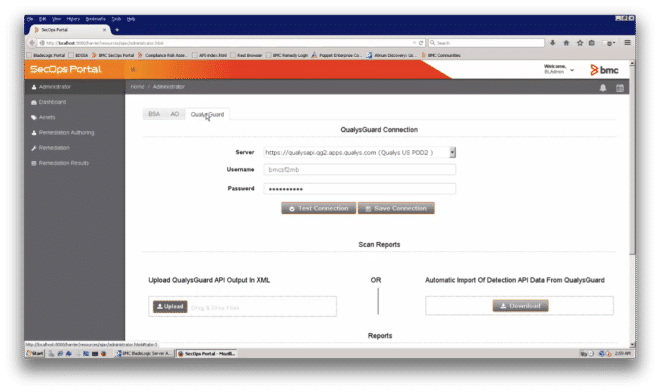
The SecOps Portal (Figure 1) allows enterprises that have deployed BMC’s BladeLogic Server Automation (BSA), Atrium Orchestrator and Remedy AR to import vulnerability scans from Qualys Vulnerability Management (VM). If the SecOps Portal user doesn’t have login credentials to the Qualys Cloud Platform, they can provide a vulnerability scan in an XML output file. If the user has Qualys login credentials, the vulnerability data can be directly imported via the Qualys API (Figure 2).
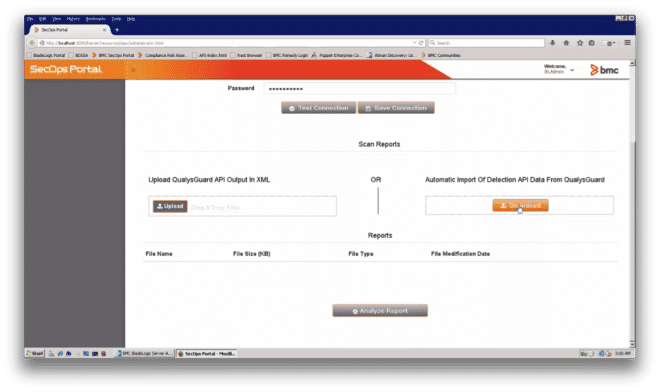
Figure 2: A user importing a Qualys vulnerability scan via the API.
The user can then view a whole variety of summary data for the imported vulnerability scan, including:
- Hosts Scanned, Hosts Managed, Total Vulnerabilities and Out-of-the-Box Remediation (Figure 3)
- Top 10 Vulnerable Servers (Figure 4)
- Potential vs. Confirmed Vulnerabilities, Vulnerabilities by Severity (Figure 5)
- Managed vs. Unmanaged Servers, Severities by Operating Systems (Figure 6)
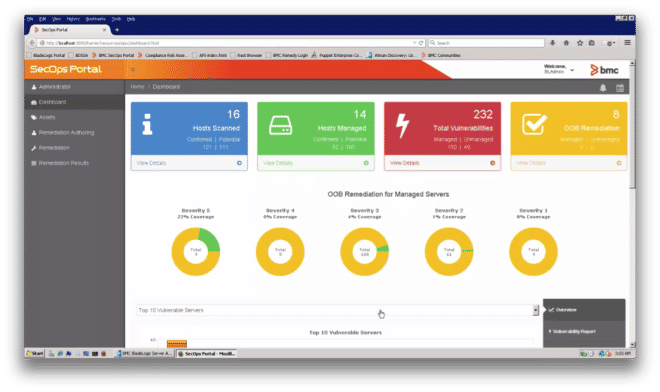
Figure 3: Hosts Scanned, Hosts Managed, Total Vulnerabilities and Out-of-the-Box Remediation
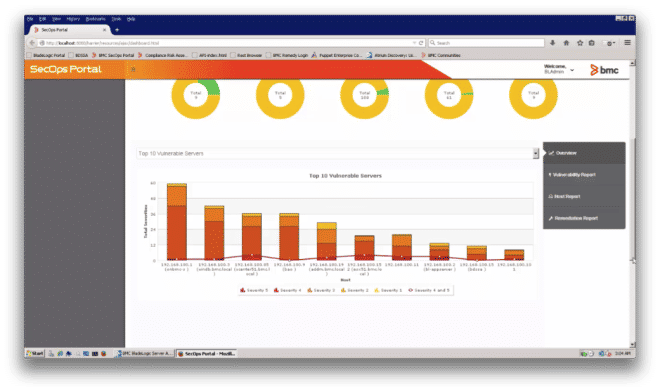
Figure 4: Top 10 Vulnerable Servers
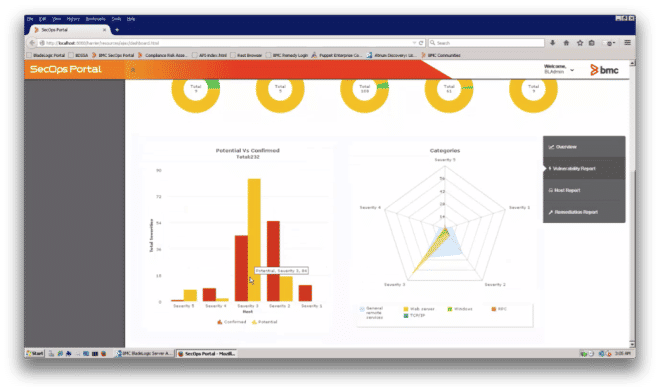
Figure 5: Potential vs. Confirmed Vulnerabilities, Vulnerabilities by Severity
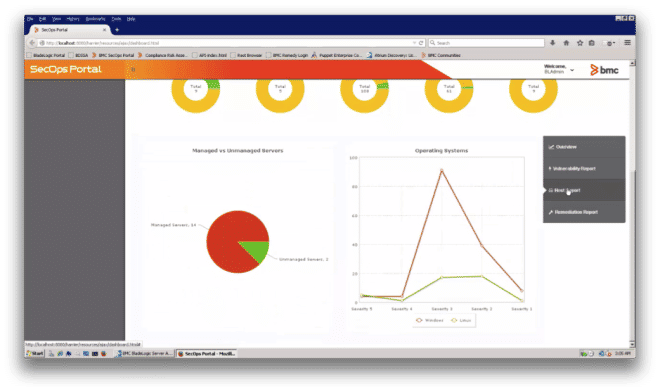
Figure 6: Managed vs. Unmanaged Servers, Severities by Operating Systems
The user can also view the Assets that have been identified in BladeLogic, Qualys, or both (Figure 7).
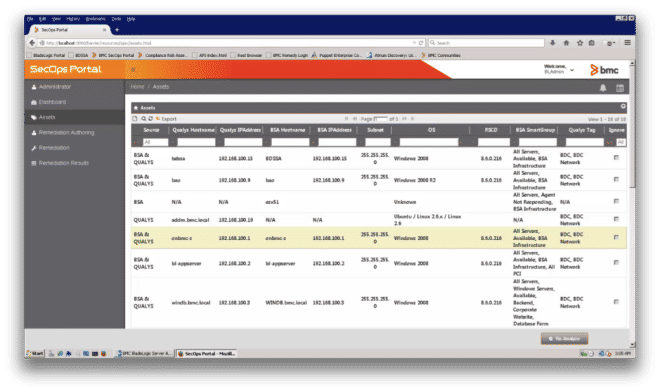
Figure 7: Assets within BladeLogic, Qualys, or both
Now the Remediation screen (Figure 8) is where the magic begins to happen. Here BladeLogic has analyzed the Qualys vulnerability information and determined what the appropriate patches/remediations are. The user has the option to view this data through a variety of filters (e.g., IPAddress, HostName, Operating System, Remediation Type, Severity, etc.).
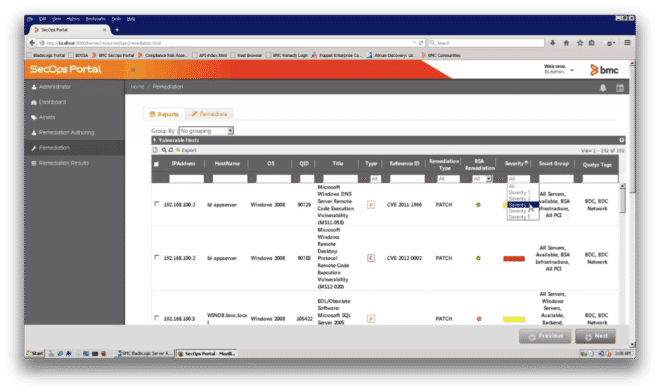
Figure 8: SecOps Portal Remediation screen
The user then may choose all the vulnerabilities that BladeLogic has determined it is able to remediate (Figure 9).
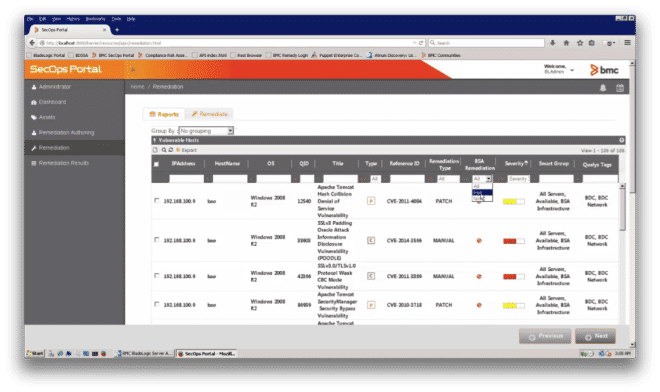
Figure 9: SecOps Portal user choosing all vulnerabilities that can be remediated by BladeLogic
This will ready a remediation job to be deployed (Figure 10).
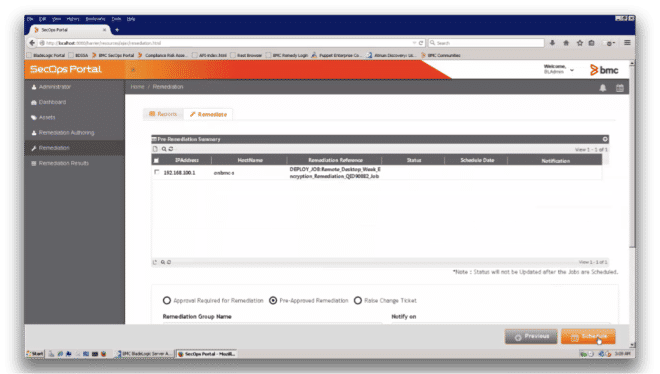
Figure 10: Remediation job about to be deployed
The job is given a group name, is scheduled, and the BladeLogic administrator is notified (Figure 11).
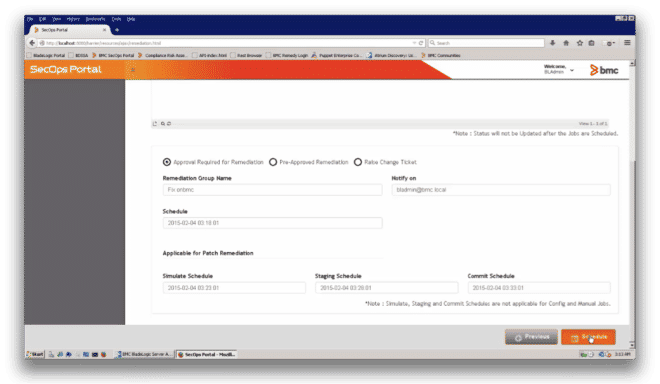
Figure 11: Assigning a group name, scheduling the job and notifying the BladeLogic administrator
This is how the request appears in Remedy AR (Figure 12).
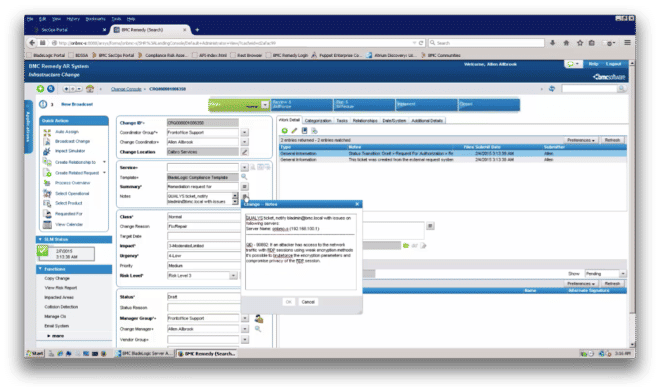
Figure 12: SecOps remediation request as it appears in Remedy AR
The Remedy AR administrator approves the request and it then appears in BladeLogic Server Automation (BSA) Console (Figure 13).
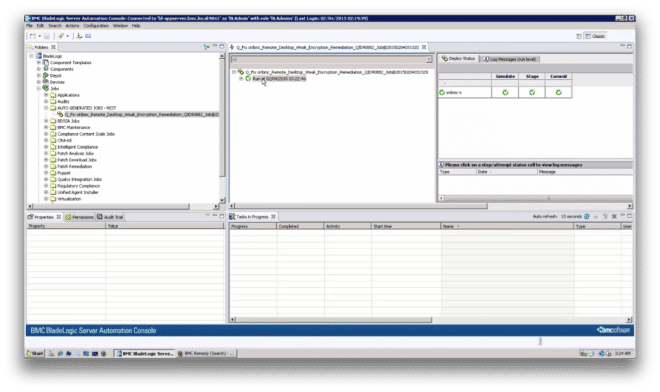
Figure 13: Remediation job in BSA after approval by Remedy AR administrator
The job executes and then appears as completed in Remedy AR (Figure 14).
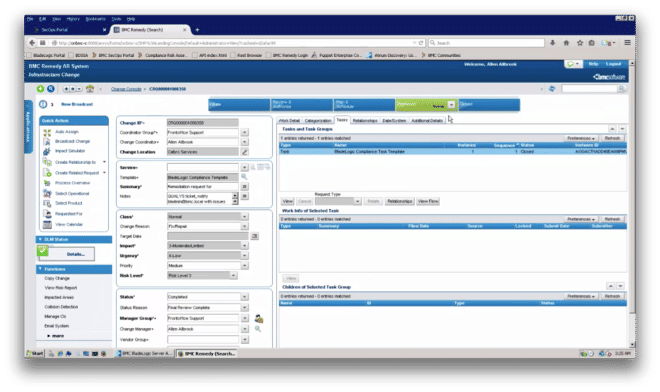
Figure 14: SecOps remediation job now shown as complete in Remedy AR
So there you have it, SecOps gap closed! The time from detecting a vulnerability to remediating it becomes nearly instantaneous. There’s no need for security or operations personnel to manually create trouble tickets, which is extremely time-consuming and highly susceptible to manual entry errors.
Learn More
SecOps Portal and Intelligent Compliance
Qualys Cloud Platform
[1] F-Secure: Companies Risking Their Assets with Outdated Software