Introducing Qualys Context XDR: the Difference between Chaos & Clarity
Last updated on: December 21, 2022
In my role as a product leader, I have the pleasure of meeting security practitioners from organizations big and small, across multiple industry segments and geographies. No matter how large or small their budget or staff is, how much they’ve invested in their tech stack or how much experience they have one issue is a recurring theme: triaging events and determining high priority incidents from the noise of security alerts is difficult and rarely done well.
That’s why today I’m especially proud that Qualys is launching Context XDR, the industry’s first context-driven XDR to help security analysts in the SOC to prioritize threat detections and reduce alert fatigue. Powered by the highly scalable Qualys Cloud Platform, this new solution combines:
- Rich asset inventory and vulnerability context
- Network and endpoint telemetry from Qualys sensors
- High-quality threat intelligence and third-party log data to identify threats quickly
To increase productivity, Qualys Context XDR leverages our Platform’s existing response capabilities – patching, fixing misconfigurations, killing processes and network connections, and quarantining hosts – to comprehensively remediate the threats identified by Qualys Context XDR.
Read the Context XDR Launch Press Release
Why We Built Qualys Context XDR
For the security operations team in too many enterprises, every alert investigation too often starts from scratch… with very little, if any, background information about the users, assets, and detected behavior under threat.
The security analyst tasked with investigating the threat must answer any number of critical questions before understanding how to respond. These can include:
- What operating system is it running?
- What is the asset vulnerable to?
- How many of these vulnerabilities are publicly facing?
- What application and security tech stack are the assets running; and are they properly configured?
- If there is a misconfiguration, could an attacker exploit this?
- Assuming this is an attack, is it likely to succeed?
- Did it succeed? If so, where is this in the attack cycle (e.g. MITRE ATT&CK framework)? Did we catch it early or late?
- Is this a run-of-the-mill security alert that a junior analyst can take; or is it an all-hands-on-deck incident with wide ranging impact?
- What happened leading up to this event and immediately after?
- Perhaps most importantly, what’s the business impact of this alert?
Assuming the organization can answer these questions, it’s rarely a complete answer and almost never from one source. As if that isn’t frustrating enough, crucial datapoints like risk exposure and asset criticality are rarely utilized by the security solutions performing threat detection and response. Best case: they are bolted on after the fact.
All these pivots the analyst must make from console to console, gathering necessary context, takes time. Time that impacts their overall productivity. Time that could be used addressing high priority alerts – the work that actually reduces risk.
The SOC has three immediate needs in threat assessment:
- Immediacy: defense against any possible attack needs to be fast, scalable, and real-time
- Criticality: understanding the impact or potential impact of an event is a must for proper prioritization
- Response: stopping or preventing an attack hinges on quickly taking action (e.g. killing processes, quarantining files, etc.)
XDR solutions must break down security data silos to deliver a holistic view into threats across the enterprise. In many organizations, there is a patchwork quilt of integrations, with disparate solutions handling vulnerability management, patching, asset inventory, identity & access, CMDB, SIEM, and all points in between. This is why the power of a unified platform such as Qualys is so important for XDR.
There’s a reason unified visibility and control are so important, and why so many organizations have struggled with technical obstacles to attaining it – context. The only way to truly understand and react appropriately to a security event is with context. Without context, alerts become noise.
Context changes the picture. With proper context the responder understands immediately what the business impact of a given alert is and can respond appropriately. Context lends a level of intelligence that aids in proper, proactive response.
Qualys Context XDR was designed with this in mind.
Benefits of Qualys Context XDR
Context XDR provides clarity through context by bringing together:
- Risk Posture – Our solution leverages comprehensive vulnerability, threat, and exploit insights not just for the asset’s OS but also third-party apps. This includes misconfiguration/end-of-life awareness for continuous vulnerability mapping that provides a complete picture of the enterprise’s risk posture. Risk scoring based on simple OS patch to CVE mapping leaves out too many possible exposures that threat actors are expert at exploiting.
- Asset Criticality – Leveraging Qualys Cloud Platform’s single Cloud Agent,
active asset discovery is coupled with policy-driven criticality assignments that evolve with the asset’s current state. This allows our XDR solution to deliver the security and business context necessary to dynamically prioritize high-value assets (like an executive’s laptop or a critical R&D server) in real time. - Threat Intelligence – Deep understanding of exploits, attacker techniques, and how threat actors use vulnerabilities to penetrate defenses is fundamental to delivering preventative and reactive response capabilities to stop active attacks, remediate root-cause, and patch to prevent future attacks.
- Third-Party Data – Using Qualys Cloud Agent as well as cloud-based and on premises sensors, Context XDR gathers up-to-the-second log and telemetry data from your enterprise’s third-party solutions and triangulates this with asset risk posture, criticality, and threat intelligence to detect threats and create high fidelity alerts.
All of this critical asset context is available to the responder inside the alert. The resulting risk score allows SOC analysts to quickly identify and prioritize high risk alerts.
A Peek Inside Qualys Context XDR
Let’s take a quick look at some of the major features and functions of Qualys Context XDR.
Context XDR provides an intuitive head’s up display, with event signals grouped by MITRE ATT&CK mapping as well as by the most notable users and assets.
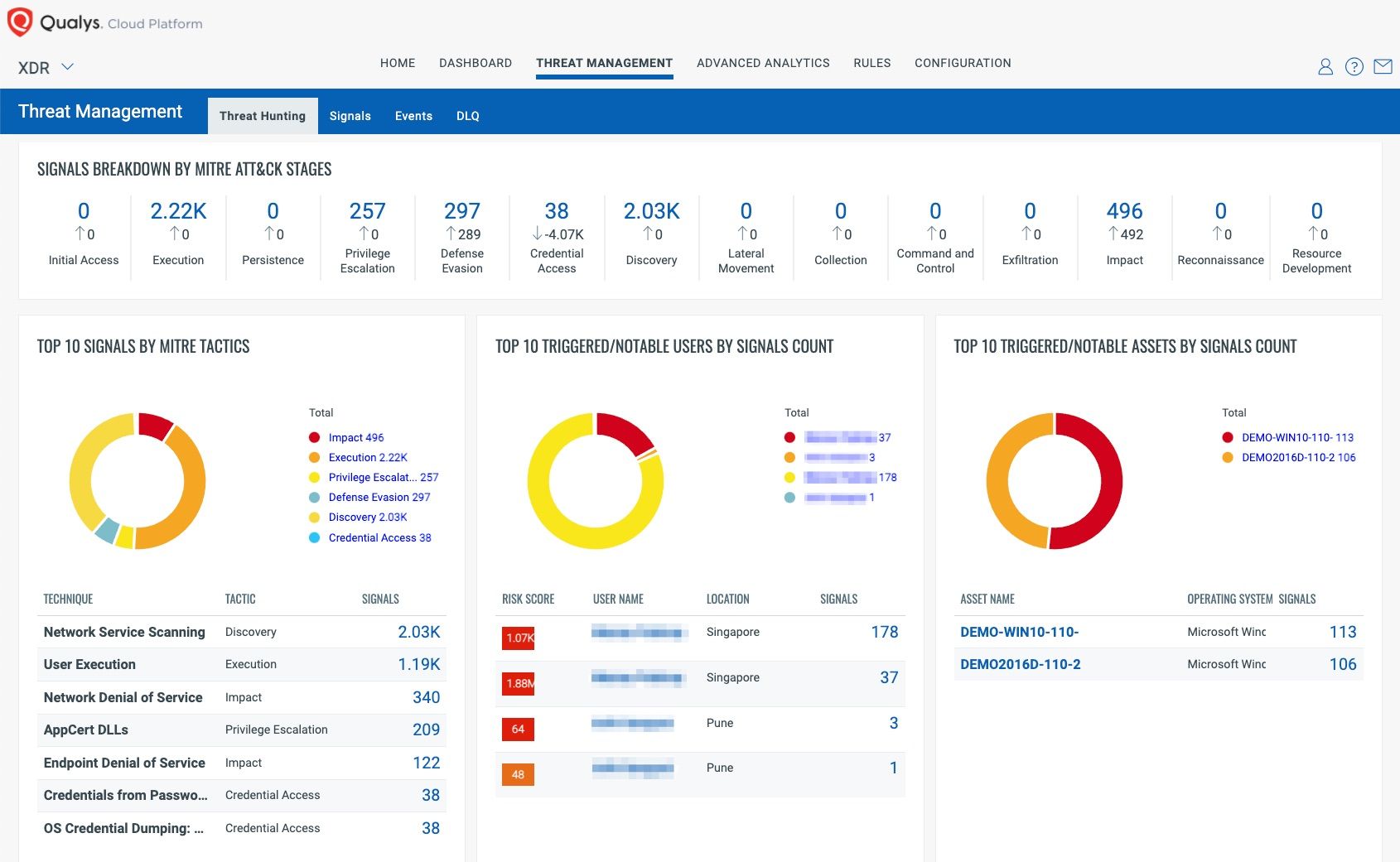
But what really sets Qualys Context XDR apart is the rich asset data that’s embedded within associated signals.
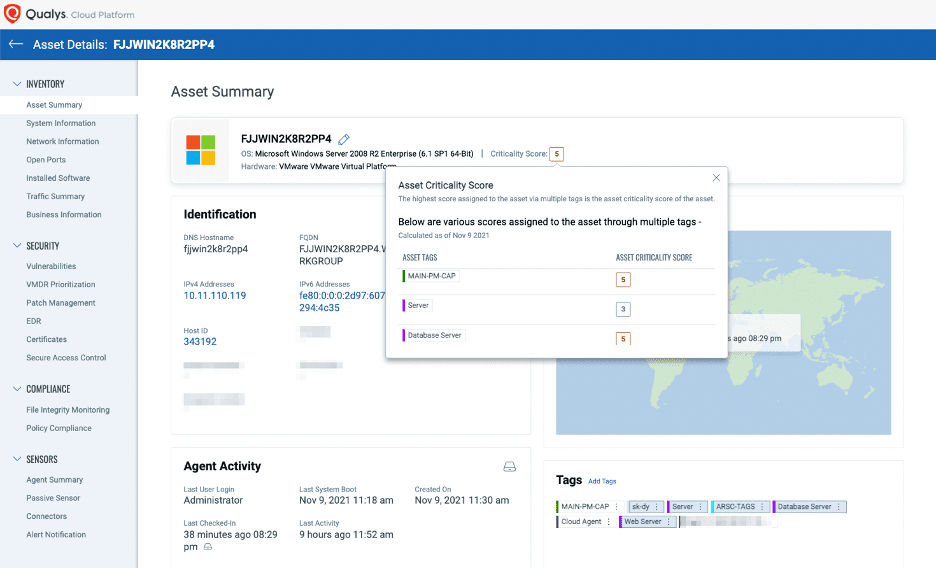
The screenshot below shows the dynamic criticality rating which is continuously updated based on the asset’s current state. The criteria-based policy (e.g. by server platform, database, or business unit) assigns a cumulative business criticality rating that changes dynamically as the asset changes.
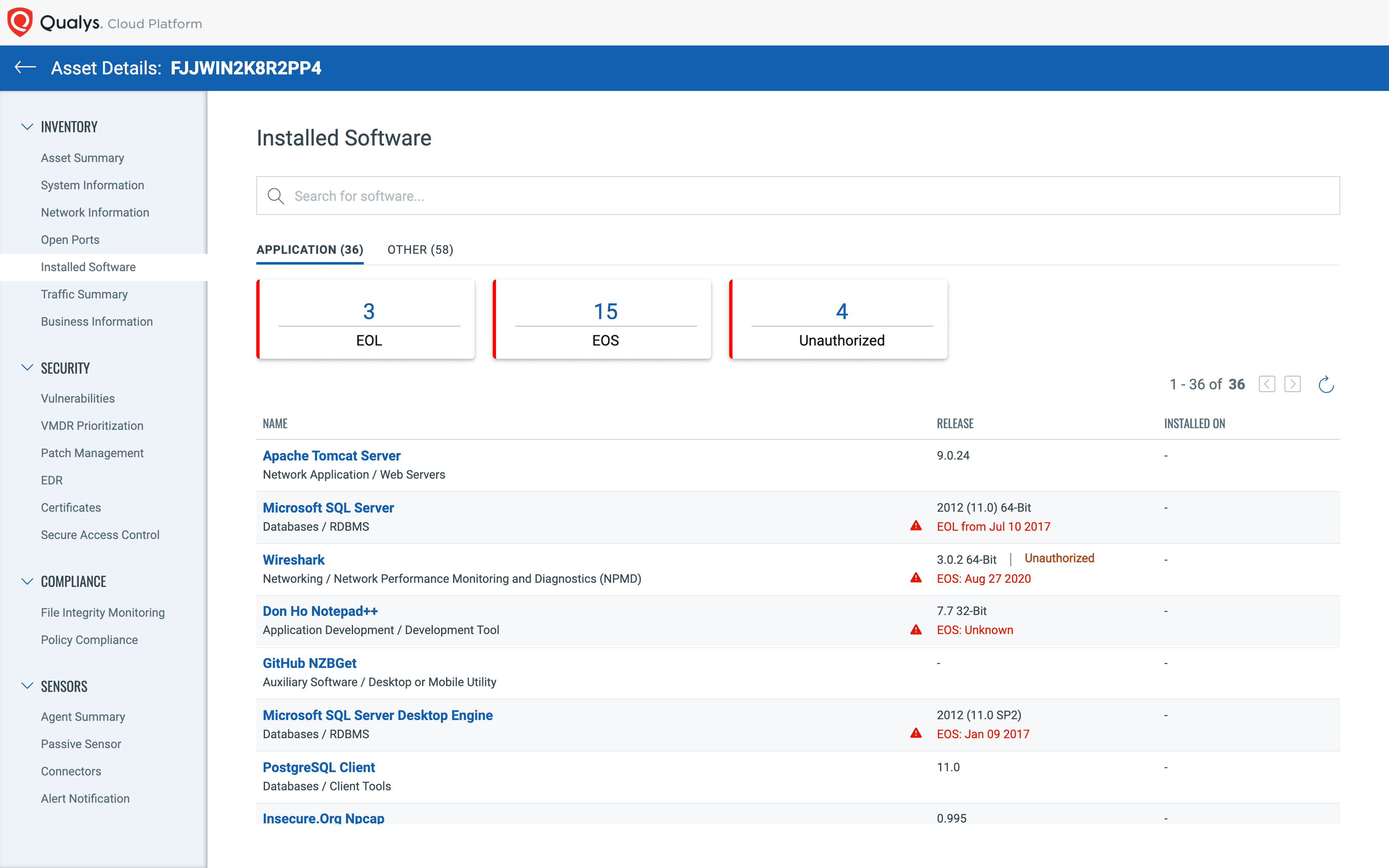
With another click, the SOC analyst can instantly see all software titles installed, along with version, end of life, and business authorization status.
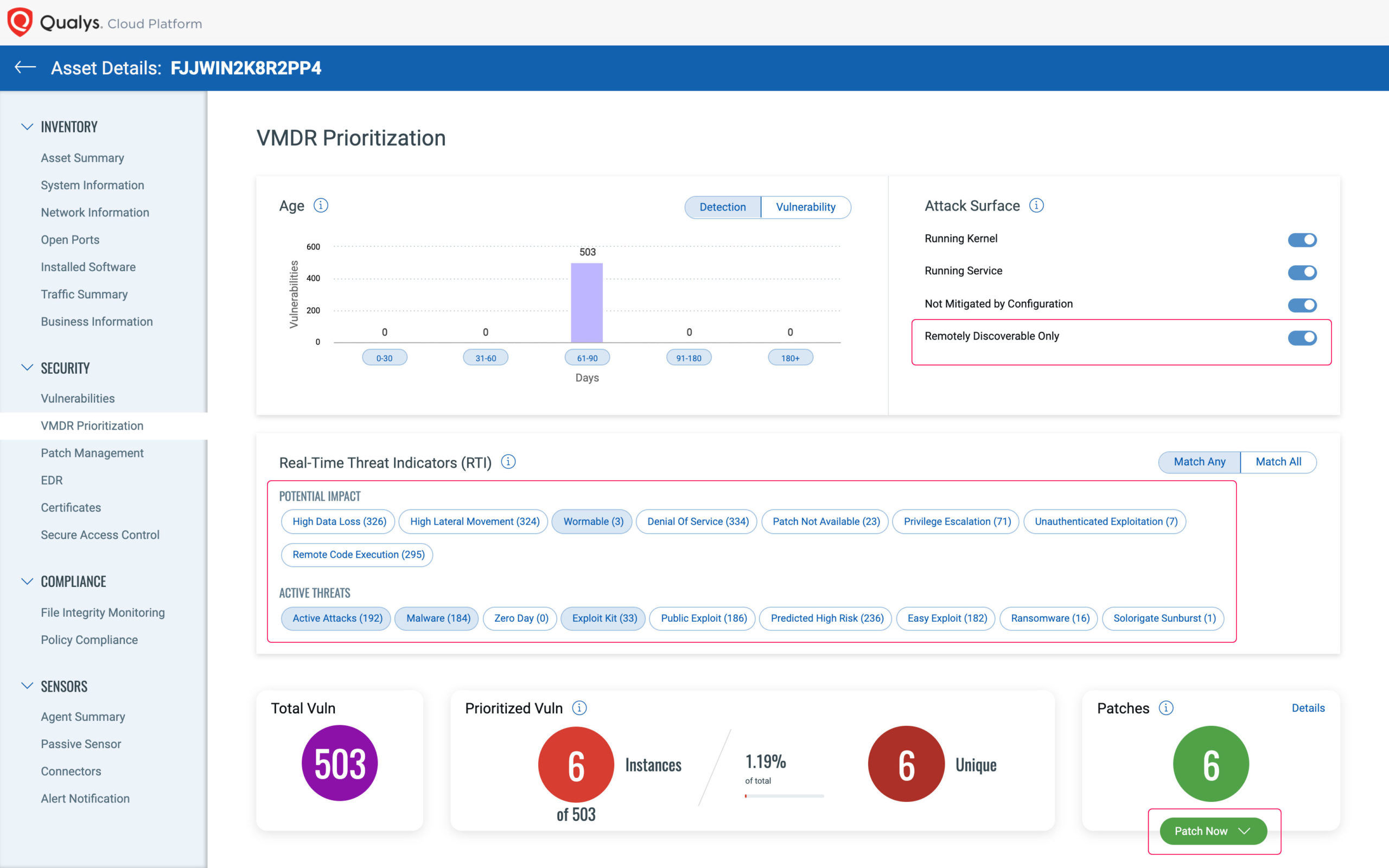
To complete the picture, system vulnerabilities are immediately visible, with a variety of search criteria and attack mapping to allow the investigator to view the asset from the attacker’s point of view.
In addition to the ability to kill processes, quarantine files, and return systems to normal operations, Context XDR allows vulnerabilities to be quickly removed both from the affected asset and proactively across the enterprise to harden the entire environment against future attacks.
As we’ve shown, Context XDR offers a powerful single pane of glass for SOC analysts. Its seamless workflow, enabled by the single Qualys Cloud Agent, allows enterprises to quickly prioritize alerts, and spend their precious time and resources where it will have the biggest impact. Productivity gains are realized by time better spent repelling attackers instead of pivoting between incompatible legacy systems.
We’re excited to introduce Context XDR and announce that it’s now generally available. If you’d like to learn more, reach out directly to the Qualys team at xdr@qualys.com and we’ll be happy to show you how Context XDR can help bring context to your security efforts. Existing Qualys customers and sales prospects can contact their Technical Account Manager or assigned sales representative.