Assess Vulnerabilities, Misconfigurations in AWS Golden AMI Pipelines
Table of Contents
Today we’re starting a blog series focused on how to integrate Qualys solutions into DevSecOps for securing cloud infrastructures. In this initial post, we’ll discuss the importance of assessing vulnerabilities and misconfigurations on AWS pipelines.

When developing golden Amazon Machine Images (AMIs), DevOps teams should run continuous and automated checks to eliminate vulnerabilities and misconfigurations in them. It’s a critical security and compliance practice that Qualys recommends its customers adopt.
To that end, Qualys partnered with Amazon to integrate the AWS Golden Amazon Machine Image Pipeline reference architecture with Qualys scanners for vulnerability and configuration compliance assessment.
The result: Qualys has just published a GitHub repository and documentation for implementing Qualys scanning of instances in a golden AMI pipeline. This will help customers detect and fix critical vulnerabilities and compliance issues in the image creation pipeline, before they reach production environments.
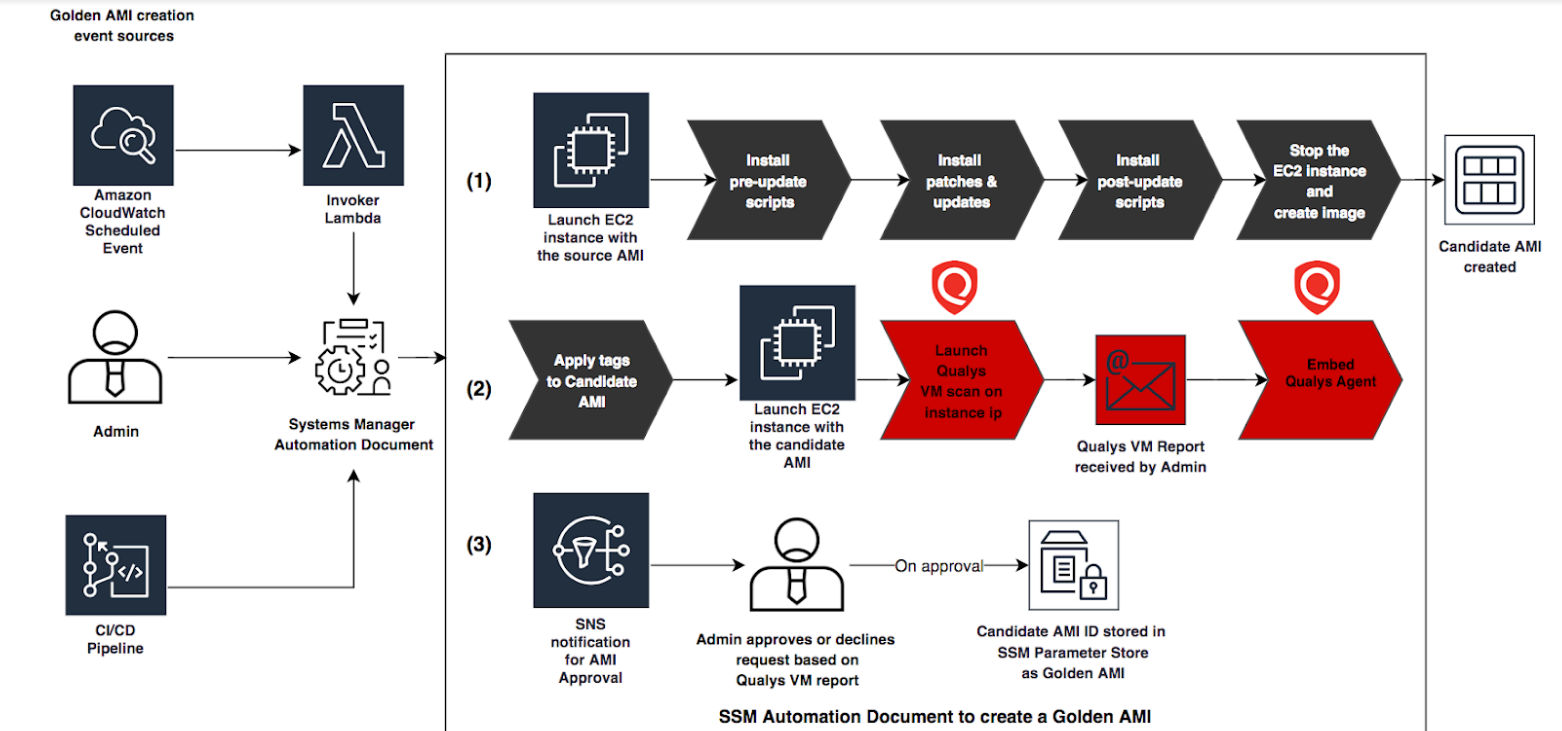
Later on, Qualys plans to include an AWS Lambda function for processing Qualys scan results for the most serious vulnerabilities — severity 5 and severity 4 — and for remotely-exploitable vulnerabilities. The AWS Lambda function will analyze the scan results of the AMI candidate and create tags to capture vulnerability characteristics. This feature can be used for automating the approval of images based on vulnerability severity or number of vulnerabilities detected.
Qualys’ AWS Golden Amazon Machine Image Pipeline will also embed the Qualys Cloud Agent into the approved golden AMI as part of the build-and-approve process. That will help customers automate the deployment of the Qualys Cloud Agent in their environment. Utilizing the Qualys Cloud Agent, customers can implement continuous vulnerability and compliance scanning of instances deployed from these approved golden AMIs, and leverage additional Qualys cloud platform applications, including:
This will provide customers with end-to-end visibility of the entire lifecycle of their AMIs and deployed instances, so that they can better qualify and quantify the vulnerabilities and risk postures of their cloud instance assets.
Meanwhile, Amazon announced a sample implementation for integrating a golden AMI pipeline with Qualys scanners. As Amazon explained in its blog post, the Qualys integration will help customers “automate your AMI creation process in a standardized fashion, as well as perform continuous assessments on the portfolio of hardened AMIs existing in your AWS environment.”
We updated the Amazon sample implementation to include Qualys’ pre-authorized scanner for AWS. That way, users don’t have to get penetration testing approvals from AWS and they can embed Qualys Cloud Agents into the final AMI. This gives them continuous visibility of their elastic cloud-based deployments in live environments.
The next blog post in this series will focus on the Qualys reference architecture for your public cloud-based infrastructure.
Resources
- AWS Golden AMI Pipeline Video Library
- Golden AMI Pipeline with Qualys (Github)
- Monitoring AWS Golden AMI Pipelines with Slack
- Creating a Golden AMI Pipeline Integrated with Qualys for Vulnerability Assessments
(Sean Nicholson is a Security Solution Architect for Cloud Security at Qualys)
You can find Qualys products for AWS security and compliance on the AWS Marketplace. We invite you to sign up for a free trial of the Qualys Cloud Platform so you can experience Qualys’ industry-leading security and compliance solutions.
I am trying to implement this pipeline in my organization.
I see there is a command in your ssm document that is making QualysRunPcScan at:
https://github.com/Qualys-Public/golden-ami-pipeline-with-qualys/blob/master/ami_golden_ami_pipeline_qualys-vm-pc.json#L1836
I am told the Qualys appliance scanner requires Qualys user to be added to the server in order for the scan to be done.
Within your pipeline do you create the user? If yes, is it removed before creating the golden ami.
OR
Do you register with the central qualys using agent?
appreciate your clarification
Hi Venu,
Just wanted to post the reply here after our working session. This pipeline uses an AWS SSH Key to access the systems, the candidate AMI is used to create the instance and the SSH key is passed as part of the instance configuration information by the pipeline. Since the scan is of the instance built from the AMI this authentication record is specific to the pipeline and is configured for the pipeline assigned IP space and does not persist on the AMI once the candidate AMI is approved or rejected. Information on using AWS SSH Keys for scan authentication can be found https://www.qualys.com/docs/qualys-securing-amazon-web-services.pdf.
Thank you
Sean