Not Your Average FIM: Why Customers Choose Qualys FIM
Choosing the right FIM solution is a crucial step for an organization. One should not need professional services just to onboard or manage. Traditional FIM solutions with legacy architecture are either too noisy or too hard to use. The market demands an intelligent FIM solution that is easy to deploy and simple to use.
Qualys File Integrity Monitoring (FIM) is a lightweight and highly scalable cloud service that provides continuous system monitoring of critical files, folders, and registry objects for changes at scale – unlike any other FIM technology available today.
Key Differentiators of Qualys FIM
Fast and Easy To Deploy
One-click activation. You can quickly find the assets not activated for FIM and activate FIM with a single click.
The World’s Most Effective Noise-Canceling FIM
Qualys FIM offers the most efficient alert noise control available in the FIM space. This is beneficial because over 80% of change events are permitted, and thus should not result in an alert or event log. With ‘Trusted Source Status’, you can easily identify the good changes due to patches and security updates and whitelist them.
User can also filter change events produced by a combination of known good users and processes and whitelist them.
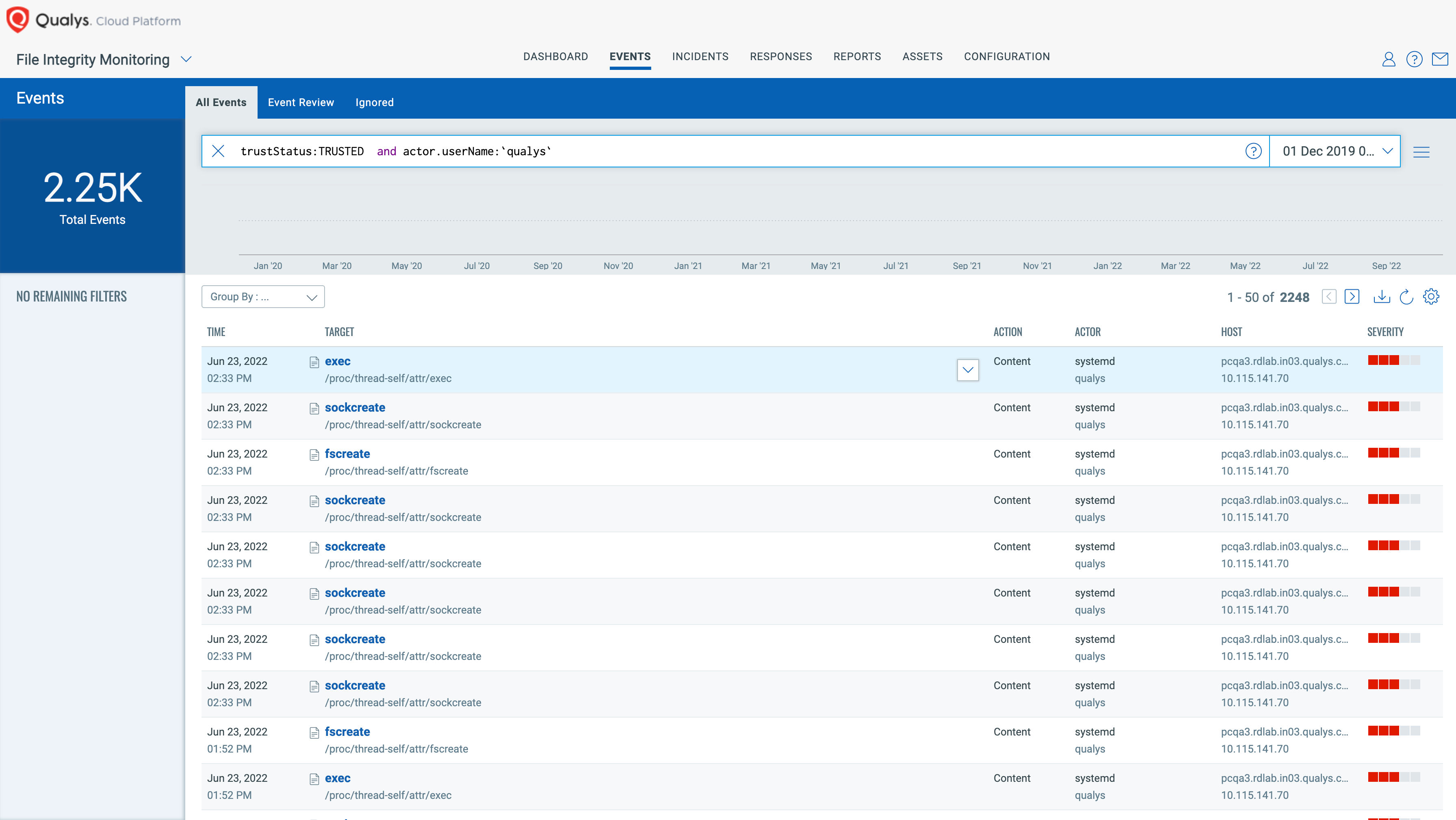
Highlights Unauthorized Changes With Risk Analysis
About 20% of all unauthorized change events will be malicious. With Qualys FIM, you can quickly find unauthorized changes and leverage threat intelligence to find malicious or suspicious events from unauthorized change events. For example, use a query like this: not (actor.userName:’NT AUTHORITY’ or actor.userName:`root`) and (reputationStatus:MALICIOUS or reputationStatus:SUSPICIOUS)
Monitors Dormant and Stale Devices
On average, 30% of assets within any PCI-scoped environment are found to be dormant i.e., assets that have no change-events for an extended duration.
With Qualys FIM, you can easily detect such assets. Basically, this refers to the detection of assets that should have change-events associated with them on a regular basis but have failed to have any events logged recently. This can indicate that the FIM has been disabled on the host, which is a security and compliance concern.
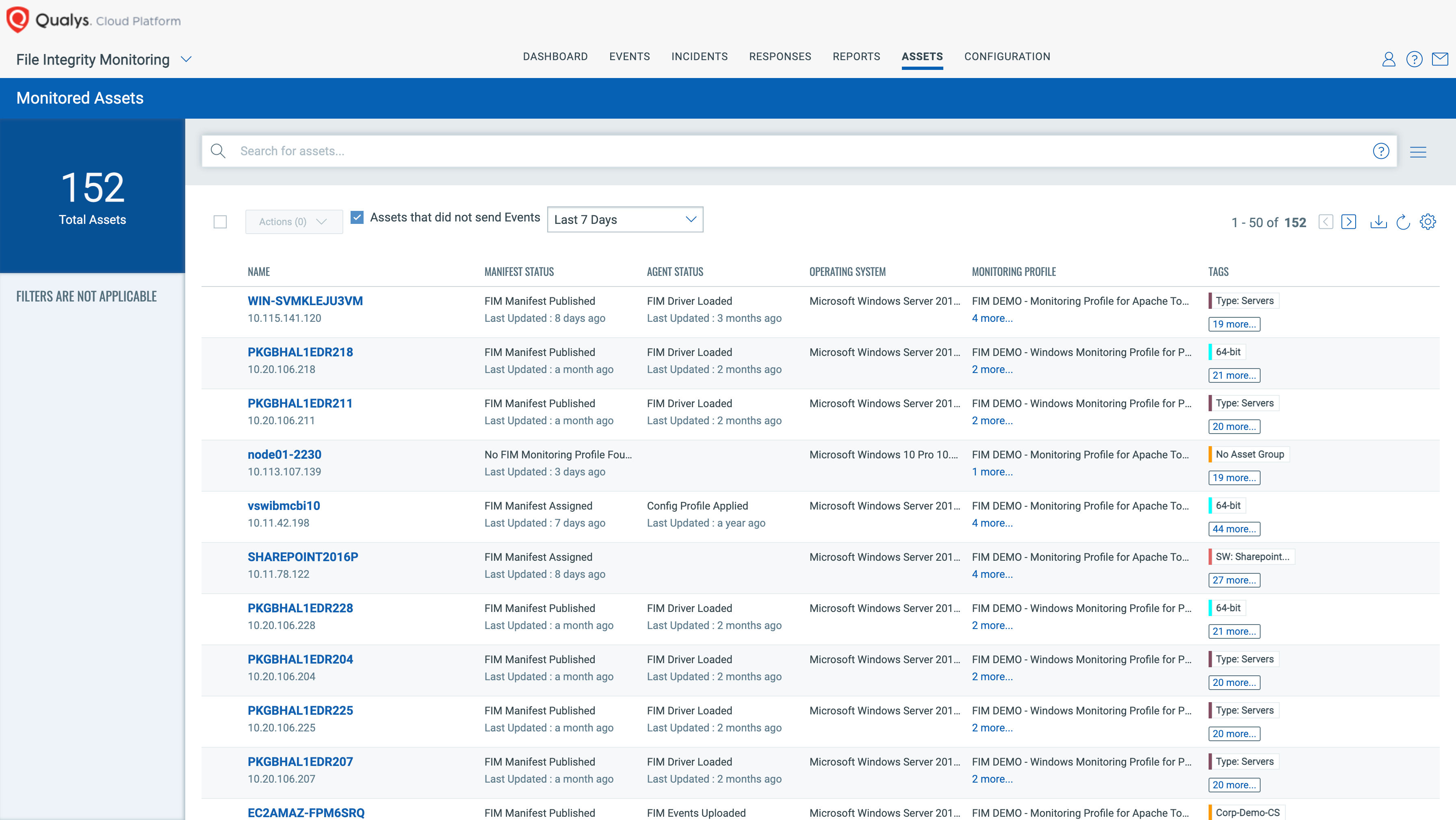
Detects Non-Compliant Assets in Your PCI Scope
FIM is listed in Control # SI-7 (7) & (8) of NIST SP 800-53. PCI DSS v4.0 Requirement 11.5.2 requires that you have a file integrity monitoring system that monitors all your critical files and all the applications files within your environment. Basically, having FIM as a security control is a compliance requirement, but Qualys goes one step ahead!
We not only check if FIM is deployed and activated; we also check the current state of FIM process on each host and generate on-demand and scheduled reports for non-compliant assets i.e., assets on which FIM was activated but not currently running. Such expanded visibility and documentation keeps your organization Audit Ready.
Saves Analyst and SecOps Time
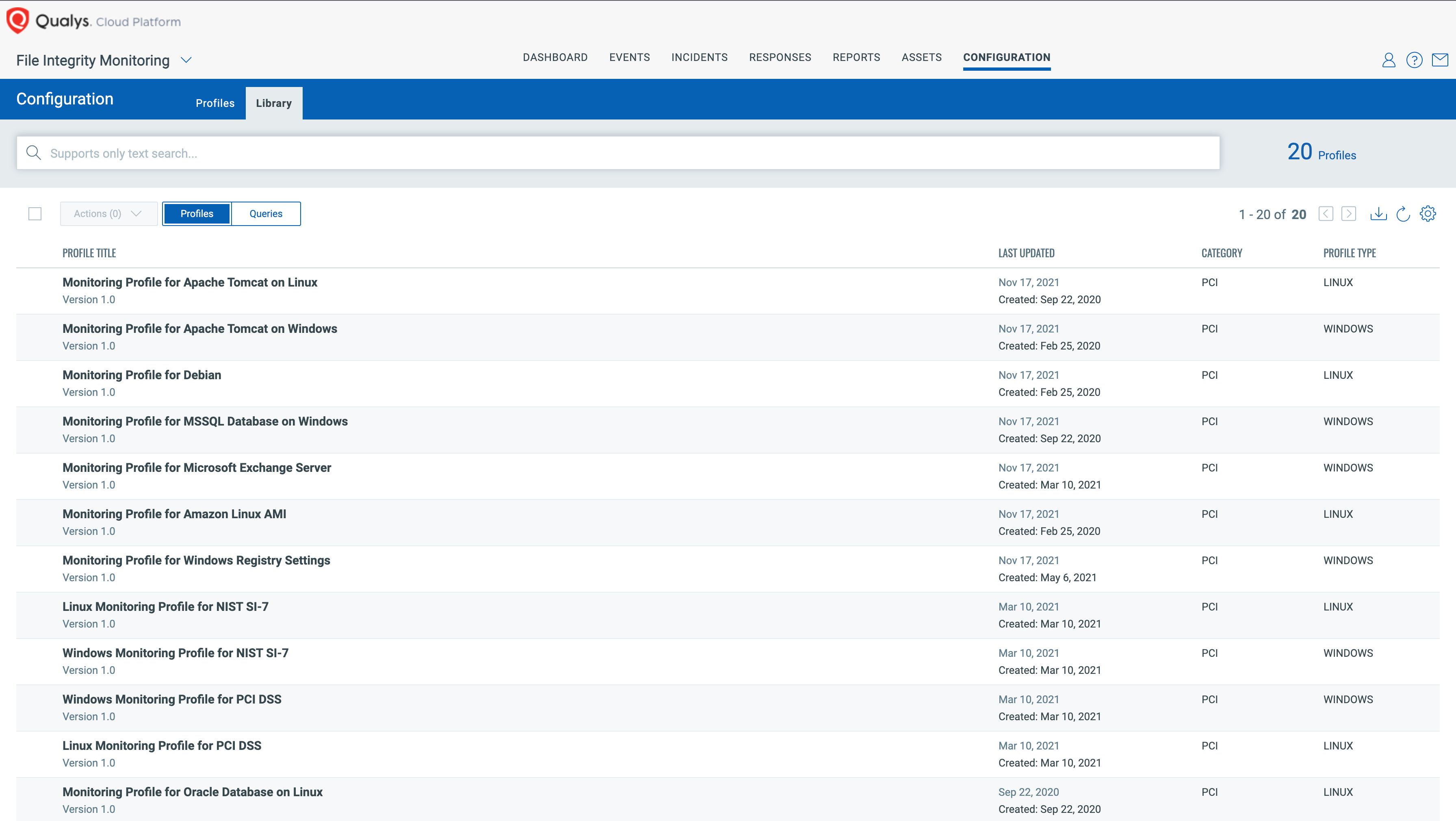
50% of analyst and SecOps time goes into defining what to monitor and manage change events. Thankfully, Qualys FIM contains its own library of out-of-the-box monitoring profiles, empowering analysts with deep insight and the ability to create OOTB profiles to provide you with a set of highly critical files that must be monitored for specific activities.
With Qualys FIM, use of established profiles that match monitoring scope with requirements of each compliance standard to save time and reduce human error.
Contributors
- Mukesh Choudhary, Compliance Research Analyst, Qualys
- Mohd. Anas Khan, Compliance Research Analyst, Qualys
Give Qualys FIM a spin with our 30-day no-cost trial!
Free Trial
Get real-time monitoring of integrity violations across global IT systems
To learn more, explore the links below.