If You Think File Integrity Monitoring is Boring, Think Again
Table of Contents
You’ll be hard pressed to find file integrity monitoring on any list of cool, emerging, cutting-edge cybersecurity technologies. But if you choose to ignore this mature, foundational technology, it’ll be at great risk.
File integrity monitoring, or FIM, plays a key role in critical security and compliance scenarios. An effective FIM system can help you to promptly detect a variety of changes stemming from normal IT activity, compliance and change control violations, or malicious acts such as ransomware/malware attacks and configuration tampering. FIM can be your last line of detection for complex and evasive rootkits or mobile code. It is also invaluable in making sure validated scripts and configurations are not changed by insiders, malicious or not.
In this blog series, we’ll address the major uses for FIM, starting with regulatory compliance, and specifically the PCI DSS (Payment Card Industry Data Security Standard) mandate.
While FIM is an implicitly required control in many regulations for ensuring information integrity, it is explicitly mentioned in PCI DSS for any system handling personally identifiable information. The best practices and insights from those monitoring systems with FIM for PCI compliance are just as applicable to other regulations and mandates, such as HIPAA, GDPR and Sarbanes-Oxley.
FIM basics
FIM products monitor files of any type for change, to ensure they haven’t been altered when they shouldn’t be. They bring changes to the attention of someone on your infosec team, so that policy violations, security and compliance issues can be identified quickly.
Almost always, a change is normal, and usually related to patching or configuration updates, especially with rapid rollouts and highly automated processes. Sometimes, the cause of such changes can be unintended, such as configuration modification by IT automation systems, or employee error. Rarely, but most worrisome, are changes that are malicious, such as hacker attacks and malware infections.
Faster detection can help IT recover more quickly from downtime caused by a change, regardless of the intent of the person making the changes, and significantly reduces the time that a malicious attack could go unnoticed.
In short, FIM systems watch your IT assets and bring to your attention evidence that a change to file contents or file metadata occurred, and help you identify the breadth and depth of the incident.
PCI DSS
Now in version 3.2 and managed by the PCI Security Standards Council, PCI DSS (Payment Card Industry Data Security Standard) is an industry mandate for protecting payment cardholder information from security breaches.

PCI DSS is part of the technical requirements for the data security compliance programs of the Council’s founding members: American Express, Discover Financial Services, JCB International, MasterCard and Visa.
In PCI DSS, FIM is mentioned in requirements 10 and 11, which we’ll summarize below and then discuss in the context of best practices and Qualys capabilities in the next section of this blog post.
Requirement 10, titled “Track and monitor all access to network resources and cardholder data,” stipulates that FIM or change-detection software must be used on logs to ensure that “existing log data cannot be changed without generating alerts” while allowing new data to be added.
The PCI DSS mandate goes on to say that “for file integrity monitoring purposes, an entity usually monitors files that don’t regularly change, but when changed indicate a possible compromise.”
Requirement 11, titled “Regularly test security systems and processes,” states that organizations should deploy a change-detection mechanism, such as FIM tools, “to alert personnel to unauthorized modification (including changes, additions, and deletions) of critical system files, configuration files, or content files.” The FIM software should also be configured to perform critical file comparisons at least weekly.
PCI DSS says files that should be monitored include:
- System executables
- Application executables
- Configuration and parameter files
- Centrally stored, historical or archived, log and audit files
- Additional critical files determined by entity (for example, through risk assessment or other means)
Unauthorized and undetected file changes “could render existing security controls ineffective and/or result in cardholder data being stolen with no perceptible impact to normal processing.”
How Qualys can help
The highly scalable Qualys File Integrity Monitoring (FIM) Cloud App lets you centrally manage real-time change detection for global IT environments, including those involved with processing payment card transactions and thus in scope for PCI DSS compliance.
Specifically, Qualys FIM comes with pre-built monitoring profiles for PCI DSS to help organizations decide which files to monitor on systems that process PCI related data.
As PCI DSS requires, Qualys FIM identifies changes to file contents, directory structures, and file system metadata such as file permissions, across global IT systems, giving organizations centralized cloud-based visibility of file change activity. Qualys FIM does this with real-time detection locally, and with minimal impact to the monitored host.
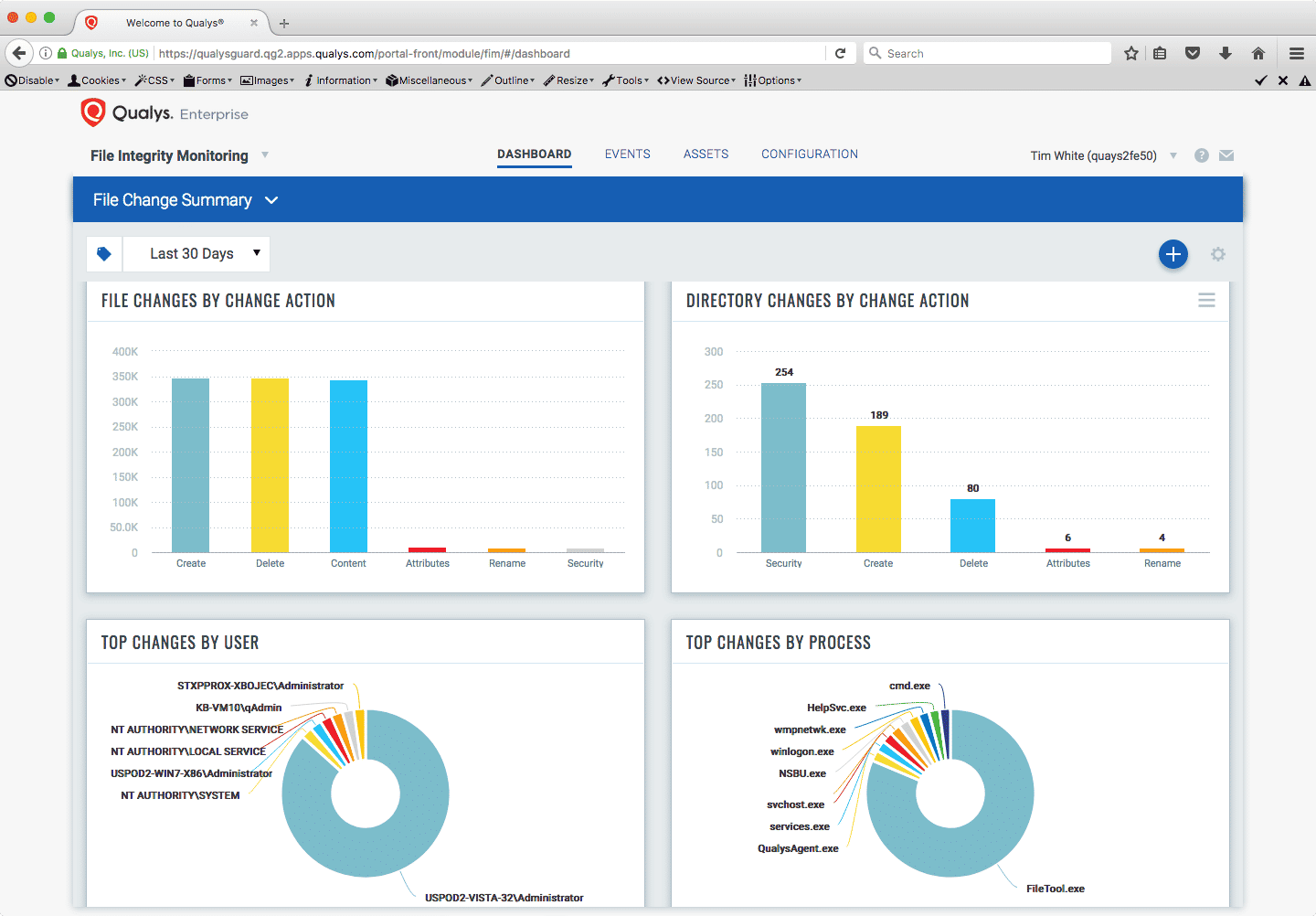
The Qualys Cloud Agent continuously monitors the files and directories specified in the monitoring profile and captures critical data to identify what changed along with environment details such as which user and process was involved. It sends data to the Qualys Cloud Platform for analysis and reporting.
These lightweight agents are remotely deployable, centrally managed, self-updating and consume minimal CPU resources. They can be installed on any host, such as a laptop, desktop, server, or virtual machine — on-premises, mobile, or in the cloud.
In addition, Cloud Agent communication is optimized to support large-scale agent deployments, providing flexible and granular performance configuration controls that allow organizations to fine-tune agent performance and bandwidth usage to meet their specific environmental requirements.
Because Qualys FIM is based on the Qualys Cloud Platform and uses the same Qualys Cloud Agent as other Qualys Cloud Apps, it allows organizations to easily scale easily their FIM efforts across on premises and cloud environments. This also lets organizations benefit from a consolidated security solution to reduce cost and complexity of maintaining multiple point products.
Other key features of Qualys FIM that help with PCI DSS compliance include:
- Scalable, easy to manage architecture: FIM can be instantly activated on existing agents, monitoring for changes locally with minimal impact to the endpoint. The Qualys Cloud Platform allows you to scale to the largest environments, without having to purchase expensive server software, hardware and storage.
- Easy setup and no maintenance: FIM operates on endpoints via the lightweight Qualys Cloud Agent. Modules can be instantly activated across any or all assets without reinstalling the agent or rebooting the endpoint.
- Minimal performance impact: The Cloud Agent minimizes performance impact on the endpoint by simply monitoring for file changes and system activity locally, sending all data to the Qualys Cloud Platform for storage, correlation, analysis, and reporting.
- Automated change review (Upcoming feature): Qualys FIM provides review workflows and points for external integration to reduce the data users have to look at so they can focus on critical changes and violations first.
Try Qualys FIM for free with an unlimited-scope trial of Qualys Cloud Platform.
(Tim White is Director of Product Management for Policy Compliance at Qualys)