Unified SaaS Application Security, Detection, and Response
Organizations are rapidly embracing Software as a Service (SaaS) applications for scalability, ease & flexibility of use, and the benefits of not using their own infrastructure. To maintain their focus on business objectives during the new ‘remote workforce normalcy’, organizations have fast-tracked the adoption of SaaS apps like Zoom, Slack, Salesforce, Box, DropBox, Google Workspace and Microsoft Office 365 for increased agility and increased collaboration between teams. On the other hand, the dynamic nature of SaaS applications and the sensitive data they contain has brought new security risks to organizations such as cybersecurity attacks which exfiltrate sensitive data and external exposure of critical data.
SaaS security should be prioritized due to the access & sensitive data in SaaS applications
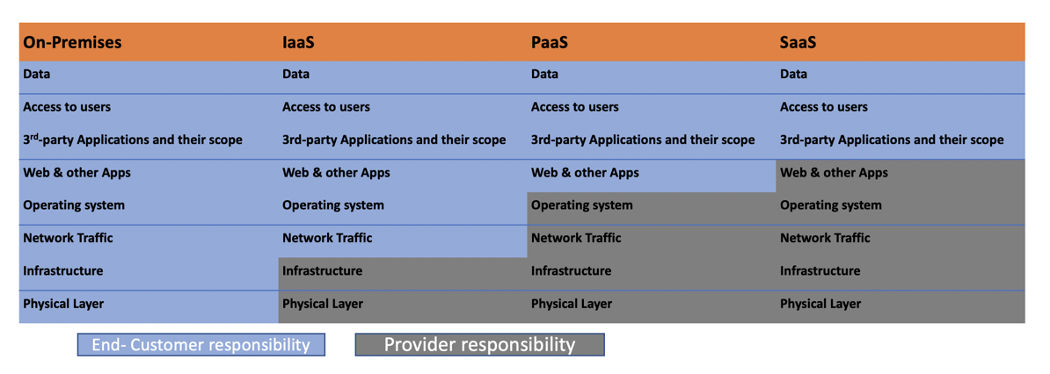
While cloud infrastructure and component security is a responsibility of cloud providers and SaaS applications are typically brought in by the business teams, the organization’s security teams still have responsibility for the data itself, plus data access, data visibility, and user management. As the core of business processes and a repository of sensitive data, SaaS applications are subject to compliance auditing and are juicy targets for attackers. Most security teams concentrate on host security at the expense of close management of data access via SaaS applications.
Take the example of a recently observed Business Email Compromise (BEC) scam: After learning about a planned wire transfer, an attacker impersonated a payment recipient by compromising the Microsoft Office 365 account on their personal device. The fraudster then supplied new payment instructions that misled the company to deposit the money into the scammer’s wallet instead of the legitimate account. Upon investigation, it was discovered that fifteen Office 365 accounts were used to register 150 domains for this BEC scam. All the domains were registered with GoDaddy’s Wild West Domains and employed a homograph technique to trick the victims. This attack method exploits closely related domains that are hard to distinguish, for example, paypal.net, paypaI.com or PayPall.com.
Another recent attack leveraged the SolarWinds Orion compromise on hosts and laterally escalated to compromise privileged accounts managed by Azure Active Directory. In this attack known as Dark Halo (FireEye tracks it as UNC2452), attackers exfiltrated the organization’s critical data by compromising privileged user accounts and their emails via misconfigurations in Office 365, such as MFA disablement, access for creation of domains and more.
Interestingly, these attack techniques are well represented by MITRE. However, to defend against such attacks consistently across their lifecycle, security teams need an automated solution that detects SaaS application weaknesses, identifies the users accessing them, and responds to potential data exposure by correlating insights with telemetry of assets.
Additionally, as SaaS applications store critical data, compliance teams are looking for a solution which can continuously audit these SaaS applications and report on industry standards such as PCI-DSS, NIST and others.
Today, organizations either must rely on native security controls provided in each SaaS solution or on Cloud Access Security Broker (CASB) point solutions to address both security & compliance of SaaS applications. But CASB focuses on intercepting the traffic for either allowing or denying access, and most SaaS security point solutions interpret only the context of users and applications, without understanding the profile of the device accessing the applications.
Introducing Qualys SSPM
Built on the FedRAMP-authorized Qualys Cloud Platform which enables vulnerability and security management for datacenter and cloud infrastructure, Qualys SSPM provides a single console for IT and Security teams to gain continuous visibility, data access control and security configuration hygiene of critical SaaS apps such as Microsoft Office 365, Zoom, Salesforce, and Google Workspace, with support for Slack and Okta coming soon. This solution includes SaaS connectors to continuously collect application, user and posture data. Start a free trial.
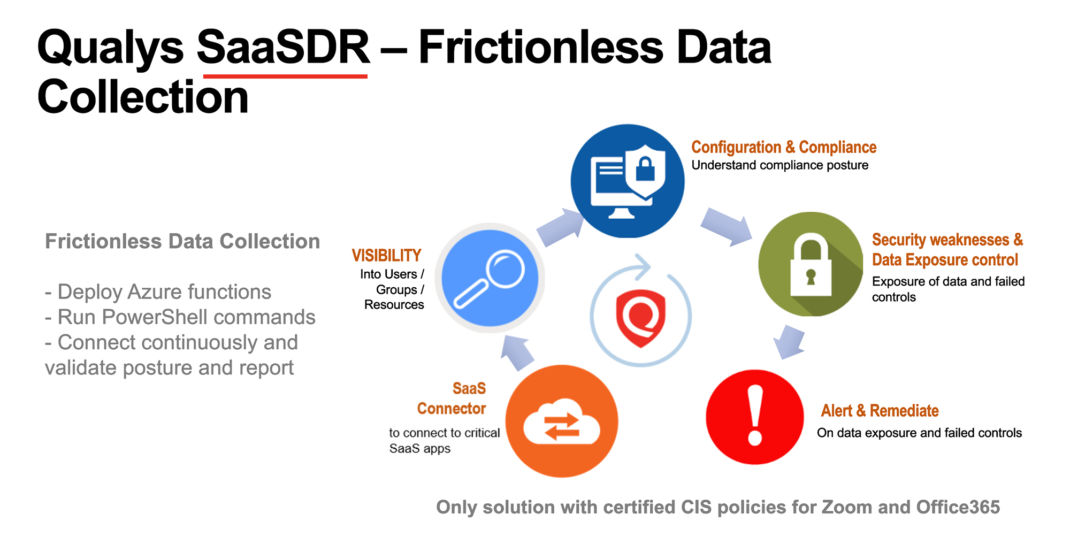
Instead of deploying an appliance or an image in the environment to collect SaaS application data, Qualys SSPM supports a ‘frictionless data collection’ approach for Office 365, where a SaaS connector collects data via native Azure functions which are deployed dynamically to run PowerShell commands and collect deeper data about misconfigurations, instead of only relying on APIs. With the intuitive and seamless deployment and configuration of a SaaS connector, security teams can immediately gain connectivity to SaaS applications on a continuous basis.
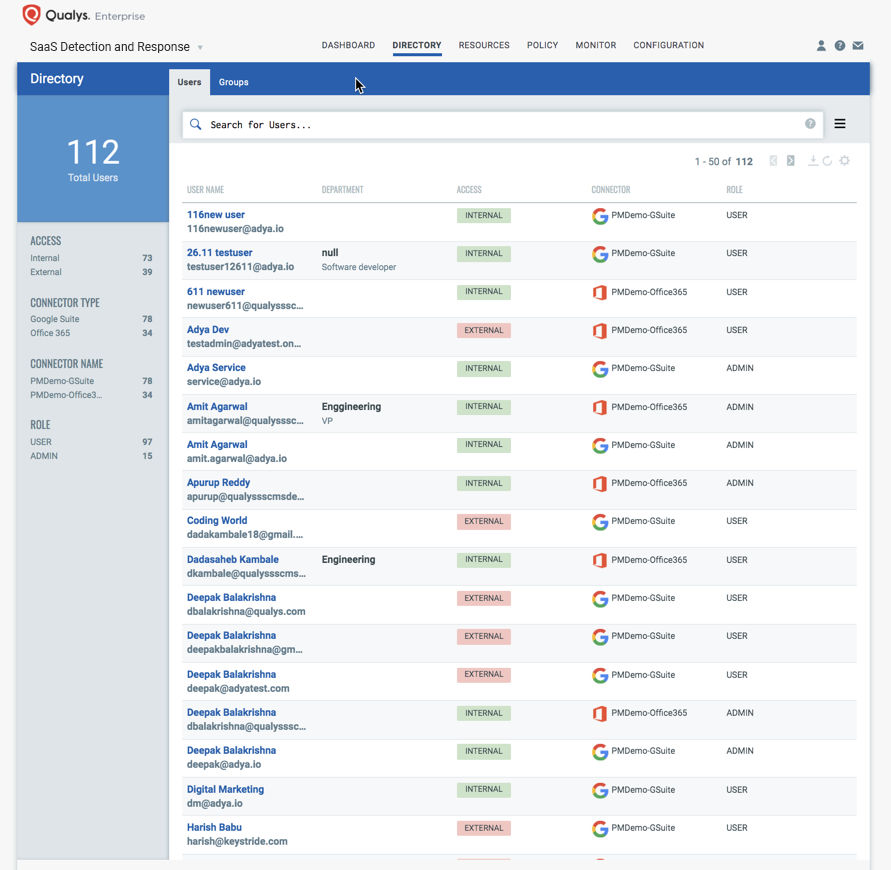
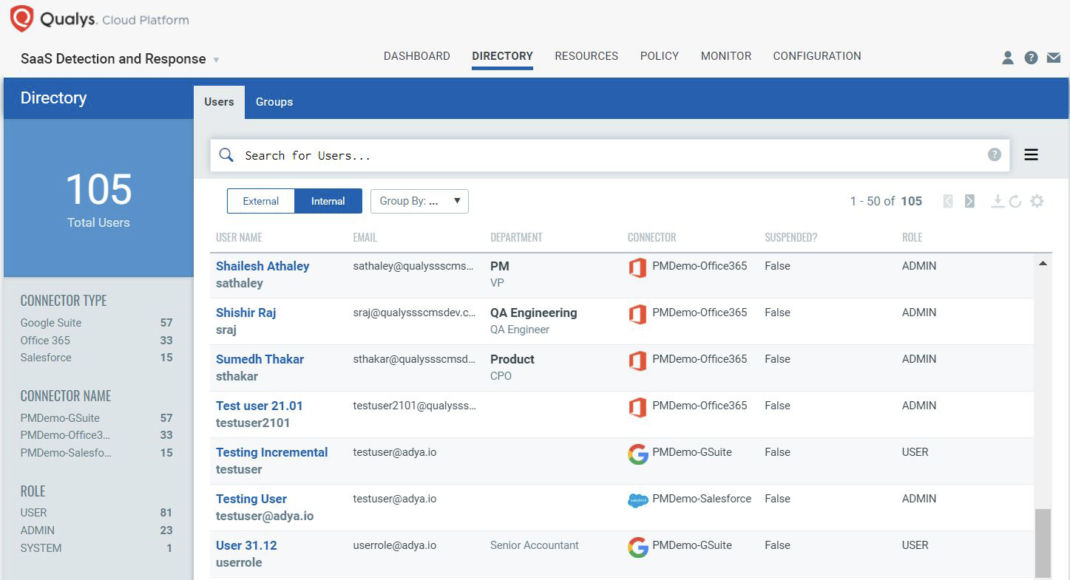
Unified visibility of users, groups correlated with their endpoints
Knowing your users, their roles and their access to SaaS applications is fundamental to continuous SaaS security. Qualys SSPM enables you:
- To inventory all user roles/groups, their membership, and access privileges in a centralized manner, addressing questions such as who has access to what applications, making sure only the required applications are given access on need-to-have basis.
- To gain continuous visibility of internal versus external users with access to applications and critical data, helping security teams monitor access enabled for contractors, ex-employees, etc.
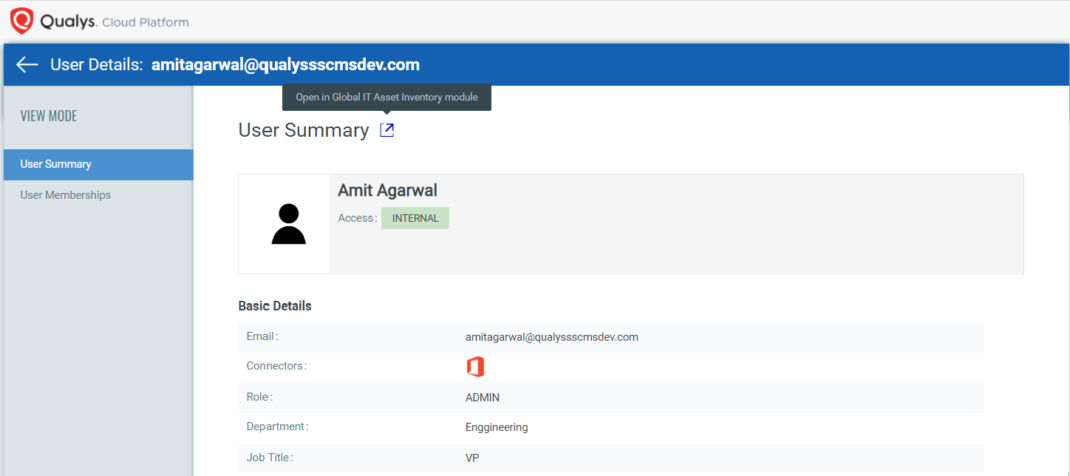
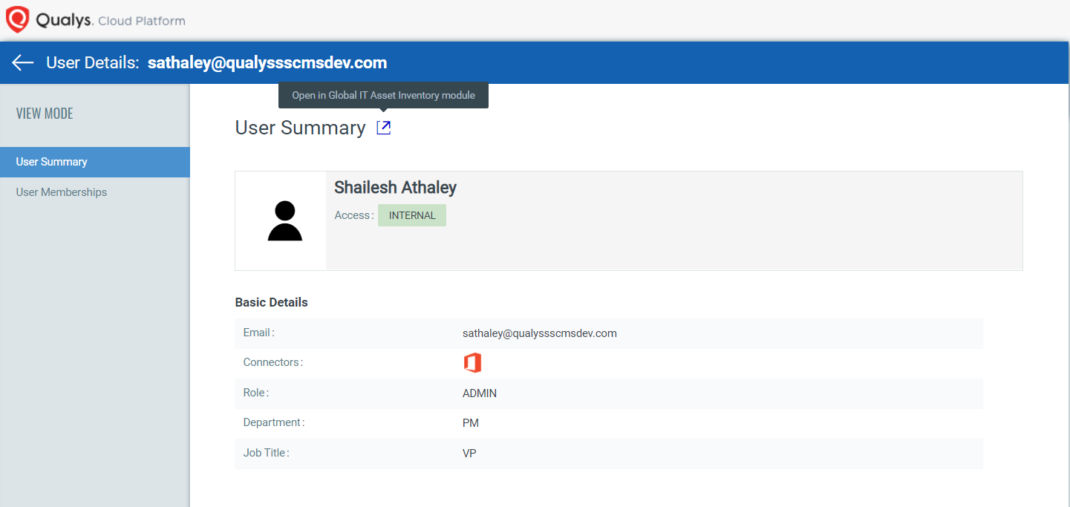
- A continuous view of users and the endpoints they are using for accessing applications. SSPM insights include SaaS application vulnerabilities, endpoint configuration hygiene, location of the asset, alerts generated by Qualys Multi-Vector EDR and File Integrity Monitoring (FIM) on assets for this user and critical data. This correlated insight of users and endpoint security posture helps security teams gain complete context of control weaknesses and potential attacks.
Insights into data access and exposure
Qualys SSPM supplies insights into application and data exposure. Using advanced correlation on the platform, security teams can prioritize and respond to suspicious user and data exposure activities by natively correlating endpoint security insights generated from Qualys VMDR, FIM and EDR. At a granular level, you gain:
- Continuous inventory of all files/folders holding your sensitive data in SaaS applications with visibility into access to internal versus external users
- Granular insights into external users having access to data, along with permission-level information for detecting data leakage
- Visibility into internal users exposing data outside the organization for detecting potential inside threats
- Unified inventory of all 3rd-party SaaS apps installed across your organization along with usage metadata to understand most-used versus underused applications for SaaS cost analysis
- Intelligent, correlated insights of SaaS applications with their vulnerabilities data mapped from Qualys VMDR, enabling security teams to prioritize patching and hardening for SaaS applications
- Heuristic insights into third-party apps that are used by employees using their company credentials and granting these apps potentially dangerous permissions (aka “scopes”)
- Visibility into exposure of Zoom meetings and recordings and data files shared in your organization, with Zoom security posture management
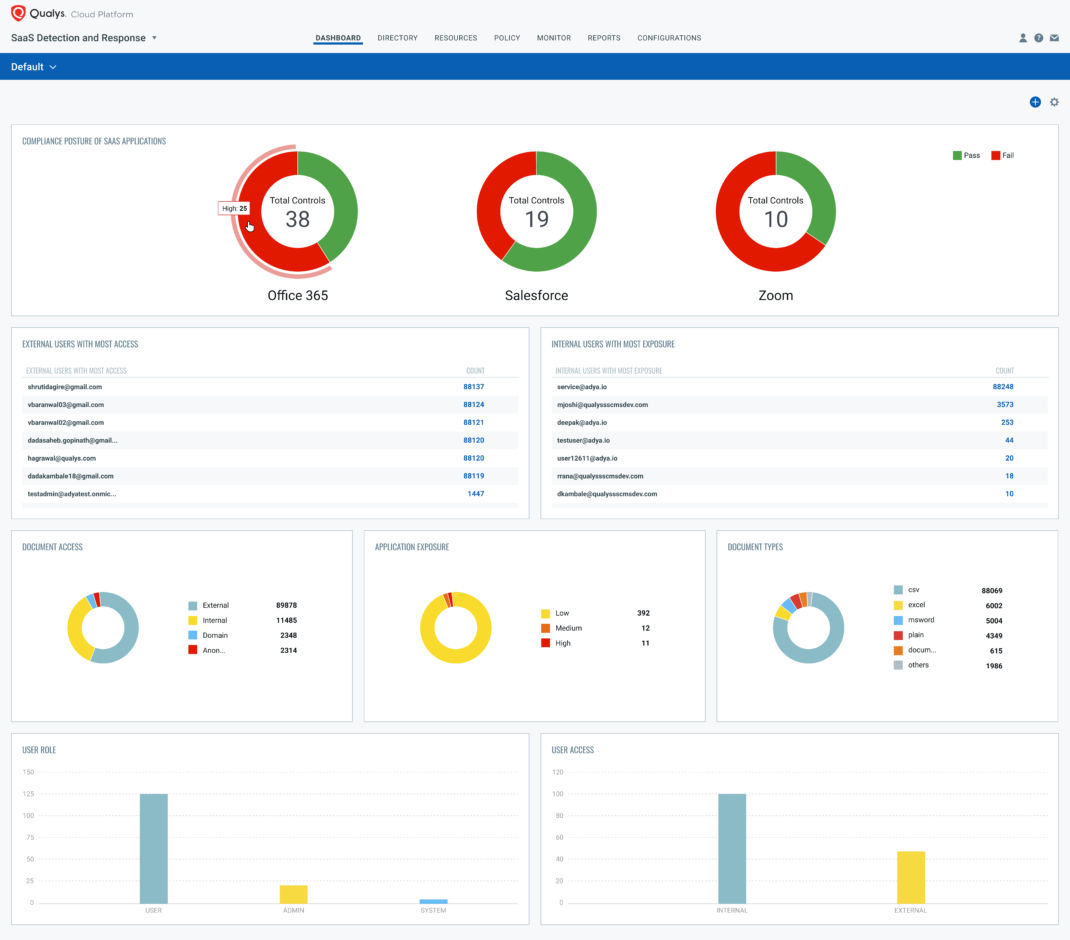
SaaS security posture management and compliance
As CASB (Cloud Access Security Broker) and siloed SaaS security solutions struggle to go beyond user and access management, the key to protect against state-of-the-art cybersecurity attacks like SolarWinds, business email and data compromise is detection and monitoring of security weaknesses of SaaS applications, especially the vulnerabilities and misconfigurations leveraged by attack techniques.
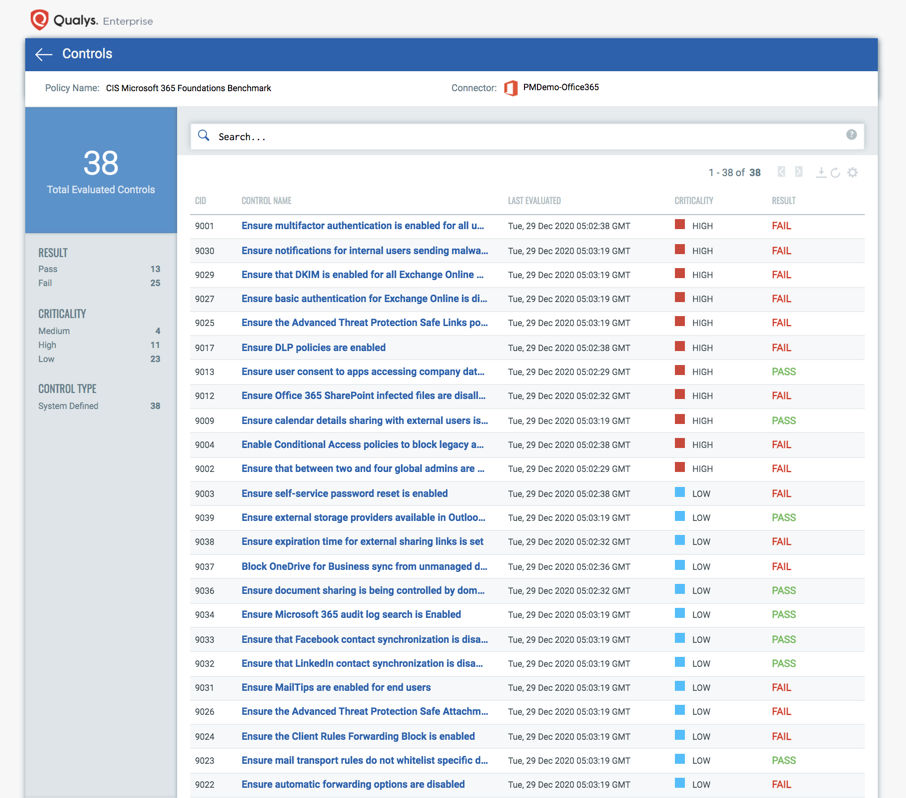
Qualys SSPM enables continuous security posture assessment of Office 365 via the CIS (Center for Internet Security) certified policy for Office, along with automated security configuration assessment for Zoom, Salesforce and Google Workspace based on the analysis of all security weaknesses, critical vulnerabilities, exploits leveraged by attackers in historical attacks as well as security assessment based on the MITRE ATT&CK framework. This security posture assessment enables:
- Automated alerting when critical security misconfigurations are detected, such as disabled Multi-Factor Authentication (MFA), disabled malware scanning for file downloads, or automatic mail forwarding not disabled during off hours
- Detailed recommendation reports with remediation steps for your security and IT teams
- Auditing and reporting on compliance with industry standards such as PCI-DSS, NIST, CIS, etc. with the ability to instantly search for critical failures and prioritize them based on control criticality or their impact on data exposure
Move from siloed solutions to a holistic platform approach for context-driven detection & response
Finally, key for detection and prioritized response to suspicious data exposure activities and anomalies are the full context of the user and endpoint activities. As siloed SaaS posture management and CASB solutions focus only on SaaS applications and user activities to detect attacks, they lack the full context to analyze potential attacks and prioritize responses accurately. This leads to an incomplete picture and a high rate of false positives and negatives, requiring organizations to use multiple point solutions and large incident response teams.
With the FedRAMP-authorized Qualys Cloud Platform, security teams can natively correlate data insights from SSPM such as user access and data exposure from SaaS applications, with security telemetry generated for the user host accessing SaaS applications such as vulnerabilities and misconfigurations on the host, FIM and EDR alerts generated for this user, unusual location, or time of the access. This unified picture of risk context helps security teams pinpoint to the potential security finding and prioritize the right response, eliminating the need for additional point solutions which require data to be normalized and pushed to yet another data lake tool for full context of security.
With SaaS applications, user, file, and posture data indexed in Elasticsearch along with endpoint telemetry, the Qualys Cloud Platform makes it easy to search, filter, and correlate data for the full context of the potential attack on sensitive data and security posture.
A complete solution in a single console
As adoption of SaaS applications grows exponentially and increase attack surface and data exposure risks, security teams are looking for a solution, which goes beyond traditional CASB to provide inventory and security for their SaaS technology stack. Qualys extends the power of its FedRAMP-authorized platform to SaaS technology, for:
- Visibility into SaaS apps, users and their access
- Data exposure monitoring
- Risk view of third-party apps installed via Google Workspace and Microsoft Office 365, based on their privileges
- Security posture & compliance management for continuous auditing against CIS benchmarks, PCI-DSS, ISO, NIST standards
- Context-driven security by combining user activities with endpoint security telemetry.