Reinforce Defense with File Reputation and Trusted Source Intelligence in Qualys FIM
Monitoring change events in the file system is both a crucial aspect of security and a critical compliance requirement. A file integrity monitoring tool functions as an essential layer of defense to identify illicit activities across critical system files and registries, diagnose changes, and send alerts, so that such actions may be prevented from disrupting your IT environment. However, due to the shortcomings in traditional FIM tools, enterprises usually fail to achieve these requirements.
Challenges in Traditional FIM Solutions
Organizations using legacy FIM tools are commonly challenged by alert fatigue and the lack of threat intelligence to differentiate between malicious and benign changes.
Inability to Suppress False Alarms
Hundreds or thousands of events are generated during an update, upgrade, or patching activity, making it impossible to analyze all the events and to verify if patches are coming from a trusted source. This desensitizes SOC teams and compliance auditors, often causing them to miss crucial events, or on occasion even leading them to turn the alerts off.
Inability to Identify Malicious or Suspicious Changes
Traditional FIM solutions may provide the basic details about a change activity. A few of them may even provide the ‘who-data’ around the change, but what they fail to provide is the reputation score of the file dropped on the asset. Once a malicious file makes way into your system, it can rapidly infect your network, leaving your infrastructure completely vulnerable.
How Qualys Can Help You
Qualys File Integrity Monitoring has introduced two new groundbreaking features that add context to the change events in your file system – File Reputation Status and Trusted Source.
These features provide users with real-time event enrichment to quickly identify malicious or suspicious changes and whitelist trusted changes, which primarily helps you with:
- Noise control: With “Trusted Source Status”, user can easily identify the good changes due to patches and security updates, and whitelist them.
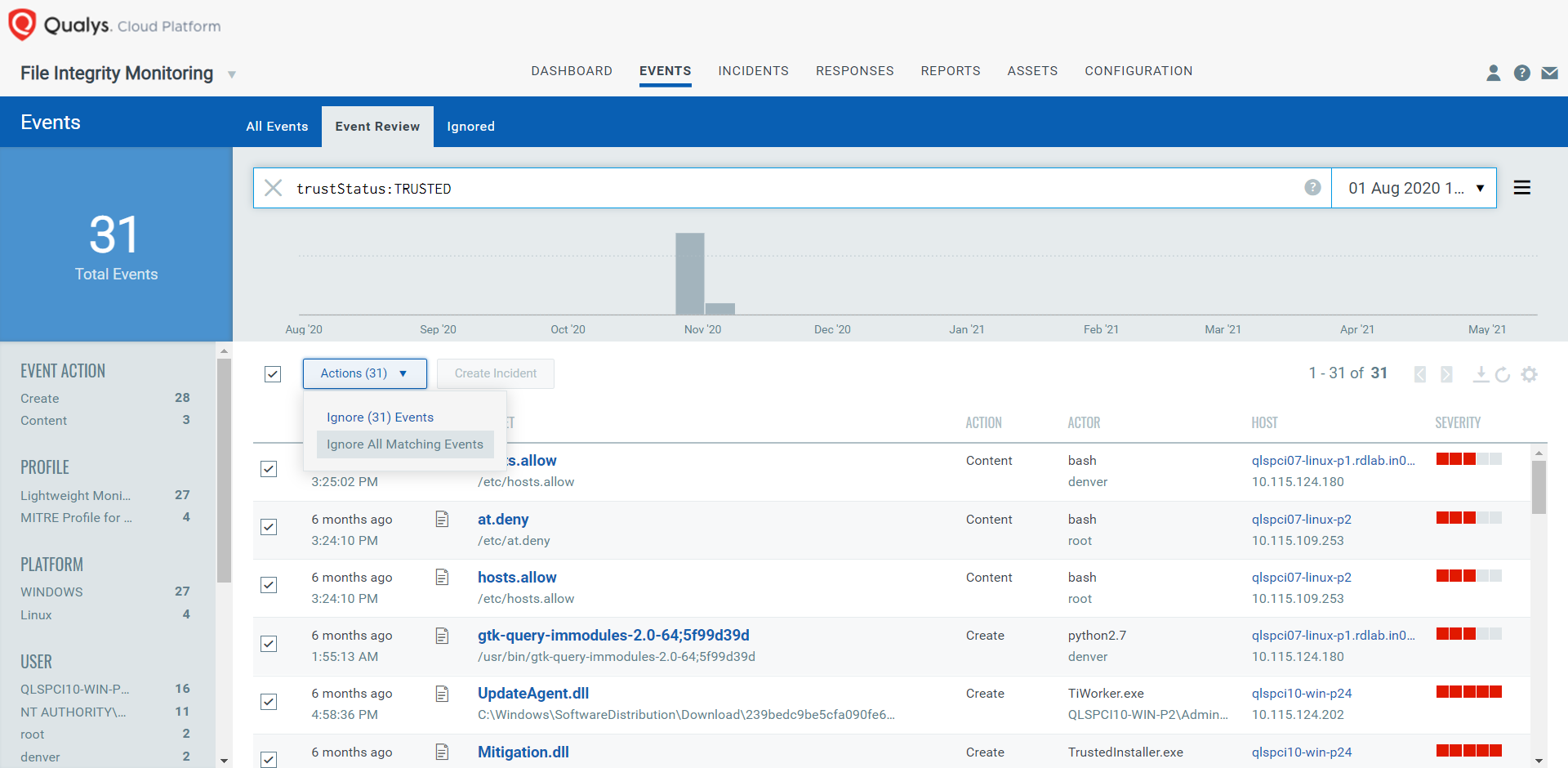
- Event prioritization: With “File Reputation Status”, user can identify if the change on the system is malicious or suspicious, and take necessary action to restrain the attack.
Note: For Windows, these features are applicable for PE files only and for Linux, all types of files are supported.
Filter, Review and Analyse the File Changes
These new features are completely automated built-in capabilities. As soon as an event is sent to the Qualys Cloud Platform, it gets enriched with Qualys threat intelligence. All you need to do is execute the right query to fetch the results.
For example,
(reputationStatus:MALICIOUS or reputationStatus:SUSPICIOUS) and trustStatus:UNAVAILABLE
This query would list all the events whose reputation status is malicious or suspicious and the trust status is unavailable.
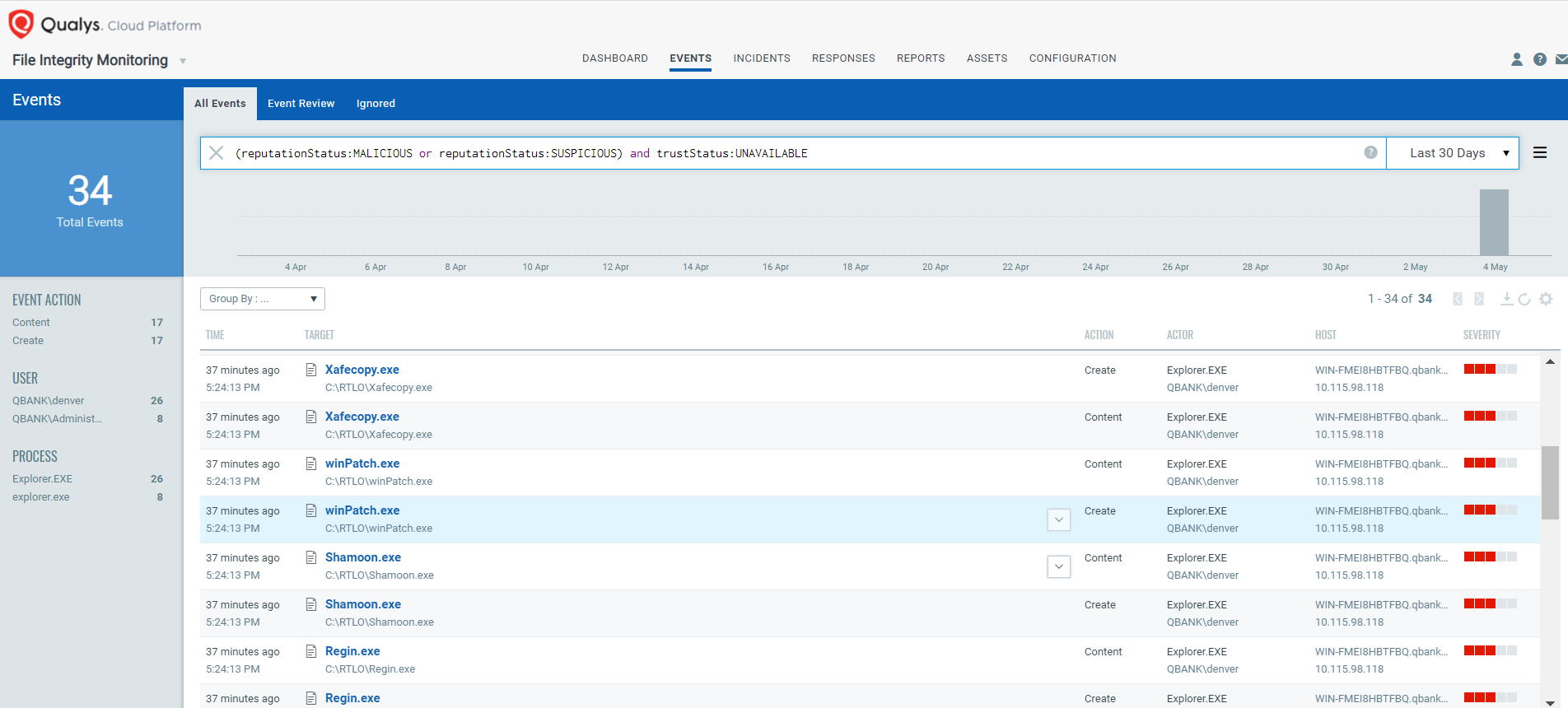
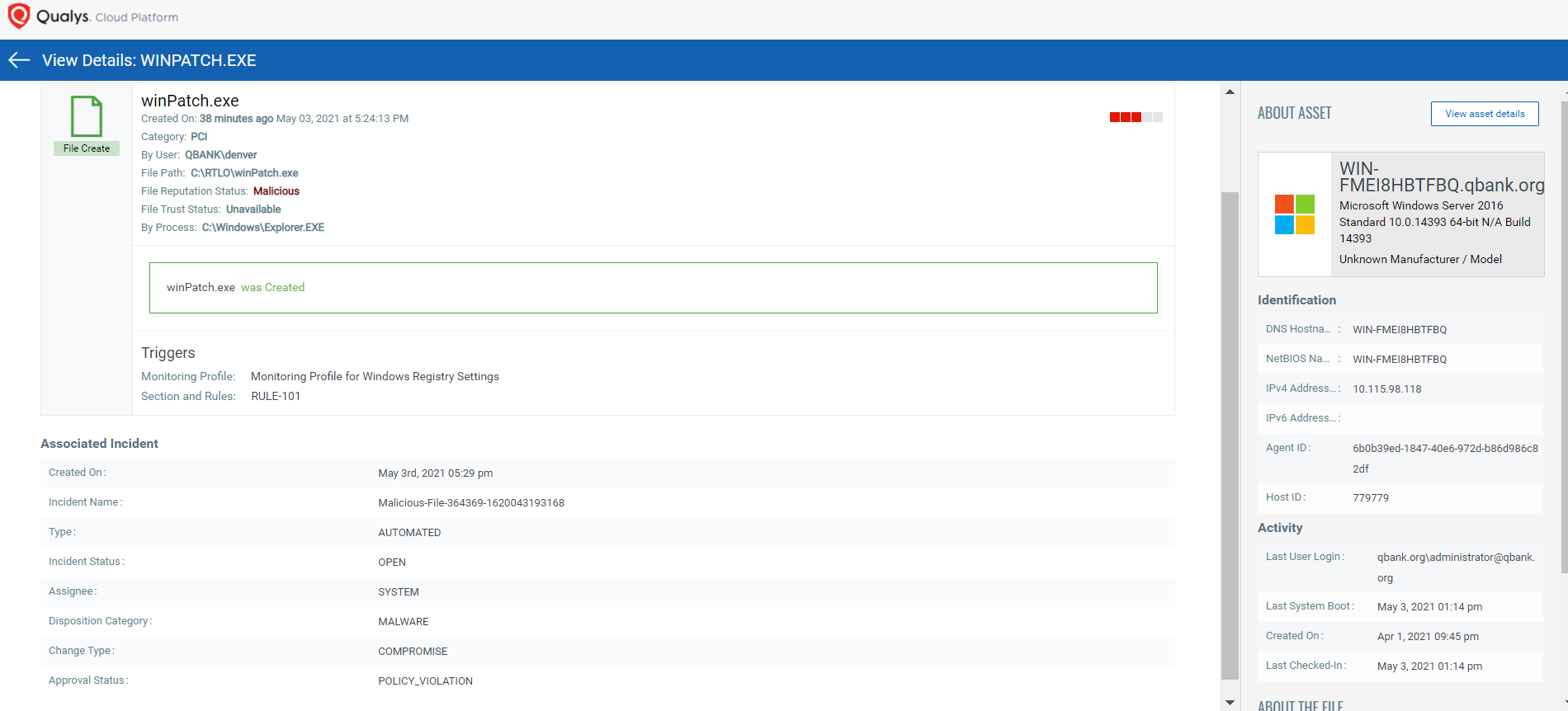
Granular Event Details
Comprehensive event details are captured when a file is dropped on a monitored asset. These details are comprised of who-data, reputation status and trust status.
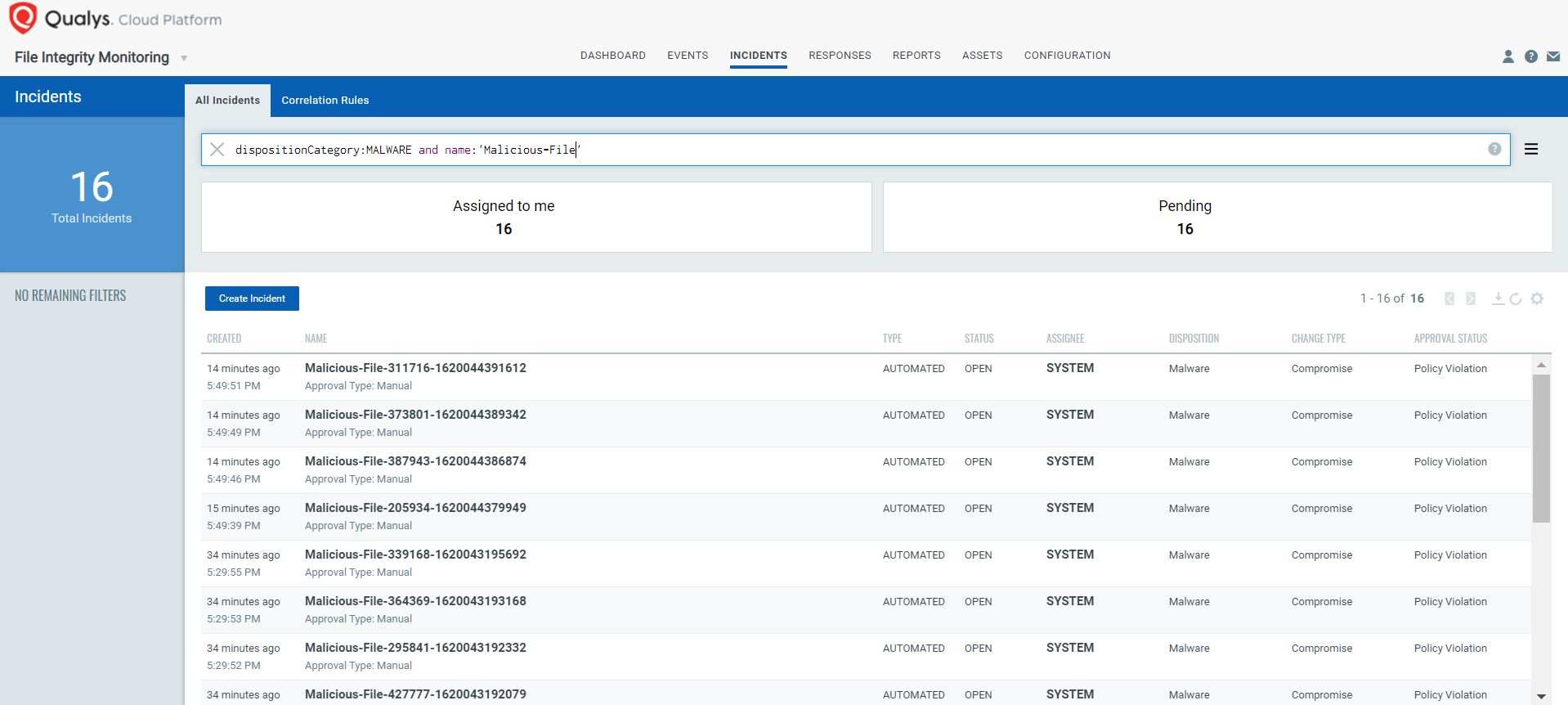
Automated Incident Generation for Malicious Changes
Qualys has designed this feature in such a way that automated incidents are generated upon each malicious change.
When Qualys FIM identifies the file reputation status as “Malicious,” an incident is automatically created with the following details:
- Disposition: Malware
- Change Type: Compromise
- Approval Status: Policy Violation
- Comment: Malicious change detected on the system
Report or Push Data to an External Data Lake
Export to the ELK Stack
Qualys FIM APIs are devised to enable easy custom integrations. The Rich FIM API set produces data in well-defined and structured JSON format which can be easily exported to the ELK stack.
Native Integration with Splunk
The Qualys App for Splunk Enterprise with TA provides a dashboard for Qualys FIM events data. It pulls and indexes the data to produce dashboards and reports. The dashboard gives quick information bites on total changes, events by severity, file and directory changes by change action. It also has widgets to show you top changes by user, process and operating system. You also have options to search for Qualys FIM events, ignored events and incidents.
Manage Alerts for Better Response
With the inclusion of these two powerful new capabilities, Qualys ensures that alert redundancy no longer attributes to security lapses in your IT environment. The Trusted Source and File Reputation filters contextualize alerts for security teams, enable easy classification of good and bad changes, and help in successfully mitigating alert fatigue – marking Qualys FIM as a robust addition to your security repertoire.
Resources
- Learn more about Qualys File Integrity Monitoring
- For questions, please contact your TAM or Qualys Technical Support
- Try Qualys FIM yourself as part of a free 30-day Qualys trial