Qualys Performance Tuning Series: Remove Stale Assets for Best Performance

Table of Contents
As organizations transition to the cloud, their cloud environments and assets rapidly grow. Many of the assets within the cloud are ephemeral in nature, they exist for a few minutes, hours or days and then are terminated. These transitory assets pose a unique challenge from an asset and vulnerability management perspective. Stale assets, as an issue, are something that we encounter all the time when working with our customers during health checks. The most significant issue caused by stale assets is the decline in data accuracy that affects your reports and dashboards.
Stale Assets:
- Decrease accuracy
- Impact your security posture
- Affect your compliance position
- Reduce Performance
- Increase your license costs
Reporting on assets that no longer exist in your environment causes IT teams to chase vulnerabilities that aren’t there anymore (which impacts mean time to remediation (MTTR)), obscures an enterprise’s overall security posture and compliance position, and results in management losing confidence in and starting to question the data. This is an easily avoidable problem, with the automated purge features available in Qualys to be able to remove these assets automatically.
To make it easier for customers to track stale assets in their subscriptions, we have created the Subscription Health dashboard, which you can download and import into your subscription.
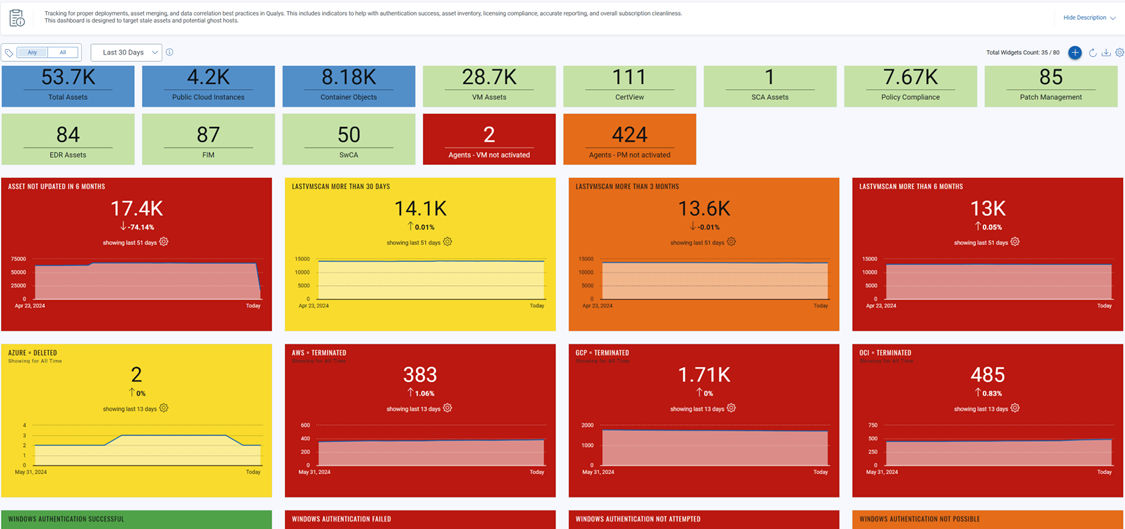
The top row of the dashboard shows the number of assets you have in your subscription, and how many of those are activated for some of the most popular modules. This allows you to quickly view and understand the number of assets in the subscription and identify any potential issues if assets are not getting activated for a module where you believe they should have been.
In the second row, we see the stale asset count.
- The first widget on this row that is labeled “Asset Not Updated in 6 Months” shows the number of assets not updated in the last six months.
- An asset is updated when a scan is carried out OR when a Cloud Connector is run (usually every 4 hours) OR if an agent checks in
- If an asset has not been updated in more than 6 months, there is a very good chance that this asset should be purged from the subscription.
- The next three widgets (in this second row) show the number of assets that haven’t had a vulnerability scan in the previous:
- 30 days
- 3 months
- 6 months.
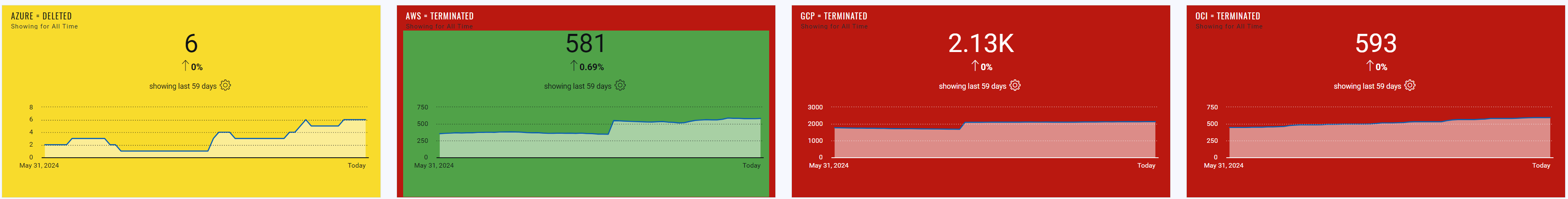
Once you have purged the assets that have not been updated in 6 months, these widgets give you a good indication of where an asset potentially is unreachable or has problems communicating, as we haven’t been able to scan it for some time, especially if these are assets with a cloud agent installed, as they typically send data to the Qualys platform every 4 hours.
The third row on this dashboard is dedicated to the assets hosted by cloud service providers like AWS, Azure, and GCP. In the first 3 widgets of this row, we can see how many assets for each cloud platform are in a terminated or deleted state, while the final widget shows the total number of cloud-hosted assets.
Terminated and deleted assets should be purged automatically using the Purge Feature available within Qualys. If you don’t already have cloud connectors and purge rules configured and running, then it is best practice to create and enable these rules – this will automatically remove any asset entries from your Qualys subscription, where that asset or object is no longer present in one of your cloud venues as it has been terminated or deleted.
Purge Rules Best Practices
There are a few purge rules that are recommended for most of our customers, and we will go through the recommended setup of these rules. For the purge rules based on the state of the assets to work successfully, you must have cloud connectors setup in your subscription, so that Qualys can poll AWS/Azure/GCP for the state of an asset. We recommend the following purge rules settings:
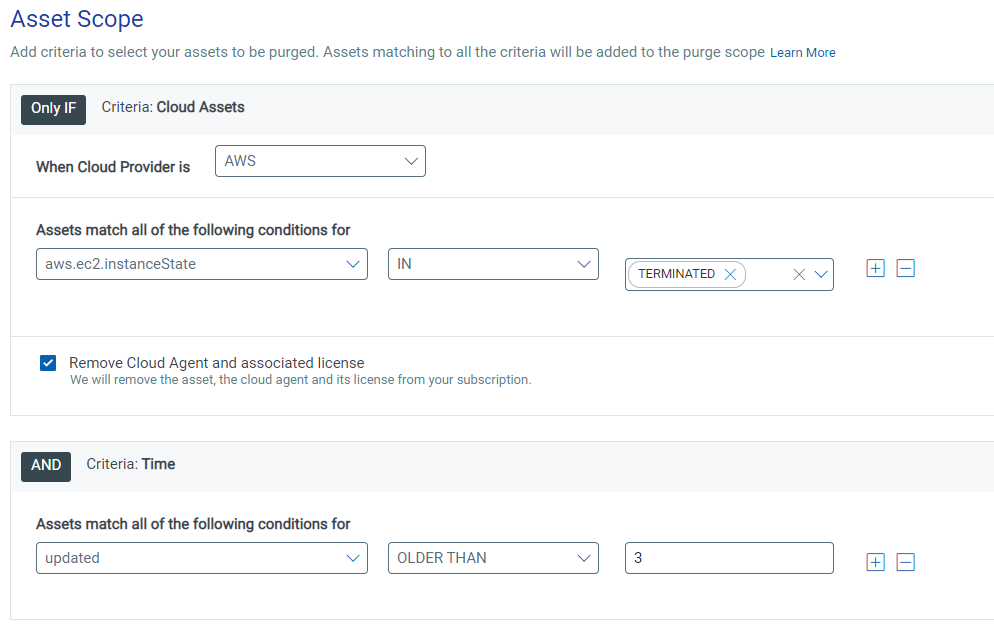
- Amazon Web Services Connector – aws.ec2.instanceState = TERMINATED
This will purge any AWS asset that has been terminated for at least 3 days (you can change the number of days by changing the value under the Time criteria, although we do not recommend setting it greater than 14 days).
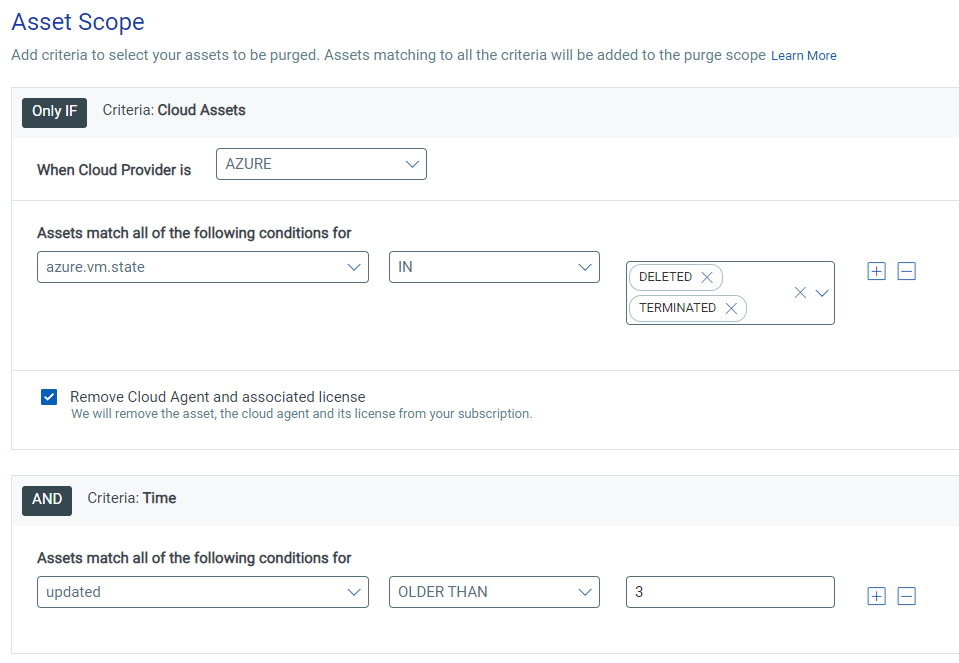
- Azure Connector – azure.vm.state= DELETED or TERMINATE
This will purge any Azure asset that has been terminated or deleted for at least 3 days (you can change the number of days by changing the value under the Time criteria, although we do not recommend setting it greater than 14 days).
- Google Cloud Platform Connector – gcp.compute.state = TERMINATED
This will purge any GCP asset that has been terminated for at least 3 days (you can change the number of days by changing the value under the Time criteria, although we do not recommend setting it greater than 14 days).
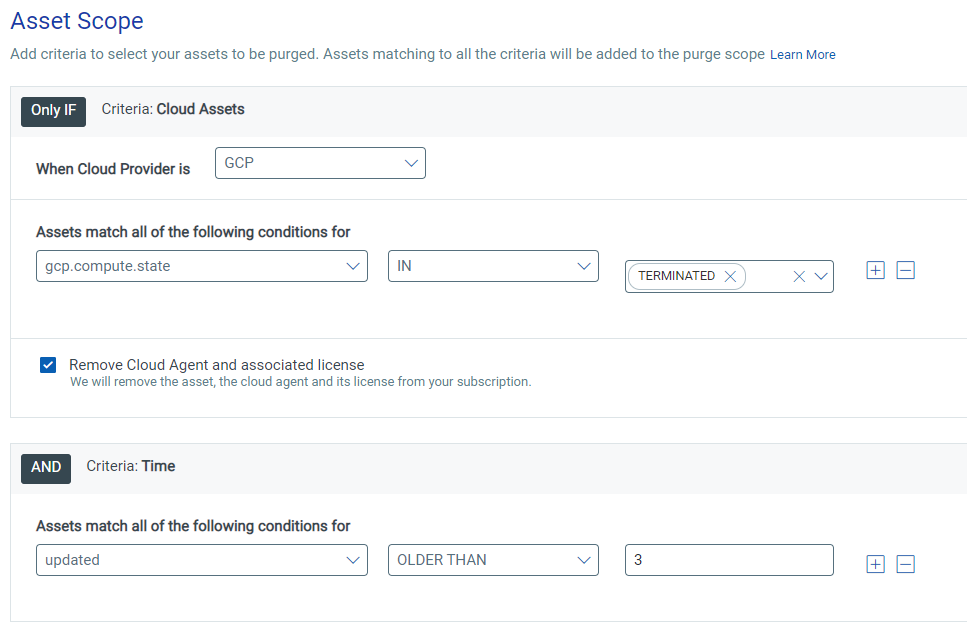
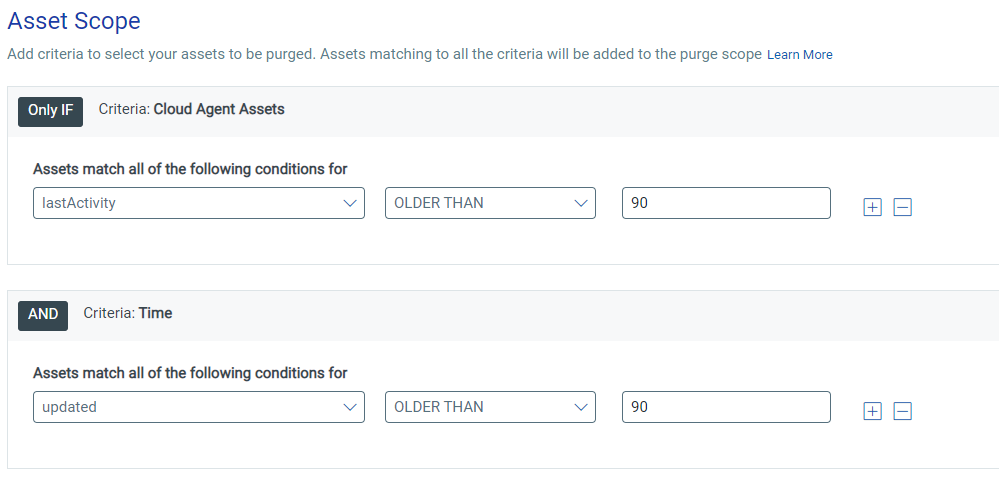
- No Connector + Cloud Agent Assets – lastActivity AND Time OLDER THAN 90 (DAYS)
The final purge rule is relevant for assets that have a Qualys Cloud Agent installed, but either do not reside in a cloud environment or are hosted where the cloud connectors are not set up. This rule will purge any agent that has not checked in or been scanned in more than 90 days. You can be more aggressive and purge after 30 or 60 days, but as a best practice, we do not recommend keeping any agents that have not been updated in more than 180 days.
All the above rules will require a maximum limit for assets to be purged. If this is the first time you are purging, it would make sense to purge stale assets in blocks – think 365 days, 180 days, 90 days, and see how many are removed at each stage… once the initial backlog of stale assets has been purged, you can edit the purge rules to purge more frequently.
- IP/DNS/NetBIOS tracked scanned assets (no Cloud Agent)
The final asset type we haven’t talked about yet is IP/DNS/NetBIOS tracked assets which are created when you carry out network scans using our Qualys Scanner Appliance:
- These IP/DNS/NetBIOS tracked assets can’t be purged using the purge rules mentioned above.
- To purge this type of asset, you will need to use the purging functionality which is included with Asset Search
- Verify purge rule operation and effectiveness
Once the purge rules have been created, make sure to check back after 1 – 2 days to ensure they are running successfully as shown below:
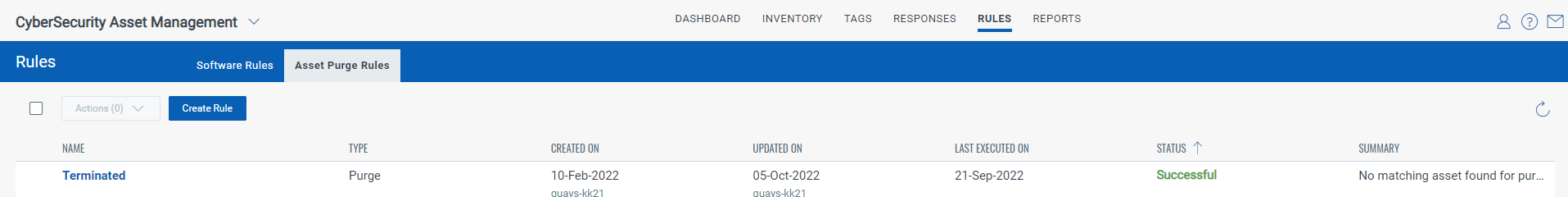
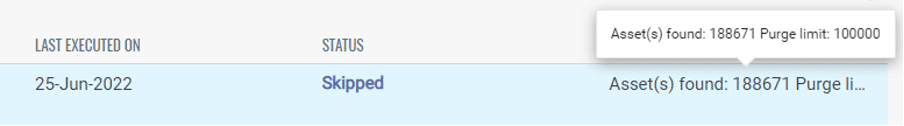
- If the purge limit was lower than the number of assets that need to be purged, then you will see that the rule will have a status of “Skipped”
- If a rule is skipped, raise the limit to ensure the rule can run successfully.
- In the summary section, it will list the number of assets that matched the criteria on the previous run, so make sure the limit is at least as large as that number, plus a buffer for any new assets that meet the criteria.
We have included a short tutorial video on stale assets to complement this blog. View the video to learn how to manage and purge Stale Assets:
There are other widgets in the Subscription Health dashboard, and we will look to cover those in a future blog where we will focus on other areas of best practice.
In summary, this Remove Stale Asset article is part of our Best Performance Series. This series is intended to show how to optimize and effectively manage your Qualys subscription and use it in process automation. For questions and further assistance, schedule a time to meet with our Solutions Architects and Product Managers; we are here to help.