Prioritizing Remediation: Visualize and Share the Data, Apply It to Your Organization
This is the last part in our series on prioritizing vulnerability remediation, where we’ve been outlining basic requirements so you can always identify the IT assets you must patch right away.
In our first two posts, we met Steve, an infosec manager whose organization’s inability to manage its IT environment’s vulnerabilities had turned him into an insomniac. We also described the first three requirements for success:
- compiling a complete, detailed IT asset inventory;
- logging the constant stream of vulnerability disclosures;
- and correlating external threat information with your IT assets’ vulnerabilities.
In this last installment, we discuss the last two of the five requirements: having dashboard tools to visualize and share your threat landscape; and making precise assessments of your organization’s risk scenarios.
Visualize and Share Your Threat Landscape with Dashboards, Graphs and Reports
The infosec team in charge of establishing remediation priorities also must communicate its findings, conclusions and decisions via customized dashboard views, graphs, reports and other methods. And it must share this information not just internally among its members but also with a variety of constituencies within the organization, such as CxOs, board directors, developers and IT operations teams.
Vulnerability data is also often shared externally as part of collaborations with industry groups, peer companies, partners and customers. As a result, you need tools that allow you to package this data efficiently and quickly so that it can be used by different individuals and teams both inside and outside of your organization. You must be able to drill down on the correlated data, mine it for patterns, slice and dice it, aggregate it in custom reports and represent it graphically.
In summary, you should be able to measure your progress and remediation efforts with real-time trend analysis and generate reports for a variety of stakeholders.
Precise Assessments of the Seriousness of Certain Threat Scenarios in Your Organization’s Specific Context
Now you’re now ready to factor into your prioritization calculation the technology and business criteria that are unique to your organization. Taking these elements into consideration is essential to make an accurate assessment of your threat scenarios. After all, every IT environment is different, and every organization has its own particular business models, market challenges and competitive strategies.
Let’s say a serious vulnerability was just disclosed for a database software and a patch was made available by the vendor. Company A and Company B both own this particular product, but patching it is a high priority on the first and a low priority on the other.
At Company A, the database is only present in a system of marginal importance that is isolated from the rest of your infrastructure. If that asset were compromised, the risk to Company A would be trivial. At Company B, the database is at the heart of a business-critical, customer-facing, Internet-exposed system. Thus, Company B needs to scramble and patch that vulnerability as soon as possible.
Here’s a sampling of other such criteria to take into account:
- How many users have access to and depend on the vulnerable asset? What are the roles of these users in the organization?
- What software and services run on the asset?
- To which other systems is it connected on the network?
- What would be the severity of the impact if the asset is compromised?
- How much effort is required on the part of attackers to compromise the asset?
How Qualys ThreatPROTECT Helps You with These Two Requirements
Reports, graphs, charts
With the new Qualys ThreatPROTECT, which leverages vulnerability and IT inventory data from Qualys Vulnerability Management and AssetView, you can generate reports, graphs and charts for display on your dashboard, as well as for sharing them with colleagues.
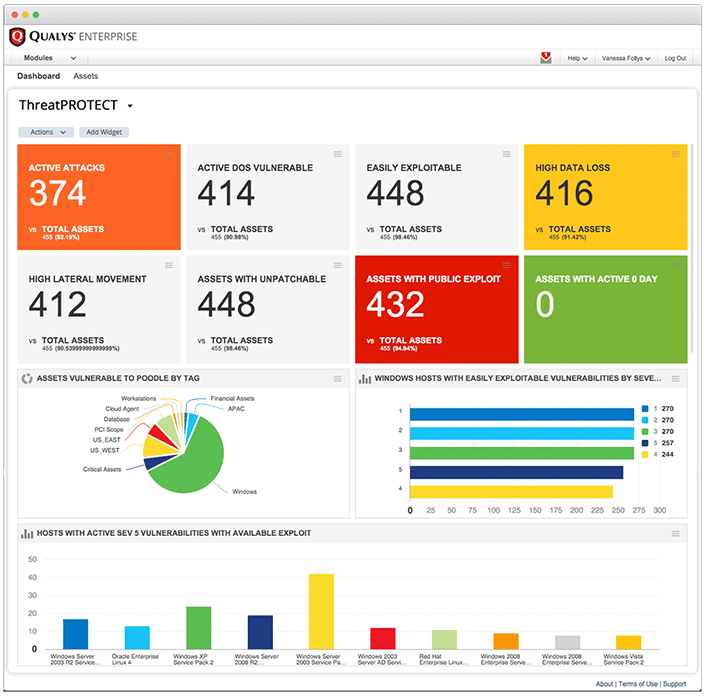
ThreatPROTECT lets organizations create customized dashboards tailored for different IT and business roles, and makes it possible to easily and quickly share reports across the organization. That way, plans for remediating critical vulnerabilities, and ongoing progress, can be swiftly communicated to those responsible for patching the affected system.
Multi-dimensional threat analysis for holistic and contextual risk assessment
Qualys’ global team of researchers constantly monitors and tracks threat data points, such as vulnerability disclosures, active attacks and exploits. But these experts go much deeper, further classifying these Real-Time Threat Indicators (RTIs) into more precise categories that paint a sharper picture of your risk landscape, including:
ZERO DAY: A vulnerability for which there is no vendor patch available and for which an active attack has been observed in the wild
PUBLIC EXPLOIT: A vulnerability whose exploit knowledge is well known and for which exploit code exists and is publicly available, even if no active attacks have been observed in the wild
ACTIVELY ATTACKED: A vulnerability that is being actively attacked in the wild
HIGH LATERAL MOVEMENT: A vulnerability that, if compromised, lets the attacker propagate the attack broadly throughout the breached network
EASY EXPLOIT: A vulnerability that can be exploited easily, requiring few skills or little knowledge
HIGH DATA LOSS: A vulnerability whose exploit will yield massive data loss
DENIAL OF SERVICE: A vulnerability whose payload could overload the compromised systems so that they become permanently or temporarily unavailable
NO PATCH: A vulnerability for which there isn’t a fix from the vendor
MALWARE: A vulnerability associated with malware infection
EXPLOIT PACK: A vulnerability for which an exploit pack is available
It’s important to note that ThreatPROTECT, and the Qualys applications suite that it’s a part of, are all cloud based, an architecture that gives customers:
- Continuous discovery of IT assets wherever they are
- Real-time, distributed collection of vulnerability data
- A powerful correlation analytics engine on the backend
Get Control of Vulnerability Remediation and Get a Good Night’s Sleep
We urge you to take care of the five requirements for successful remediation prioritization we’ve outlined in these three posts, and to add ThreatPROTECT to your toolbox. If you do, you’ll have the peace of mind of always knowing which vulnerabilities represent the highest risk to your organization at any given point.
And you’ll be able to sleep soundly at night.

For more best practices, download our whitepaper “Prioritizing Vulnerability Remediation in the Age of Threat Disclosure Overload.”