Real-Time Alerting and Incident Management for Unauthorized Changes
The security landscape is constantly changing, and you need to adopt proactive measures to stay ahead of security breaches by being extremely vigilant about every little change in your environment. In our previous blog, we discussed how you can leverage the ready-to-use monitoring profiles in your CI/CD pipeline to start monitoring your critical system and application files. However, just setting files to monitor isn’t sufficient. You need a layer of ‘real-time detection’ to eliminate all blind spots in your network. Hence, once you are done configuring the “what to monitor” part in your environment, the next step is to configure the correlation rules to generate real-time alerts for changes and create authorized or unauthorized incidents automatically. Receiving instant alerts upon file changes in your network is the next line of defense mechanism for you to mitigate impending loss of data.
Implementing tools to receive alerts upon changes in a monitored environment in itself is a prerequisite for compliance per PCI-DSS requirement 11.5, which states – “Deploy a change detection mechanism (for example, file integrity monitoring tools) to alert personnel to unauthorized modification of critical system files, configuration files, or content files; and configure the software to perform critical file comparisons at least weekly.” Many other regulations and frameworks such as HIPAA, GDPR, FedRAMP (NIST 800-53) require you to receiver alerts and notifications on unauthorized changes to critical files.
Instant Notifications with Qualys File Integrity Monitoring
With Qualys File Integrity Monitoring (FIM), you receive real-time updates about each such anomalous event that is detected, complete with granular details such as who-what-when-where, about the changes occurring within the scope of your monitored area. Events can be expected and authorized or unexpected and malicious. With alerts and notifications, you can make sure that nothing that is unauthorized goes unnoticed and eventually leads to a security hazard.
With the flexibility of creating correlation rules for grouping similar events together and for alerting authorized users upon an incident, you know that you are in control of security and integrity of your data. And that’s exactly what Qualys FIM does for you with the help of the ready-to-use queries for alert rules in its library. You can avail the easy-to-use, predefined set of queries in the Qualys FIM Library to create alert rules or correlation rules. The correlation rules can be used to group similar events of interest and then to receive notification for the same.
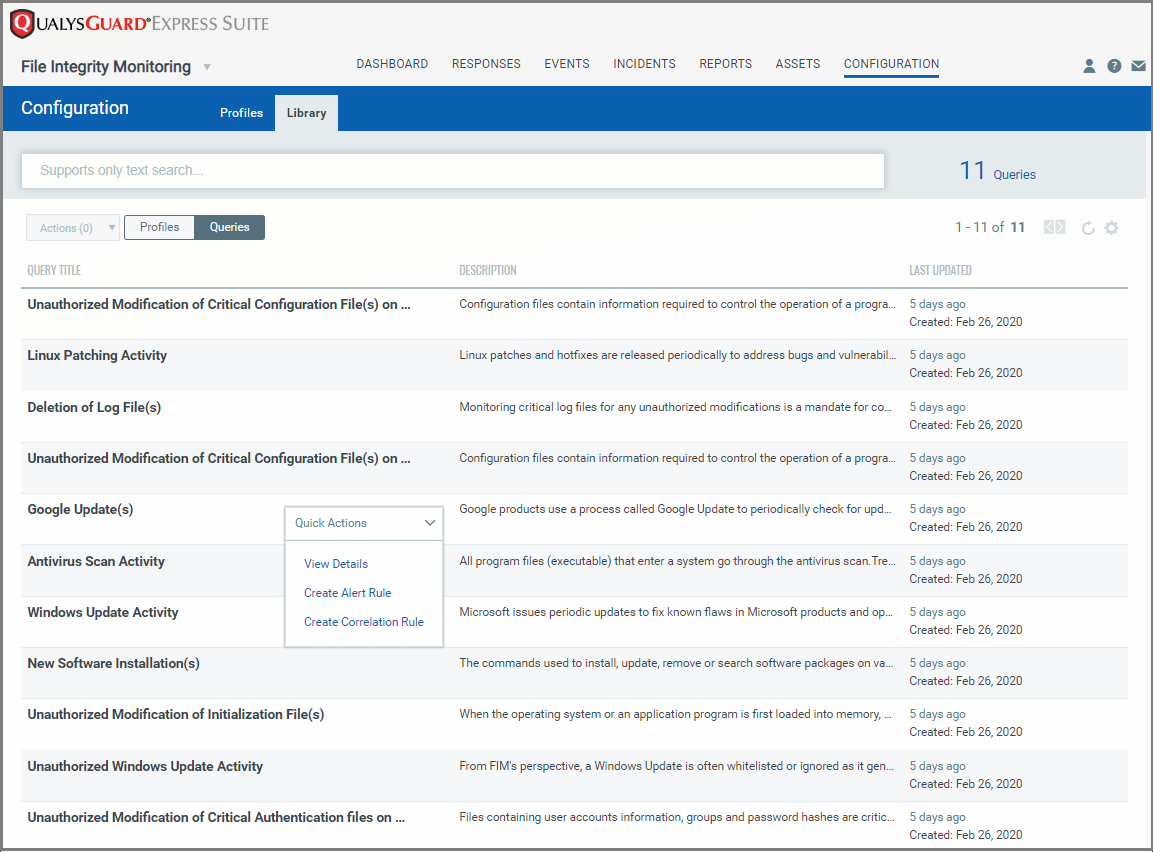
Real-time Alerting and Automated Incident Management with Ready-to-Use Rules in Qualys FIM
The preconfigured rules in Qualys FIM’s Rule Library are created by Qualys’ team of security experts, with the focus on providing you with a solution that’s intuitive and easy to implement. These queries can be used for creating rules for alerts and incidents. All you must do is import the queries from the library and use them as they are. If required, you can also customize them to suit your organizational requirements. The tailor-made approach drastically reduces the volume of data that needs to be monitored and the complexity around it. It unifies monitoring capabilities, alerts, and event management efforts and enables users to optimize performance with dedicated focus on events that need attention and an immediate action.
Leverage pre-configured rules for managing common, potentially unauthorized activities.
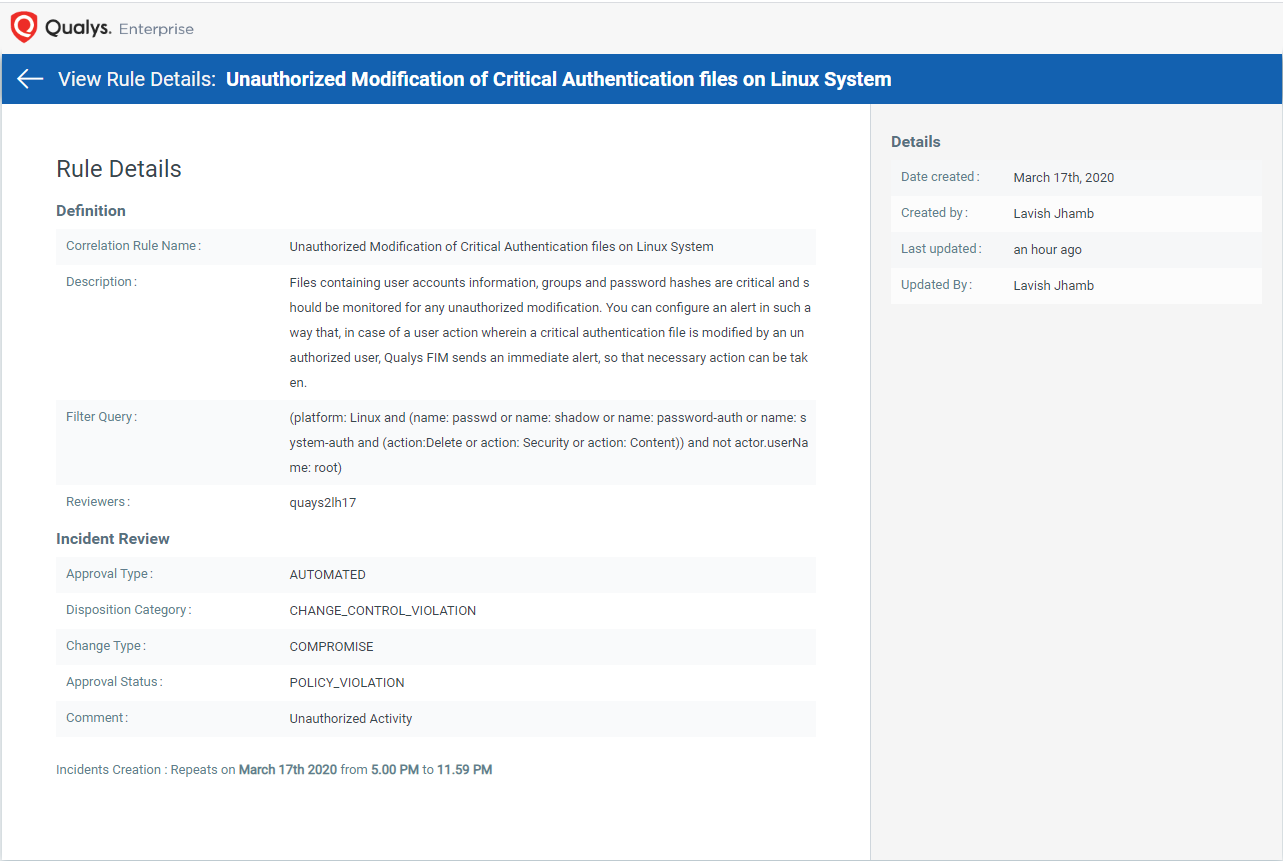
Tracking unauthorized modification of critical authentication files on Linux systems
Not all users are security conscious, and they may not necessarily create strong passwords all the time. Hence, an attacker may take a chance on human error or overconfidence and gain access into critical data.
Files containing user account information, groups, and password hashes are critical and must be monitored for any kind of unauthorized modifications. For example, unauthorized changes in critical files such as ‘/etc/passwd’ and ‘/etc/shadow’. It is critical to ensure that the ‘/etc/passwd’ file is protected from unauthorized write access. Although it is protected by default, the file permissions could be changed either inadvertently or through malicious actions.
Similarly, if attackers gain read access to the ‘/etc/shadow’ file, they can easily run a password cracking program against the hashed password to break it. Security information that is stored in the ‘/etc/shadow’ file (such as expiration) could also be useful to subvert the user accounts.
Such files are highly critical and are mentioned in almost all compliance mandates such as CIS, DISA etc.
Qualys FIM’s default monitoring profiles include these files as well, so they are under continuous monitoring. Any unauthorized change to such files can cause the entire environment to be compromised.
To elaborate on how Qualys FIM’s rules library can be leveraged in such a scenario, here is an end-to-end depiction of the same and how the real-time alerts on unauthorized changes help you stay on top of detections.
Let’s assume you already have monitoring rules in place for ‘/etc/shadow’ and ‘/etc/passwd’ files for continuous monitoring. Ideally these files must be altered by a user who has the rights and is authorized to make modifications, such as ‘root’. In the event of an unauthorized user making changes in these files, you definitely would want to receive notifications so that you can take necessary action. This can be achieved by using the following query from the Rules Library:
(platform: Linux and (file.name: passwd or file.name: shadow or file.name: password-auth or file.name: system-auth and (action:Delete or action: Security or action: Content)) and not actor.userName: root)
The query specifies the files – ‘passwd’, ‘shadow’, ‘password-auth’, and ‘system-auth’ – that are to be monitored and for the actions – deletion, modification of security settings and content.
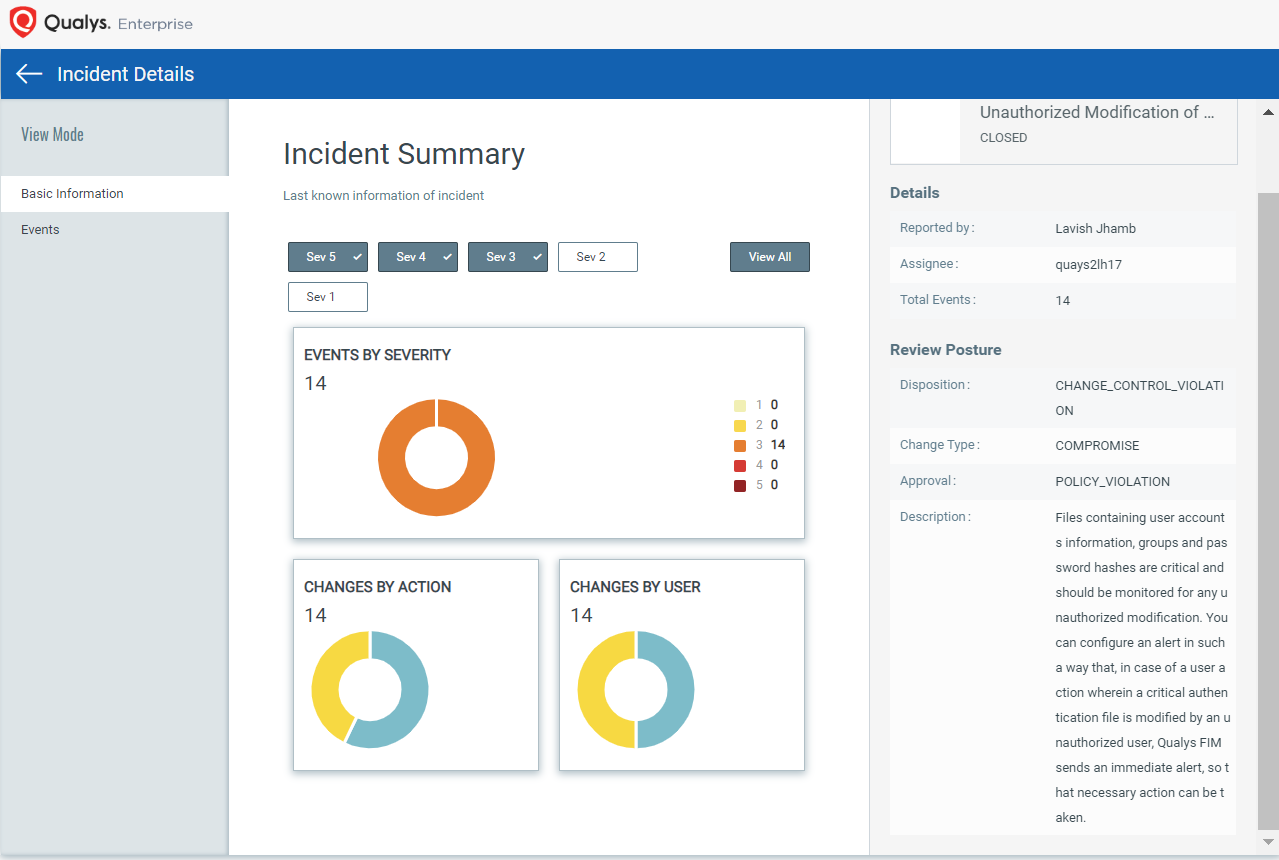
As soon as a specified action is detected on any of these files, and alert will be triggered and sent to the specified user.
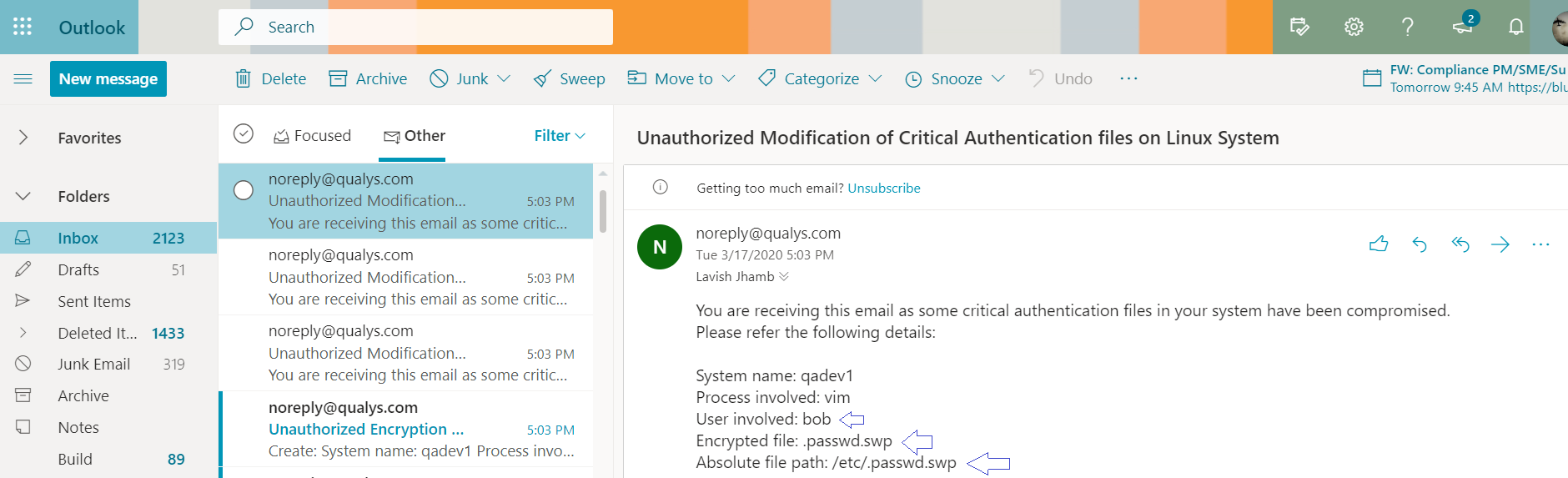
Many More Preconfigured Ready-to-Use Rules for Managing Incidents and Alerts
Here are a few examples of activities we see our customers monitoring, with preconfigured rules available in the Qualys FIM Library, and how they use them in their environments for instant alerting and automatic incident management.
Deletion of log files
Monitoring critical log files for any unauthorized modifications is a mandate for compliance regulations such as PCI DSS, HIPAA, SOX and others. Qualys FIM’s alerting capabilities can be utilized to create a custom alert whenever a critical log file is deleted. Fimc.log and Qualys Cloud Agent log files are critical for Qualys FIM to operate. Hence, creating a rule to check for an unauthorized deletion would enhance the overall security.
Unauthorized modification of critical configuration files on Linux systems
Configuration files contain information required to control the operation of a program. Qualys FIM helps you create alerts for any unauthorized modification in configuration files that are of utmost importance for system startup and are also read by various applications to customize the environment.
Unauthorized Modification of Critical Authentication files on Linux Systems
Files containing user accounts information, groups, and password hashes are critical and must be monitored for any kind of unauthorized modification. You can configure an alert in such a way that, in case of a user action wherein a critical authentication file is modified by an unauthorized user, Qualys FIM sends an immediate alert, so that necessary action can be taken.
Conclusion
Backed by the powerful Qualys Cloud Platform, Qualys FIM’s ‘pre-configured’, ‘ready-to-use’ rules for alerts and incident management, make it easy for you to ensure that every critical change is highlighted in real time and enable you to avoid the drudgery of manually combing through thousands of events. The critical information provided by these meticulously drafted, ready-to-use query rules enable you to make quick decisions and proactively mitigate the risk of data breaches.
Additional Resources
Learn about all Qualys File Integrity Monitoring capabilities and how you can try them for free: https://www.qualys.com/apps/file-integrity-monitoring/
Qualys File Integrity Monitoring Data sheet:
https://www.qualys.com/docs/fim-datasheet.pdf
See details on how multi-function Qualys Cloud Agent can be leveraged for File Integrity Monitoring:
https://www.qualys.com/training/library/fim/
https://www.qualys.com/training/library/cloud-agent/
Acknowledgements
Lavish Jhamb, Senior Compliance Research Analyst at Qualys, provided technical guidance for this blog.