The Convergence of Endpoint Protection with Detection & Response
By almost every account, trend, or metric, the cybersecurity threat landscape is getting worse year over year. According to Qualys Labs, 2020 saw the highest number of vulnerabilities ever recorded. The average time it takes to patch vulnerabilities is months (not weeks or days). Ransomware payouts are growing in terms of amount and frequency. We’re seeing a record number of data breaches. Billions of cumulative records have been compromised by those breaches. It takes companies 6 months to identify a breach and over 2 months to contain it.
To accomplish their actions on objectives, the bad guys will utilize any and every tactic at their disposal to execute their attack. To deliver malware onto an endpoint, a threat actor could utilize social engineering via a phishing attack, exploit an unpatched vulnerability, take advantage of a system misconfiguration, piggyback of an undetected Trojan, or any of myriad techniques.
History of Siloed Endpoint Security Point Products
Meanwhile, cybersecurity products are oftentimes siloed or myopic in their ability to protect and respond to threats in a holistic manner. The problem is exacerbated by the fact that point products are often designed and architected to solve one specific issue and not the problem at large.
We’ve seen many examples of this throughout the history of endpoint security. What is known today as Endpoint Protection Products (EPP) is really an amalgamation of a bunch of point products.
- Antivirus was originally created to only detect nefarious threats like parasitic infectors, worms, and trojans.
- Anti-Spyware/Adware came onto the scene in the early 2000s to address a new trend in the threat landscape. It was eventually merged with antivirus as a feature to detect Potentially Unwanted Applications. The two combined became anti-malware.
- Host Intrusion Prevention System (HIPS) was once a point product that monitored endpoint activity for suspicious behavior and memory exploitation. Once it was absorbed by anti-malware products, its features were broken up and renamed “behavioral protection” and “memory protection.”
- Host-Based Firewall was once a product that was sold separately. Now it comes standard with most operating systems while a subset of its protection capabilities became known as “network protection” in EPP.
- Application Control was a point product that only allowed known good files to run, which was the opposite approach as anti-malware which only blocks known bad. Now it’s a whitelisting feature of EPP.
Even after combining all these capabilities together, EPP struggled to keep pace with the threat landscape. A new product was conceived dubbed Endpoint Detection and Response (EDR). EDR acts like a flight data recorder to collect events and telemetry from the endpoint to identify suspicious objects and activities.
Qualys Multi-Vector EDR Integrates Anti-Malware Capabilities
Given the history of the expansion and contraction of endpoint security products, combining EPP with EDR was an inevitability. Qualys Multi-Vector EDR has integrated endpoint protection capabilities to deliver more holistic security to your endpoints:
- Anti-Malware proactively protects endpoints against known threats while EDR augments those detection capabilities by capturing endpoint activity and telemetry to detect and respond to unknown zero-day threats and living-off-the-land attacks.
- When there is a symptom of a compromise or attack, EDR provides more in-depth visibility and contextual enrichment for incident responders and threat hunters to get a complete picture of the endpoint to do root cause analysis.
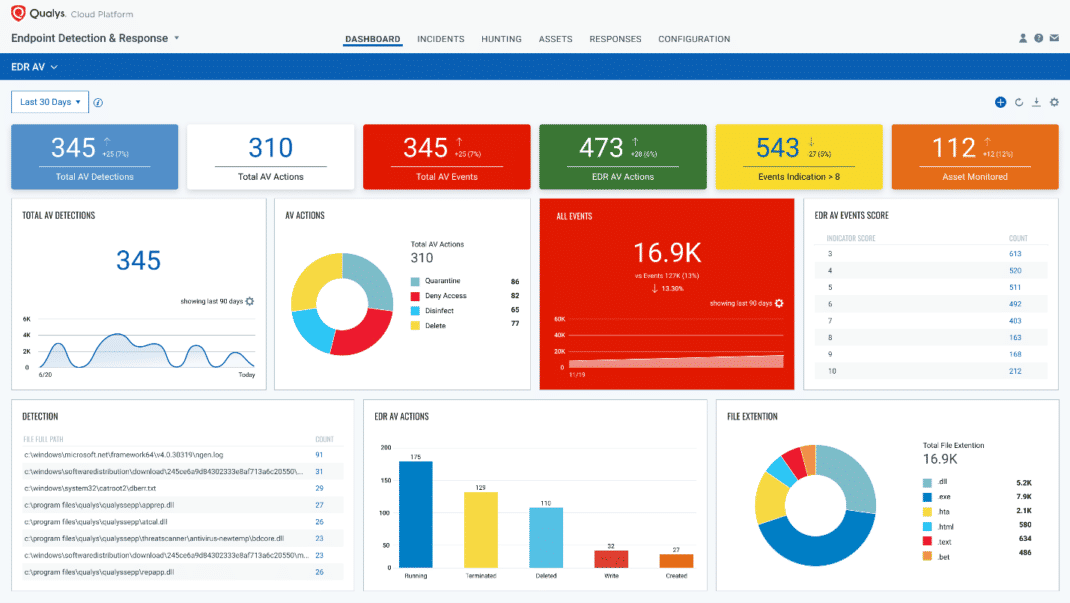
Optimize your Security Posture with Continuous Monitoring & Assessment
To implement continuous monitoring and assessment of endpoints, Security Operations Teams should follow these steps:
- Predict – In order to fully protect our environment, we must have comprehensive situational awareness of our attack surface. To understand that baseline, we must have a complete catalog of the following: devices, operating systems, applications, users, cloud, and container.
Qualys Global IT Asset Inventory, Vulnerability Management, Detection, and Response, and Container Security provide this complete picture. Without it, we will have blind spots, which could be potential attack surfaces. - Prevent – After fully understanding our attack surface, we become aware of our attack vectors: vulnerabilities, exploits, misconfigurations, compromised credentials, etc. Qualys Patch Management, Policy Compliance, and File Integrity Monitoring help prevent and minimize these attack vectors to increase companies’ security hygiene.
- Detect – Even with perfect security hygiene, inevitably threats will fall through the cracks due to zero-day vulnerabilities, zero-day malware, insider threats, and social engineering attacks. This is where endpoint security comes into the picture. EPP is valuable in identifying and protecting against known threats, but with the exponential explosion of the threat landscape, unknown threats, living-off-the-land attacks, and fileless malware often go unnoticed. EDR helps catch what EPP misses while giving context to suspicious activity monitored on endpoints.
- Respond – Detection of a single threat or indicator of compromise (IOC) is often a symptom of a larger attack. Incident responders and threat hunters need access to real-time endpoint telemetry to understand the full scope of an attack to properly remediate. Qualys Multi-Vector EDR provides protection, detection, and response capabilities by using a variety of detection capabilities: real-time anti-malware technology, anti-exploit memory protection, endpoint telemetry and correlation that identifies suspicious & malicious behavior, industry-leading threat intelligence, and Mitre ATT&CK tactics & techniques.
- Learn – One of the most important (yet overlooked) steps to improving our overall cybersecurity posture is taking the lessons learned from a threat incident or threat hunt, applying the findings from root cause analysis, then turning that new knowledge into actionable mitigating steps that will prevent future incidents across the entire environment.
Qualys’ Cloud Platform Delivers Holistic Protection Against Multi-Vector Threats
Built natively on top of the Qualys Cloud Platform, Multi-Vector EDR provides a complete picture of endpoints. When combined with the perspectives of asset inventory, vulnerability detection, patch protection, and compliance, the Qualys Cloud Platform provides visibility in breadth and depth to protect against today’s sophisticated attacks.
Qualys Multi-Vector EDR with its new integrated anti-malware capabilities are deployable to any endpoint using the Qualys Cloud Agent, a single agent that delivers detection and remediation for malware, vulnerabilities, and compliance. The Qualys cloud management console provides a single pane of glass to configure, analyze, query, and visualize all your cybersecurity needs.
Beta Release
Sign up for the Qualys Multi-Vector EDR with Integrated Anti-Malware Beta to detect and block advanced threats in real time.
Webinar
Join our webinar on May 26 to see real-time malware protection in action.
Black Hat Featured Session
For insights into the problem of multi-vector attacks and why they complicate defense and gives attackers an advantage, join us for the presentation titled “Why are the bad guys winning?” at Black Hat Asia 2021 Virtual.