Meltdown / Spectre: New Concerns Over Intel Patches, as Hackers Test Exploits
This week brought new developments in the Meltdown / Spectre saga, including more concerns about Intel’s buggy patches, and mounting evidence that hackers are trying to create exploits for the vulnerabilities.

It seemed that after weeks of complaints and confusion, Intel’s issue had hit bottom and was headed for a resolution on Monday of last week. That’s when the company said its firmware updates for Broadwell and Haswell CPUs shouldn’t be installed anymore, because, as many customers had reported, they made systems behave erratically, including unexpectedly rebooting.
At the time, Intel said it had discovered the “root cause” for the firmware’s problems, and was already actively developing new updates. However, another shoe was about to drop. Three days later Intel acknowledged in its quarterly earnings report that the glitchy firmware can also cause “data loss or corruption.”
This disclosure prompted Microsoft to take the unusual step of releasing an emergency Windows update designed to disable Intel’s fix for one of the two Spectre variants. Microsoft’s “out-of-band” update — KB4078130 — targets Intel’s patch for CVE-2017-5715, Spectre’s branch target injection vulnerability.
“In our testing, this update has been found to prevent the described behavior in devices that have affected microcode,” reads Microsoft’s accompanying support article.
Microsoft also independently confirmed Intel’s latest findings. “Our own experience is that system instability can in some circumstances cause data loss or corruption.”
Meanwhile, although there have been no widespread attacks against these vulnerabilities since their disclosure on Jan. 3rd, there are signs that the bad guys are actively working on exploits. AV-Test, an antivirus testing vendor, said this week the number of samples it has collected that “appear to be related” to exploits for Spectre and Meltdown continues to rise, reaching 139 as of Thursday.
AV-Test’s CEO Andreas Marx told ZDNet he can’t confirm that all samples successfully exploit the vulnerabilities. “Due to the extremely high number of affected computers/systems and the complexity to ‘fix’ the Spectre-Meltdown vulnerabilities, I’m sure that the malware writers are just looking for the best ways to extract information from computers and especially browsers,” he said.
Fortinet chimed in, saying on its blog that it has analyzed all publicly available samples — about 83% percent of all samples collected — and determined that “they were all based on proof of concept code” released by the researchers that discovered the vulnerabilities.
Avast has reached the same conclusion. “Avast has been actively seeking samples and we have received samples from AV-Test, but, so far, they seem to just be variations of the proof of concept code,” Michal Salat, Threat Intelligence Director at Avast, told eWEEK.
Salat also put the sample discoveries in a larger context, saying that the current amount — 139 — “is very little if we consider that we at Avast see tens of thousands of new malicious files per day.”
As we approach the one-month mark of the Spectre and Meltdown disclosures, it’s clear that mitigating these widespread hardware flaws remains complex both for tech vendors and for their customers. Read on to learn all the ways in which Qualys can help you with this issue.
Qualys insights and recommendations
Qualys has been on top of the Meltdown / Spectre issue from the very start, dispensing advice and insight publicly via blog posts, media comments and webcasts, as the industry scrambles to deal with vulnerabilities that affect most Intel CPUs released in the past 20 years, as well as a smaller quantity of ARM and AMD CPUs.
Meltdown (CVE-2017-5754) provides access to all physical memory, including kernel memory, via a user mode, ring 3 process, so that “any process running in the system can access all the contents of physical memory,” Qualys Product Management Director Jimmy Graham said recently during a webcast.
Attackers could steal passwords, grab private keys and do whatever necessary to escalate their system privileges to administrator levels. “Anything that can be stored in memory can be accessed through Meltdown,” Graham said.
Meanwhile, Spectre (CVE-2017-5753, CVE-2017-5715) impacts Intel, AMD, and ARM CPUs by abusing branch prediction and speculative execution, resulting in data leakage from compromised processes. “An attacker process on a system can access the memory contents of other process, and can include kernel memory in some circumstances,” Graham said.
Graham offered the following recommendations for managing the Spectre and Meltdown mitigation process.
- Detect vulnerable assets using Qualys Vulnerability Management authenticated scans or with Qualys Cloud Agents. It’s crucial to have a clear idea of how many impacted systems are in your environment, which vulnerabilities you have, and which patches have been applied.
- Prioritize patching efforts based on asset risk and exposure. If you can’t install the microcode patches because they’re problematic or non-existent at this point, focus on the OS and browser patches. “For workstation type devices, I’d focus on patching the underlying OS, because performance concerns are not as great, compared to servers, and patch the browsers as well to start enabling some of these mitigations,” Graham said.
- Test and test again. “Everything needs to be tested. These patches are not simple software patches that we’ve seen previously. These are fundamental changes to how the kernel is treated in Linux and in Windows,” he said.
- Tests should go beyond simply verifying that updates and patches they’ve been successfully installed. You must test workloads on servers. “You don’t want to be blindly installing these patches on very critical database systems without testing them with some kind of load,” Graham said.
- Make sure third-party antivirus software is up to date.
- Install browser patches for workstation type-devices.
- Patch virtual systems such as Xen and VMWare.
- Patch Windows workstations and servers with the most recent January patches.
Qualys now has more than 75 QIDs to determine the patch state for Spectre and Meltdown. Qualys provides both agentless scanning and agent-based detections, so you can use the most appropriate method for any given IT asset.
In addition, Qualys recently rolled out a pre-built Spectre/Meltdown Dashboard to give you visibility into the remediation progress. It can be downloaded from the Qualys Community site.
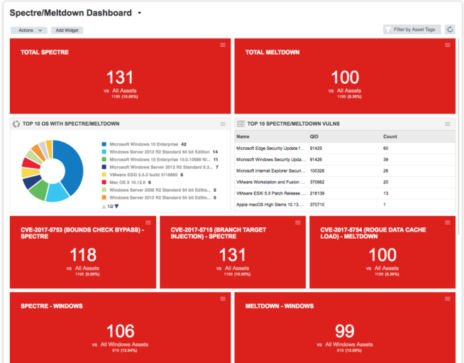
You can also find detailed and illustrated instructions on how to create Qualys Search Lists, Scan Option Profiles, Remediation Tracking and Patch Reports for Spectre and Meltdown in this article published to our community site by Debra M. Fezza Reed, Qualys’ Product Manager for Reporting.
Graham’s webcast also includes a demo of the new Spectre/Meltdown dashboard, and his answers to questions from the audience.
Spectre / Meltdown Resources
- How to Inventory Systems and Track Patching Progress
- January 17 Webcast Recording and Summary
- Visualizing Impact and Remediation Progress with AssetView
- Configure Spectre/Meltdown Dashboards in AssetView
- List of QIDs for Meltdown & Spectre
- Spectre/Meltdown Search Lists, Scan Option Profile, Remediation Tracking and Patch Reports
- Protecting the Qualys Cloud Platform
- Meltdown/Spectre: Intel Nixes Patches, Tech CEOs Questioned on Information Blackout
Hopefully Intel is working on hardware solution of this flaw. Obvious solution is adding fully electrically isolated device ( or chip sector) that performs scheduled encryption for all sensitive information, (that does not used for computation ), then decryption is done only when request is longer then access time of meltdown.. Such solution will help not only for Meltdown, but also for any attempt to get password without touching keyboard.