Upgrade Your FIM Program to Detect Risk and Streamline Compliance
File integrity monitoring (FIM) tools are essential for defending business and customer data, but legacy tools are falling short by swamping security analysts with irrelevant alerts. This blog describes how Qualys FIM easily solves such issues by accurately isolating file-level breaches and sending only relevant alerts to security teams.
File integrity monitoring (FIM) is an essential layer of defense for protecting the business and customer data of enterprises large and small. FIM solutions identify illicit activities across critical system files and registries, diagnose changes, and send alerts, so that such actions may be prevented from disrupting business.
Choosing the right FIM solution will help streamline tasks for both compliance auditors and the SOC team. It also helps with tool convergence and security stack consolidation efforts. While these goals seem attainable, traditional FIM tools have not kept pace with the volume and complexity of attacks, nor with ever-changing requirements for compliance monitoring.
Consider these challenges:
- Cybercrime is up 600%, partly as a result of the COVID-19 pandemic
- 66% of security stakeholders have experienced a cyberattack in the past 12 months
- The costs of cybercrime are rising, with estimated worldwide losses of $10.5 trillion annually by 2025
Let’s consider some typical pitfalls of traditional FIM tools which are all too familiar to most security and compliance practitioners.
Challenges with Current File Integrity Monitoring Tools
Many FIM tools suffer from inefficiencies that hobble their effectiveness. These include lack of alert context, lack of detection capabilities, and lack of scalability. Let’s examine each of these drawbacks.
Too many alerts, not enough context
More alerts do not equal more security. Some FIM and asset inventory tool vendors have made attempts to differentiate their offerings from competitors by generating more alerts with increasingly customized risk ratings. The boost in alerts has resulted in burying compliance and security analysts under a pile of hundreds of thousands of events without accurate or meaningful prioritization. In addition, alerts often do not differentiate between malicious and benign changes. Over 99.99% of alerts require no action, dramatically taxing SOC teams and compliance auditors alike – and making efficient incident response nearly impossible.
Inability to identify malicious or suspicious changes
Traditional FIM tools provide the basic details about a change activity. A few of them even provide data on who made the change. What they all fail to provide is a reputation score of the file newly associated with the asset. Once a malicious file makes its way into your system, it can rapidly infect your network, leaving your infrastructure completely vulnerable. Suspicious files need to be flagged and continuously tracked to limit propagation.
Expensive or inefficient scalability
At a time when most security and compliance teams are looking for tools and solutions that can help them do more with less, most FIM vendors have failed to answer the call. Traditional FIM tools are commonly stand-alone solutions that require integration with third-party asset inventories. In addition, FIM vendors often require professional services to integrate or scale beyond a certain node count.
Finally, most FIM tools need to evolve their analytic capabilities to enable a deeper understanding of adversarial tactics, techniques and procedures (TTPs) at scale.
Qualys FIM – Evolved File Integrity Monitoring
Qualys File Integrity Monitoring (FIM) is a lightweight and highly scalable cloud service that provides continuous system monitoring of critical files, folders, and registry objects for changes at scale – unlike any other FIM technology available today.
With Qualys FIM, your organization can enjoy new groundbreaking capabilities that add context to common change events in your file system such as File Reputation Status and Trusted Source Status. These capabilities provide users with real-time event enrichment to quickly identify malicious or suspicious changes and build an “allow-list” of trusted changes. Qualys FIM provides security and compliance teams with:
- The Industry’s First “Noise Control FIM”: Qualys FIM reduces up to 99% of alert noise with trusted source intelligence and profile tuning that optimizes compliance and risk analysis. With “Trusted Source Status,” a user can easily identify beneficial changes due to patches and security updates and update them within an allow-list.
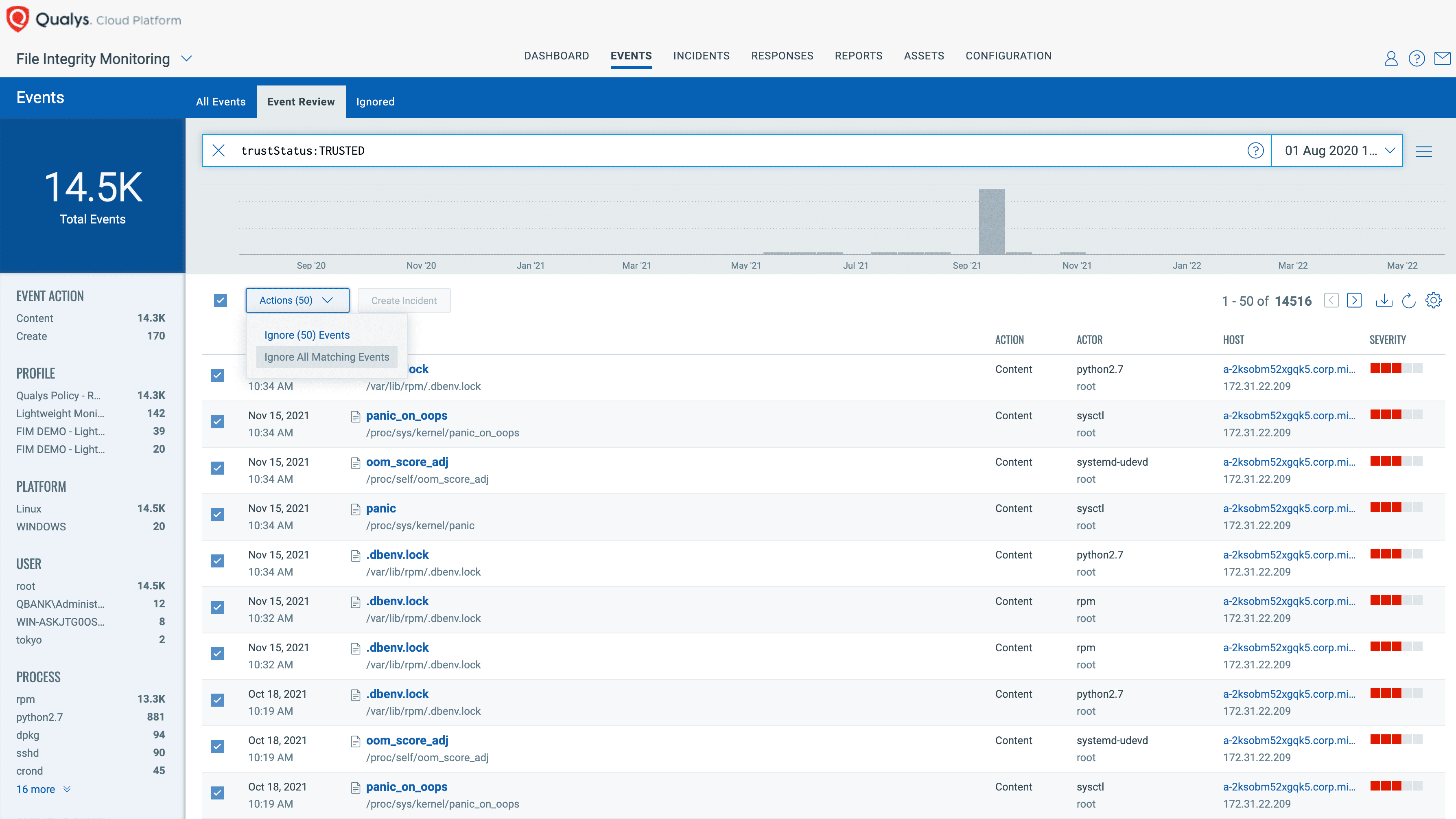
- Accurate Event Prioritization: Qualys FIM arms security and compliance analysts with “File Reputation Status,” allowing users to identify if any change on the system is malicious or suspicious – and take necessary action to kill the attack chain.
- Rich Asset Context: As part of Qualys Cloud Platform, Qualys FIM leverages the asset contextual data present in Qualys VMDR and Qualys CSAM. Where other FIMs rely on third-party compliance solutions and asset inventories to deliver full benefit, Qualys FIM provides complete context and granular asset detail to security and compliance teams without extra fees, additional third-party vendors, or costly integration services.
While the capabilities of Qualys FIM are powerful from an individual use case perspective, the utility of Qualys FIM is really highlighted when these capabilities work together. Qualys FIM is delivered as a truly out-of-box ready solution that is easily deployed with one-click activation.
Here are a few notable benefits that Qualys FIM provides for security and compliance stakeholders:
Rapidly filter, review, and analyze with ease and accuracy
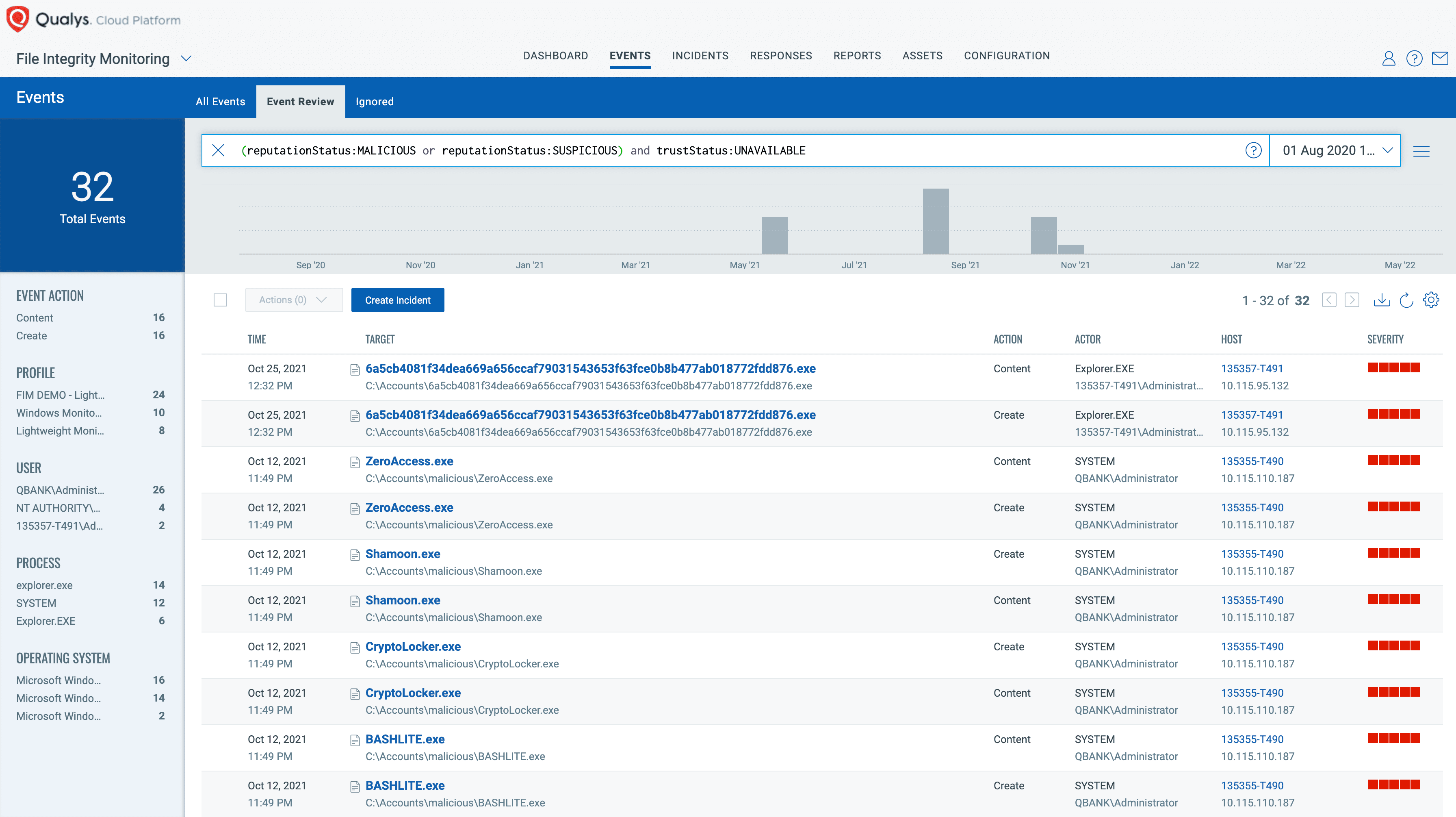
As an analyst, consider a filtering query like this:
(reputationStatus:MALICIOUS or reputationStatus:SUSPICIOUS) and trustStatus:UNAVAILABLE
This query would list all the events whose reputation status is malicious or suspicious.
As soon as an event is sent to Qualys Cloud Platform, the event is enriched by Qualys threat intelligence. This insight is readily available in an intuitive dashboard allowing users to quickly search the events using a query. With Qualys FIM, organizations can address their day-to-day security and compliance needs while continuously honing its threat intelligence capabilities via automated machine learning.
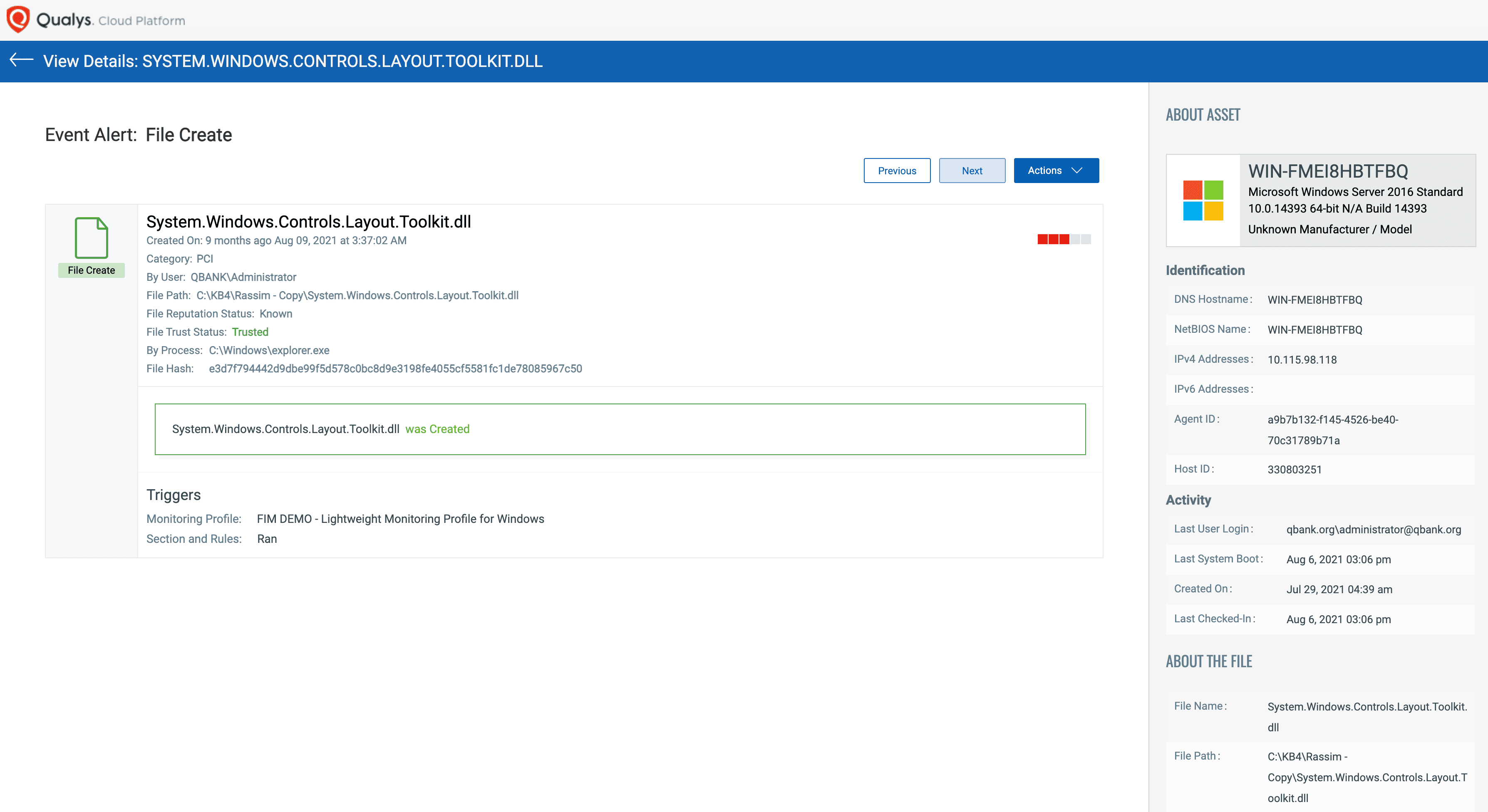
Granular event details with data for who, what, when, and where
Comprehensive event details are captured when a file is dropped on a monitored asset. These details are comprised of who-data, reputation status, and trust status. Most other FIM solutions cannot provide exact user and process details, resulting in incomplete and uninformed response to alerts.
Automated incident generation
Unlike most FIM solutions, Qualys FIM empowers users with automated incidents and alert generation with each malicious change within their environment. With automated incident generation, Qualys FIM operates as if it is a full-fledged SIEM, providing higher ROI than traditional FIMs.
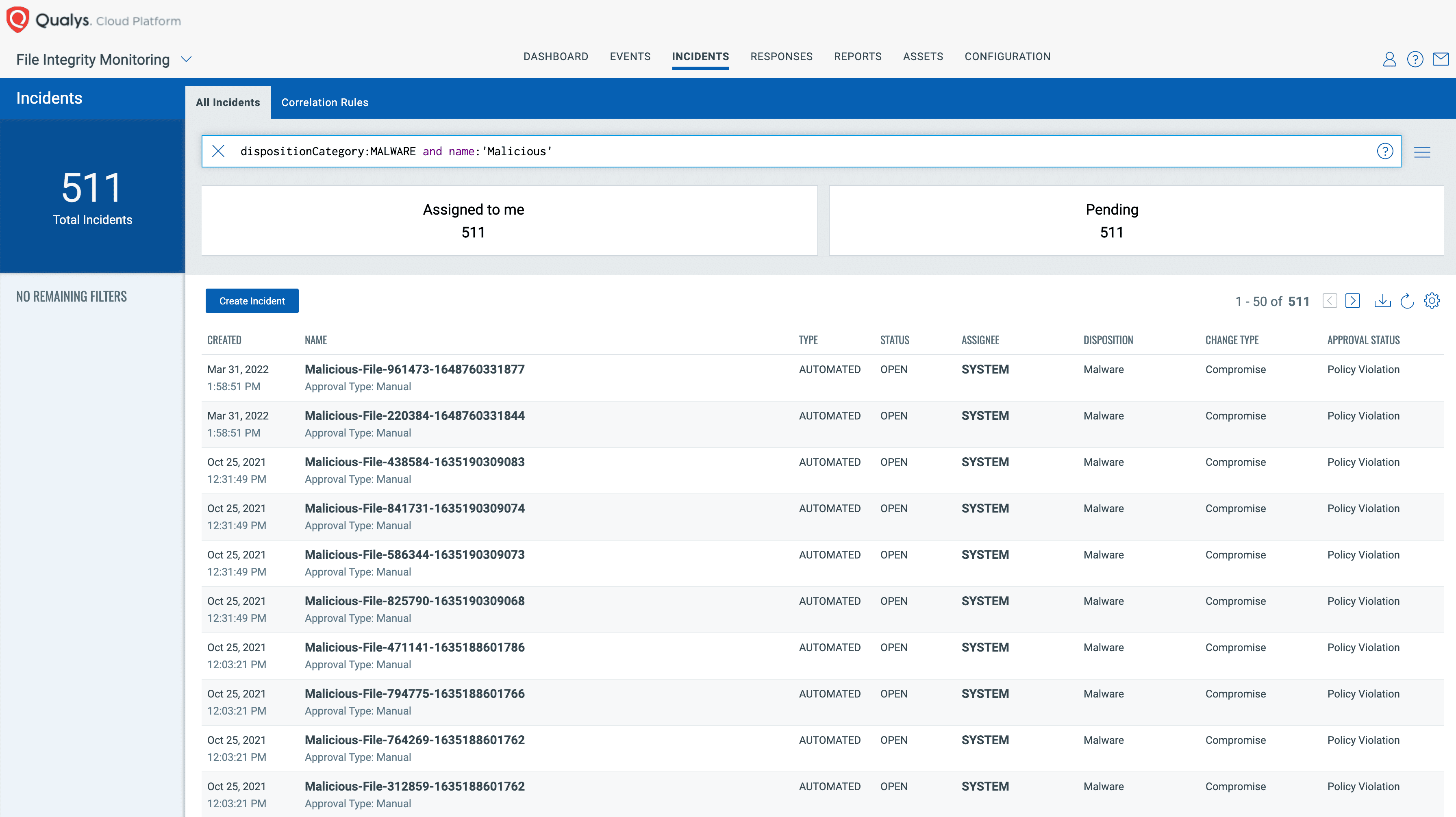
When Qualys FIM identifies the file reputation status as “Malicious,” an incident is automatically created with the following details:
- Disposition: Malware
- Change Type: Compromise
- Approval Status: Policy Violation
- Comment: Malicious change detected on the system
Report or push data to external data lakes
Qualys FIM includes APIs that are devised to enable easy custom integrations. The Rich FIM API set produces data in a well-defined and structured JSON format. Results can be easily exported to the ELK stack and support native integrations with Splunk, IBM QRadar, and ServiceNow.
How Qualys FIM Can Help
The Qualys approach to File Integrity Monitoring leverages the full power of Qualys Cloud Platform and a FIM library to reduce alert noise by up to 99%. Notifications from Qualys FIM are always tested and validated. This gives security and compliance analysts time to focus on what matters most: high priority risks that demand immediate attention.
We also invite you to see how Qualys FIM can help your organization adhere to compliance mandates such as PCI DSS, FedRAMP, HIPAA, GDPR and more – all at lower cost and greater system performance than traditional FIM solutions.
Give Qualys FIM a spin with our 30-day no-cost trial!
Free Trial
Get real-time monitoring of integrity violations across global IT systems
To learn more, explore the links below.
Great sample. Regards
Hi Thomas,
Which version of FIM will have the option to trustedsource and reputation status?