Threat Hunting: Adoption, Expertise Grow, but Work Remains
 Threat hunting, an often misunderstood but powerful security practice, is gaining traction, as more organizations reap benefits from it and get better at it. However, there is still a lot of room for adoption to increase and for practices to improve.
Threat hunting, an often misunderstood but powerful security practice, is gaining traction, as more organizations reap benefits from it and get better at it. However, there is still a lot of room for adoption to increase and for practices to improve.
Those were key findings from the SANS Institute’s 2018 threat hunting study, which experts from SANS, Qualys and other companies discussed recently in the two-part webcast “Threat Hunting Is a Process, Not a Thing.”
“Over the past two to three years, threat hunting has been moving from a ‘What is it?’ discussion into a more formal mentality of: ‘This is what it is. Am I doing it right?’,” said Rob Lee, a SANS instructor. “But we’re still in a transition.”
For starters, there’s still considerable confusion about what threat hunting is. For example, it’s very common for many to equate it with reactive practices such as incident response. Rather, threat hunting is by definition proactive. It assumes that the organization’s prevention defenses have been bypassed, and the IT environment breached, without any alerts being triggered.
Using threat intelligence analysis and other tactics, hunters formulate and act on a hypothesis about where the intruders are likely to be lurking in silence while pursuing their nefarious goals.
Threat hunting basics
SANS defines threat hunting as: A focused and iterative approach to searching out, identifying and understanding adversaries who have entered the defender’s networks. Its hypothetical approach — SANS says — validates data collection, detection, and analysis ahead of an incident.
Organizations can’t start engaging in threat hunting out of the blue, Lee said. Some elements must be in place, namely having:
- A security operations center (SOC) with continuous monitoring and SIEM (security information and event management)
- A dedicated or ad-hoc incident response capability
- Access to cyber threat intelligence, collected in-house or obtained from a third party
- An understanding of the organization’s security baseline, to truly recognize anomalies
One piece of good news from the survey is an increase in awareness from last year of the importance of proactively hunting for intruders that slip in undetected. “We’re starting to see more organizations getting the mindset that the likelihood of intruders out there compromising us is quite high and that they’re already inside our organization,” Lee said.
These stealthy intruders remain invisible on average for 90 to 100 days, so the sooner you find them, the fewer chances they’ll get to do maximum damage.
The study, which polled 600 organizations, found that 43% of respondents do threat hunting continuously, which is ideal, while 17% do it on a regular schedule, which is second best. The rest engage in threat hunting triggered by an event or a hunch (37%) — which is more reactive and thus closer to the incident response — or couldn’t answer (3%).
Study highlights
- The most common trigger for a threat hunt was reactive — “alerts from monitoring tools” — while some proactive triggers barely registered, like “predictions based on previously detected threat indicators.”
- Difficulty in obtaining data varies. Threat hunting teams easily access SIEM alerts, endpoint security data, network IDS/IPS feeds, web proxy logs and open source threat intel. But they obtaining third-party and in-house threat intel, endpoint user activity and forensics, full packet capture, and deception and decoy system data capture.
- Respondents listed investigation functions and skills, and better data searching, as the top threat-hunting areas in need of improvement.
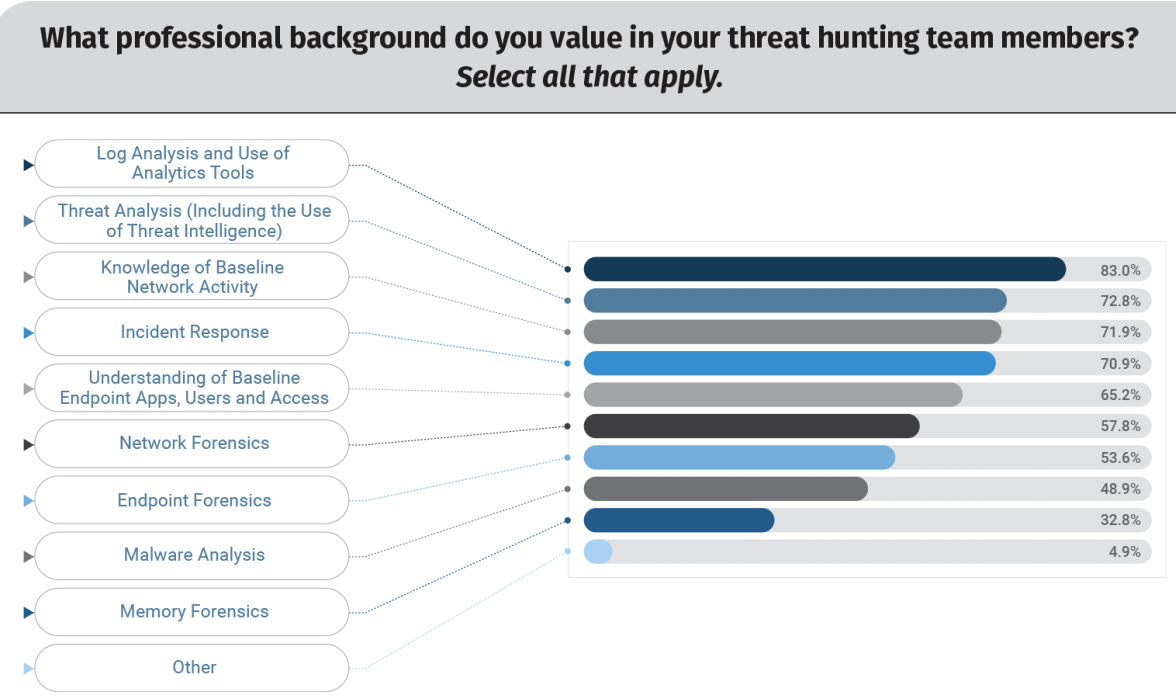
- The threat hunting team should reflect a diversity of skills, including log analysis, threat analysis, malware analysis, forensics versatility and broad baseline security knowledge. Beyond that, it’s key to get the best people available. “Trained staff is key to running threat hunting engagements,” Lee said.
The bottom line
Hunting is starting to show that organizations are using intelligence properly to identify threats instead of solely relying on traditional alerts and alarms. It’s also helping organizations find threats more effectively, and it improves security operations and incident response.
“Threat hunting has these trickle-down effects of improvements across security in your entire organization,” he said.
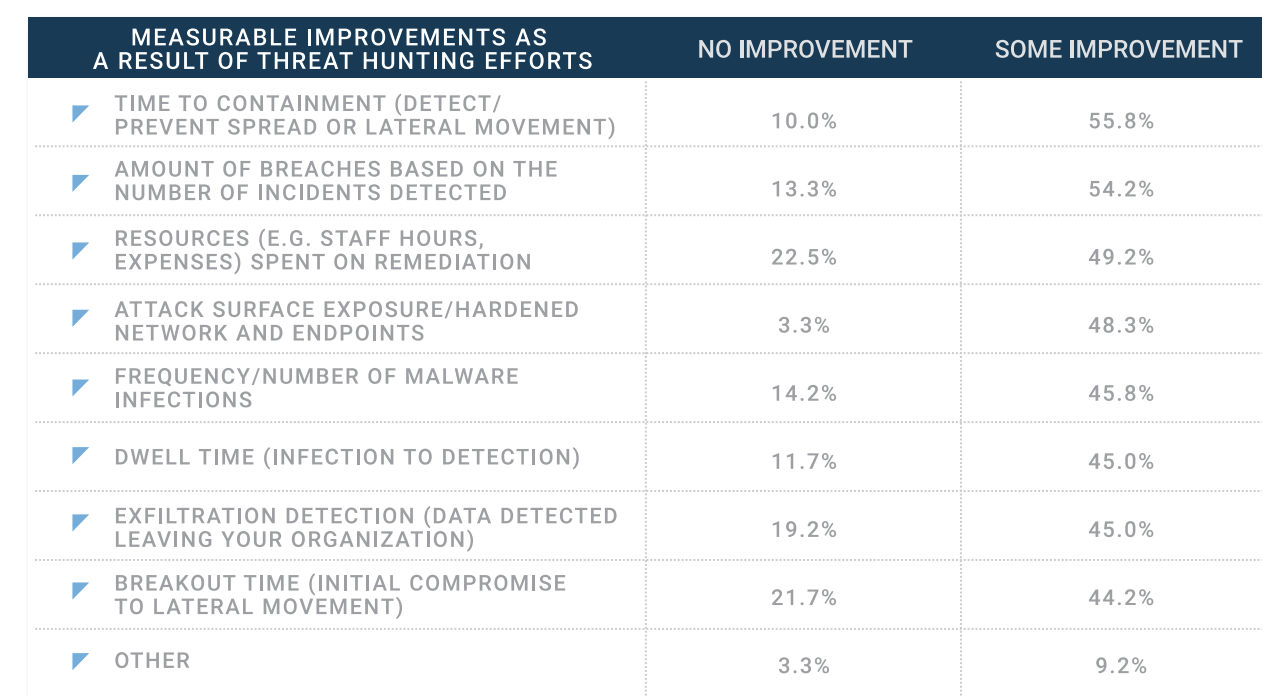
Among the respondents who measure benefits obtained from threat hunting, almost 90% reported seeing improvements in overall security. Areas that improved thanks to threat hunting included time to containment, and number of breaches.
“Once you’re able to achieve even a minimum capability of threat hunting, it helps the overall security posture of your organization,” Lee said.
How Qualys can help
Qualys VP of Product Management Chris Carlson explained how Qualys can help organizations strengthen incident response by reducing their attack surface and doing proactive threat hunting.
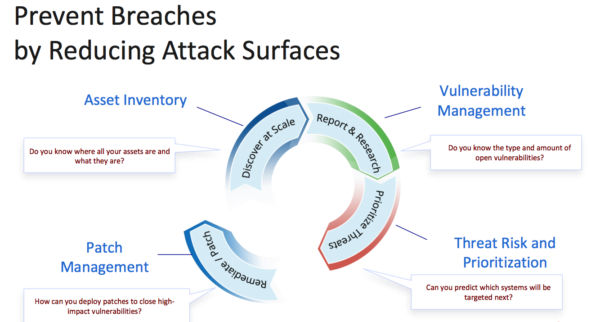
For attack surface reduction, Qualys offers apps that help you:
- Compile a continuously updated asset inventory, so that you have complete visibility into all your assets wherever they are: on premises, in clouds, and at endpoints
- Manage vulnerabilities, so you know the amount, nature and severity of bugs present in your IT environment
- Assess risk and prioritize remediation, so you can take full control of evolving threats, forecast which systems will be attacked next, and identify what to patch or mitigate first
- (Upcoming) Manage the patching process so you can effectively deploy patches to close high-impact vulnerabilities
To illustrate, Carlson cited an example where he bought a Red Hat 7.4 image in the Azure marketplace and assessed its vulnerabilities with the Qualys Cloud Agent. The agent, whose integration with Azure Security Center allows organizations to automatically deploy it on Windows or Linux images, found 27 active vulnerabilities.
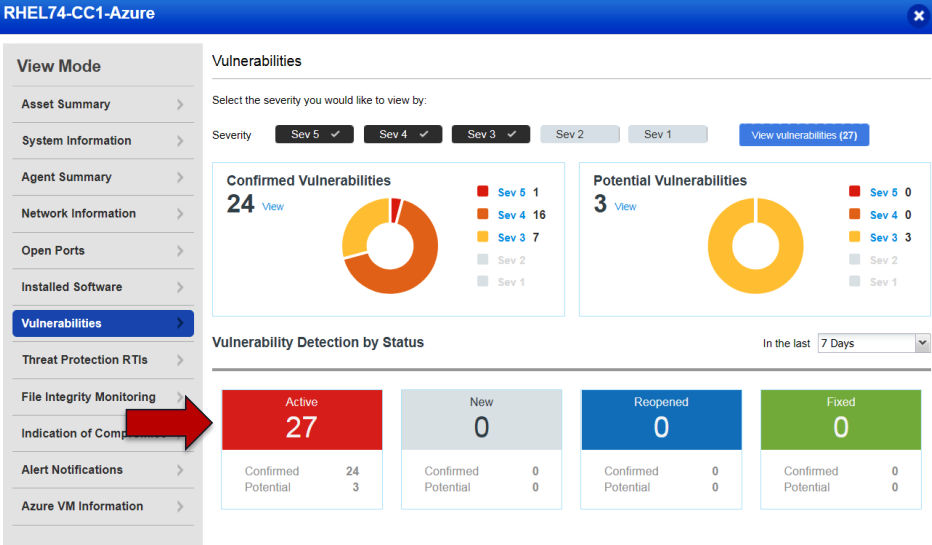
In a real-life scenario where an organization deploys 1,000 of those images with the click of a button, “that attack surface is huge,” Carlson said.
Further threat intelligence analysis using Qualys apps revealed that 14 of the vulnerabilities have known public exploits, including a zero-day bug and one that’s being actively attacked.
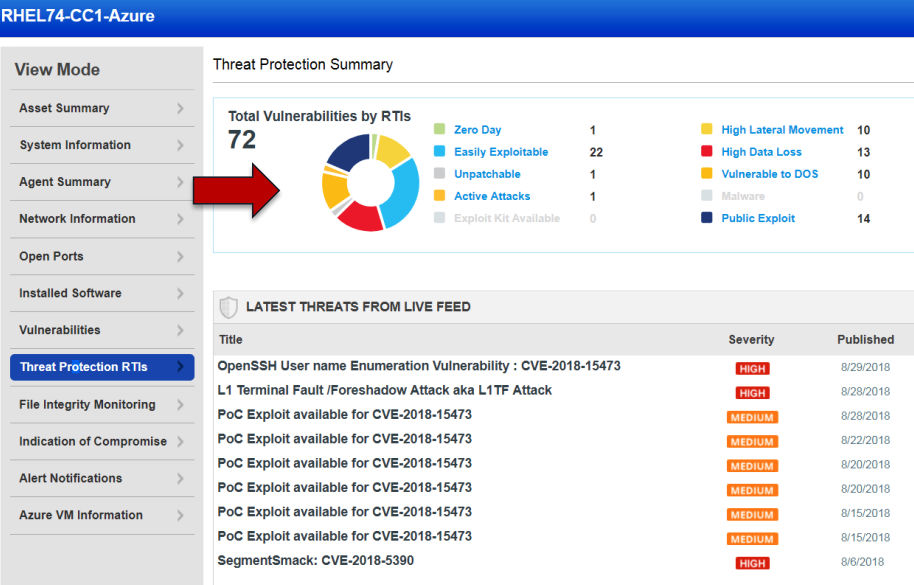
“That’s a lot of wasted time for incident response if they’re trying to respond to these items when the attack surface is this wide open,” Carlson said.
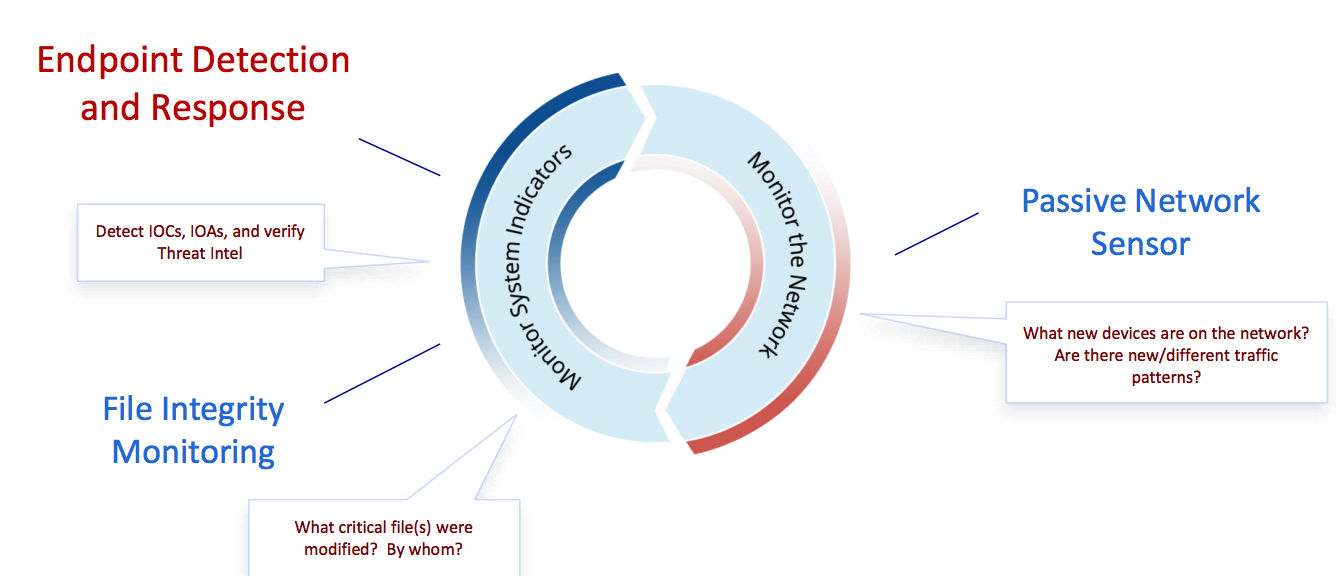
Meanwhile, for proactive hunting, detection and response, Qualys offers apps for:
- Endpoint detection and response, so you can verify threat intelligence and detect indicators of compromise, of attack, and TTPs (Tactics, Techniques and Procedures of cyber threats)
- File integrity monitoring, so you can identify files that were modified and by whom
- Passive network scanning, so you can be alerted of new devices on the network, and of different traffic patterns
Qualys has a content library with over 95 indicators of activity and TTPs to detect:
-
- “Fileless” malware attacks
- Malware evasion techniques
- Stolen code-signing certificates
- Adversaries “living off the land”
Carlson said a key component in all of these scenarios is the Cloud Agent, which can collect data for multiple Qualys apps. That way, organizations can remove point-solution agents, and consolidate security and compliance functions in a single agent, reducing costs and complexity.
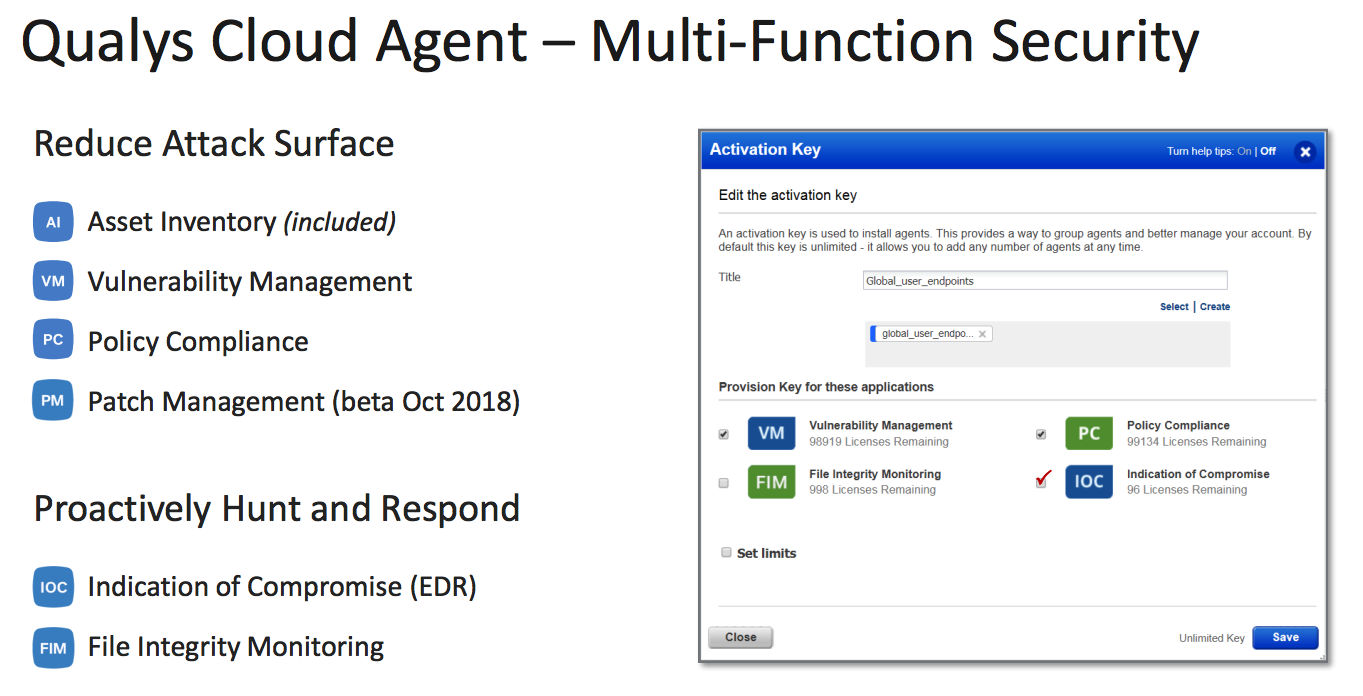
The Cloud Agent is lightweight, consuming negligible computing and network resources. After a comprehensive initial data collection of the asset, it only gathers changes. Broad OS support includes Windows, Linux, MacOS, and “cloud native” platforms such as AWS, Azure and Google Cloud. It works on premises, in clouds and remote endpoints.
We invite you to watch a recording of the webcast, which includes many more details about threat hunting, presentations from several other participants, and a Q&A session with the audience, and read the study.