Global IT Asset Inventory: The Foundation for Security and Compliance

When IT directors and CISOs look at their digitally transformed networks, they encounter many shadows that their legacy enterprise software tools can’t illuminate. These blind spots often include cloud workloads, containers, IoT systems, mobile devices, remote endpoints, and Operational Technology wares.
Since full visibility is essential for security, this foggy, fragmented view of a network makes the organization vulnerable to cyber attacks. It’s a problem Qualys is tackling head on, as several speakers stated during QSC 2018 in Las Vegas.
“This is a really big deal because it’s the basis of security: If you don’t know what you have, you can’t secure it,” Qualys Chief Product Officer Sumedh Thakar said.
That’s why Qualys is releasing a global IT asset inventory solution that offers full visibility across even the most hybrid, complex and distributed IT environments. Qualys Asset Inventory, now in beta, will provide complete and detailed visibility into on premises, cloud, remote, mobile, IoT and OT assets.
“It’s the source of truth that enterprise software hasn’t been able to deliver,” Qualys CEO Philippe Courtot said. “That’s the bedrock of what we’re doing.”
It will provide complete, continuous, structured and enriched asset inventory for IT and security teams managing assets in hybrid environments, according to Pablo Quiroga, Qualys’ Director of Product Management for IT Asset Management.
Read on to learn more details about Qualys Asset Inventory and the use cases it’s designed for; and watch the live demo from Qualys Security Conference 2018.
Common challenges
Without the right processes and technologies, it’s hard to maintain a continuously updated and comprehensive IT asset inventory. A major problem is the lack of cohesive visibility across hybrid environments when different tools are gathering asset data throughout the organization.
“The issue is the gap between these solutions. Those will be your biggest blind spots,” Quiroga said.
Having to manually clean up and correlate the asset data that these disparate point products gather is difficult and time-consuming. “A lot of time is wasted crunching data instead of making business decisions,” he said.
At issue is the nature of IT asset data, which Quiroga refers to as the “three Vs.” Volume: There’s lots of it. Velocity: It changes quickly. Variance: It’s highly inconsistent.
That last point, its variance, is ultimately “what complicates everything,” Quiroga said.
In the average asset inventory, vendor names are rendered eight different ways, and product names 20 different ways. As a result, when searching the asset database for, say, Microsoft, queries must be formulated for “Microsoft,” “Microsoft Corp.,” “Microsoft Corporation” and so on.
The Qualys approach
The platform service Qualys AssetView collects and indexes asset telemetry data, and provides instant visibility to customer’s assets. Asset Inventory takes that same continuous stream of asset telemetry and automatically adds structure by normalizing and categorizing the data.
This means that it scrubs the data and makes it uniform, eliminating, for example, the variations in product and vendor names that clutter asset inventories and render them ineffective.
It also enriches the inventory with non-discoverable metadata, such as vendor lifecycle dates and license types. This data is provided by Qualys via research and curation.
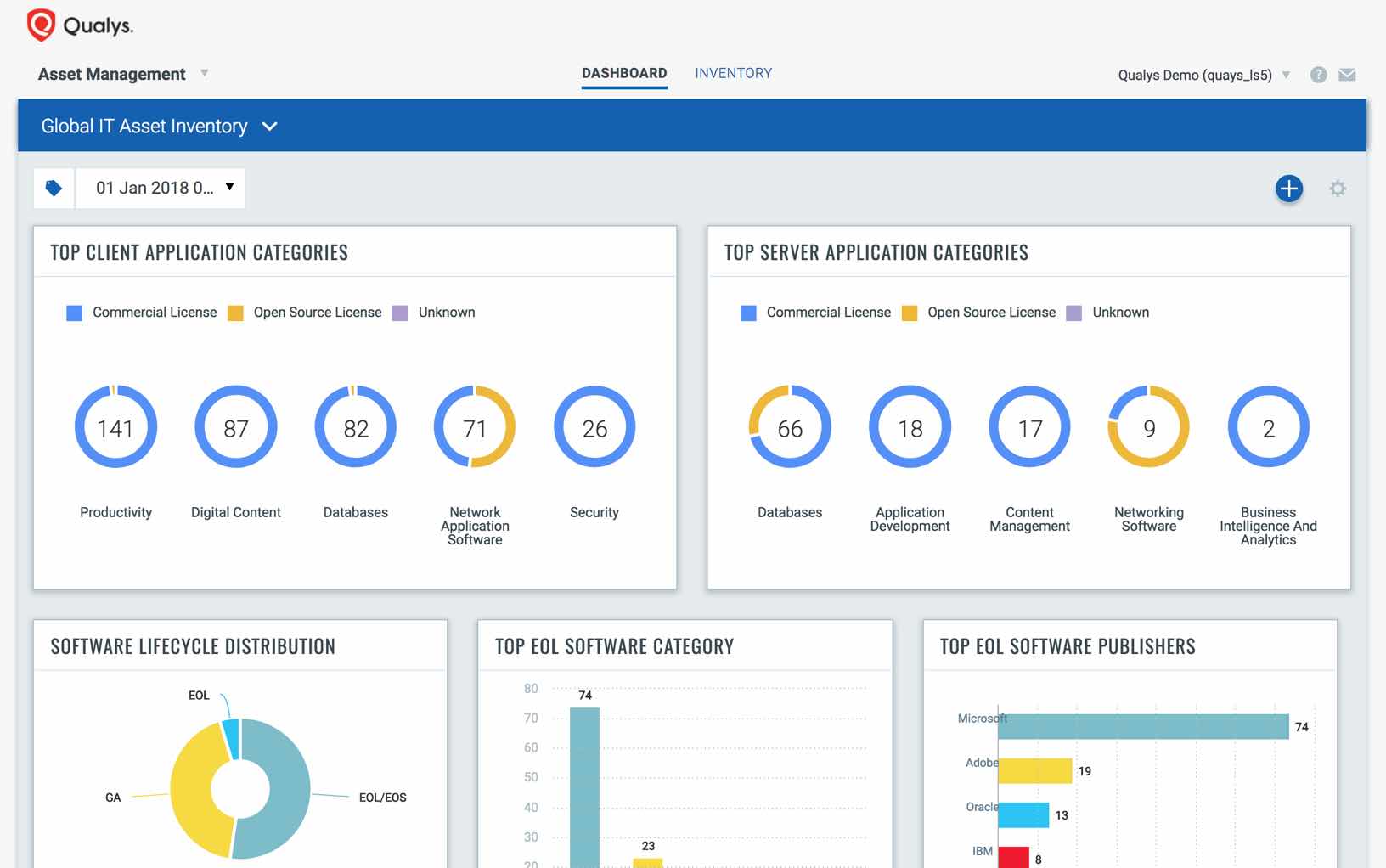
With simple queries in its powerful search engine, or a few clicks on pre-defined asset categories in its unified dashboard, organizations can instantly discover things like:
- How many Lenovo laptops running the latest Windows 10 version and located in the New York office have a particular vulnerability?
- Which servers are running an operating system that its vendor recently stopped supporting?
- Which devices have unauthorized software?
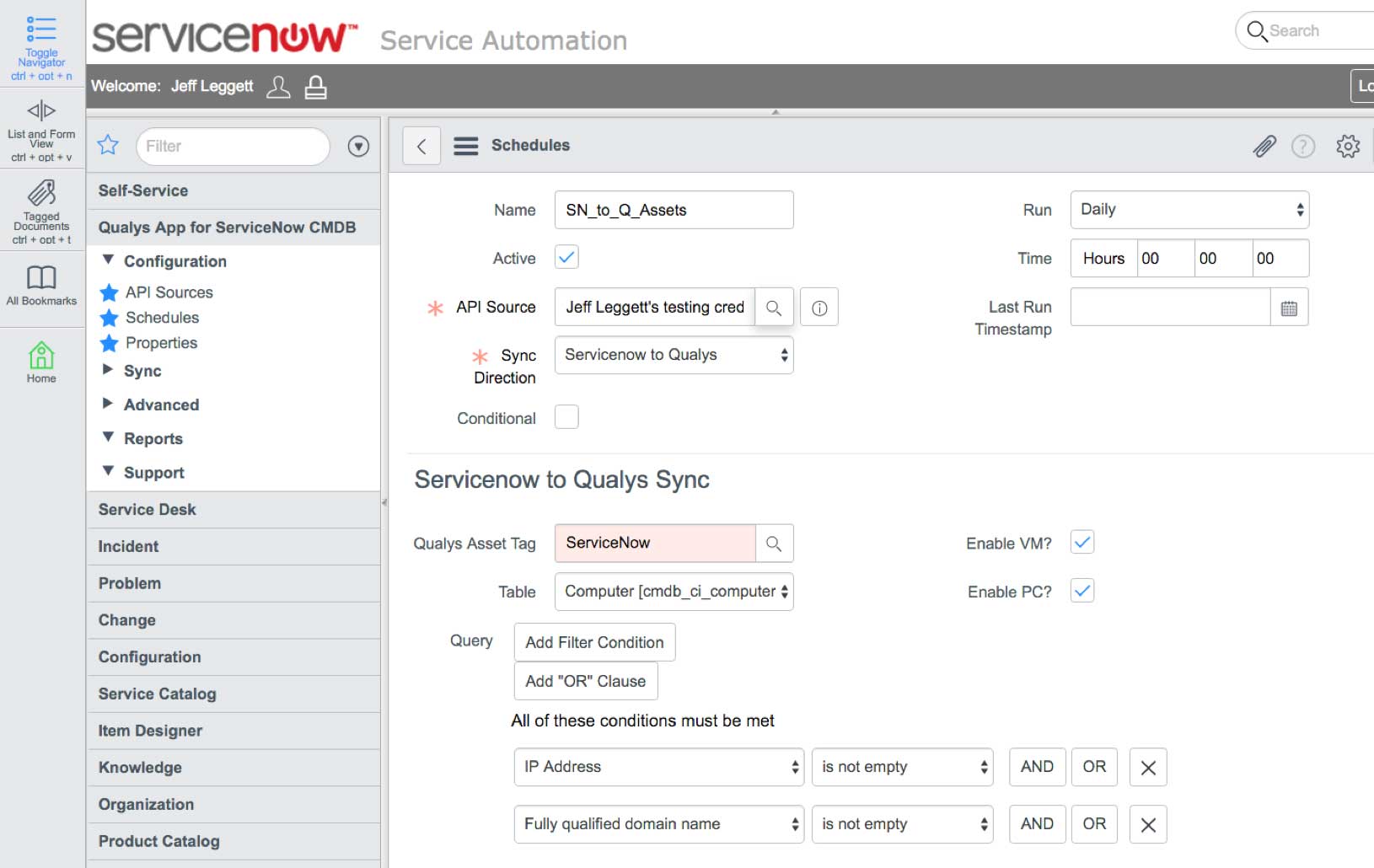
The product also syncs up with ServiceNow’s CMDB, continuously feeding it fresh data, so the CMDB can accurately map assets’ relationships, connections, hierarchies and dependencies. “The Holy Grail of CMDBs is complete, continuous, categorized, clean data,” Quiroga said.
Like other Qualys apps, Asset Inventory gets its data from Qualys sensors, so its reach is as broad as the various sensors’ coverage, including on prem, clouds and remote endpoints. “Everything starts with our scalable, self-updating and centrally managed sensors,” Quiroga said.
By collecting data with agentless, agent-based and passive sensors, Qualys provides a truly multidimensional view of the assets and of the IT environment as a whole.
Quiroga highlighted the Passive Network Sensor, currently in beta, which does real-time network analysis, eliminating blind spots through continuous traffic monitoring.
That allows Asset Inventory to include both “managed” assets which the organization is monitoring with scanners or agents, and “unmanaged” assets which are continuously detected by the passive sensor.
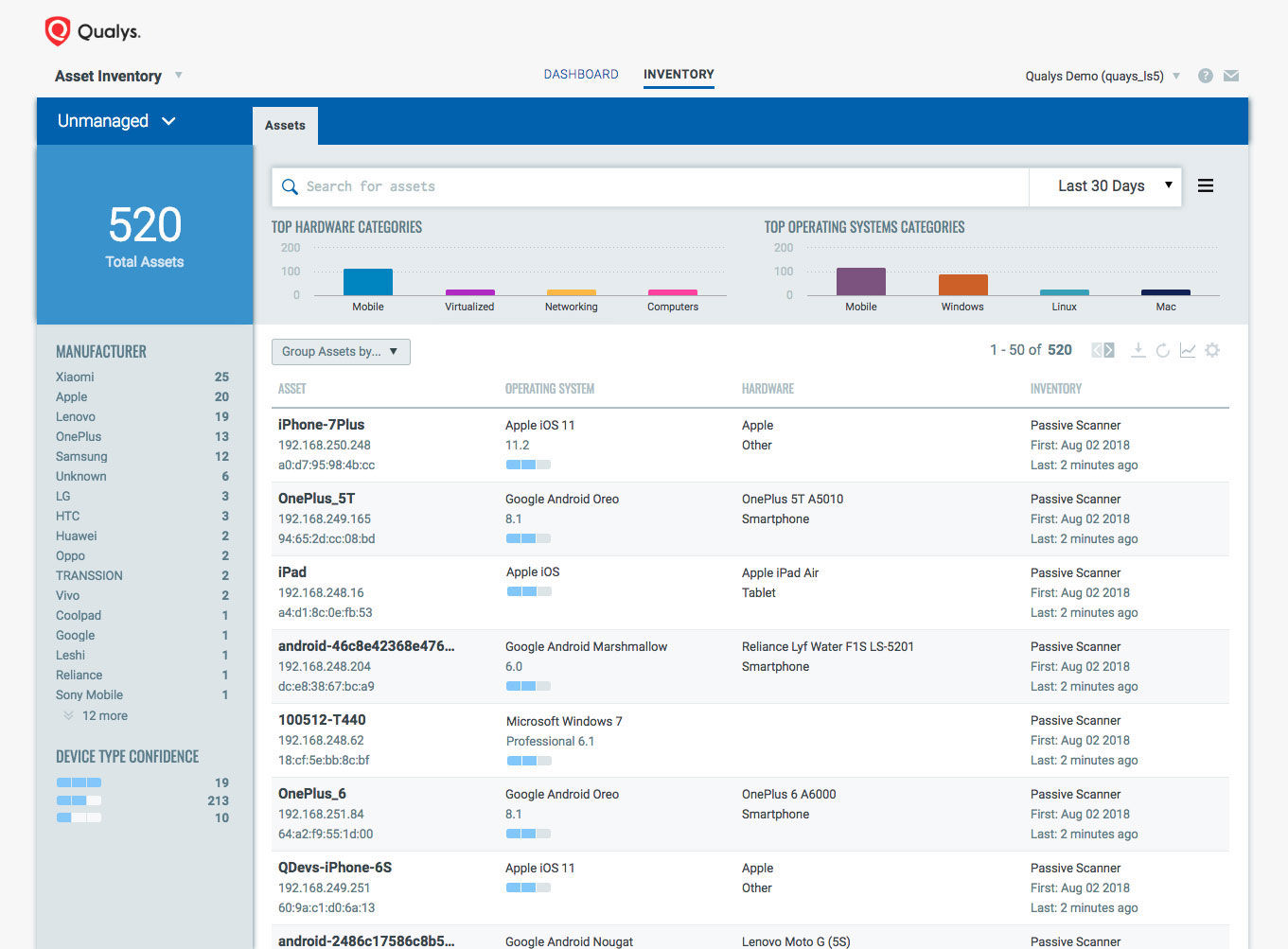
Those unmanaged assets can include anything: From IoT and OT devices to any of the many WiFi-enabled gizmos that employees or intruders can connect to a corporate network. “Everything we see on the network, we bring it together on a single view,” Thakar said.
This ability to account for the myriad types of assets found on today’s hybrid networks sets Asset Inventory apart from competing products that lack this reach and scope.
A wide variety of use cases
Beyond security, an automated IT asset inventory benefits the entire organization, in areas like financial planning, procurement, service desk automation, compliance and strategic projects.
“Harnessing a good IT asset inventory from single data source that you can use across these different teams is very powerful,” Quiroga said. “They can share the same visibility.”
By providing complete, continuous, structured and enriched asset data, and storing it in a central cloud-based backend repository, Qualys Asset Inventory can help in multiple scenarios.
For example, it can help improve the efficiency of IT help desk staff by giving them accurate, complete information about assets they’re called to support and troubleshoot.
It can also be used to optimize the use of existing assets by making it easier to identify hardware and software that’s underused, completely idle, damaged, or obsolete.
The app can also be tapped for providing detailed asset information to auditors, which eases regulatory and internal compliance processes that require documenting asset information.
Asset Inventory can also assist in prioritizing vulnerability remediation work by focusing on patching the critical assets that need the most immediate attention.
Furthermore, it can help in responding more quickly and precisely to incidents like breaches by revealing the location, configuration, and owner of a device, or the presence of rogue software.
Ultimately, Asset Inventory can play a key role in helping IT and security achieve their main common goal: “To make sure you enable your users to be productive and secure,” Quiroga said.
Please watch a video of Quiroga’s presentation, which has a lot more details about Qualys Asset Inventory, including a live demo, and a question-and-answer session with the audience.