Kaseya REvil Ransomware Attack (CVE-2021-30116) – Automatically Discover and Prioritize Using Qualys VMDR®

On July 2, 2021, Kaseya announced its software had been compromised and was being used to attack the IT infrastructure of its customers. The REvil ransomware attack leveraged multiple zero-day vulnerabilities in Kaseya’s VSA (Virtual System/Server Administrator) product that helps Kaseya customers to monitor and manage their infrastructure. To deploy ransomware payloads on the systems of Kaseya customers and their clients, the REvil operators exploited zero-day vulnerability CVE-2021-30116.
REvil ransomware (also known as Sodinokibi) is ransomware-as-a-service (RaaS), meaning an attacker distributes the licensed copy of this ransomware over the internet and the ransom is split between the developers. After an attack, REvil would threaten to publish the information on their page ‘Happy Blog’ unless the ransom is received.
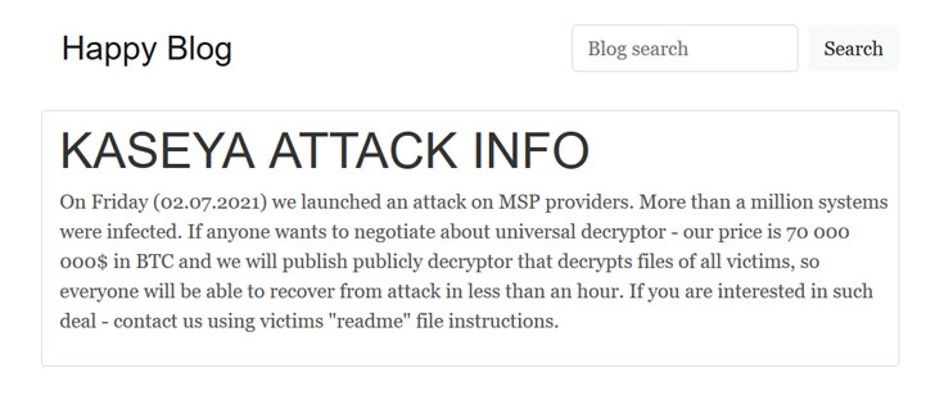
The REvil ransomware group has demanded a $70 million payment to provide a universal decryptor tool to unlock the files corrupted by REvil ransomware.
REvil’s attacks on Kaseya VSA servers have led to outages in unexpected places, such as supermarket chains in Sweden, kindergartens in New Zealand, and some public administration offices in Romania. In a message posted on their dark web blog, the REvil gang officially took credit for the attack for the first time and claimed they locked more than one million systems during the Kaseya incident.
On July 4, CISA and FBI published an advisory to respond to REvil attack and have urged users to download the Kaseya VSA Detection Tool that determines if any indicators of compromise are present on system.
Kaseya is sharing regular updates on their website and believes that this has been localized to a very small number of on-premises customers only.
Identification of Assets using Qualys VMDR
The first step in managing vulnerabilities and reducing risk is identification of assets. Qualys VMDR makes it easy to identify systems with Kaseya installed.
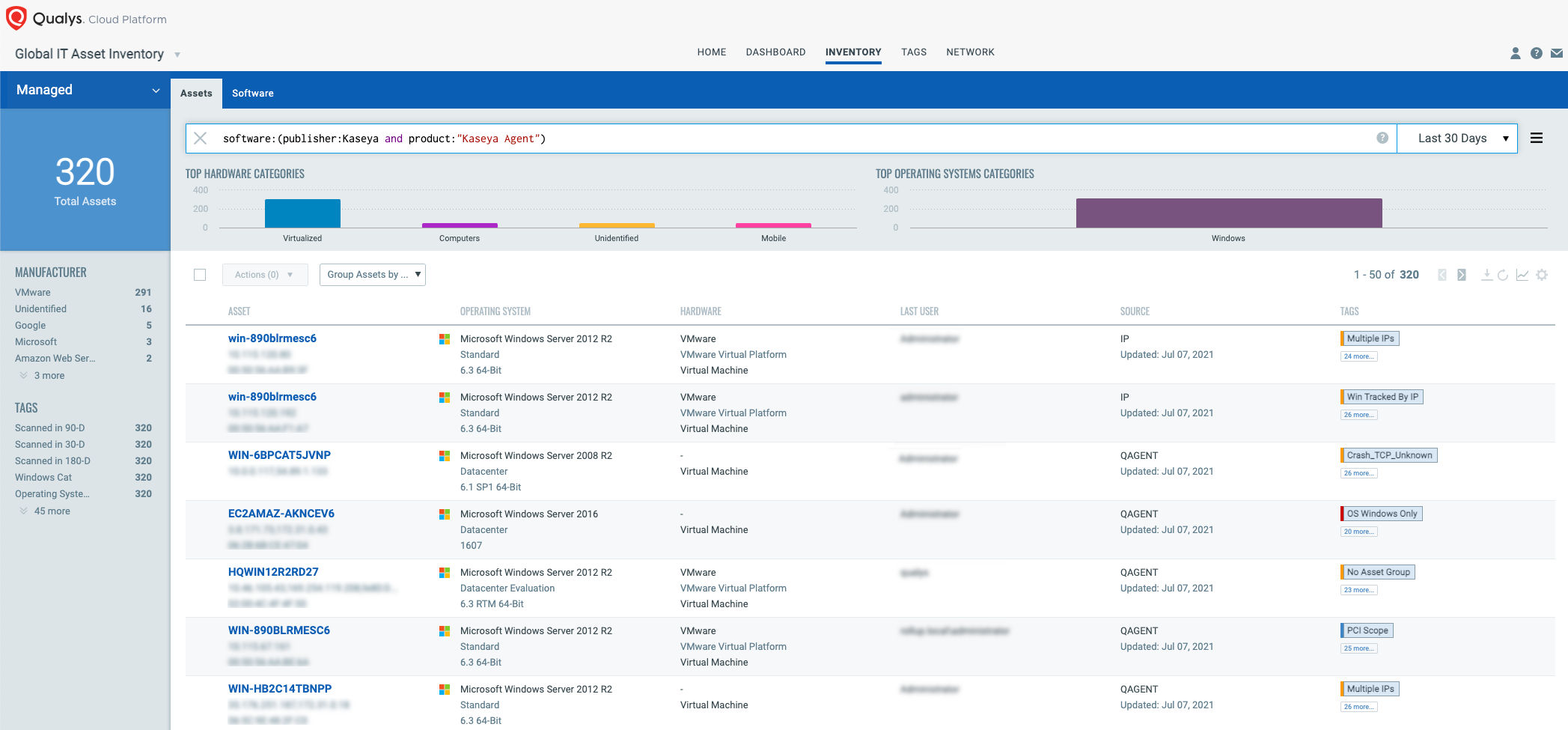
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “REvil ransomware”. This helps in automatically grouping existing hosts with ransomware as well as any new systems that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover Kaseya VSA Vulnerability
Now that hosts with REvil Ransomware are identified, you want to detect which of these assets have flagged this vulnerability. Qualys VMDR automatically detects new vulnerabilities like Kaseya VSA based on the always updated Knowledgebase.
Qualys has released an IG (information gathered) QID to detect the presence of Kaseya VSA.
You can see all your impacted hosts for this vulnerability tagged with the ‘REvil Ransomware” asset tag in the vulnerabilities view by using this QQL query:
vulnerabilities.vulnerability.qid: 48187
This will return a list of all hosts that have Kaseya VSA installed.
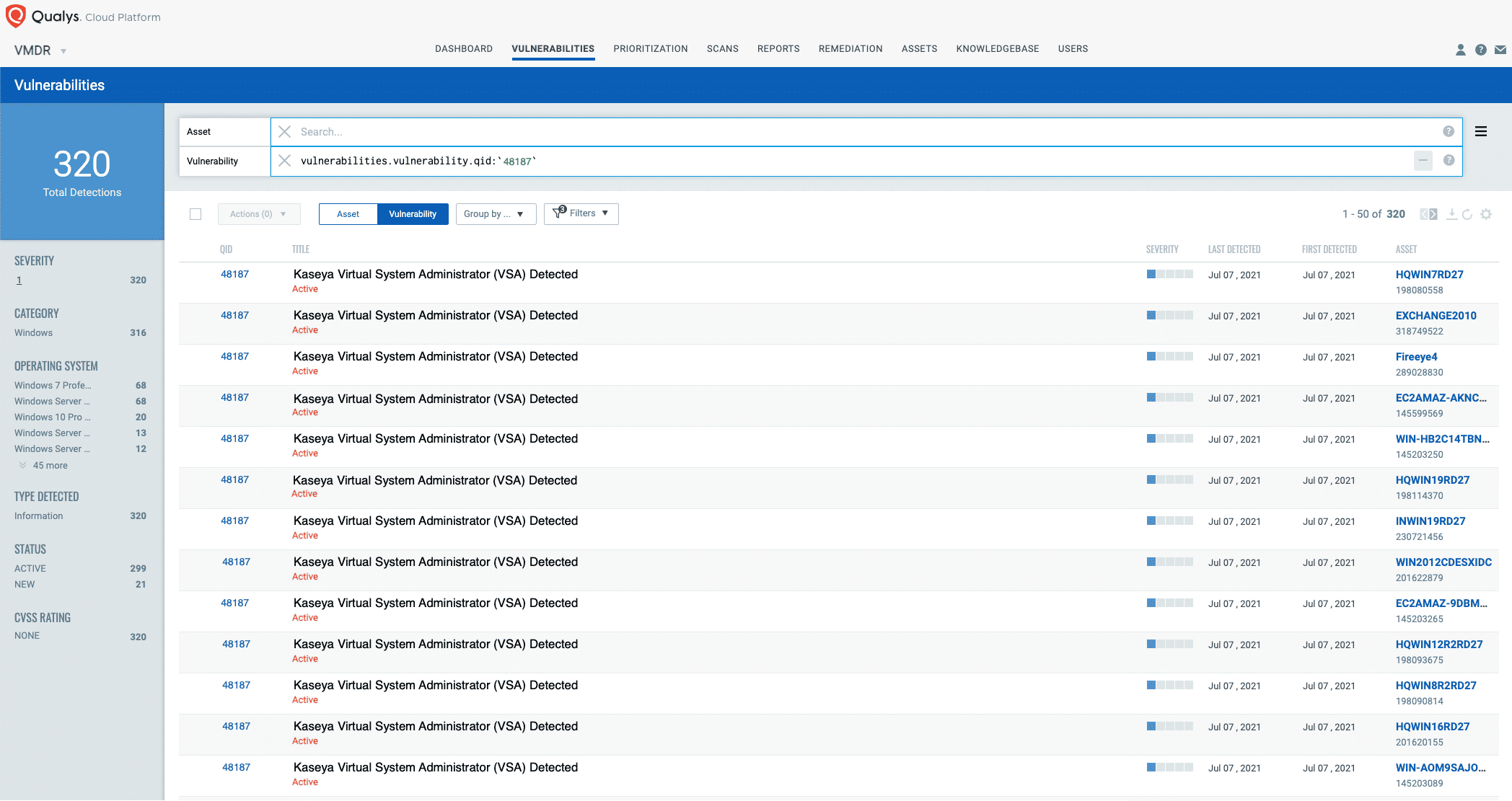
IG QID: 48187 is available in signature version VULNSIGS-2.5.226-3 and above and can be detected remotely.
VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
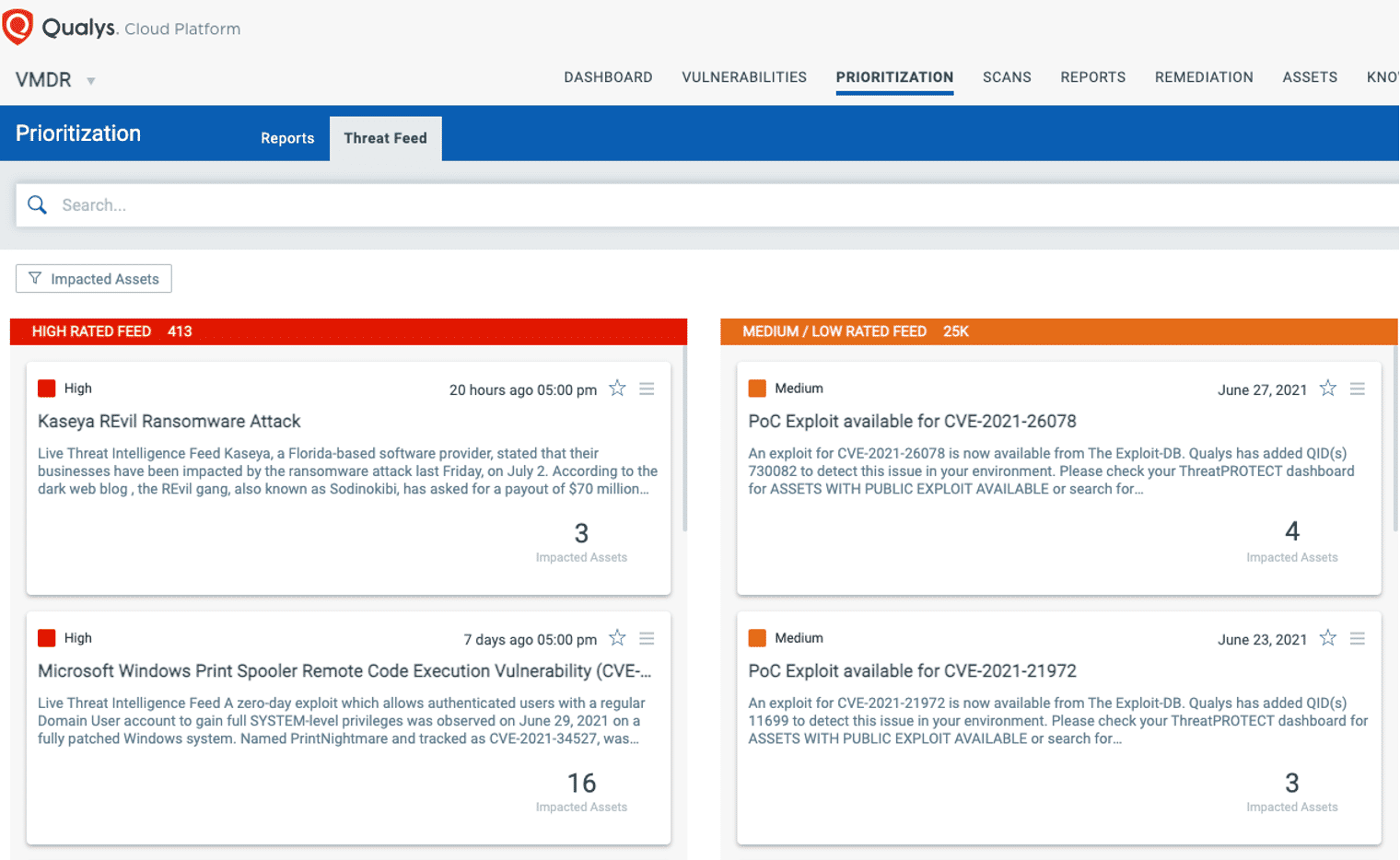
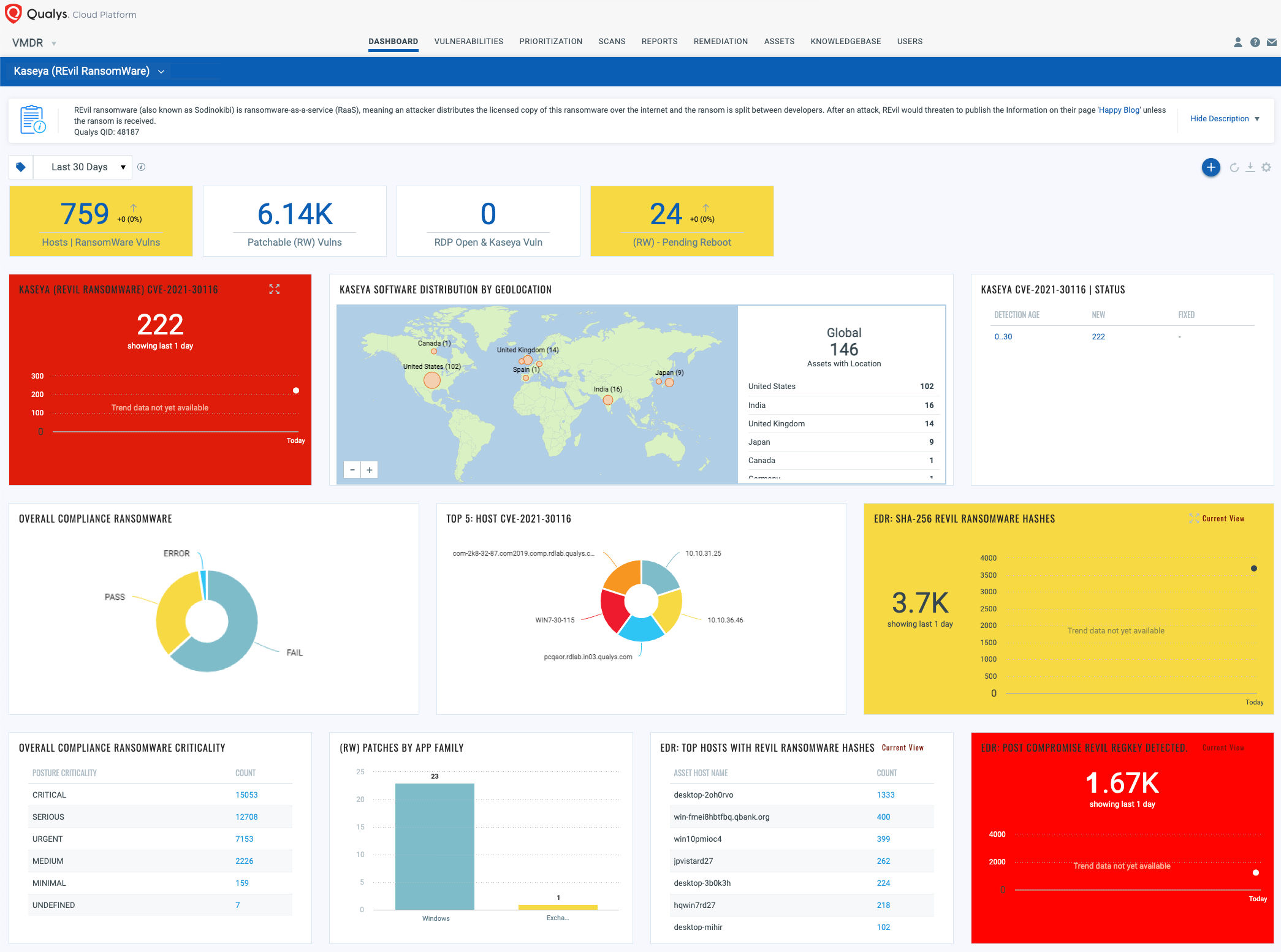
With Qualys Unified Dashboard, you can track REvil ransomware, impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of Kaseya VSA vulnerability trends, EDR events and ransomware-related compliance controls in your environment using the REvil ransomware Dashboard.
Workarounds
Disable RDP if not used. If required change the RDP port to a non-standard port.
After identifying vulnerable assets, monitor them for malicious activity.
As a best practice, follow these steps:
- Keep operating systems, software, and applications current and up to date.
- Make sure anti-virus and anti-malware solutions are set to automatically update and run regular scans.
- Create backup copies of all important data as a good step towards securing the data. Backup copies can be kept on physically disconnected systems to maximize security.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching critical Kaseya VSA vulnerability CVE-2021-30116.