Achieve Continuous Security and Compliance with the CIS Critical Security Controls
For InfoSec pros, it’s easy to get overwhelmed by the constant noise from cybersecurity industry players — vendors, research firms, consultants, industry groups, government regulators and media outlets. A good antidote for this hyperactive chatter is to refocus on foundational InfoSec practices. That’s what SANS Institute Senior Analyst John Pescatore and I will do this week: An immersion into the Center for Internet Security’s Critical Security Controls (CSCs).
During an hour-long webcast on Sept. 28, we’ll be discussing the benefits of implementing these 20 recommended controls. Initially published in 2008, these information security best practices have been endorsed by many leading organizations and successfully adopted by thousands of InfoSec teams over the years. Now on version 6.1, the CIS CSCs map effectively to most security control frameworks, as well as regulatory and industry mandates, and are more relevant and useful than ever.
Critical Security Controls Provide Clear Direction for Improving Security Posture
Today, many CISOs and IT leaders find themselves grappling with the growing complexity of their increasingly hybrid and distributed IT environments, and with ever more sophisticated and aggressive cyber attacks.
Fortunately, the CIS CSCs provide clarity and direction by shining a light on fundamental steps that organizations can take to bolster their security posture. As described by CIS, the CSCs are a set of “high-priority, highly effective actions” that offer “specific and actionable ways to thwart the most pervasive attacks” and that provide a starting point for cyber defense improvement using a “must do, do first” approach.
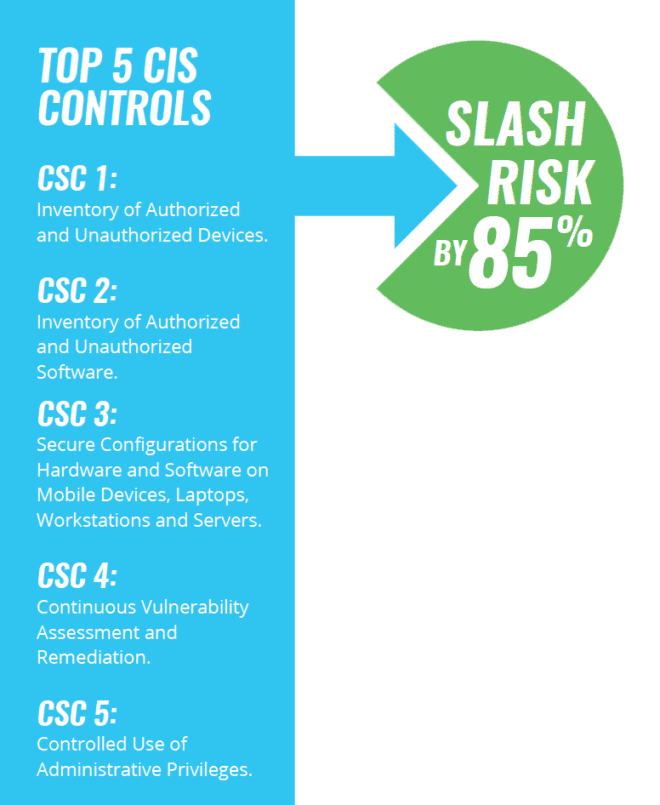 In fact, CIS states that organizations can shrink their cyber attack risk by an impressive 85% if they just apply the first five controls, which provide what the organization calls “foundational cyber hygiene.” These include such essentials as having a full, continuously updated and detailed inventory of all your IT assets — hardware and software — and conducting continuous vulnerability assessments and remediation.
In fact, CIS states that organizations can shrink their cyber attack risk by an impressive 85% if they just apply the first five controls, which provide what the organization calls “foundational cyber hygiene.” These include such essentials as having a full, continuously updated and detailed inventory of all your IT assets — hardware and software — and conducting continuous vulnerability assessments and remediation.
“In terms of building a house, if the foundation is not properly structured, the integrity of everything built on top of it is compromised,” SANS Institute states in its paper “Leading Effective Cybersecurity with the Critical Security Controls.” “Extending this concept to cybersecurity, if an advanced security solution is architected on top of a flawed security foundation, the solution has an extremely high risk of its integrity being compromised.”
These 20 battle-tested controls, described in a free document that has been downloaded more than 70,000 times, were developed and are maintained by a global team of expert volunteers from all cybersecurity sectors, including government, industry and academia.
The CSCs were used as part of the U.S. National Institute of Standards and Technology (NIST) process for drafting its Framework for Improving Critical Infrastructure Cybersecurity, and have been recommended and adopted by many other organizations including the European Telecommunications Standards Institute (ETSI) , the U.S. National Governors Association (NGA) and the U.K.’s Centre for the Protection of National Infrastructure (CPNI).
Webcast: Automating CIS Critical Security Controls for Threat Remediation and Enhanced Compliance
If you feel there are opportunities for your organization to solidify its cyber defense foundations, but you’re not sure where or how to start, join John and me for our webcast “Automating CIS Critical Security Controls for Threat Remediation and Enhanced Compliance.” We’ll talk candidly and in-depth about this set of structured and prioritized InfoSec best practices.
Specifically, we’ll provide an overview of the CSCs, discuss successful, real-world implementations and talk about recent attacks that leveraged misconfigured systems. We’ll also explain how to prioritize remediation, describe how you can leverage Qualys solutions to broadly and comprehensively adopt all 20 controls, and take questions from you and other participants.
(Tim White is a Director of Product Management at Qualys)