Qualys WAS 4.3 New Features

Feature Highlights
- Override DNS for WAS Scans
- Enhanced Support for Sitemap for Scans
- Enhanced Patchable Detections Logic
- Clarify Time Limit Exceeded and Time Limit Reached and Scan Timeout
- Enhanced WAS Scan Reports
- Implement Web Application Custom Attributes
- User Customizable Mail Settings for When Scan is Launched
- Enhance Tag Selection Component in WAS Module
- WAS Search Lists – Deprecate Compliance Type options
Override DNS for WAS Scans
Our customers wanted to be able to override DNS for the FQDN included in the web application target specification. This would allow customers to scan web apps that may be in development and no DNS entry yet exists, or that there is a different IP address associated with the web application in the development or QA environment than what is available in DNS (typically the production IP). Previously customers would have had to stand up a special DNS server that the appliance uses to be able to manipulate the target IP for these situations, and many of our customers do not have this ability. Most customers can just update their own ‘hosts’ file on their local system to accomplish the DNS override for their system, but there is no way to do this for the Qualys appliance. Now, you can!
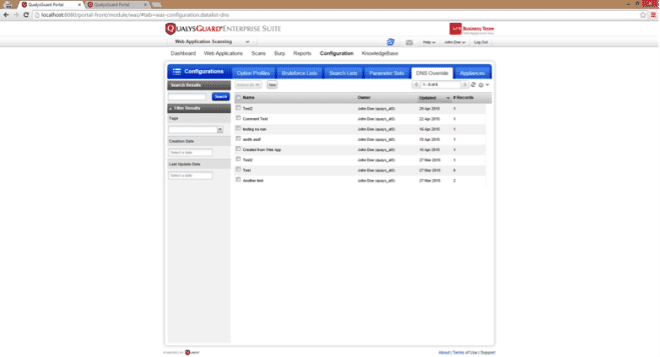
WAS UI > DNS Overrides Section
A new sub-tab under Configuration is added to display list of available DNS override records:
DNS override list has following Actions available:
If user is having permission to create new DNS override record then this button will be enabled.
This will allow the user to edit the existing DNS override record.
The Preview Panel has the name of the DNS override, last updated by, last updated date, tags, and number of web applications associated with the record.
Upon clicking on the number of web applications, you will see a new dialog which shows a list of web applications associated with it.
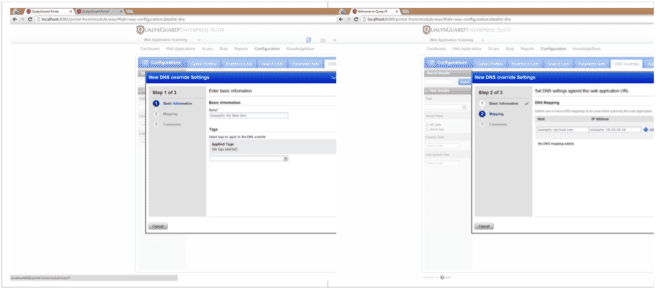
A new step is added in web application create/edit/view dialog to bind DNS Override records with Web Application. Only these selected records will be available while launching scan/schedule for this web application
Scan report will show DNS override record name.
Enhanced Support for Sitemap for Scans
This feature is brought to you so you will now be able to display the sitemap results for a specific scan exactly as it is done already for WebApps. WebApplications blacklist and whitelist can now be created from the directory tree!
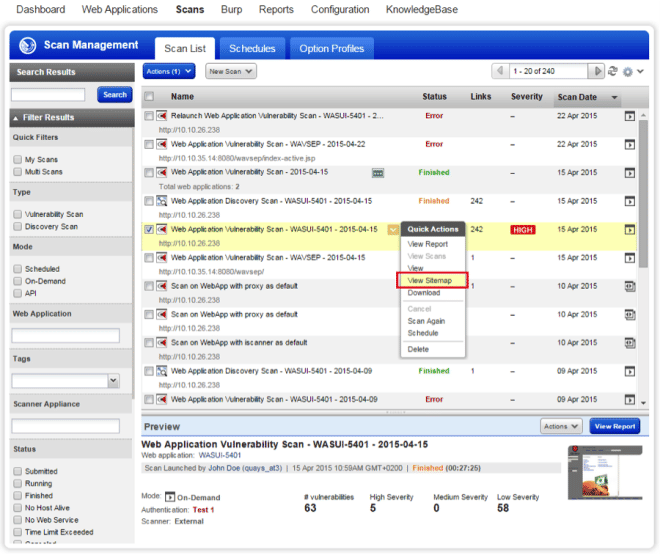
From the Scan List a new “View Sitemap” action can be launched if a scan is selected.
This Sitemap action is also accessible from the context menu.
Or from the Preview panel.
This action opens a Sitemap window the same way as it is in the WebApp section except that data are taken from a scan result.
Enhanced Patchable Detections Logic
- ) Enable Add Patch action even when patch cannot be added
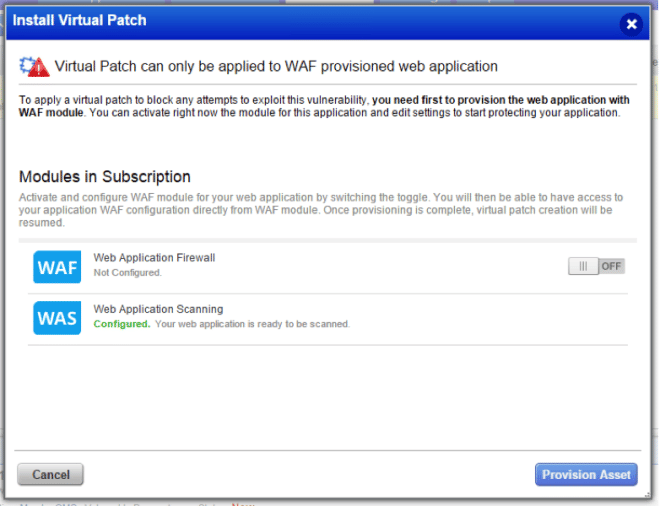
The WAS > Web Applications > Detections section allows users to add a virtual patch to a vulnerability. The contextual action “Install Patch” is however only enabled when WAF module is enabled in subscription and that the web application has WAF module provisioned. This will lead this action for most users disabled, without them the possibility to understand why the feature is disabled.
We now allow for enabling the Install Patch action in Detections datalist in all cases and explain to the user why the action cannot be performed. This will allow user to understand the need of activating WAF module to enhance their security.
When clicking the action, we would display a dialog explaining that user cannot add a patch because <the correct reason> and we explain steps to enable the feature.
When WAF module is not enabled at all in subscription, we will display a dialog explaining that WAF module needs first to be added to the subscription to have virtual patches installed.
A description of the WAF module will help user understand the goal of WAF, and a list of steps will be added to make it clear to the users what needs to be done to have virtual patches feature available.
When WAF module is enabled in subscription, but the web application on which the vulnerability is not yet provisioned on WAF side, we will explain to user that the application needs now to be added to this module in order to apply the patch.
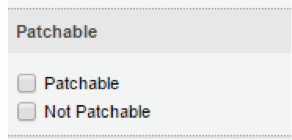
- ) Add Patchable Filter for WAS Detections
This feature provides customers a detection filter that allows them to see only patchable/not patchable detections. Doing so will make it very easy to apply virtual patches and not cause customer to try each one and get confused on why the option is not available for many in the list.
The datalist will provide a new filter Patchable Status with following options:
- Patchable – Show all detections for which WAF module would be able to create a patch for.
- Not Patchable – Show all detections that cannot be patched by Qualys WAF
Clarify Time Limit Exceeded and Time Limit Reached and Scan Timeout
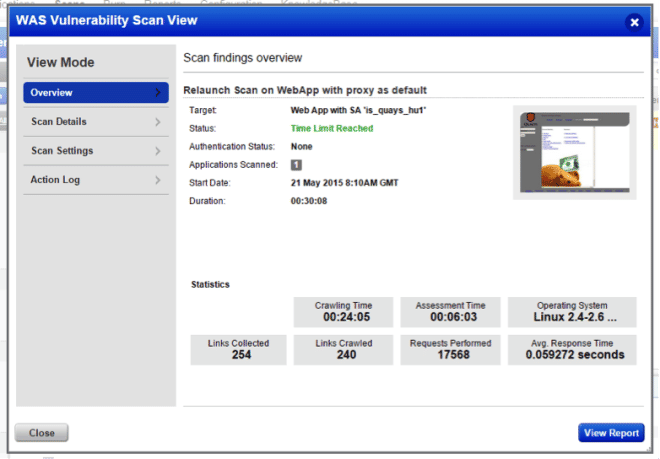
The “Time Limit Exceeded” status indicates that the scan went beyond the time limit when in fact the scan was actually stopped at the time limit. This change will provide clarification that the scan did not go beyond the time limit set by the user.
We now display Time Limit Reached instead of Time Limit Exceeded for following components:
- Status column
- Last Scan Status filter
- Preview Panel
The view dialog will also display the new Time Limit Reached value in its Overview panel.
We now display Time Limit Reached instead of Time Limit Exceeded for following components:
a. Last Scan Status
b. Filter Preview Panel
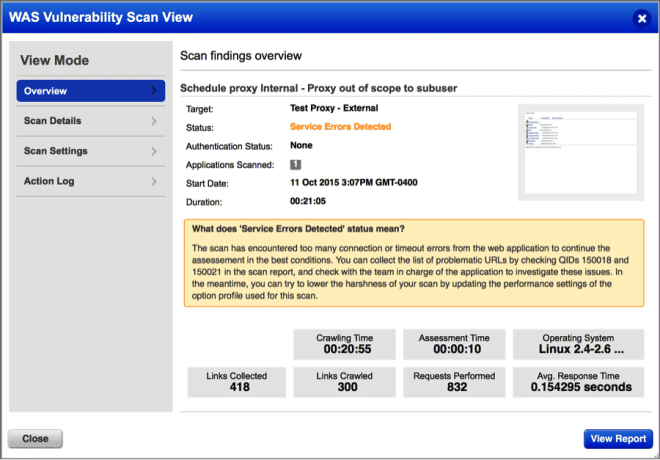
Another issue that has been raised is the problem of scans stopping before the end of the scan, because they reached an internal threshold of target connection / timeout errors.
However the UI reports the scan status as Finished, leading the user to think that the scan thoroughly assessed the web application, which can lead to confusion/frustration. This has been fixed. To help with this feature, the WAS scan engine team has fixed the Critical error conditions for WAS scans, listing the different error cases that we have to support when monitoring scan or processing scan results.
Enhanced WAS Scan Reports
Current scan reports display a status along each detection, which corresponds to the status when comparing vulnerability detection among all scans selected.
This means that when only one scan is selected, the status always displays NEW, which is misinterpreted by users as being a vulnerability newly discovered for the web application in that scan. This is now corrected!
The main changes are:
- ) For scan reports, we will add a mention for the Status filter to explain when this filter is effectively used
- ) Whenever it is possible we will not show the Status filter options when only one scan is selected
- ) For any scan report generated with only one scan, we will not add anymore the finding status
The Scan Report view dialog will add in the Filter step, Vulnerability Filters > State Filter section a notification block explaining to users its application context.
If only one scan is selected, the status options in Filter step will be replaced by notification block explaining that the status filter has no meaning in this context.
When more than one scan is selected, we will display the usual notification block explaining how status is computed in scan reports.
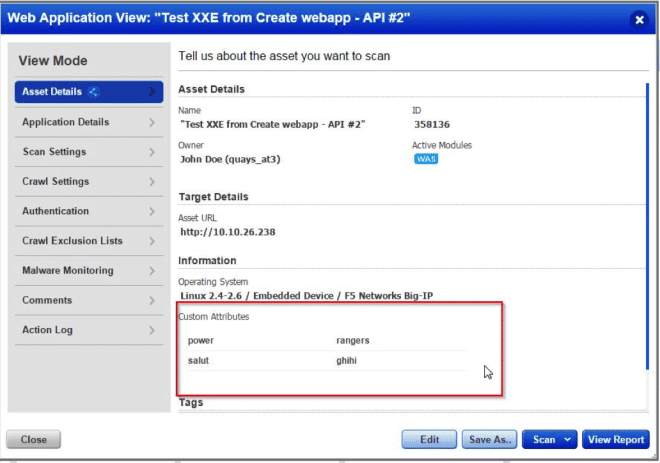
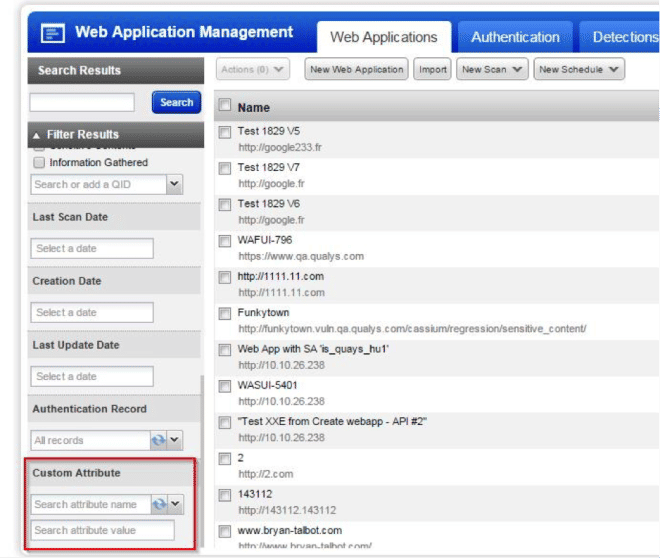
Implement Web Application Custom Attributes
Users requested that they would like to associate to each asset, different information, like their internal host ID. This feature changes the details of a web application, in order to support custom attributes for them.
We removed Information data section on “Application details” of web application dialog.
Asset details additions.
When you edit a web application on which has previous business information data, these old fields data are always displayed. In order to remove them, click on remove link. The save process will delete these old information and won’t be displayed the next edit time.
Custom attributes filter results.
For this, we added a combobox on the filter results left panel for “Custom Name Attribute.” Below, we have a search field used to find the associated “Custom Value Attribute.” These two fields allow values which are not present in the datalist.
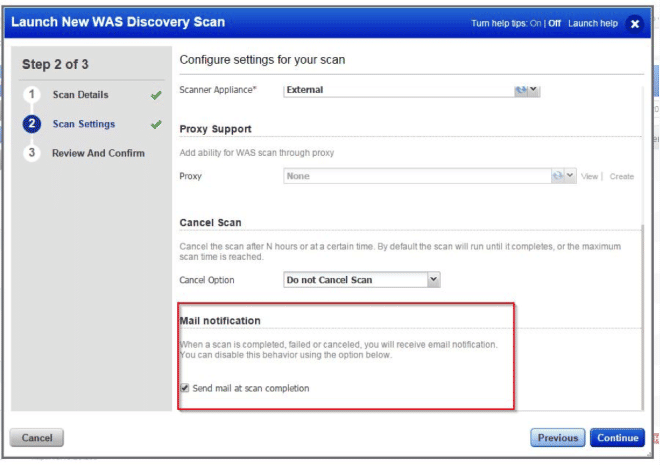
User Customizable Mail Settings for When Scan is Launched
After successful completion or cancellation of scan, an email notification is sent to an email address or set of email addresses. Now you have the ability to disable this for automation testing purpose for example.
Scan settings edition step on scan dialog
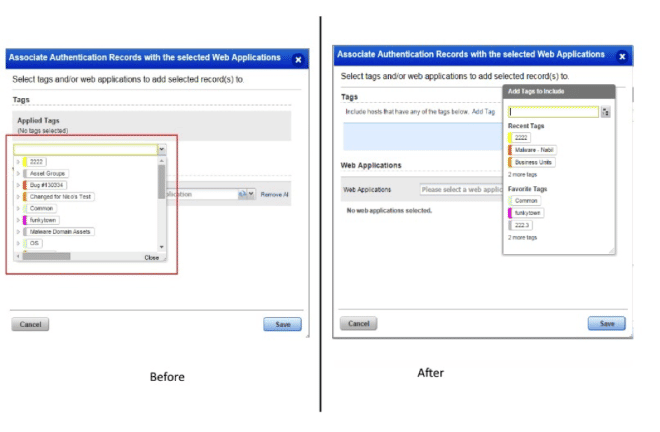
Enhance Tag Selection Component in WAS Module
This feature enhances the current tags selection component used in the WAS Webapp/Scorecard reports to look and work the same as the one implemented in VM and other modules, for consistency.
Example as follows:
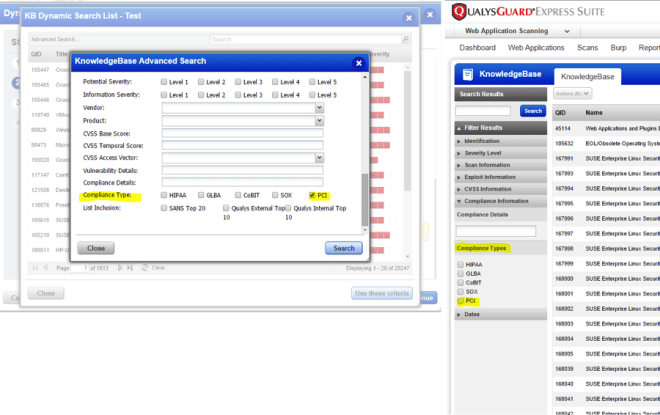
WAS Search Lists – Deprecate Compliance Type Options
Compliance Type – PCI has been removed from Create/Edit Dynamic Search List dialog.
To open the advanced search panel:
- Launch Create Dynamic Searchlist>Go to Criteria tab>Set Criteria
- Click Test button>Click Advanced Search button
Please see attached screenshot:
Release Schedule
For details about the release dates for specific platforms and to subscribe to release notifications by email, please see the following: