New Qualys App for Splunk Enterprise Delivers Real-time Dashboard and Analytics for Security and Compliance Data

Many customers that use the Qualys Cloud Platform for vulnerability management are also using Splunk Enterprise to collect their security and compliance data. Thanks to the new Qualys VM App for Splunk Enterprise with the included Qualys Technology Add-on (TA), customers can monitor and evaluate real-time threat alerts and analysis through a single dashboard. With this unified perspective, customers achieve a more complete picture as well as a streamlined workflow – across their entire infrastructure.
Big Data Analytics + Vulnerability Data
 The Qualys App for Splunk Enterprise offers access to valuable, integrated vulnerability data that empowers security operations and incident response teams to more efficiently gather information needed to identify where and when organization may be vulnerable to attack. Additionally, this integration can also be leveraged to collect, analyze and report audit data for accelerated and continued compliance with standards such as PCI, HIPAA, SOX, NIST, and more.
The Qualys App for Splunk Enterprise offers access to valuable, integrated vulnerability data that empowers security operations and incident response teams to more efficiently gather information needed to identify where and when organization may be vulnerable to attack. Additionally, this integration can also be leveraged to collect, analyze and report audit data for accelerated and continued compliance with standards such as PCI, HIPAA, SOX, NIST, and more.
How It Works
The Qualys App for Splunk Enterprise, which can be found in Splunkbase, accesses the Qualys VM data through the Qualys Cloud Platform API. The app streamlines the importing (with ETL capabilities) of the Qualys vulnerability and KnowledgeBase data into Splunk. Within Splunk Enterprise, the Qualys App provides a vulnerability dashboard containing a variety of summary charts as well as multiple vulnerability search tools. For example:
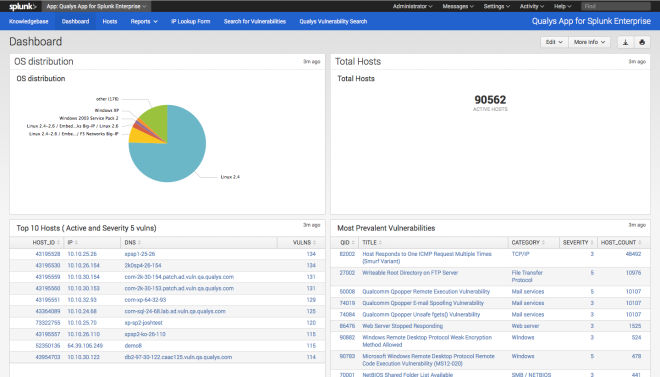
The main Dashboard includes information on Total Hosts, OS Distribution, Top 10 Hosts and Most Prevalent Vulnerabilities (Figure 1).
Days Since Last Scan (Figure 2) provides a timeline of the number of Hosts Scanned, the OS Distribution, as well as details on the individual hosts in the bottom pane.
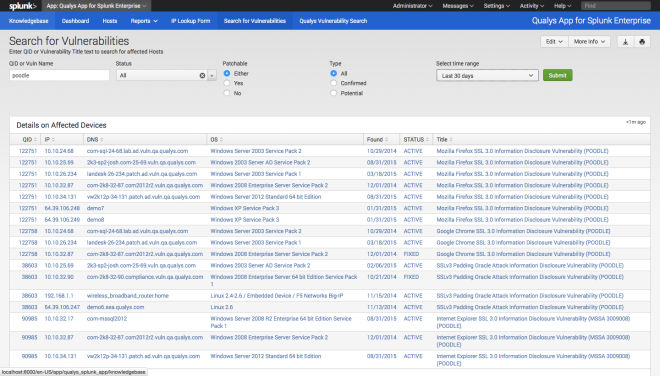
With Search for Vulnerabilities (Figure 3), one of the two search tools, users can search for vulnerabilities by Qualys ID, vulnerability name, time range, whether or not they are patchable, and whether or not that are potential or confirmed. Details on the affected devices are provided in the lower pane.
The other search tool, Qualys Vulnerability Search (Figure 4) provides a timeline of vulnerability counts as well as individual event details. Users can build complex searches across all of the available vulnerability fields and save those searches for repeated use.
The examples above are just the proverbial “tip of the iceberg.” Additional tools include the Qualys KnowledgeBase, Hosts and the IP Lookup Form. The Dashboard also includes preconfigured searches and reports, and can also be configured to display data in formats and aggregations that match your organization’s needs.
Getting Started
Getting started is easy if you’re presently a joint Qualys-Splunk customer.
- Download the App – You can download the present version of the Qualys VM App for Splunk Enterprise (1.0.0) from Splunkbase. Note you will also need the Qualys Technology Add-on (TA) for Splunk. In previous versions we had the TA and the VM App bundled together, now they are separate.
- Ensure You Have Qualys API Access and the Qualys KnowledgeBase Enabled – You will need a Qualys account that includes Vulnerability Management and API access. If your account does not have API access, please contact your Qualys Technical Account Manager to add it and also check that the Qualys KnowledgeBase is enabled for your account.
- Sign up for a Splunk Account – Since the app only works with Splunk Enterprise, you will also need a Splunk Enterprise account. Please contact your Splunk sales representative if you need to upgrade to Splunk Enterprise.
It will only take you a few minutes to upload the app to Splunk, enter your Qualys credentials and the URL for your Qualys API server platform and voila! you’re ready to set the default schedule for syncing data. The first time the app connects with the Qualys API, it pulls all data, after that it pulls changes only.
Once you start using the app, you’ll see that its biggest benefit is the ability to transform Qualys vulnerability data into user customizable, dynamic reports and dashboards to help quickly identify and respond to the most critical threats within your enterprise. Also for the first time, you’ll be able to correlate Qualys and other security data such as IDS/IPS logs in Splunk to create a holistic view of your security posture across multiple tool sets.
Resources
- See Qualys Solutions for Splunk.
- Download the Qualys VM App for Splunk Enterprise now!
- Download the Qualys Technology Add-on (TA) for Splunk now!
- Learn more about the Qualys Cloud Platform.


Very much looking forward to testing this out. Hopefully it’ll be ready by the end of the week as eluded to in the post :-)
When will the next version of this app be available?
Are you ever planning to fix this app? It’s kind of a mess. The docs reference a “TA-QualysCloudPlatform”, which I can’t seem to find anywhere. Does this exist, and I’m missing it? Are you ever planning to clean up the app directory? It has things scattered about that aren’t really supposed to be in the root of the app. I would really like to use this app, but in its current form, I’m not sure that I can. Thanks.
Hi
I tried to intergrate the qualys data into Splunk (only VM and PC), but i am not getting any data to be indexed in Splunk indexer.
I am using 3 splunk servers with distributed setup,
The Addon is configured in both heavy forwarder and Search Head, the inputs are configured in the Splunk Heavy forwarder.
Please help me to resolve the problem