SANS Survey Report: Organizations’ Continuous Monitoring Programs Must Keep Maturing to Yield Full Benefits
Organizations worldwide have expanded and sharpened their continuous monitoring (CM) programs over the past year, but their adoption of this key set of security practices remains far from perfect.
That’s the main finding from the SANS Institute’s second annual survey on CM programs titled “Reducing Attack Surface” and published Nov. 2016.
Despite tangible improvements, CM “still has a way to go to attain the maturity needed to become a critical part of an organization’s business strategy,” reads the study, which polled almost 300 Infosec and IT pros actively involved in vulnerability assessment and remediation.
The Good, the Bad and the Ugly
 CM, designed to reduce cyber-attack risks, improved the security postures of 63 percent of respondents’ organizations. Moreover, only 16 percent of respondents said their organizations have “immature or nonexistent” CM and remediation programs, major progress from last year, when this stat stood at 37 percent.
CM, designed to reduce cyber-attack risks, improved the security postures of 63 percent of respondents’ organizations. Moreover, only 16 percent of respondents said their organizations have “immature or nonexistent” CM and remediation programs, major progress from last year, when this stat stood at 37 percent.
But the study also found cause for concern. For example, the percentage of respondents conducting at least weekly active vulnerability scans dropped slightly from 38 percent to 37 percent, while only 11 percent said they practice continuous assessment, down from 13 percent in 2015.
Also disappointing was a big drop in the number of respondents who said their CM program improved their ability to accurately detect and remediate malicious events: from 44 percent to 28 percent this year.
In addition, the report found that 22 percent of respondents don’t regularly assess key network devices such as firewalls and routers, and that 56 percent lack measures to protect connected assets during remediation.
What Is Continuous Monitoring and Why Is It Important?
The report author — senior SANS analyst Barbara Filkins, with input from SANS fellow instructor David Hoelzer — cautions against viewing CM as a single, unidimensional activity, saying it involves a variety of tools and processes that organizations need to orchestrate.
Elements including asset and configuration management, host and network inventories and continuous vulnerability scanning “must be integrated and automated all the way down to the remediation workflow,” she wrote.
This, in practice, implies monitoring all systems and activities at all times “for unauthorized changes, vulnerabilities, abnormal operation, needed patches and workarounds.”
If implemented properly and conducted correctly, a CM program gives organizations a clear picture of their exposure to cyber risk, triggering a process of continuous improvements in their efforts to reduce their “attack surface” and improve overall security.
For U.S. federal government agencies, CM carries even more weight, as it’s an important compliance component of the Federal Information Security Management Act (FISMA) regulation.
What’s Involved in CM?
To do CM properly, organizations need to implement a number of processes outlined in the CIS Critical Security Controls 6.0, including:
- run automated vulnerability scanning tools against all network systems at least once a week
- correlate attack detection events with earlier vulnerability scan results
- perform vulnerability scanning in authenticated mode
- subscribe to a vulnerability intelligence service
- deploy automated patch management and software update tools
- monitor logs for scanning and admin account activity
- check that remediation was completed by comparing back-to-back scans
- rate vulnerabilities’ risk
Let’s take a closer look at key study findings.
CM Programs Show Positive Signs of Maturity
The study found encouraging improvements among respondents’ ability to identify critical assets and vulnerabilities, with the percentage of organizations at either “mature” or “maturing” levels growing from 62 percent to 82 percent this year.
Another positive development was a clear shift in the business drivers behind CM programs from compliance last year to prevention and detection.
“CM is actually becoming part of organizations’ business survival strategies,” the author wrote.
However, the actual rate of success in achieving the goals behind most of the 11 drivers evaluated remains too low, which indicates organizations may not be reaping the full benefits of their CM programs.
For example, only 38 percent of respondents reported successfully reducing their attack surfaces with CM.
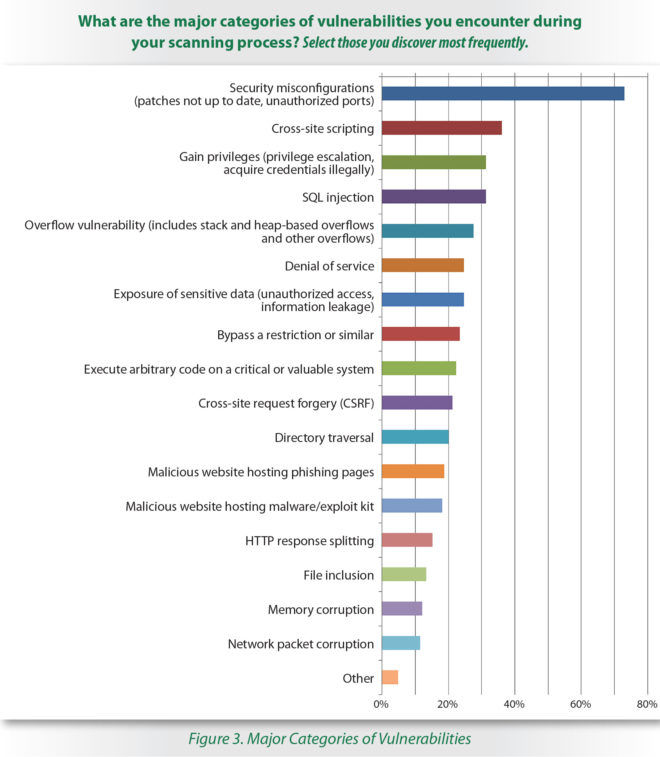
On the flip side, the one driver with a positive success rate — defending assets through patch management — has a direct correlation with the strong awareness among respondents (73 percent) that security misconfigurations pose the greatest threat to their organizations.
“This is a big indicator of program maturity,” reads the report.
Comprehensiveness of CM Programs Still Lagging
In 2015, only 13 percent of respondents had succeeded in corralling all of their critical assets into their assessment programs, a rate that rose a bit to 18 percent this year, but that is still clearly too low.
Moreover, scanning is still not done on a continuous basis, with most organizations performing some level of active scanning, but only 65 percent doing periodic scans, whether on a monthly, weekly or more frequent basis.
The authors were also discouraged by the disconcertingly sharp drop of endpoints and workstations in respondents’ rankings of critical assets: They went from ranking third last year to tenth place this year.
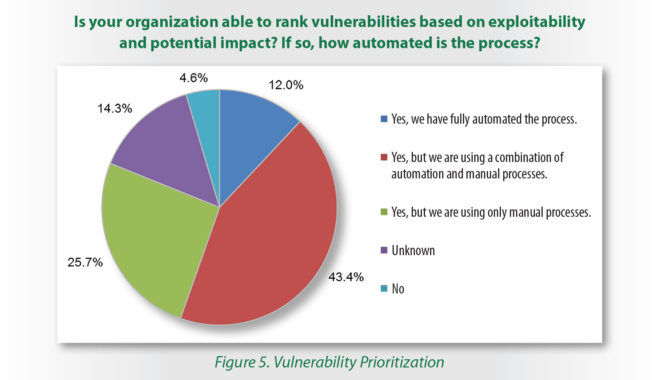
Bright Spots: Prioritization of Vulnerabilities and Remediation Speed
Important components of CM are being able to identify the most critical vulnerabilities in the IT environment and then remediating them promptly.
More than half (55 percent) of respondents said their vulnerability ranking process is either partially automated (43 percent) or fully automated (12 percent).
Meanwhile, almost 62 percent called their remediation process either “very effective” (8 percent) or “effective enough” (54 percent). Time to remediate improved, with 68 percent of respondents this year able to repair, patch or mitigate critical vulnerabilities in under a month, up from 54 percent in 2015.
When it comes to remediation, sooner is always better, with the ideal being to fix vulnerabilities in one day, because risk reaches moderate levels at the one-week mark and becomes high when a vulnerability remains in a critical system for a month or longer.
An area of concern here is that a small percentage (less than 6 percent) of respondents was able to remediate all critical vulnerabilities in their IT environments.
Learn more about prioritizing and remediating vulnerabilities.
Building an Effective Program Doesn’t Have to Break the Bank
The author closes the study outlining a number of best practices for launching or improving CM programs. SANS recommends that the first area to look at for improving a CM program is asset and inventory management, which involves identifying critical assets, determining, testing and documenting their baseline security configurations, and then monitoring and remediating.
Once that’s been addressed, organizations should move on to assessing their CM capabilities, including sharpening existing processes and evaluating current tools. Finally, they can assess the effectiveness of their CM program by benchmarking it against industry metrics.
If this sounds daunting, it needn’t be, according to the author, who states that organizations probably already have a lot of the necessary skills and tools for CM available in house, namely:
- Organizations may already have in place many of the processes associated with a CM program, and they just need to identify gaps and bring them all together.
- Likewise, organizations likely own many of the tools required for CM, even if they need to be tweaked or re-configured.
For whatever additional budget, staff and resources are needed, it’s critical to get a commitment from management for the CM program. Consequently, the CM program should have a clearly-defined scope and a dedicated program manager, as well as specific metrics to demonstrate progress and achievements.
These reports “allow management to assess the effectiveness of the CM on the security posture of the organization, as well as to validate their return on the investment,” the author wrote.
The survey, which was conducted between July and September and sponsored by a number of vendors, including Qualys, polled respondents representing organizations of all sizes and from most major vertical industries.