The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization
It’s a well-known fact that most successful cyber attacks are easily preventable. That’s because the majority are neither highly sophisticated nor carefully customized.
Instead, they are of the “spray and pray” sort. They try to exploit known vulnerabilities for which patches are available, or to take advantage of weak configuration settings that IT departments could have handily and quickly hardened.
One recent and infamous example was the WannaCry ransomware, which infected 300,000-plus systems and disrupted critical operations globally in May. It spread using the EternalBlue exploit for a Windows vulnerability Microsoft had patched in March.
So why do many businesses, non-profit organizations and government agencies — including those with substantial cybersecurity resources and knowledge — continue falling prey to these largely unrefined and easy to deflect strikes?
In most cases, the main reason can be traced back to hygiene — of the cybersecurity type, of course. Just as personal hygiene practices reduce the risk of getting sick, applying cybersecurity hygiene principles goes a long way towards preventing security incidents.
That was the key message Qualys Product Management Director Tim White and SANS Institute Analyst John Pescatore delivered during the recent webcast “Automating CIS Critical Security Controls for Threat Remediation and Enhanced Compliance.”
Going back to cybersecurity basics
When high-profile hacks such as Equifax’s make headlines, InfoSec teams, top executives and boards huddle and wonder if they’re ready to deflect such an attack. “Very often that first step points to basic security hygiene,” Pescatore said.
White said he spends a lot of time with customers trying to help them understand what’s holding them back from implementing basic security hygiene practices in their organizations. “Why do we not do these things? It seems pretty self explanatory,” he said.
Unfortunately, achieving cybersecurity sanitation isn’t always easy, according to White. One key reason: Digital transformation is quickly and drastically changing IT environments, making them more complex to defend.
“It’s challenging to know the technical depth of all the systems in your environment,” White said.
Fortunately, there is a tried and true set of practices that, since its first release in 2008, has given thousands of organizations a solid cybersecurity foundation: The Center for Internet Security’s Critical Security Controls.
During the hour-long webcast, White and Pescatore drill down into these 20 cybersecurity practices, explain why they work effectively and outline how they can implemented.
They pay particular attention to the first five controls, whose adoption, according to the CIS, can reduce the risk of cyber attack by an eye-popping 85%:
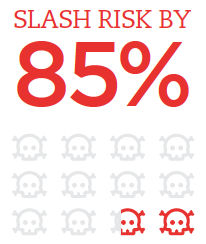
- Inventory of Authorized and Unauthorized Devices
- Inventory of Authorized and Unauthorized Software
- Secure Configurations for Hardware and Software
- Continuous Vulnerability Assessment and Remediation
- Controlled Use of Administrative Privileges
“When you look at enterprises who know what’s on their network from a hardware and software point of view, who know what vulnerabilities exist, who take steps to make sure they’re managing configurations and limiting privileges, they’re the ones that usually don’t show up in the news for having a major security incident,” Pescatore said.
The CSCs, developed and periodically updated by leading security experts, have been endorsed by many leading organizations and successfully adopted by thousands of InfoSec teams over the years. Now on version 6.1, the CSCs map effectively to most security control frameworks, as well as regulatory and industry mandates.
As described by the non-profit CIS, the CSCs are a set of “high-priority, highly effective actions” that offer “specific and actionable ways to thwart the most pervasive attacks” and that provide a starting point for cyber defense improvement using a “must do, do first” approach.
With the CSCs in place, organizations can prioritize and deal with “the most important things, which are the ones that stop real world attacks,” Pescatore said. “That’s what the Critical Security Controls have been aimed at” since they were first developed.
Over the years, Pescatore has seen time and again that what makes the difference is having strong security processes, InfoSec teams and CISOs that focus first and foremost on fixing the issues that enable attacks against critical assets.
Mapping Qualys to the CSCs
During the webcast, White explains how several Qualys security and compliance apps can help organizations adopt the CSCs. A companion guide goes into in-depth detail, mapping the controls and sub-controls directly to specific features in Qualys apps.
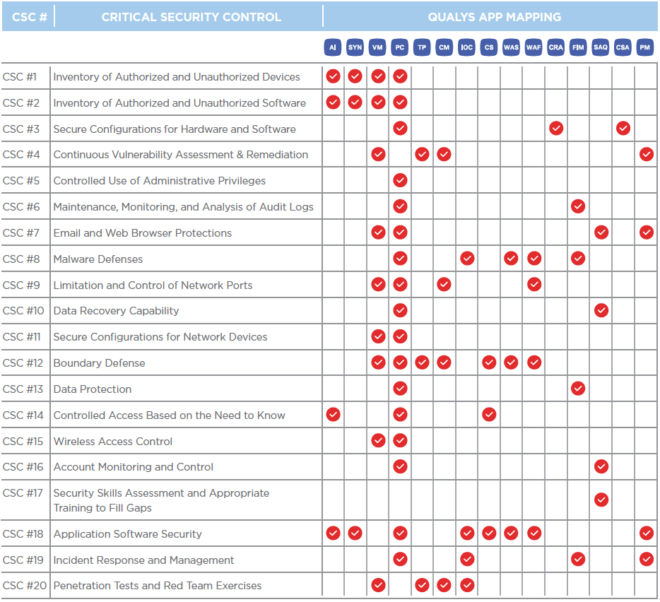
In particular, White focuses on Qualys Policy Compliance (PC), which is especially relevant to the CSCs because 17 of the 20 controls have configuration assessment components. In this respect, Qualys PC can help organizations demonstrate continuous risk reduction and compliance with internal policies and external regulations, fix violations and configuration drift, centrally manage exceptions, and document progress.
Qualys PC, along with all the other Qualys apps that can help you implement the CSCs, such as Qualys Asset Inventory (AI), Qualys Vulnerability Management (VM), Qualys Web Application Scanning (WAS), and Qualys Indication of Compromise (IOC), are all powered by the highly-scalable and centralized Qualys Cloud Platform.
The Qualys Cloud Platform gives organizations a continuous, always-on assessment of their global security and compliance posture, with instant visibility across all IT assets, wherever they reside.
“Using an automated approach for finding out what your weaknesses are, and then pushing remediation of those in a prioritized manner, helps improve overall security,” White said.
So take a listen to the webcast and download our guide, and see how these 20 battle-tested controls, whose freely available document has been downloaded more than 70,000 times, can help you sanitize your security and compliance posture, and strengthen your cyber defenses.