Agility and Flexibility Needed To Manage Risk Throughout Vendor Relationship Lifecycle
We conclude our series on assessing third-party risk, where we’ve described scenarios in which an automated, cloud-based system can help you identify security and compliance gaps among vendors, partners and employees.
As we have outlined in this blog series, CISOs and their infosec teams need clarity and visibility not only into their IT environments, but also across their roster of trusted vendors. Organizations that don’t properly assess and manage the risk of doing business with their vendors, partners, suppliers, contractors and other third parties make their IT network and data vulnerable to hackers.
Why? As part of their business interactions, organizations give hundreds or even thousands of trusted third parties varying levels of access to their physical premises, computer systems and confidential data.
If these third parties are careless, negligent or clueless about complying with regulations and following industry best practices, criminals could breach their security and gain access to your systems and data.
Managing Risk at Every Stage of Your Relationship with Each Vendor
Previously, we described five scenarios in which you need an automated, centralized cloud-based system to run your vendor risk management program effectively.
In this last post, we’ll outline a final problem area: Your company has a deficient method for tracking your fast-changing vendor landscape.
This scenario refers to the need to tailor your vendor risk assessments to the stage your relationship with them is at, such as:
- Current vendors: You must conduct periodic assessments to make sure they remain compliant with your internal processes and rules, as well as external regulations.
- Prospective vendors: You ’re evaluating multiple vendors with the goal of choosing one for a project you’re about to embark on.
- First assessment of a key supplier: You just signed up a company that will be doing important business with you on a regular and long-term basis.
- A vendor slips: You need to do a “post mortem” assessment of the incident to document what happened, why it happened and how it can be prevented going forward.
Managing this process manually becomes a logistical challenge because you’re unable to assess risk with agility and comprehensiveness.

In a hypothetical case study of two CISOs — Emily and Jane — that we discussed in the previous posts, we illustrated how a vendor relationship that starts out successfully can take an unexpected dive years later.
A back-office services outsourcer hired at the same time by Emily’s and Jane’s respective companies started running into financial, operational and technological trouble a few years later.
The automated vendor-risk assessment program Emily had put in place quickly detected the trouble and raised enough red flags that the organization cut off ties with the outsourcer.
Unfortunately, Jane overlooked the importance of having such a program, and continued its relationship with the outsourcer. Eventually, the outsourcer’s systems were breached by hackers who in turn compromised the networks and data of several of its customers, including Jane’s company.
With a cloud-based, scalable software tool, you can quickly and easily design and deploy security assessment questionnaire campaigns for all types and stages of vendor relationships, giving you the agility and flexibility you need.
Automate and Centralize with Qualys Security Assessment Questionnaire
The traditional way of conducting these third-party risk assessment surveys involves emailing questionnaires and tracking and aggregating responses on a spreadsheet, a method that no longer cuts it.
Qualys Security Assessment Questionnaire (SAQ) automates and streamlines this entire lifecycle, including survey design, response monitoring, data aggregation and report generation.
With the cloud-based SAQ, an organization can quickly and precisely identify security and compliance gaps among third parties, as well as internally among its business units and employees.
Because it is built upon the Qualys Cloud Platform, SAQ lets organizations automate risk assessments at scale, meeting the requirements of even the largest ones.
How SAQ Helps You Orchestrate Security Assessments and Compliance Audits
SAQ simplifies the design, distribution, tracking and management of multiple internal and external risk assessment surveys from a web-based central console.
Design Surveys and Track Campaigns
SAQ’s wizard walks users through the creation of campaigns, which can be launched with pre-set due dates and notifications.
Questions can have various types of answer formats, such as multiple-choice check boxes, drop-down menus and open-ended text boxes. Survey designers can also require that evidence files be attached to certain answers.
Meanwhile, a template library helps campaign administrators get started with pre-configured surveys for common regulations like HIPAA, Basel 3 and SOX, and industry standards like PCI.
It’s important to note that these predefined templates are prepared by experts and are always current on compliance requirements. Administrators can also create their own templates and individual surveys with SAQ’s drag-and-drop Template Builder feature.
SAQ also gives organizations flexibility for designing campaigns with varying workflows. For example, a survey can be considered finalized once it’s been completed, or additional steps can be required, such as an expert’s review and a supervisor’s approval.
Distribute Questionnaires
With SAQ, you don’t need to set up user accounts. You enter or select vendor emails and SAQ auto-provisions the surveys. Respondents can complete surveys on browser-based forms, and delegate questions they can’t answer. As deadlines approach, administrators are able to trigger reminder emails to respondents. Organizations can also set up recurring campaigns that need to be run with a specific frequency.
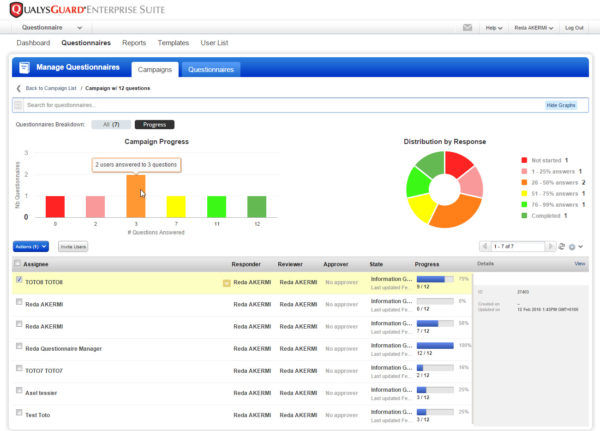
Track Campaigns and Analyze Results
SAQ captures responses in real time and aggregates them in one place: administrators can literally watch as questions are answered, tracking up-to-the-minute progress of campaigns.
Administrators can visualize campaign progress through charts updated live, and they can drill down to see details of individual respondent surveys. This monitoring capabilities help administrators flag questionnaires that respondents may be having trouble understanding.
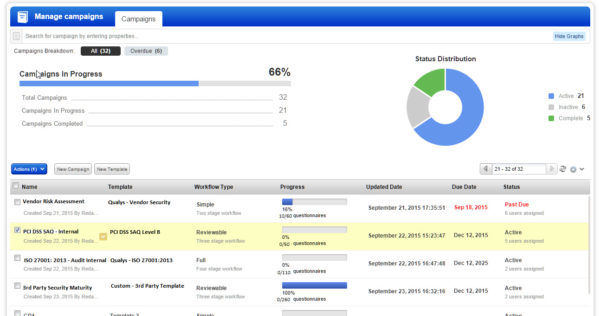
Campaign results can be sliced and diced using a variety of criteria, such as by vendor, recipient or specific questions. SAQ also generates proof of compliance with detailed reports.
SAQ also caters to a variety of corporate constituencies that need to see these survey results in various formats and with different levels of details. For example, it can generate executive-level dashboards for upper management and board members, as well as more granular reports for auditors and compliance officers.
Furthermore, organizations can create custom dashboards designed to reflect the risk and compliance postures of specific third parties, while administrators track and manage simultaneously multiple campaigns at different stages of completion.
In summary, Qualys SAQ is a self-contained, turnkey solution requiring no other tools or surveys, and it’s easy to use. It lets you get answers fast from your third parties so you can manage the risk of giving them access to your IT systems and protect your business.
Try Security Assessment Questionnaire for free with nothing to install.
The Big Picture
If you missed some or all of the previous posts in this series, here’s a rundown of the other scenarios for risk assessment:
In our first post, we outlined an assessment methodology scenario in which your organization lacks a standard third-party risk assessment methodology, employing instead a flawed approach that’s siloed and fragmented.
Next, we dove into risk management and internal assessment scenarios:
— Your vendor risk management program relies on inefficient, labor-intensive and error-prone manual processes.
— You can’t perform internal assessments of employees and supervisors at the scale required in large and geographically dispersed companies.
In our third post, we addressed training and regulation scenarios:
— You’re having trouble coordinating and conducting required employee training.
— Your organization is struggling to keep up with the ever-changing and increasingly complex regulations that apply to it.