How to Quickly Prioritize Risks with VMDR 2.0 and Orchestrate Response with CMDB & ITSM Integration

Table of Contents
- Asset Management Reinvented for Cybersecurity Teams
- Assign Risk Profile to Drive Risk Quantification & Prioritization
- Qualys Customers Benefit from CMDB Sync with ServiceNow
- 3 Primary Use Cases for Qualys CMDB Sync with ServiceNow
- Accurately Orchestrating Tickets for Prioritized Vulnerabilities
- Prioritize based on Attack Surface
- Qualys CSAM Capabilities beyond Bi-directional Integration with CMDBs
- Read More:
A single source of truth for asset inventory enables Cybersecurity and IT teams to optimally automate risk prioritization and response. Qualys VMDR 2.0 with TruRiskTM leverages Qualys CSAM to automate the Asset Criticality Score, a key parameter of risk scoring. This blog explains how with insights from Qualys customers including City & County of Denver.
Traditional configuration management database (CMDB) and IT asset management tools do an excellent job at capturing static information, especially information that does not change frequently such as asset ownership, business criticality, environment, business use, who supports and maintains the asset, and more. Having this contextual information is extremely important for Cybersecurity teams when building an asset inventory. It allows them to better assess the true impact of a security risk to the organization. It also helps to optimize remediation processes by knowing who owns a particular resolution task.
However, CMDB implementations are often troubled with inaccurate asset and configuration information. Many times, the CMDB is maintained manually or via ad-hoc integration with tools that have not been designed from the ground up to discover all assets and inventory them with extensive asset and security configuration telemetry.
Having multiple, siloed, and often incomplete sources of asset information leads to workflow inefficiencies that affect your cybersecurity program. The mean-time-to-remediate (MTTR) can be significantly impacted by these process inefficiencies because they significantly extend the time it takes for Cybersecurity and IT Operations teams to collaborate to resolve issues. For example, a vulnerability ticket is opened by the security team against an outdated configuration item (CI) with inaccurate data. The person in charge of resolving the issue needs to request additional information from a different environment or a separate console that she or he may not even have access to.
Cybersecurity and IT Ops teams need a single source of truth for asset and configuration information, to enable accurate risk prioritization to optimally orchestrate response processes.
Asset Management Reinvented for Cybersecurity Teams
Cybersecurity teams need a way to go beyond static IT asset inventory to understand the security context of each asset, detect security gaps and respond to mitigate risk. Qualys enables them to see the entire picture of their assets – with a comprehensive view of their IT infrastructure – all from a single comprehensive solution called Qualys CyberSecurity Asset Management (CSAM), natively built in the cloud and delivered as a service.
With Qualys CSAM, enterprises both large and small can:
- Continuously inventory assets
- Discover blind spots, such as unknown internet-connected assets
- Dynamically assign business information including asset criticality
- Detect security gaps like unauthorized or end-of-life software
- Always maintain CMDB with up-to-date cyber asset information
- Respond with appropriate actions to mitigate risk, thus reducing ‘threat debt’
Free Trial
Qualys CyberSecurity Asset Management Trial
Assign Risk Profile to Drive Risk Quantification & Prioritization
Qualys recommends that enterprises focus security prioritization efforts on high-value or business-critical assets, by defining asset criticality based on key business and technical contexts. In Qualys CSAM, asset criticality is a user-defined measure of asset function, environment, and the business service it supports. Qualys CSAM enables customers to combine the following approaches to define asset criticality:
- Automatically import business information from the CMDB (such as ServiceNow CMDB) and dynamically assign criticality ratings to assets
- Dynamically assign criticality through rules that are based on asset attributes such as server type, network or environment, applications they run, and more
- Manually assign to one or a group of assets through user-defined tags
Qualys CSAM computes the Asset Criticality Score (ACS) by taking all tags applied to a given asset and picking the highest ACS across all tags. A simple numeric scale allows customers to easily rank assets from 1 to 5, where 1 is the lowest and 5 represents the highest criticality.
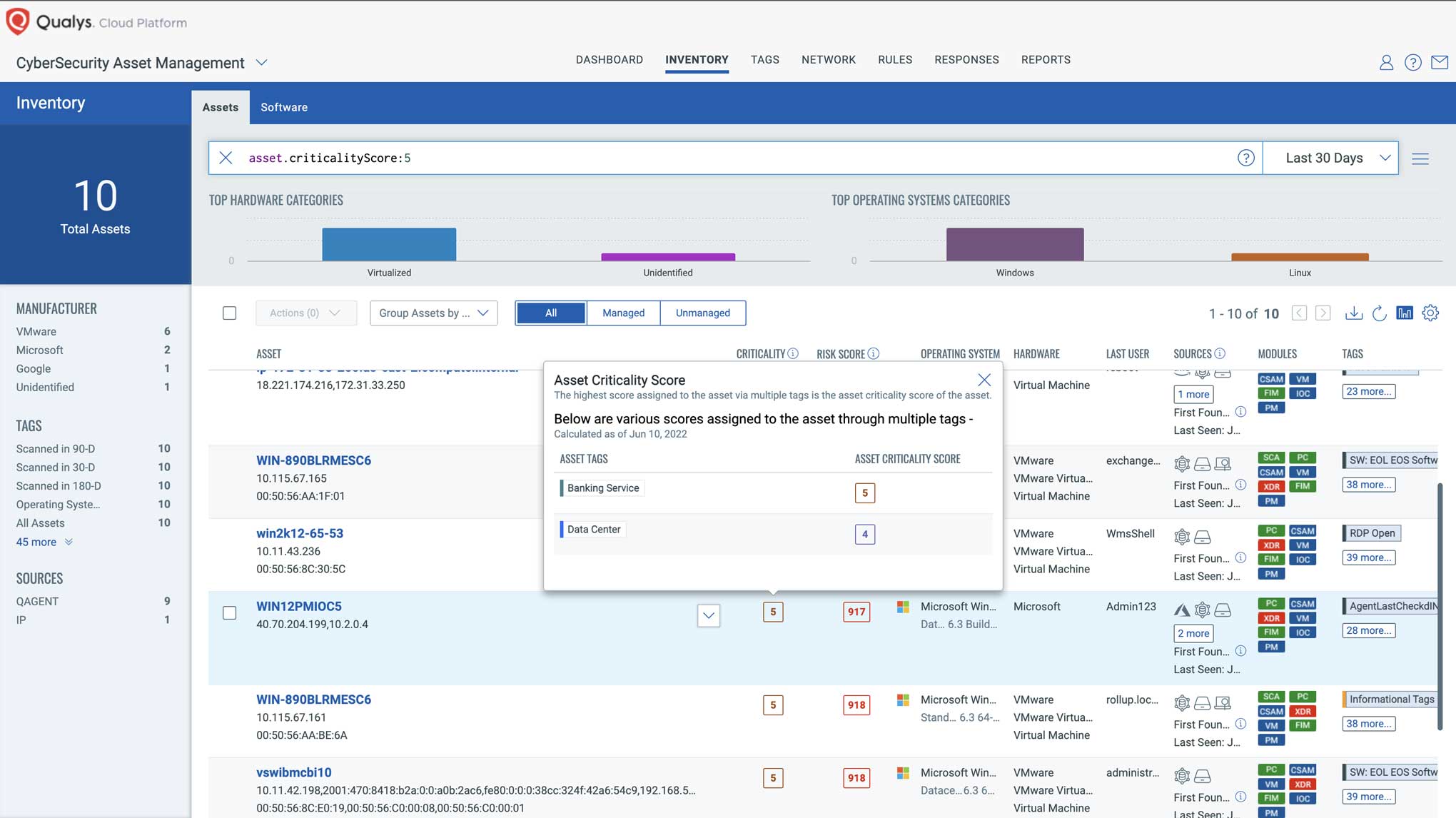
With Qualys VMDR 2.0, enterprises are empowered with visibility and insight into cyber risk exposure
Qualys TruRiskTM allows Cybersecurity and IT teams to reduce risk with holistic scoring. It quantifies risk across the entire attack surface including vulnerabilities, misconfigurations, and digital certificates, and then correlates with business criticality and exploit intelligence from hundreds of sources, including external attack surface exposure data.
The Qualys TruRisk calculation factors in the Asset Criticality Score (ACS), automatically increasing or decreasing the overall risk score proportional to its criticality. ACS multiplies the weighted average of vulnerabilities, misconfigurations, and other key factors to transparently calculate the risk the asset poses to the organization.
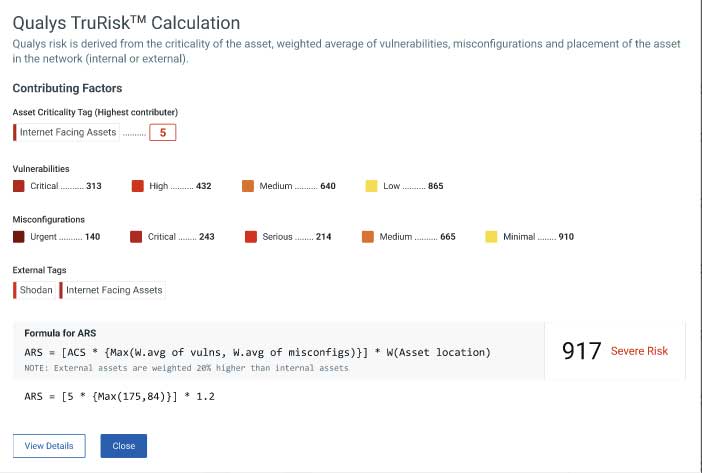
Qualys CMDB Sync App for ServiceNow automates asset tagging and Asset Criticality Score (ACS) by reading metadata from your CMDB and applying this context to Qualys VMDR. Here’s how it works…
Qualys Customers Benefit from CMDB Sync with ServiceNow
The CMDB Sync App is integrated with Qualys CSAM, which leverages the highly distributed and scalable Qualys Cloud Platform and sensors, including the unified Qualys Cloud Agent, to compile and continually update a full inventory of all IT assets everywhere: on premises, in elastic clouds, and mobile endpoints. Qualys CSAM automatically categorizes assets and enriches asset inventory with important layers of asset health and security context such as asset criticality, hardware and software end-of-date and end-of-service, and unauthorized software flags.
The Qualys CMDB Sync Service Graph Connector App for ServiceNow CMDB automatically synchronizes comprehensive information about the organization’s global IT resources that are continuously monitored by Qualys. Qualys CSAM turbo boosts Qualys VMDR 2.0 via this ServiceNow CMDB synchronization, thus allowing Qualys and the CMDB to exchange critical asset and business information required to optimally operate, which in turn helps accurately assess the asset risk. It’s easy for enterprises to synchronize comprehensive asset metadata with ServiceNow to operationalize their CMDB in days, instead of months.
One example of a Qualys customer deriving value from the combination of VMDR 2.0 with Qualys TruRisk and Qualys CSAM is City and County of Denver, Colorado. The U.S. municipality says that innovation is part of their DNA. This means that their IT and Operations teams are continuously rolling out new platforms and applications across on-premises, clouds, and their remote workforce.
“We use ServiceNow’s Now Platform to automate and track our workflows, and the integration with Qualys Cloud Platform is key,” states Julie Sutton, Information Security Manager at City and County of Denver, Colorado. “Qualys CSAM enables us to get up-to-date, continuous, and detailed asset visibility – including hardware, configuration, and application changes across the board. In addition to continuous inventory, Qualys VMDR enables vulnerability, configuration, and policy assessment. It is critical that we get a 360-degree view of these assets and their security posture under a single pane of glass so that our Security and IT teams can collaborate when managing the entire asset lifecycle.”
Another Qualys customer deriving similar value is a large Canadian telecommunications company.
This telecom carrier recently implemented Qualys CMDB Sync to:
- Easily understand an asset’s owners and business criticality when applying patches
- Bring information from ServiceNow for 8000+ business applications into Qualys, including their relationship with critical assets
- Automate asset tagging and Asset Criticality Score (ACS) based on CMDB metadata
- Drive vulnerability prioritization and response based on every asset’s business context
As a result, the firm reduced its average mean-time-to-remediation (MTTR) by half and eliminated multiple consoles and manual processes.
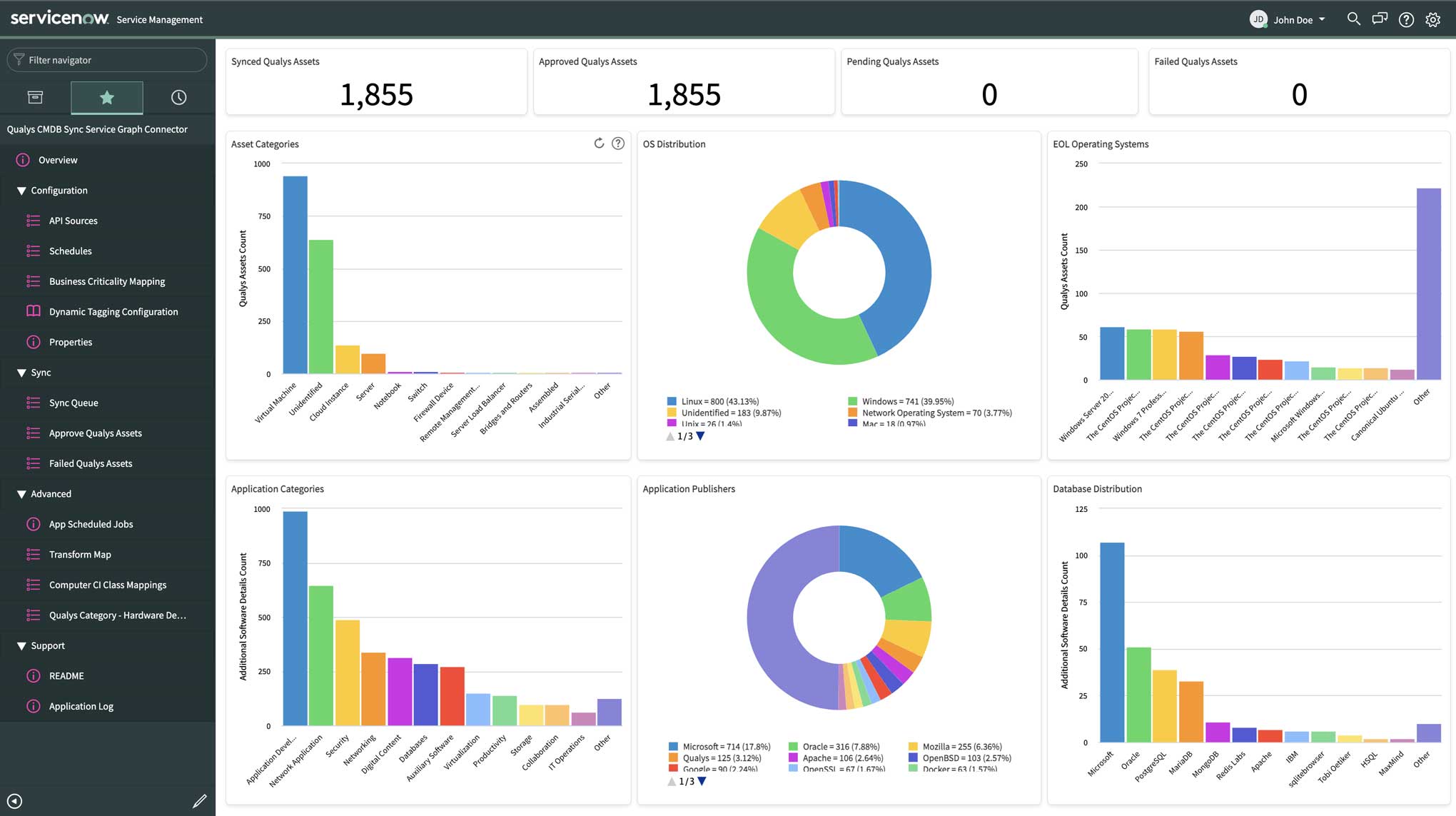
3 Primary Use Cases for Qualys CMDB Sync with ServiceNow
There are three primary customer use cases for Qualys CMDB Sync with ServiceNow:
- Enterprises that need to build their CMDB from scratch or are just starting with ServiceNow CMDB. Many Qualys customers wish to leverage their current Qualys deployment of agents and/or scans to quickly populate their CMDB within a clean and structured asset inventory.
- Enterprises that are maturing their CMDB practice may already have portions of their networks/environments covered by other tools such as ServiceNow Discovery or Microsoft SCCM. These customers need to overlay Qualys data to make sure they have the broadest possible coverage. In this scenario, Qualys is typically utilized in portions of their environment that are not yet covered by other tools.
- Enterprises that have their ServiceNow CMDB populated with basic asset data (either manually, or automatically) and wish to enrich their CMDB with additional asset configuration information. This helps these customers have better context about their assets for downstream processes such as reporting, ticketing, and vulnerability remediation.
Accurately Orchestrating Tickets for Prioritized Vulnerabilities
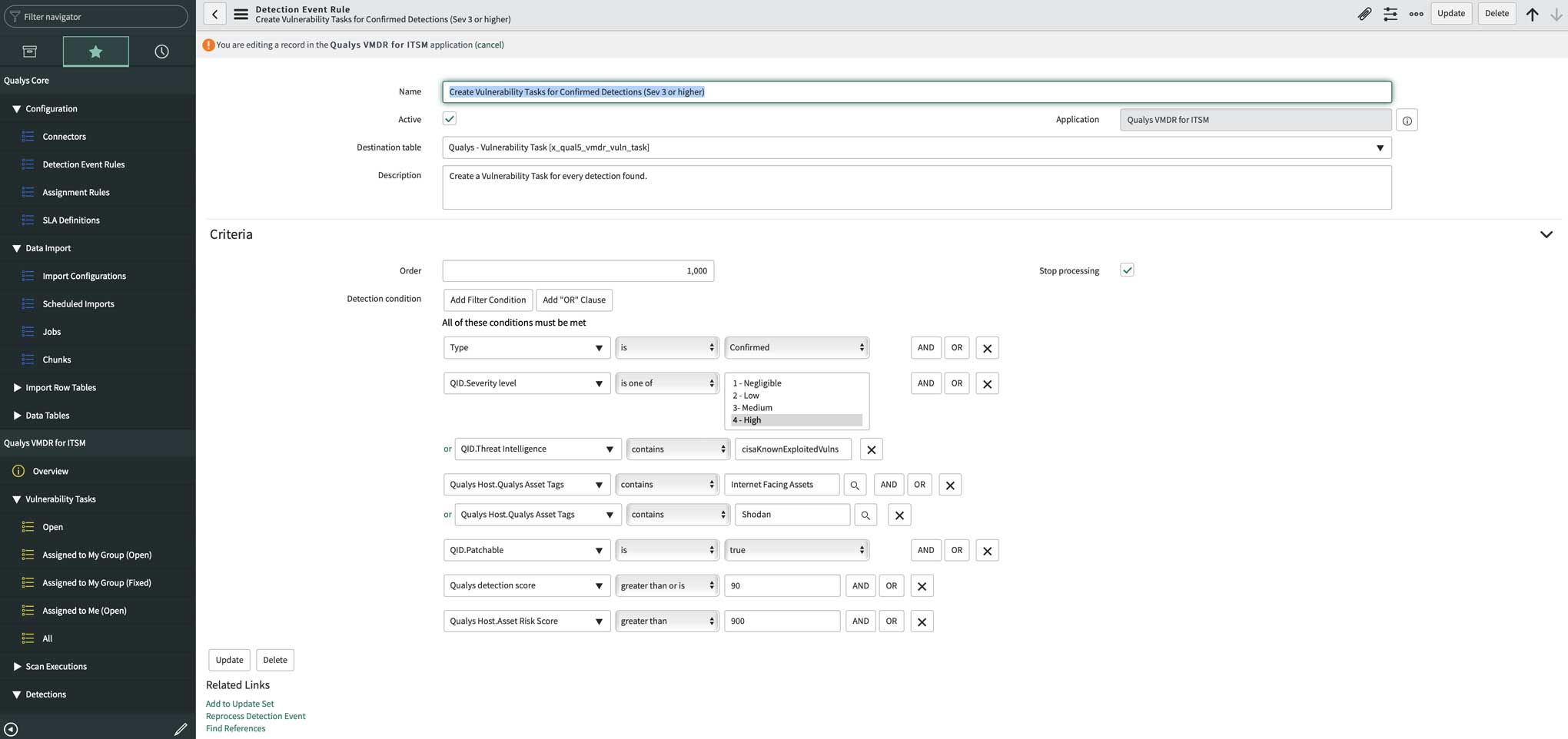
Recently, Qualys announced a new app for ServiceNow ITSM as part of VMDR 2.0 that enables security teams to automatically import vulnerability findings into ServiceNow ITSM. From there, tickets can be created, assigned to rightful owners for remediation, and orchestration of remediation enabled to reduce MTTR and ultimately, to reduce risk.
In addition to that, if CMDB Sync is installed then Qualys VMDR for ITSM leverages CI matches from CMDB Sync to match imported vulnerabilities to correct CI items. In our tests, this resulted in a nearly 100% match for existing CIs. This greatly reduces the time that it takes to accurately map vulnerabilities to assets and their respective owners.
If the imported assets don’t match an asset, they are classified as unmatched CIs that can later be converted into a matched CI item using a workflow provided in the ITSM app.
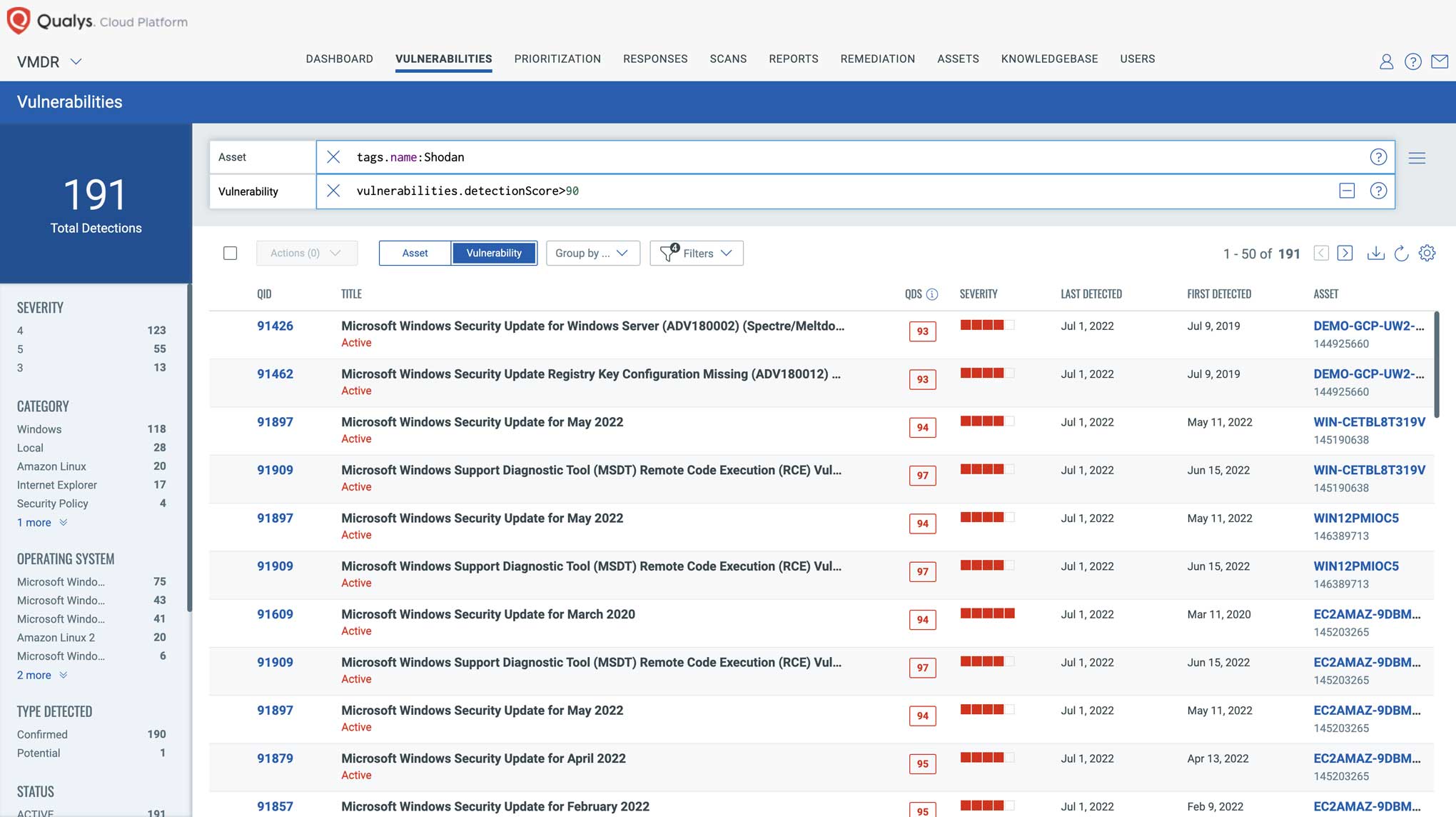
Prioritize based on Attack Surface
Qualys CSAM also directly integrates with internet search engines such as Shodan. When critical vulnerabilities are disclosed, attackers quickly search for vulnerable assets on Shodan and start to exploit them within hours of vulnerability disclosure. With VMDR 2.0 and CSAM organizations can quickly prioritize vulnerabilities on assets that are exposed to Shodan and prioritize them for remediation.
Enriching the CMDB with asset and security configuration information through Qualys CMDB Sync ensures that CIs with detailed information are available within the CMDB before tickets are created, so that assignees have the full context to resolve issues. This allows the entire IT organization to share the same asset context when analyzing and prioritizing risk within VMDR as well as when orchestrating ticketing.
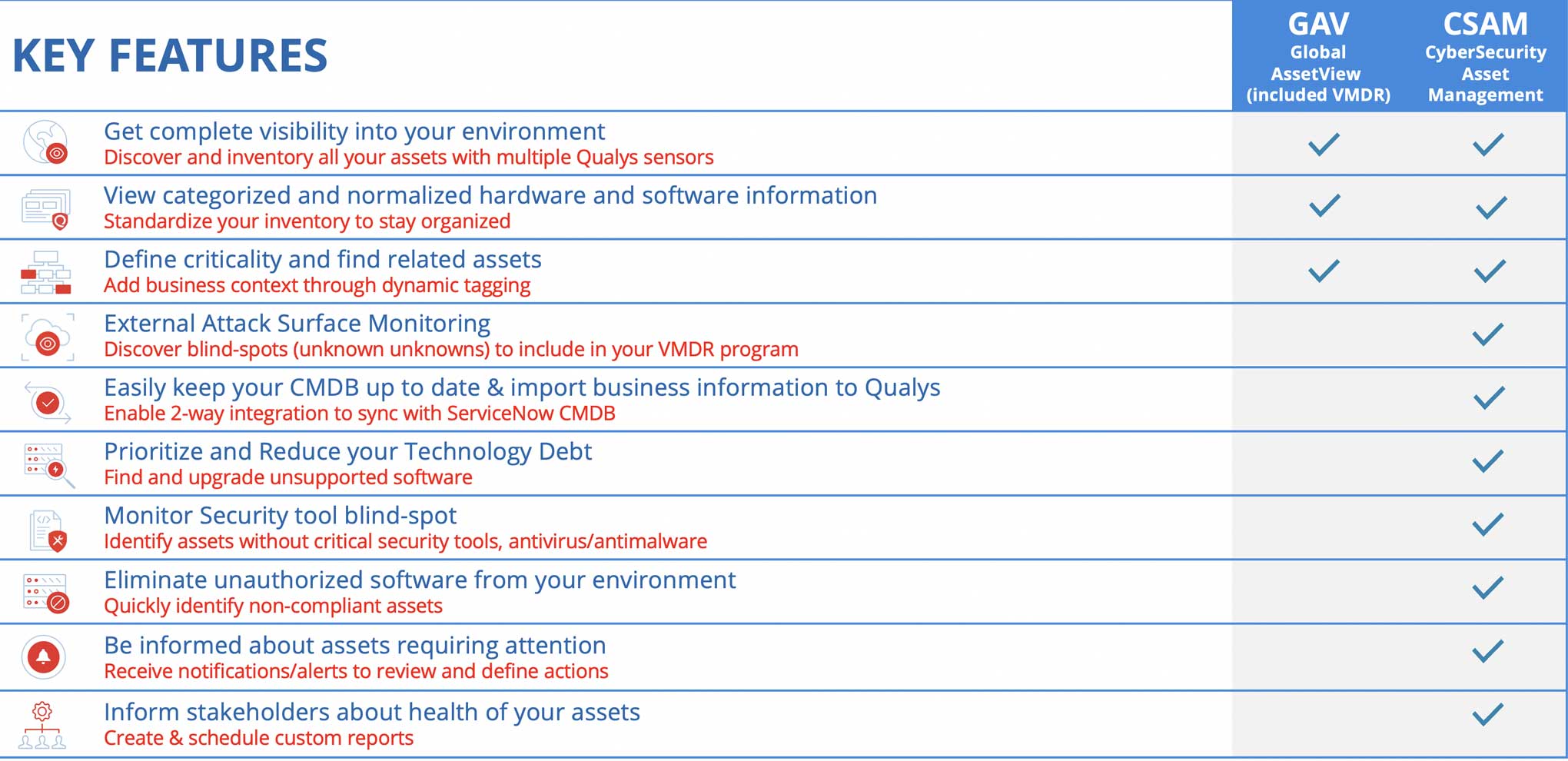
Qualys CSAM Capabilities beyond Bi-directional Integration with CMDBs
Beyond CMDB Sync, Qualys CSAM significantly extends the benefits of VMDR 2.0. The following table summarizes the additional value CSAM brings to an enterprise cybersecurity program: