Prioritizing Remediation: Plug into the Firehose of Vulnerability Disclosures and Correlate
This is part two in a three-part series on prioritizing vulnerability remediation, where we’re explaining five basic requirements for identifying on an ongoing basis which IT assets you must patch right away.
In our first post last week we met Steve, a nightmare-stricken infosec manager who loses sleep over his organization’s inability to manage its IT environment’s vulnerabilities. We also described the first requirement for success: compiling a complete, detailed IT asset inventory.
In this second installment, we’ll spell out two more requirements: Logging the constant stream of vulnerability disclosures; and correlating external threat information with your IT assets’ vulnerabilities.
Plug into the Firehose of Threat and Vulnerability Disclosures

To properly prioritize your remediation work, you must be always aware of the latest threats out in the wild and the most recently disclosed product vulnerabilities.
This information flows uninterruptedly from multiple sources, including industry groups, government agencies, academic researchers, technology analysts and security vendors.
It can be a lot to keep track of. Every year, vendors collectively disclose several thousand vulnerabilities in their products: operating systems, applications, middleware, databases, virtualization software, web servers — you name it.
Before you can act, you must qualify how much of a threat these vulnerabilities represent in the wild. For example, are they “zero day” vulnerabilities for which a patch hasn’t been released?
Are they being actively exploited? Does publicly available exploit code exist? Can they be used in “lateral movement” attacks that let hackers use a compromised system to attack other machines on the same network?
Having a handle not just on the most recently disclosed vulnerabilities, but also knowing which aggravating qualities apply to each is essential to understanding the risks your organization faces at any given moment.
Correlate the External Threat Data with Your Internal Vulnerability Map
It’s also key for you to be able to correlate external threat information with the vulnerability gaps that exist in your IT environment.
Lets say you have a comprehensive, detailed view of your IT asset landscape — our first requirement. And you’re also up to date on the universe of thousands upon thousands of disclosed vulnerabilities — our second requirement.
Now you’re in a great position to connect the dots by meshing both sets of internal and external data – your IT asset information and disclosed vulnerabilities – and correlate them. You must do this continuously, so you’re alerted whenever there is a match. This will give you a dynamic snapshot of all the vulnerabilities that exist in your IT environment at any given moment.
You also must be able to proactively conduct specific searches, combining multiple variables, to find assets that may be potentially at risk.
How Qualys Can Help You
A pioneer and leader in vulnerability management, Qualys recently tackled the challenge of prioritizing vulnerability remediation by developing Qualys ThreatPROTECT, a service designed to help organizations get this problem under control.
ThreatPROTECT is tightly integrated with the Qualys Cloud Platform and suite of security and compliance applications, in particular with the core Vulnerability Management and AssetView solutions.
This integration helps infosec teams get a clear, comprehensive view of their organization’s threat landscape via its central dashboard with customizable views, graphs, charts, search engine and real-time feed of the latest vulnerability disclosures.
Within the context of this blog post, we’d like to highlight three of these ThreatPROTECT features.
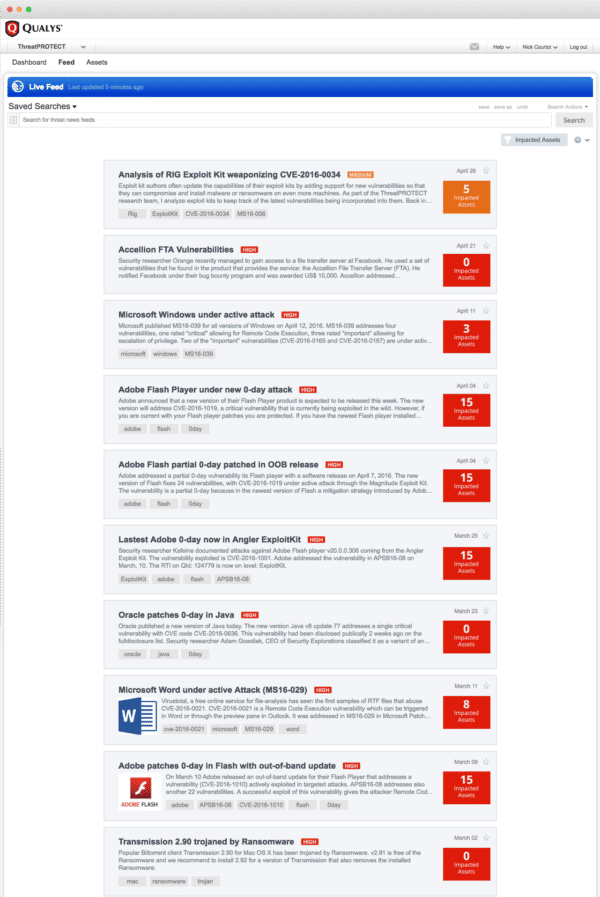
The live feed
ThreatPROTECT’s Live Threat Intelligence Feed keeps organizations up to date on the latest vulnerability disclosures and news. It also displays how many of your IT assets are impacted by each disclosure, thanks to the product’s powerful data correlation capabilities.
Dynamic dashboard views
ThreatPROTECT’s dashboard also contains dynamic, customizable views. They show specific stats, such as which assets contain active zero-day vulnerabilities and which have vulnerabilities included in publicly available exploit kits.
Real-time threat data analysis from Qualys’ world-class research team
Qualys’ global team of researchers constantly monitors and tracks RTIs (real-time threat indicators) data points, analyzing them in depth to further classify them into more precise categories, including: zero day vulnerabilities; vulnerabilities included in exploit kits; vulnerabilities being actively attacked in the wild; and vulnerabilities with a high potential of massive data loss.
The Nightmare Starts to Subside
You can see how an organization that implements the first three requirements we’ve discussed in this blog series can seriously begin to get its remediation prioritization process under control and avoid the fate of our sleepless security manager Steve.
Next week, we’ll cover how to better visualize your threat landscape and make precise assessments of your organization’s risk scenarios .
For more best practices, download our whitepaper “Prioritizing Vulnerability Remediation in the Age of Threat Disclosure Overload.”