Detect Apache Tomcat AJP File Inclusion Vulnerability (CVE-2020-1938) using Qualys WAS
As previously reported, a severe vulnerability exists in Apache Tomcat’s Apache JServ Protocol. The Chinese cyber security company Chaitin Tech discovered the vulnerability, named “Ghostcat”, which is tracked using CVE-2020-1938 and rated critical severity with a CVSS v3 score of 9.8.
This blog post details how web application security teams can detect this vulnerability using Qualys Web Application Scanning (WAS). This new Qualys WAS detection complements the detection that uses Qualys VMDR®.
About CVE-2020-1938
Apache Tomcat web servers are widely used for deploying Java-based web applications. Apache JServ Protocol (AJP) is used for communication between Tomcat and Apache web server. This protocol is binary and is enabled by default. Anytime the web server is started, AJP protocol is started on port 8009. It is primarily used as a reverse proxy to communicate with application servers.
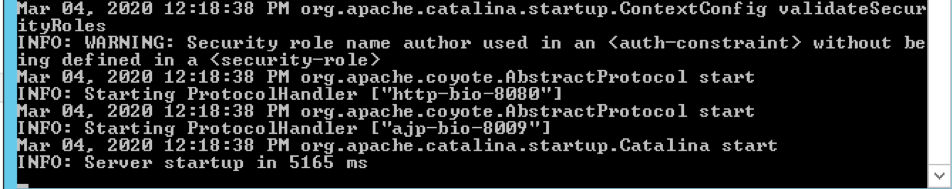
The most common way to identify whether the protocol is indeed enabled is to first locate the web server’s conf/ directory. Look for the server.xml configuration file that specifies all the default protocols and the document root directory configuration. As you would learn through reading server.xml, connector port 8009 is not commented and is explicitly enabled by default.
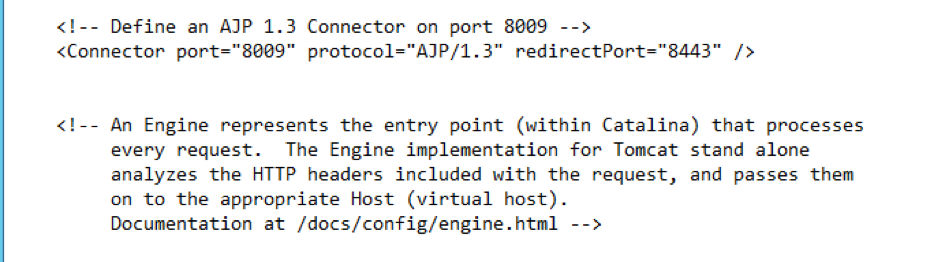
The Apache Tomcat AJP File Inclusion vulnerability (CVE-2020-1938) is exploitable only if port 8009 is exposed and AJP is installed.
Affected Apache Tomcat versions will get reported under the Qualys WAS detection (see details of the detection below).
- Apache Tomcat 9.0.0 to 9.0.30
- Apache Tomcat 8.5.0 to 8.5.50
- Apache Tomcat 7.0.0 to 7.0.99
Exploitability
With this vulnerability, an attacker can easily gain access to configuration files if the protocol is publicly available. If arbitrary file upload is not disabled, it is then possible for the attacker to upload malicious code to the web server that enables remote code execution.
Below is a report of the exploit:
You can read any webapps files or include a file to RCE .JUST A POC-GIF with no DETAILS
Tomcat has fix this vulnerability ,UPDATE! pic.twitter.com/Jauc5zPF3a
— Henry Chen (@chybeta) February 20, 2020
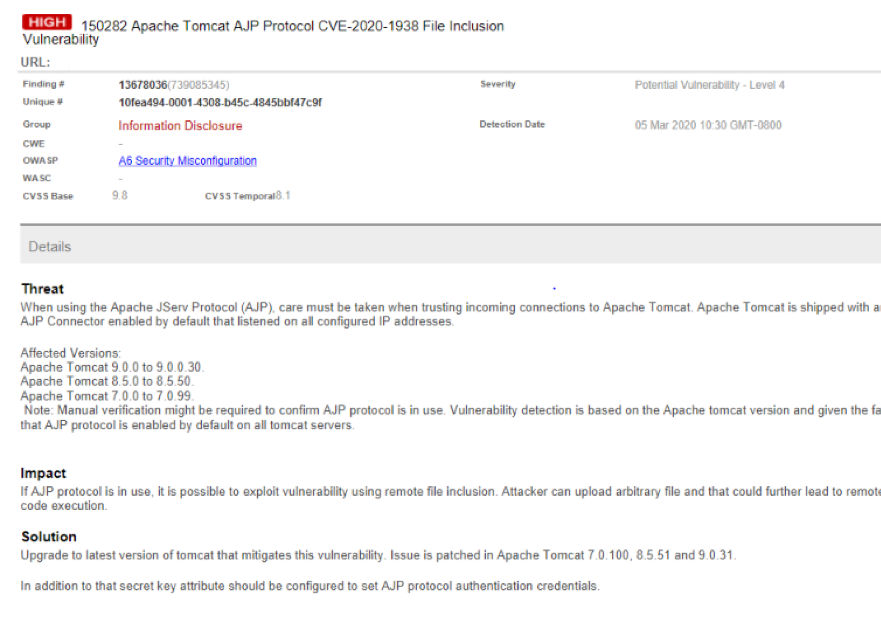
Identifying CVE-2020-1938 Vulnerability using WAS scan
Enable QID 150282 in your Qualys WAS option profiles to identify if you are running a vulnerable version of Apache Tomcat. The WAS scan will report QID 150282 as a potential vulnerability. To keep it simple, our scan will not attempt to actively determine the vulnerability by uploading an arbitrary file. We take into consideration that AJP is a binary version of HTTP and could not be requested over HTTP, hence the detection of the vulnerable server is determined based on the presence of Tomcat version and the fact that it is shipped with default configurations.
Additional Attack Vector
We also recommend to enable the following two QIDs in Qualys Web Application Scanning:
- 150114: Arbitrary File Upload
- 150125: File Upload Form Found
The vulnerability becomes more critical when the application allows file uploads. This will lead to the possibility of Remote Code Execution, allowing attacker to take complete take over of the web server. This requires immediate attention if you are using AJP and a vulnerable version of Apache Tomcat.
Remediation Guidance
Disable port 8009 by commenting out (or deleting) the block of code that enables this vulnerability.
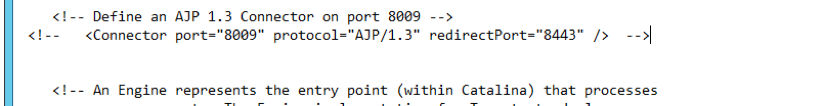
Restart Apache Web Server for changes to take effect.
RequiredSecret Attribute
Regardless of whether you disable AJP, we also recommend to define the strong secret key attribute requiredSecret in server.xml, which sets AJP protocol authentication credentials and ensures that only requests from authenticated workers will be honored. In this case, Tomcat will instantiate the AJP connector only when this attribute is specified with non-null and non-zero values. Note Tomcat documentation clearly states the default value for the attribute is null.
Upgrade Tomcat
It is recommended to upgrade to patched versions of Apache Tomcat Web Servers:
- Apache Tomcat version 9.0.31
- Apache Tomcat version 8.5.51
- Apache Tomcat version 7.0.100
Additional detection and remediation details are described in Automatically Discover, Prioritize and Remediate Apache Tomcat AJP File Inclusion Vulnerability (CVE-2020-1938) using Qualys VMDR.
What will be the impact to tomcat related application, if we disable the AJP Protocol port?
You can disable port 8009 if you do not need it, ideally this port is not exposed to outside from where it is hosted.