NSA Alert: Chinese State-Sponsored Actors Exploit Known Vulnerabilities

Last updated on: December 2, 2020
Table of Contents
Update November 25, 2020: The UK National Cyber Security Centre alerts that APT nation-state groups and cybercriminals are exploiting MobileIron RCE vulnerability (CVE-2020-15505).
Original post: On October 20, 2020, the United States National Security Agency (NSA) released a cybersecurity advisory on Chinese state-sponsored malicious cyber activity. The NSA alert provided a list of 25 publicly known vulnerabilities that are known to be recently leveraged by cyber actors for various hacking operations.
“Since these techniques include exploitation of publicly known vulnerabilities, it is critical that network defenders prioritize patching and
mitigation efforts,” said the NSA advisory. It also recommended “critical system owners consider these actions a priority, in order to mitigate the loss of sensitive information that could impact U.S. policies, strategies, plans, and competitive advantage.”
Earlier this year, the NSA also announced Sandworm actors exploiting the Exim MTA Vulnerability. Similar alerts have been published by the Cybersecurity and Infrastructure Security Agency (CISA) over the last year. CISA also issued an advisory notifying about vulnerabilities that were exploited in the wild to retrieve sensitive data such as intellectual property, economic, political, and military information.
Here is a list of 25 publicly known vulnerabilities (CVEs) published by the NSA, along affected products and associated Qualys VMDR QID(s) for each vulnerability:
| CVE-ID(s) | Affected products | Qualys QID(s) |
| CVE-2020-5902 | Big-IP devices | 38791, 373106 |
| CVE-2019-19781 | Citrix Application Delivery Controller Citrix Gateway Citrix SDWAN WANOP | 150273, 372305, 372685 |
| CVE-2019-11510 | Pulse Connect Secure | 38771 |
| CVE-2020-8193 CVE-2020-8195 CVE-2020-8196 | Citrix ADC and Citrix Gateway versions before 13.0-58.30, 12.1-57.18, 12.0-63.21, 11.1-64.14 and 10.5-70.18 Citrix SDWAN WAN-OP versions before 11.1.1a, 11.0.3d and 10.2.7 | 13833, 373116 |
| CVE-2019-0708 | Microsoft Windows multiple products | 91541, 91534 |
| CVE-2020-15505 | MobileIron Core & Connector | 13998 |
| CVE-2020-1350 | Microsoft Windows multiple products | 91662 |
| CVE-2020-1472 | Microsoft Windows multiple products | 91688 |
| CVE-2019-1040 | Microsoft Windows multiple products | 91653 |
| CVE-2018-6789 | Exim before 4.90.1 | 50089 |
| CVE-2020-0688 | Multiple Microsoft Exchange Server | 50098 |
| CVE-2018-4939 | Adobe ColdFusion | 370874 |
| CVE-2015-4852 | Oracle WebLogic Server 10.3.6.0, 12.1.2.0, 12.1.3.0, and 12.2.1.0 | 86362, 86340 |
| CVE-2020-2555 | Oracle Coherence product of Oracle Fusion Middleware Middleware; versions 3.7.1.0, 12.1.3.0.0, 12.2.1.3.0 and 12.2.1.4.0. | 372345 |
| CVE-2019-3396 | Atlassian Confluence Server before version 6.6.12, from version 6.7.0 before 6.12.3, from version 6.13.0 before 6.13.3), and from version 6.14.0 before 6.14.2 | 13459 |
| CVE-2019-11580 | Atlassian Crowd and Crowd Data Center | 13525 |
| CVE-2020-10189 | Zoho ManageEngine Desktop Central before 10.0.474 | 372442 |
| CVE-2019-18935 | Progress Telerik UI for ASP.NET AJAX through 2019.3.1023 | 372327, 150299 |
| CVE-2020-0601 | Microsoft Windows multiple products | 91595 |
| CVE-2019-0803 | Microsoft Windows multiple products | 91522 |
| CVE-2017-6327 | Symantec Messaging Gateway before 10.6.3-267 | 11856 |
| CVE-2020-3118 | Cisco IOS XR, NCS | 316792 |
| CVE-2020-8515 | DrayTek Vigor2960 1.3.1_Beta, Vigor3900 1.4.4_Beta, and Vigor300B 1.3.3_Beta, 1.4.2.1_Beta, and 1.4.4_Beta devices | 13730 |
Detect 25 Publicly Known Vulnerabilities using VMDR
Qualys released several remote and authenticated QIDs for commonly exploited vulnerabilities. You can search for these QIDs in VMDR Dashboard by using the following QQL query:
vulnerabilities.vulnerability.cveIds: [CVE-2019-11510,CVE-2020-5902,CVE-2019-19781,CVE-2020-8193,CVE-2020-8195,CVE-2020-8196,CVE-2019-0708,CVE-2020-15505,CVE-2020-1472,CVE-2019-1040,CVE-2020-1350,CVE-2018-6789,CVE-2018-4939,CVE-2020-0688,CVE-2015-4852,CVE-2020-2555,CVE-2019-3396,CVE-2019-11580,CVE-2020-10189,CVE-2019-18935,CVE-2020-0601,CVE-2019-0803,CVE-2017-6327,CVE-2020-3118,CVE-2020-8515]
Using Qualys VMDR, customers can effectively prioritize this vulnerability for “Active Attack” RTI:
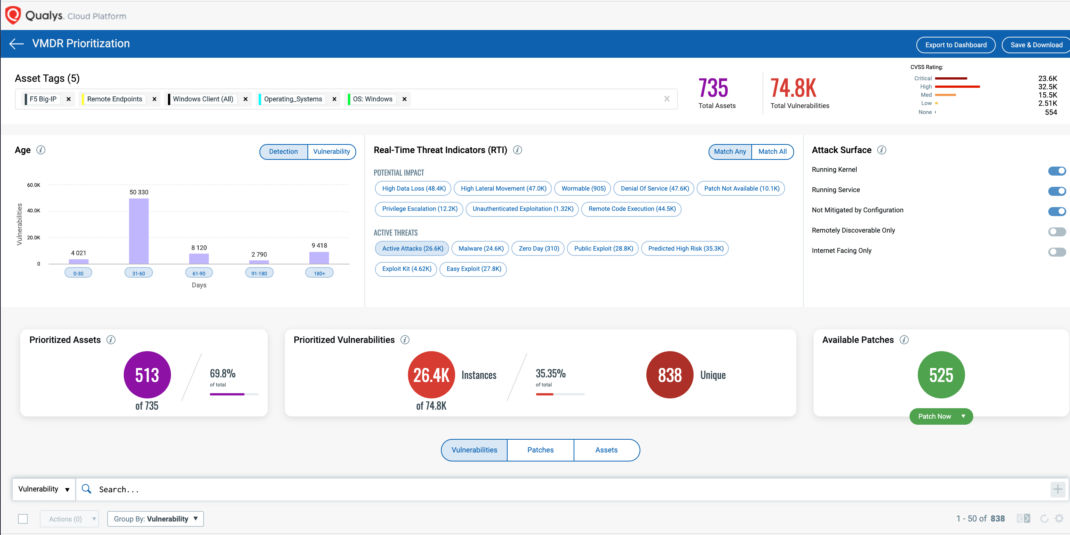
Identify Vulnerable Assets using Qualys Threat Protection
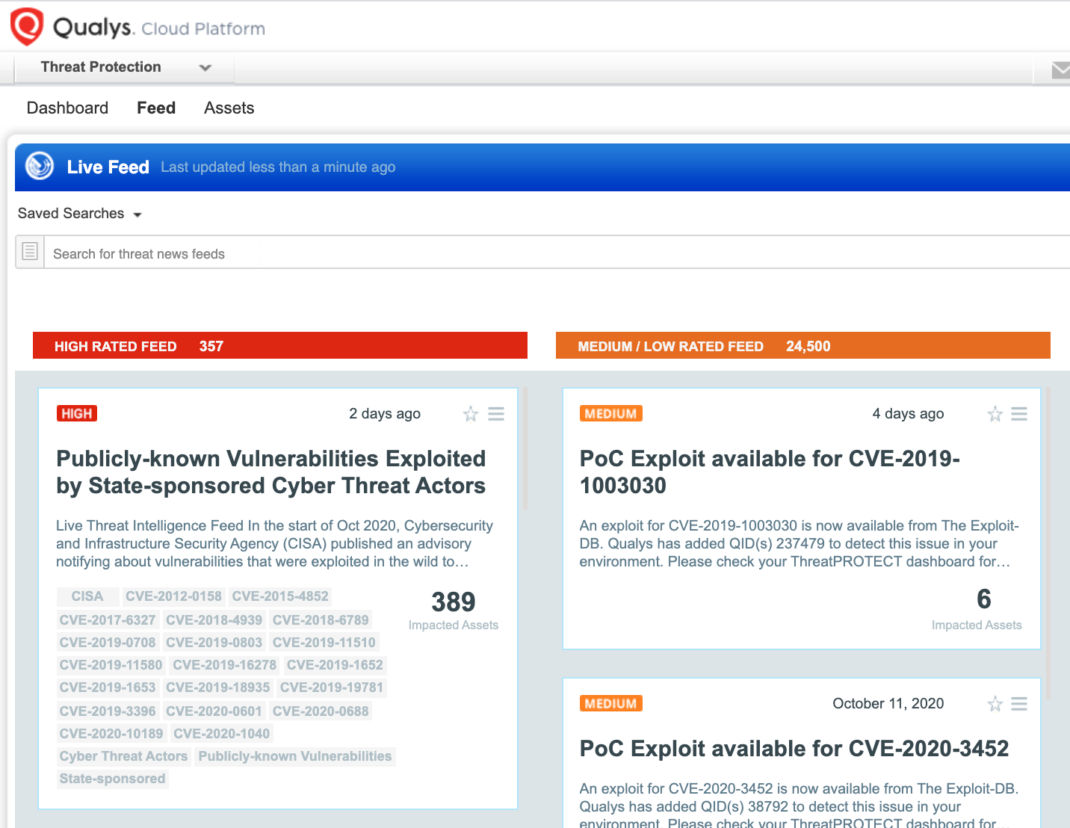
In addition, Qualys customers can locate vulnerable host through Qualys Threat Protection by simply clicking on the impacted hosts. This helps in effectively identifying and tracking this vulnerability.
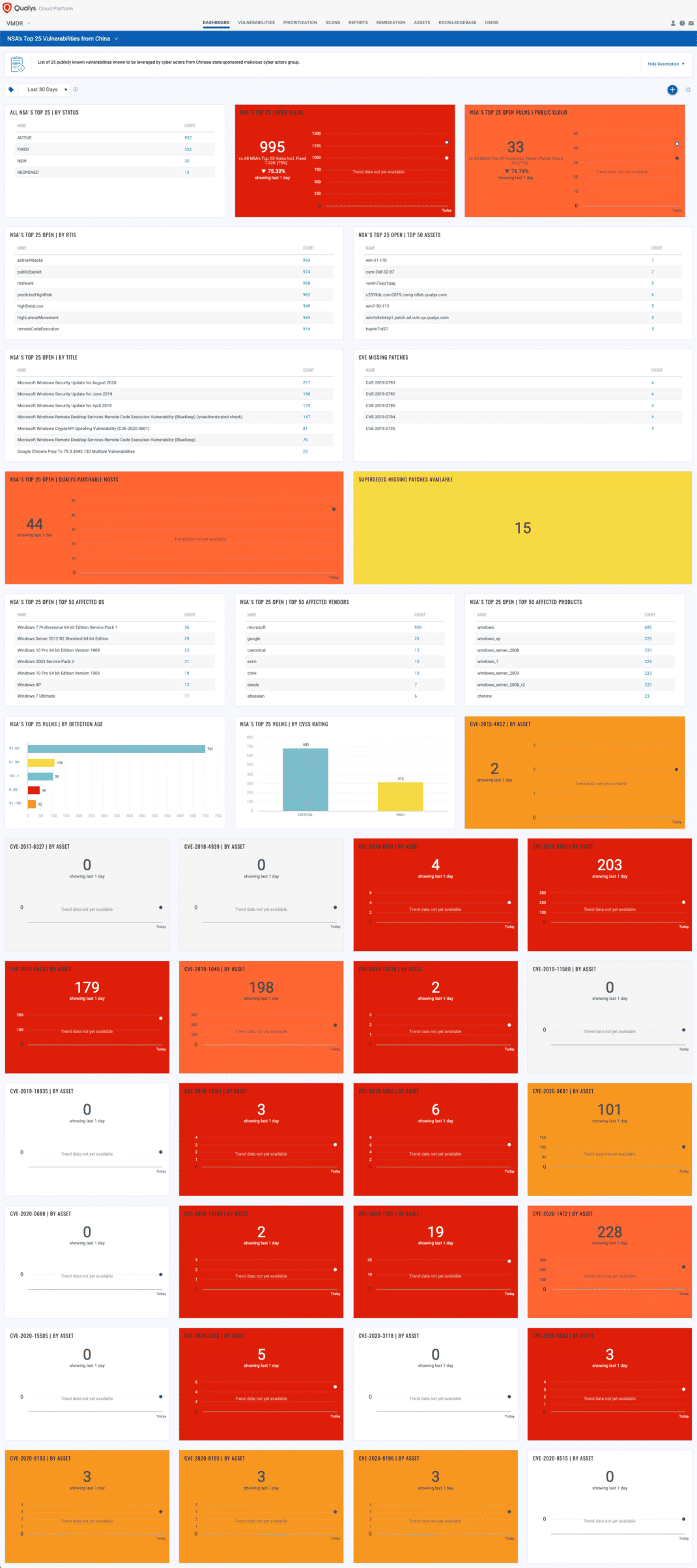
With VMDR Dashboard, you can track 25 publicly known exploited vulnerabilities, their impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of these vulnerabilities trends in your environment using the “NSA’s Top 25 Vulnerabilities from China” dashboard.
Recommendations
As guided by CISA, to protect assets from exploiting, one must do the following:
- Minimize gaps in personnel availability and consistently consume relevant threat intelligence.
- Vigilance team of an organization should keep a close eye on indications of compromise (IOCs) as well as strict reporting processes.
- Regular incident response exercises at the organizational level are always recommended as a proactive approach.
Remediation and Mitigation
- Patch systems and equipment promptly and diligently.
- Implement rigorous configuration management programs.
- Disable unnecessary ports, protocols, and services.
- Enhance monitoring of network and email traffic.
- Use protection capabilities to stop malicious activity.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching the high-priority commonly exploited vulnerabilities.

Will Qualys be providing coverage for CVE-2020-3118
Why do we not have a signature yet for CVE-2020-3118 (Cisco IOS XR, NCS) issue?
We have released following QID to address CVE-2020-3118:
QID 316792 : Cisco IOS XR Software Cisco Discovery Protocol Format String Vulnerability (cisco-sa-20200205-iosxr-cdp-rce)
You can also check for latest released Qualys QIDs and the QIDs in development – https://community.qualys.com/vulnerability-detection-pipeline/
Hello, could you check the CVE-2020-1472? I think the QID 91688 assigned is wrong, should be 91668.