NSA Announces Sandworm Actors Exploiting Exim MTA Vulnerability (CVE-2019-10149)

The Exim MTA vulnerability, initially reported by Qualys in May 2019, is currently being exploited in the wild. Recently, the US National Security Agency (NSA) announced that Sandworm actors (Russian hacker group) have been actively exploiting the Exim Mail Transfer Agent vulnerability.
Qualys released a blog post last year describing how to identify assets that are impacted by this vulnerability in your environment: Exim MTA Vulnerability (The Return of the WIZard – CVE-2019-10149)
Sandworm Attacks
Exim MTA vulnerability could be exploited by sending a malicious email to the server, allowing an attacker to run code on the server remotely. This vulnerability can lead to Remote Command Injection, and is currently being actively attacked in the wild.
NSA mentioned Sandworm actors have been exploiting this vulnerability since at least August 2019. The actors exploited victims using Exim software on their public facing MTAs by sending a command in the “MAIL FROM” field of an SMTP (Simple Mail Transfer Protocol) message. Sandworm executed shell script to perform following action on victim’s system:
- Add privileged users
- Disable Network Security settings
- Update SSH configurations to enable remote access
- Execute an additional script to enable follow-on exploitation
The unpatched systems are highly at risk and immediate action should be taken to remediate this vulnerability.
Detecting CVE-2019-10149
The best method for identifying vulnerable hosts is through the Qualys Cloud Agent or via authenticated scanning. Qualys released several QIDs for various Linux distros, as well as a generic remote Potential QID (50092) that will identify Exim hosts. You can search for these QIDs in VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.cveIds:`CVE-2019-10149`
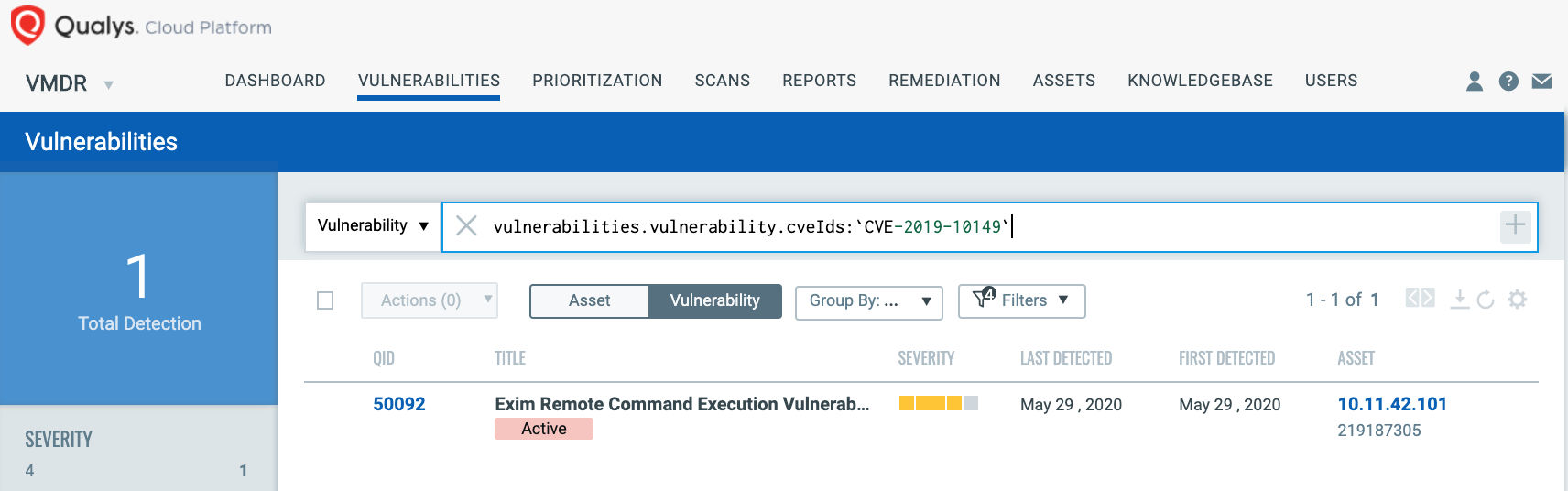
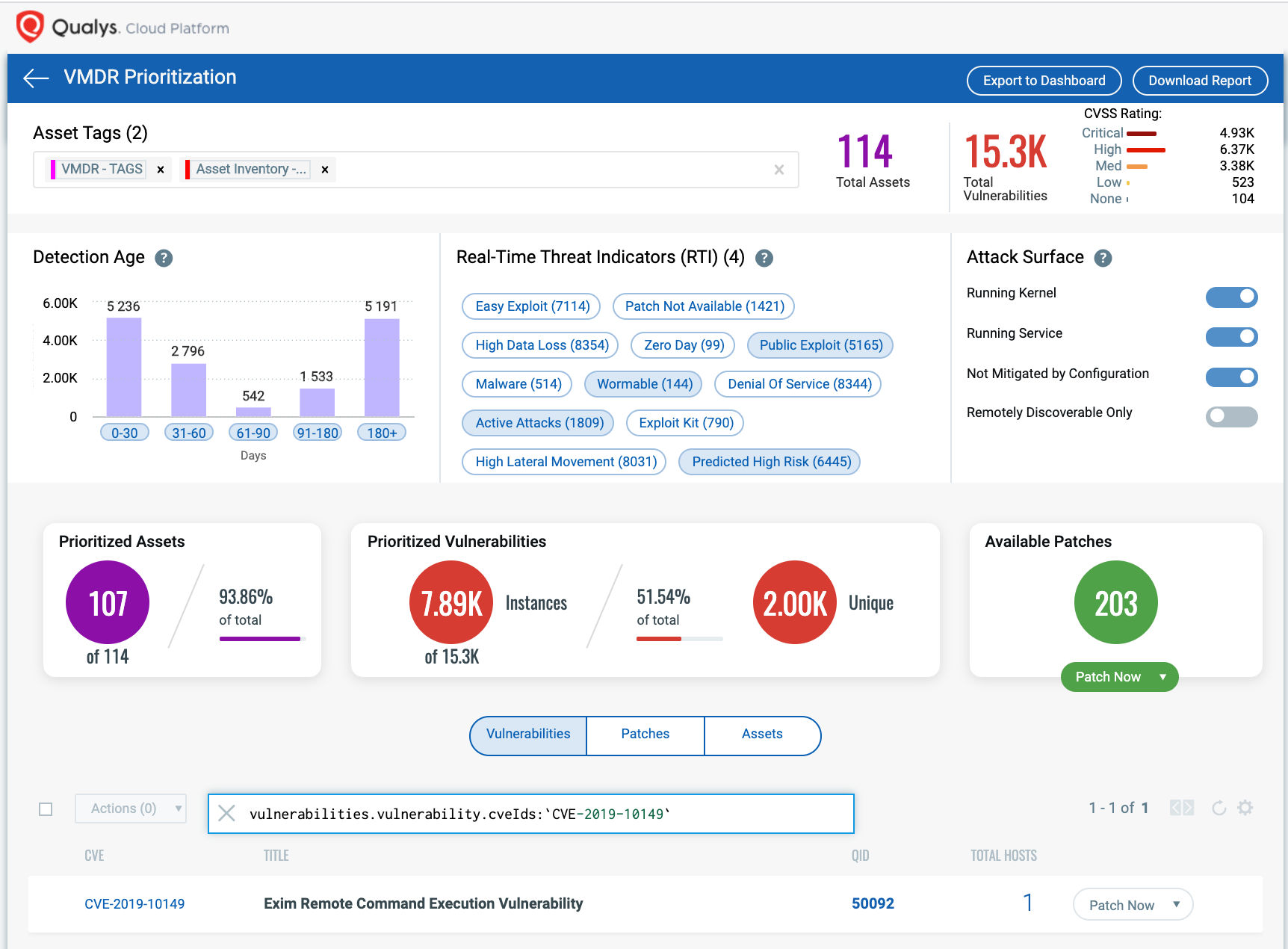
In addition, Qualys VMDR customers can effectively prioritize this vulnerability as Qualys QID 50092 contains following RTIs (Real-Time Threat Indicators):
- Active Attacks
- Public Exploit
- Predicted High Risk
- Wormable
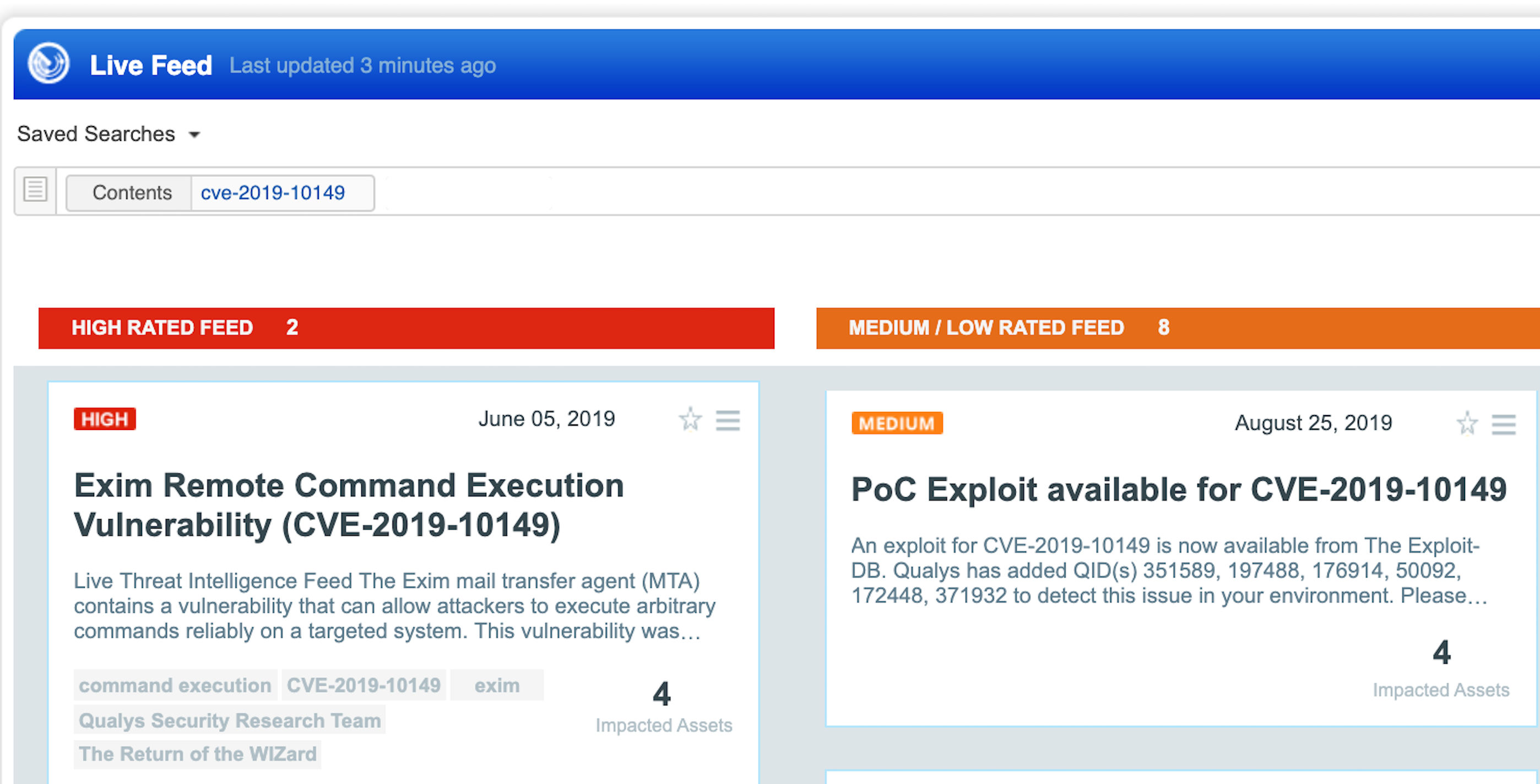
VMDR customers can also stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
Remediation
Customers are advised to update Exim immediately by installing version 4.92 or newer to remediate this vulnerability. System admins can update respective linux distros using package manager or by downloading the latest version from https://www.exim.org/mirrors.html
Get Started Now
To start detecting and remediating this vulnerability now, get the Qualys VMDR trial.