Virtual Patching: A Lifesaver for Web App Security
Here’s a common scenario organizations increasingly face: Too many web apps with too many vulnerabilities and no chance for immediate remediation.
In the interim, the organization is left exposed to potentially devastating breaches, at a time when web apps have become one of cyber attackers’ favorite targets.
How did we get here?
For starters, many organizations have caught web app fever, so it’s common for a business to be using hundreds or even thousands of apps.
Why? Whether they’re accessed via desktop browsers, mobile devices or IoT systems, these apps streamline, speed up and automate business functions for employees, partners and customers.
However, as they eagerly “appify” their businesses, many organizations aren’t properly checking how secure these apps are.
Vulnerabilities abound in web apps, whether they were custom built in-house, purchased by the organization from a vendor or acquired for free — and without authorization — by employees.
In addition to having a multitude of web apps riddled with bugs, organizations often have multiple teams using a variety of tools to manage security, which complicates matters.
Throw into the mix the fact that hackers in recent years have been relentlessly attacking these highly exposed, often insecure internet-facing apps.
Cyber criminals know web apps connect with back-end systems, offering them a conduit to valuable business data, such as intellectual property and customer information.
In its 2016 Data Breach Investigation Report, Verizon found that, among all attack patterns, web app attacks are most likely to trigger a data breach, and that 95 percent of web app breaches were financially motivated.
Meanwhile, the cost of data breaches to organizations has spiked almost 30% since 2013 to $4 million per incident on average globally, and to $7 million specifically in the U.S., according to a Ponemon Institute study.
What to do? Visibility first
First and foremost, organizations need a full, continuously updated inventory of their web apps, and must scan them for coding mistakes, configuration errors, source code weaknesses, policy non-compliance and other blunders.
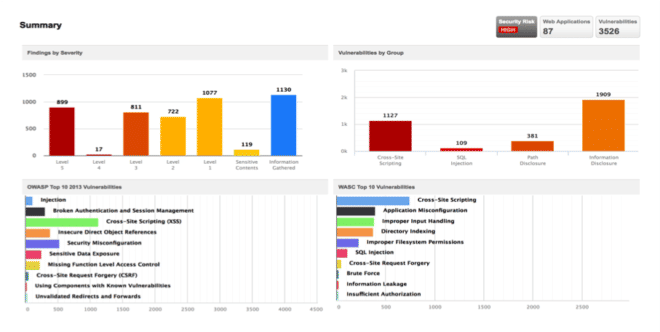
This will give the organization comprehensive visibility of its web apps — approved or unapproved, and commercial or custom built — and of their security flaws.
As a result, at any given point the InfoSec team will have a full plate of critical web app vulnerabilities that should be fixed as soon as possible.
But patching and mitigating web app vulnerabilities often takes a lot of time and effort, for several reasons, including:
- A vendor patch may be unavailable for a long time after a vulnerability is disclosed
- The application may be complicated and expensive to fix
- There may be no hope for a patch, in particular if the app is no longer supported by its vendor
- Patching the app may require a significant amount of testing and QA before deployment
- It may be necessary to take some systems offline as part of the process
- The patch management team may be understaffed and overwhelmed with work
In its “2016 State of Application Security” report, SANS Institute found that many organizations are unhappy with their application patching and repair process.
“Less than 30% are achieving a 75%–99% level of satisfaction with the speed it takes to repair their vulnerabilities,” reads the report, referring to its survey of InfoSec pros from organizations of all sizes and from all major industries.
So how can an organization protect itself during that span of time between the detection of a bug and its remediation, which sometimes can amount to months?
Virtual Patching to the Rescue
Fortunately, organizations have an excellent option for protecting themselves from attacks against a vulnerable web app whose patch hasn’t yet been applied: Virtual patching.
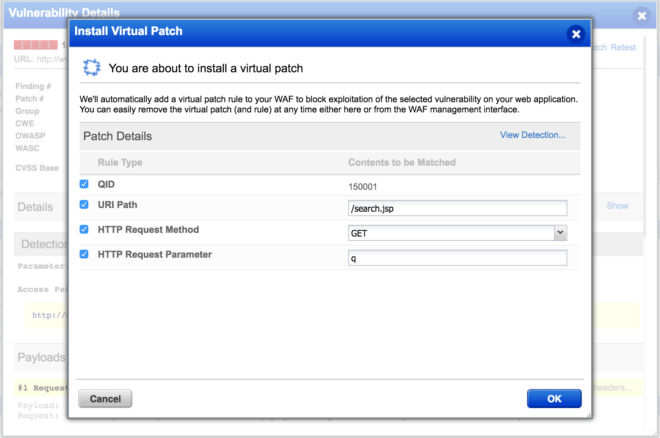
The Open Web Application Security Project (OWASP) defines virtual patching as a “security policy enforcement layer which prevents the exploitation of a known vulnerability.”
The virtual patch’s enforcement layer analyzes transactions and intercepts attacks, preventing malicious traffic from reaching the vulnerable web app.
“The resulting impact of virtual patch is that, while the actual source code of the application itself has not been modified, the exploitation attempt does not succeed,” according to OWASP’s Virtual Patching Best Practices document.
These are some of the benefits of virtual patching OWASP lists:
- As a scalable solution implemented in a few locations, it’s more convenient than installing patches on all hosts.
- It reduces risk until a vendor-supplied patch is released or until a patch is tested and applied.
- It cuts the likelihood of introducing conflicts because libraries and support code files are not changed.
- It protects critical systems that can’t be taken offline.
- It lets organizations to maintain normal patching cycles.
“In today’s dynamically changing environments, the traditional patch cycle for many organizations simply cannot scale and keep pace with the level and frequency of attacks and vulnerabilities being discovered and exploited today,” SANS Institute wrote a few years ago in its report “Reducing Organizational Risk Through Virtual Patching.”
“Through the use of Virtual Patching, organizations can help reduce web application vulnerabilities across the board and scale responses and coverage accordingly with appropriate defenses that can be put in place within minutes or hours,” reads the report.
Qualys’ Solution: Tight Web App Scanner / Firewall Integration
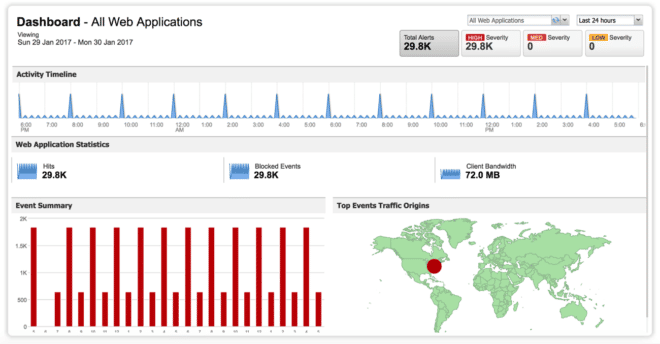
One-click virtual patching is available today with the recently released new versions of Qualys’ Web Application Scanning (WAS) and Web Application Firewall (WAF) cloud-hosted products.
Customers use WAS 5.0 to discover and inventory all their web apps and to identify critical web app vulnerabilities, which they can protect from targeted attacks by deploying virtual patches with one click in WAF 2.0.
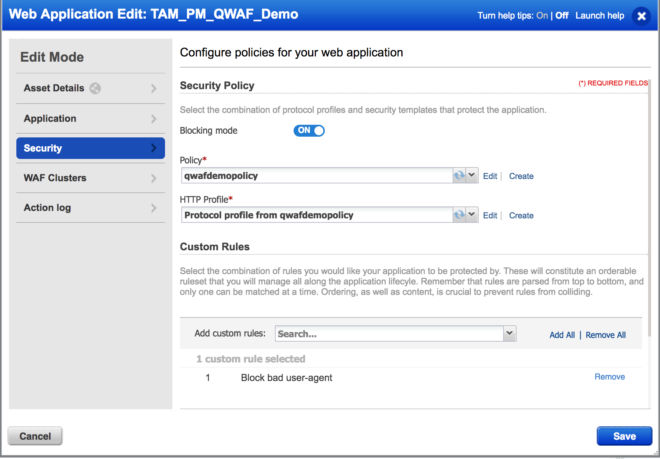
WAF 2.0’s security settings are highly customizable, allowing InfoSec teams to address specific security requirements of their website and to virtually patch certain zero-day vulnerabilities. WAF 2.0’s flexible custom rules let you use various attributes of HTTP requests, clients, servers and transactions to detect attacks.
In addition, the tightly integrated WAF 2.0 and WAS 5.0 can be managed from Qualys’ centralized, self-updating cloud platform.
All these elements give security professionals a complete end-to-end, cloud-based, solution for mitigating web application vulnerabilities that is easy to deploy and highly scalable.
- WAS 5.0 crawls and tests custom web applications to identify vulnerabilities, while its extensive APIs let you integrate scan data with other security systems.
- WAF 2.0 performs real-time inspection of website traffic and blocks attacks on web server and application vulnerabilities, and lets you control where and when your applications are accessed.
- Malware Detection (MD), available with WAS or as a standalone solution, proactively scans your websites for infections, triggers alerts and generates detailed reports.
As part of the integrated security and compliance Qualys Cloud Platform, these three apps are hosted and maintained by Qualys, can be immediately deployed, operate continuously, scale globally and offer users centralized management.
To learn more about patching web app vulnerabilities with one click, watch our on-demand webcast.