As Web Apps Become Top Data Breach Vector, Protecting Them is Critical
There’s one thing that businesses, their customers and cyber criminals have in common: They all love web applications. The reasons for their affection, of course, vary.
Web apps add agility to organizations’ operations such as sales, marketing and customer support, and make business transactions more convenient for customers. Meanwhile, hackers salivate at web apps’ often porous attack surfaces and at their links to backend databases full of confidential information.
With web apps now a key tool for millions of businesses, as well as a major target for criminals, a troubling trend is emerging: The number of successful attacks against them is rising, along with the costs to recover from the resulting data breaches.
As web services power digital transformations in B2B and B2C e-commerce, mobility, IoT and cloud computing, organizations must prioritize web app protection, which infosec teams have historically overlooked.
What can go wrong when your web apps are vulnerable
Web apps are increasingly relied upon by customers, partners, employees and supplier to interact with organizations in many different and often critical ways.
When these apps become attack vectors, the impact on these trusted groups of users is direct, significant and frightening, and the financial consequences for affected organizations are severe.
For example, a Ponemon Institute study released in June found that the cost of data breaches to organizations jumped almost 30 percent since 2013 to an average of $4 million, or the equivalent of $158 per compromised data record. In the U.S., the average cost is higher at $221 per record stolen and $7 million per incident, according to that study, which was sponsored by IBM.
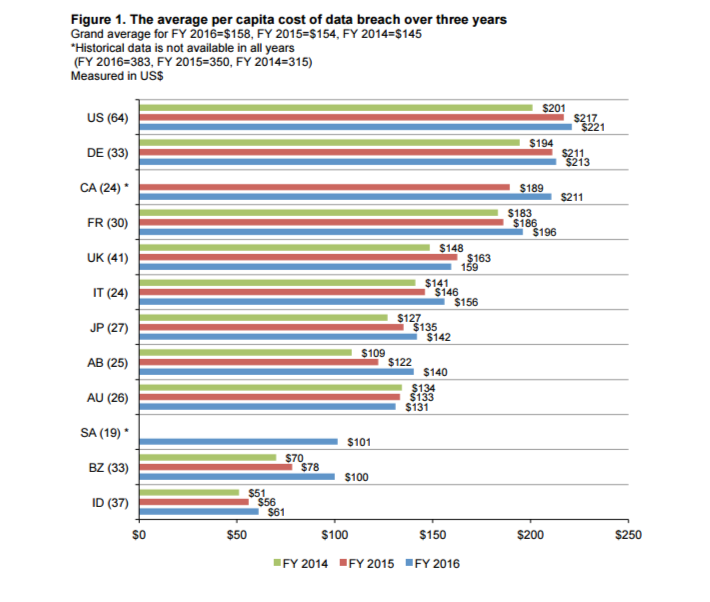
Source: Ponemon Institute’s “2016 Cost of Data Breach Study”
This calculation includes a variety of direct and indirect expenses such as:
- activation of an incident response team
- affected customers’ identification and notification
- special communications and public relations outreach
- forensic investigation expert fees
- establishment of a support hotline
- provision of free credit monitoring subscriptions
- legal costs
- loss of customers
- IT remediation work
- greater difficulty generating new business due to loss of trust
- brand and reputation damage
- the need to discount products and services
- regulatory penalties and fines
Can it happen to you?
Compared to the other attack patterns, such as crimeware and denial of service, web app attacks became the most likely to trigger a data breach in 2015 thanks to a big jump in successful attacks over 2014, according to this year’s Verizon Data Breach Investigation Report.
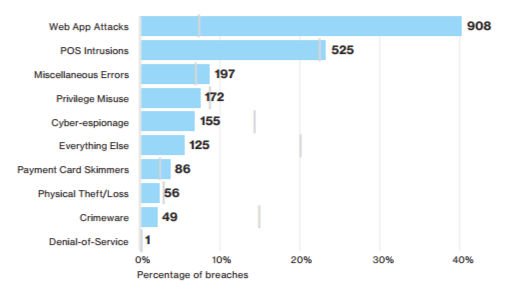
Source: Verizon’s “2016 Data Breach Investigation Report”
Specifically, web app attacks accounted for greater than 40 percent of incidents resulting in a data breach — up dramatically from about 7 percent in 2014. This despite the fact that web app attacks made up only 8 percent of total reported incidents last year, according to the 2016 DBIR.
“These findings are a clear indication that web applications in many organizations are not just exposed, but are disproportionately vulnerable compared to other points of attack,” stated Verizon’s Digital Media Services group in a statement about the DBIR’s findings.
The study, which is based on real-world investigations and reports of more than 100,000 security incidents, also states that “the most interesting discovery in the breach patterns to industry matrix was the rise of web app attacks across the board, but especially for financial services organizations.”
According to the DBIR, 95 percent of the confirmed web app breaches were financially motivated.
“The greater complexity, including the web application code and underlying business logic, and their potential as a vector to sensitive data in storage, or in process, makes web application servers an obvious target for attackers,” reads the report.
The Ponemon study estimates that there’s a 26 percent probability a company will have a data breach involving a minimum of 10,000 lost or stolen records over a 24-month period.
The good news
Web apps are attractive to hackers for a number of reasons, namely:
- Web services are by definition exposed on the Internet, offering an undisguised path to organization’s IT environments.
- Due to poor development and testing practices, web apps are often riddled with security vulnerabilities and configuration mistakes, which lead to common attacks such as cross-site scripting (XSS) and SQL injection.
- When breached, web apps can expose massive amounts of confidential business data.
Fortunately, securing them is straightforward.
For starters, you should follow standard best practices for secure application development and deployment as recommended by institutions such as the Open Web Application Security Project (OWASP), whose Top 10 Most Critical Web App Security Risks report is a must read.
That OWASP report, first published in 2003 and last updated in 2013, aims to educate development teams and IT pros about ways to protect their organizations against high-risk security weaknesses.
You also need to test, monitor and protect web apps with automated tools, such as vulnerability and malware scanners, web application firewalls, pen testing software and code analyzers.
That way, you will automate web app crawling, cataloging and testing, guard web servers from hackers, remove malware from your websites and make the software development lifecycle more secure.
To learn more, download our whitepaper, Best Practices for Selecting a Web Application Scanning Solution.