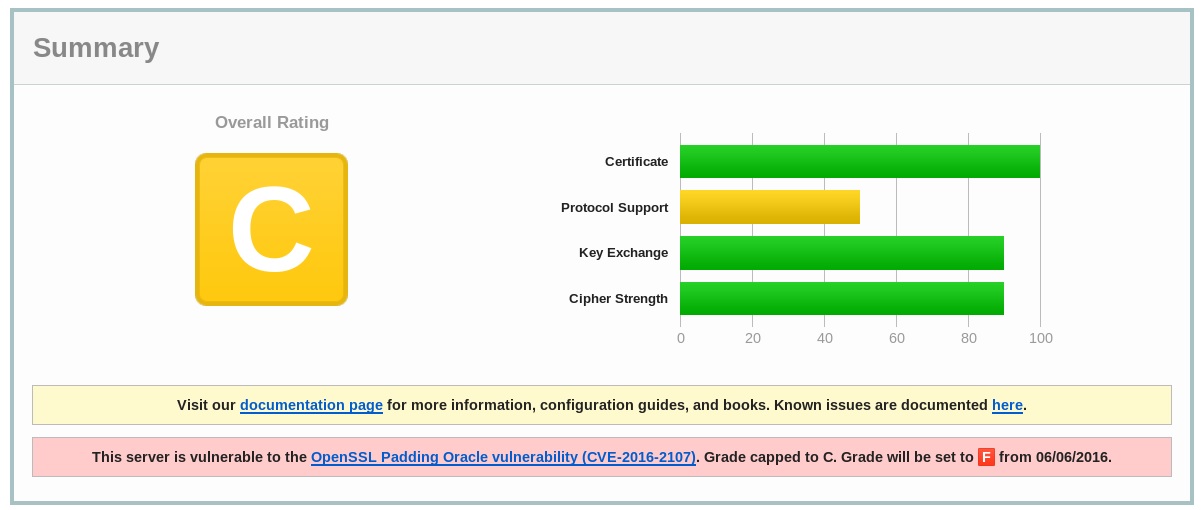
OpenSSL CVE-2016-2107 Grading Update
We are releasing an update to the grading criteria, version 2009m, to respond to the discovery of the OpenSSL vulnerability CVE-2016-2107 announced in the OpenSSL Security Advisory [3rd May 2016]. This vulnerability can be exploited by MITM attacker using a padding Oracle attack to decrypt traffic when the connection uses an AES CBC cipher and the server supports AES-NI.
We are giving advance notification for the grading criteria changes. Currently, if the server is found to be vulnerable to this attack, grades are capped at C. Grades will be capped at F from June 6, 2016.
I have the latest openssl version installed: 1.0.2h-1+deb.sury.org~trusty+1 But i still receive grade F.
More information below:
openssl version
OpenSSL 1.0.2h 3 May 2016 (Library: OpenSSL 1.0.2g 1 Mar 2016)
This is loaded by openssl:
ldd /usr/bin/openssl
linux-vdso.so.1 => (0x00007ffd3fdfc000)
libssl.so.1.0.2 => /usr/lib/x86_64-linux-gnu/libssl.so.1.0.2 (0x00007fd3aa470000)
libcrypto.so.1.0.2 => /usr/lib/x86_64-linux-gnu/libcrypto.so.1.0.2 (0x00007fd3aa028000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fd3a9c63000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fd3a9a5f000)
/lib64/ld-linux-x86-64.so.2 (0x00007fd3aa6d7000)
The Apache SSL module is also using the same library:
ldd mod_ssl.so
linux-vdso.so.1 => (0x00007ffcadb21000)
libssl.so.1.0.2 => /usr/lib/x86_64-linux-gnu/libssl.so.1.0.2 (0x00007efed9c33000)
libcrypto.so.1.0.2 => /usr/lib/x86_64-linux-gnu/libcrypto.so.1.0.2 (0x00007efed97eb000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007efed95cd000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007efed9208000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007efed9004000)
/lib64/ld-linux-x86-64.so.2 (0x00007efeda0d2000)
Jochem,
We have the exact same problem… We did the upgrade all seems OK but we still have a failing grade.
Did you find a solution?
How were you able to update mod_ssl to link to the new files, e.g.:
libssl.so.1.0.2 => /usr/lib/x86_64-linux-gnu/libssl.so.1.0.2 (0x00007efed9c33000)
I followed this tutorial: http://fearby.com/article/update-openssl-on-a-digital-ocean-vm/, but didn’t work.
Hi,
How did you solved the problem, because, I’ve the same issue and I don’t understand how to solve the problemwith my grade F
Many thanks
We’ve noticed we get an ‘a’ if we use two-way ssl, but an ‘f’ for sites with one-way ssl. Is this a bug in the testing?
For the Apache users on Ubuntu you can use this PPA: https://launchpad.net/~ondrej/+archive/ubuntu/apache2
For PHP users see http://stackoverflow.com/questions/11495034/why-does-phpinfo-have-a-header-version-and-library-version-what-are-the-differe
Since you now have a blog report on this CVE, might you consider linking to it on the SSL Labs test page, instead of just pushing link traffic to CloudFlare?
Our setup also gets an F rating but the version we are running is not vulnerable according to debian security page on the exploit
We see the same problem in tens of servers, all wheezy servers with latest openssl + nginx report vulnerable to CVE-2016-2107.
Same here with CentOS 7 server, still giving vurnerable for CVE-2016-2107 while I have OpenSSL 1.0.2h installed.
I am facing issue OpenSSL Padding Oracle vuln CVE-2016-2107
my OS version CentOS 6.6 64 bits application apache 2.4
install updates -> reboot server -> service nginx restart. It`s work!