ForeScout Integrates with Qualys
ForeScout Integrates with Qualys to Provide Joint Customers Real-time Vulnerability Management Assessment and Mitigation Capabilities
Qualys and ForeScout Technologies, Inc. recently announced a partnership which integrates Qualys Vulnerability Management (VM) and ForeScout CounterACT, to provide joint customers with real-time assessment and mitigation capabilities against vulnerabilities, exposures and violations. This post will detail how the integrated solution can help organizations improve timeliness and efficacy of their vulnerability assessments, automate policy-based mitigation of endpoint security risks, and reduce security exposures and their attack surface.
Secure Your Network Against Advanced Threats with ForeScout – RSA Conference 2016 San Francisco
How CounterACT Works with Qualys
If you’re not familiar with CounterACT, it is an appliance that identifies and evaluates network users, endpoints and applications to provide visibility, intelligence and policy-based mitigation of security problems. Policies within CounterACT allow one to evaluate a one or more conditions and based on the results, take one or more actions. Let’s look at a simple example in the case where a new endpoint is added to the enterprise network (Figure 1).
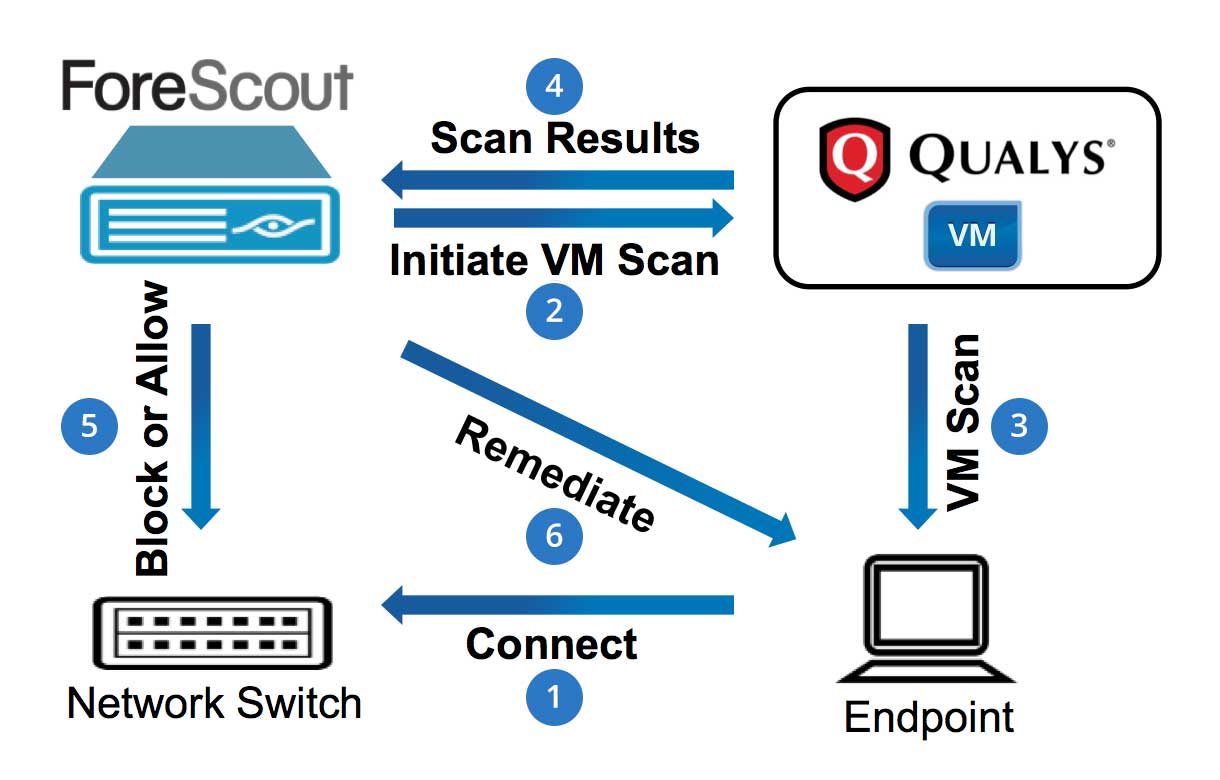
Figure 1: ForeScout-Qualys VM Workflow Resulting from Addition of a New Endpoint
Of course the IT security team doesn’t want a vulnerable machine to be added to the network, so a simple policy can be created within CounterACT to ensure various steps are taken to vet that endpoint before it’s granted full network access. As soon as the endpoint is connected to the network (Step 1), CounterACT detects it, knows it’s a new endpoint and can isolate it until it can be scanned for vulnerabilities.
CounterACT then requests Qualys VM, via its REST-based API, to initiate a scan on that device (Step 2). Qualys VM performs the scan (Step 3) and returns the results to CounterACT (Step 4). For this simple example, let’s assume that a CounterACT user reviews the scan results, sees that the endpoint has several vulnerabilities and decides to temporarily block it from the network (Step 5). The policy can then instruct CounterACT to remediate the endpoint as CounterACT integrates with 3rd-party patch management solutions (e.g., Microsoft SMS/SCCM, WSUS, etc.). After the endpoint is patched, this policy workflow would restart with CounterACT asking Qualys VM to rescan the endpoint (Step 2), and once it is determined that it is a “clean” machine, CounterACT will grant it full network access.
Automated Detection and Mitigation
This is just one example of how the integrated ForeScout/Qualys solution can leverage CounterACT’s continuous monitoring capabilities to increase the chances of detecting transient devices as they join the network. A small sampling of the capabilities of the combined solution are:
- Each time the enterprise initiates its standard periodic vulnerability scan (e.g., weekly), CounterACT will compare the endpoints in the scan results with what is in the CounterACT Inventory. If there are endpoints that are missing from the scan results (usually because they were not connected and/or powered on when the scan occurred), CounterACT can ask Qualys VM to initiate a scan for those endpoints when they next appear on the network.
- Depending on the maturity of the enterprise’s vulnerability management and remediation programs, there may be an extended period of time between when a vulnerability is discovered and when it is remediated, leaving those affected endpoints open to compromise. In these cases CounterACT has the ability to: 1) isolate them from the network, 2) block ports or shut down services that are causing the endpoint to be vulnerable or 3) patch the machine via CounterACT’s integration with 3rd-party patch solutions.
The combined solution can also automate remediation and reduce the gap between detection and mitigation of risks. For example, once Qualys VM system scans a device, CounterACT then analyzes the scan results, and initiates risk mitigation actions if vulnerabilities are detected.
So there you have it, by combining the functionality of Qualys VM and ForeScout CounterACT, the integration provides joint customers real-time assessment and mitigation capabilities against vulnerabilities, exposures and violations.
Implementation Resources
This integration can be obtained from the ForeScout customer portal as a 3rd-party plugin within their Vulnerability Assessment Integration Module. Install the plugin, do some very basic configuration (e.g., provide CounterACT your enterprise’s Qualys API credentials, etc.), and you’re ready to begin creating policies (in addition to those that are included out of the box).
Learn more about: