The Digital Transformation Age Is Dawning: Do You Know Where Your Certificates Are?
Last updated on: May 14, 2025

How many digital certificates are in use in your organization? When do they expire? Do you have a way of discovering digital certificates from unapproved Certificate Authorities?
Most organizations can’t answer these questions with complete certainty, because they lack the necessary visibility and control over their certificates. This creates the potential for security lapses, since SSL/TLS certificates are critical for the integrity and protection of a host of e-business functions.
With proper certificate management, organizations can cut their risk of breaches and unplanned outages, and continuously and effectively protect their digital assets, Asif Karel, a Qualys Director of Product Management, said recently during a webcast.
Since their creation in the mid-1990s, digital certificates have provided security for Internet traffic. They’re meant to ensure the confidentiality, authenticity, integrity and non-repudiation of online communications in public-facing online services, internal services, machine-to-machine communications, public cloud services and API integrations.
During his webcast, Karel outlined the current challenges organizations face with certificate visibility, and explained how Qualys can help with CertView, a free app available now.
The problems start with limited visibility
Karel polled webcast audience members, asking them whether their organizations have a full inventory of their digital certificates. The results were not surprising.
“It looks like most of you have little to no visibility into certificates, and this is very common. You’re not alone,” Karel said. “Often, certificates and SSL configurations are forgotten or not given enough attention.”
Qualys SSL Labs’ SSL Pulse, which monitors the quality of SSL/TLS support across 150,000 websites, rated about 43% of the sites monitored as having inadequate security in its May report.
Faults included expired (5,500) or soon-to-expire certificates (6,000), weak or insecure cipher suites (5,000), and use of obsolete protocols such as SSLv2 and SSLv3 (20,000), and TLSv1 (120,000).
In mid-May, Comodo, a Certificate Authority based in New Jersey, released a study that revealed that more than 1 million distrusted SSL/TLS certificates from Symantec remain in use.
As is well known, hackers feast on weak certificates and TLS configurations, exploiting them to use encrypted traffic to transmit malware, power botnets, launch man-in-the-middle attacks, communicate with malicious command and control centers, and exfiltrate data, Karel said.
Highlighting the importance of TLS, Google recently announced that with the release of version 70 of its Chrome browser, it’ll start showing a red “not secure” warning when users attempt to access an HTTP page.
However, it’s important to understand that while certificates and TLS offer protection, encrypted traffic can also be a problem, Karel said. Gartner recently predicted that 70% of network attacks against enterprises will hide in encrypted traffic by 2020, he added.
What’s at the root of the problem? Most businesses lack full and continuously updated inventories of their certificates, a faulty foundation that must be addressed as a first priority.
“Most organizations don’t have any visibility into their certificates. They don’t know where they are, how many there are, and what purpose they’re being used for. Certificate ownership information is typically missing for most of these organizations,” he said.
“The unknown is always very difficult to manage, and usually results in unplanned outages. For every unplanned outage caused by an expired certificate, there are usually many more near misses,” Karel added.
As a result, certificates expire taking IT admins by surprise, and causing outages and interruptions of online services and communications. This, in turn, tarnishes the company’s brand, hurts sales and harms customer and partner satisfaction. Even large technology players aren’t immune to this problem. Google, Facebook and LinkedIn have all suffered service interruptions due to expiring certificates.
Another problem is the adoption, often unwittingly, of certificates from unapproved Certificate Authorities, which creates its own set of security and compliance risks. For example, DevOps teams, which release code quickly and continuously, often can’t wait days for the IT department to get them certificates from preferred sources, and instead get them themselves from free services.
“DevOps teams are spearheading this age of digital transformation and they can’t be held back,” Karel said.
Another issue is organizations’ reliance on manual processes for managing certificates, often via the use of spreadsheets, which yields errors and outdated information. With a manual approach, the inventory is limited to the certificates the IT department is aware of, so it will lack unreported certificates that may be in your environment.
In fact, the average Global 5000 company spends $15 million to recover from the loss of business caused by a certificate-related outage, and faces another $25 million in costs related to compliance issues, according to Ponemon Institute.
Downsides of niche products
Existing certificate management products often suffer from a variety of weak spots arising from their design as narrow point solutions. As a result, they work in a vacuum and don’t communicate with other security systems, creating data silos and making it difficult for teams to collaborate and share information.
These products are also hard to scale, requiring multiple deployments to cover large environments, which increases cost of ownership and management complexity.
In addition, these tools are often designed to work either only on premises, or only in cloud environments, but not in both. “In today’s world of digital transformation, the cloud and enterprise networks are tied more than ever, and this segregation approach doesn’t work anymore,” Karel said.
The solution: Automate and centralize your visibility and tracking of global certificate deployments with a tool that works across hybrid IT environments.
Qualys CertView
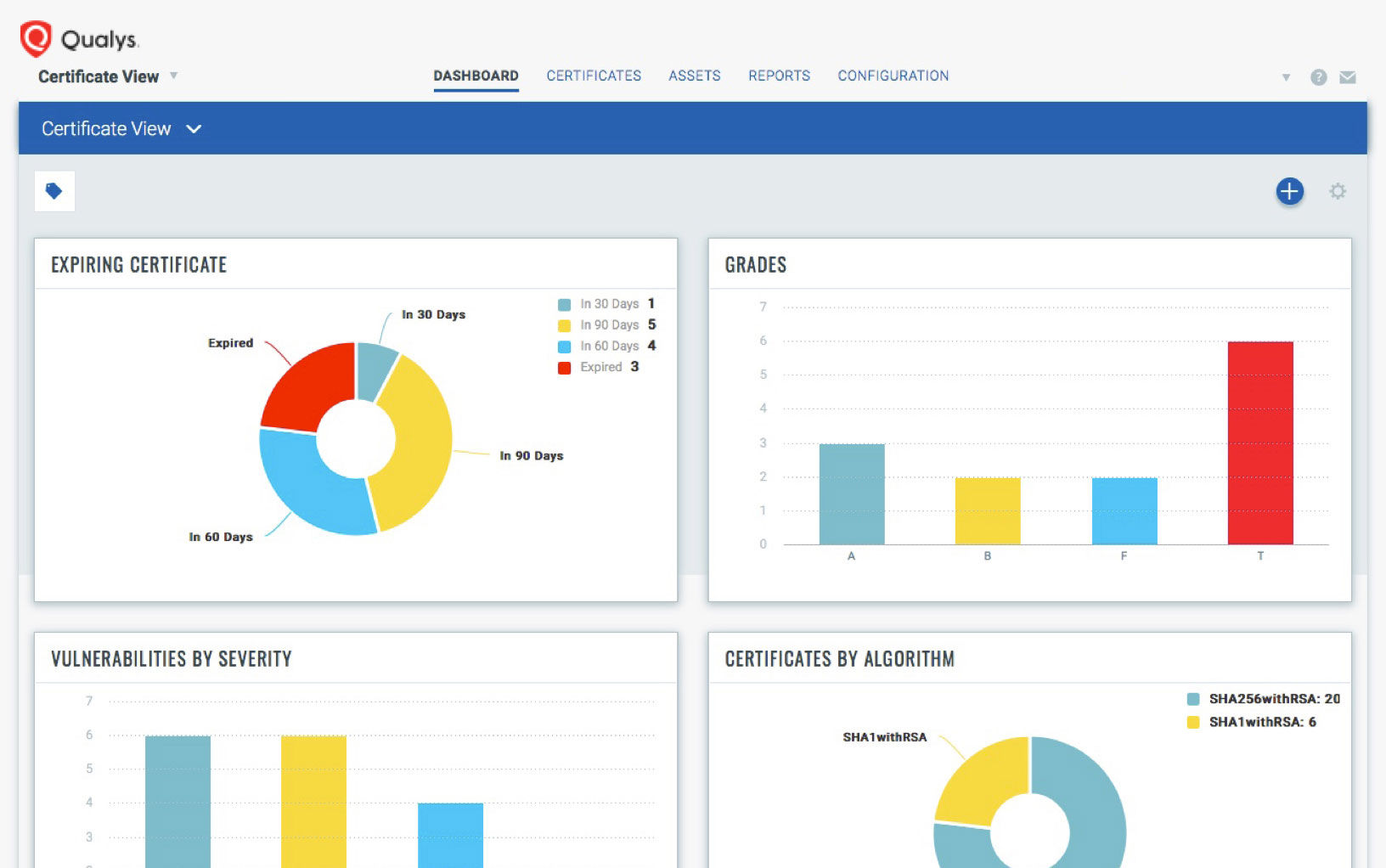
With the free Qualys CertView, organizations can discover, inventory and monitor their Internet-facing digital certificates, along with their host SSL/TLS configurations and vulnerabilities.
They will obtain a graded assessment that takes into account elements such as the host, port, service and certificate of assets both on premises and in cloud environments. “You don’t have to be an SSL/TLS configuration expert,” Karel said.
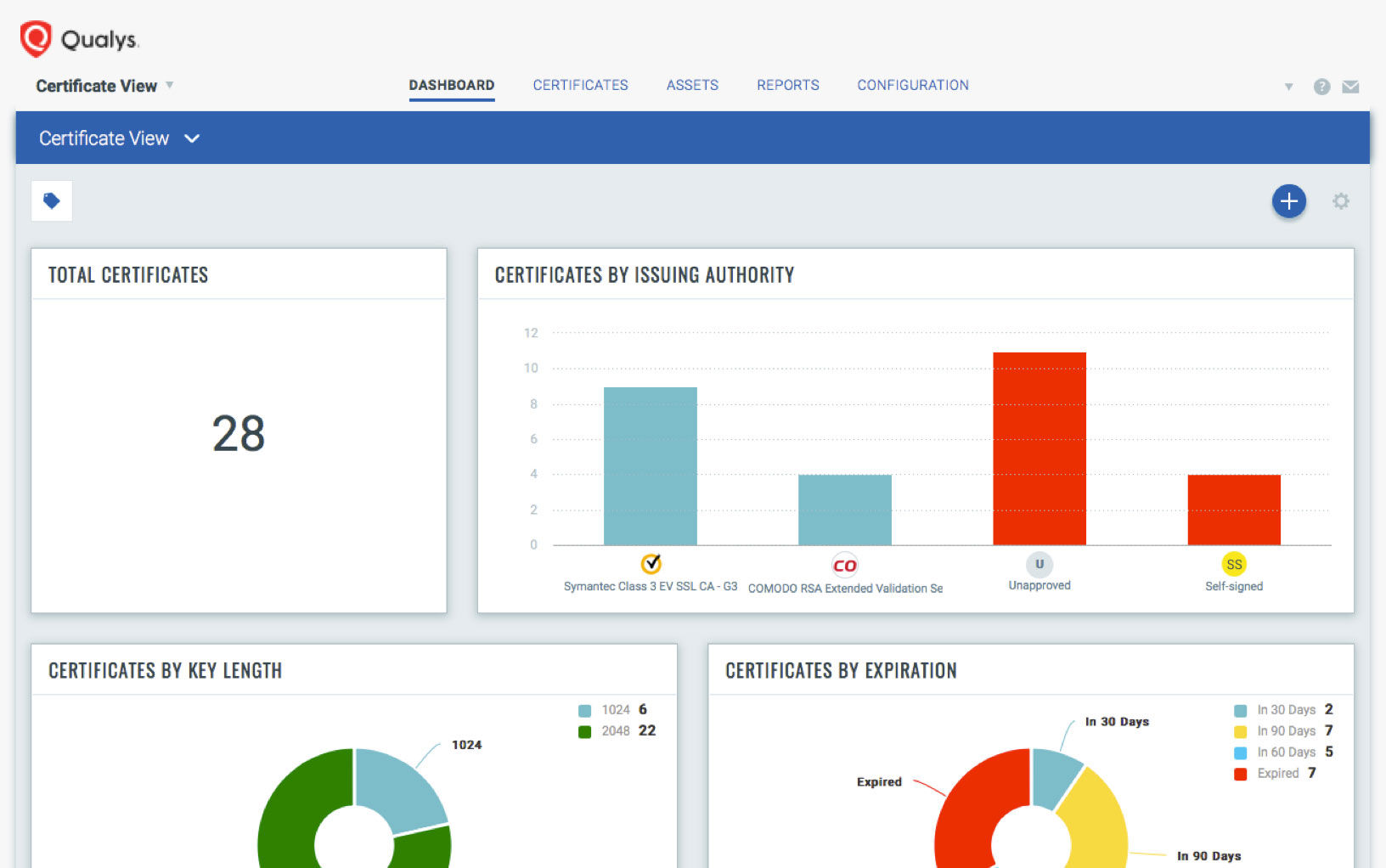
With CertView, organizations can address common use cases such as:
- Preventing downtime and outages caused by expired certificates
- Assessing the strength of SSL/TLS configurations via intuitive certificate grades (A, B, C, D, …) using SSL Labs’ methodology
- Detecting certificate-related anomalies
- Obtaining full certificate visibility via continuous discovery and inventorying, and managing them from a single-pane-of-glass interface with a powerful elastic search engine
- Achieving audit success with automated, downloadable reports
- Carrying out fast, precise remediation
A key advantage of Qualys CertView is that it uses the same Qualys scanners that existing customers have deployed for other Qualys Cloud Apps, such as Qualys Vulnerability Management and Qualys Policy Compliance.
With CertView, you can quickly identify externally-facing certificates that are weak and non-compliant, along with their associated grades, vulnerabilities and assets, and quickly search through this data, getting results in seconds.
Like the other Qualys Cloud Apps, Qualys CertView is a software-as-a-service product that’s built on top of the robust, highly scalable Qualys Cloud Platform, where all data is stored and analyzed.
The Qualys Cloud Platform consolidates a wide variety of security and compliance services for prevention, detection and response, through its self-updating, natively-integrated suite of 18 Cloud Apps. Platform users get a single-pane-of-glass view across their security and compliance posture across their entire IT environment — on premises, in clouds and at endpoints.
We invite you to listen to a recording of the webcast, which has a lot more details about this topic of digital certificate management, a CertView demo and a Q&A session with the audience.
Sign up for Qualys CertView. If you are an existing Qualys customer, you can activate a trial from within the Qualys console. With an upgrade, you can extend inventory and assessment of your Internet-facing certificates to include your internal network where your most critical data resides.