Fingerprinting Web Applications and APIs using Qualys Web Application Scanning
Decoding the impact of Fingerprinting
Organizations develop an effective, actionable go-to-market plan to launch a profitable product into the target market. A go-to-market strategy predicts market demand by analyzing market research, competitor data, and previous examples. Without a solid go-to-market plan, you would not know if you have targeted the right audience, if there is market demand or saturation for your solution, or whether you are too early or late in a given market.
Nowadays, almost everything you can imagine has already been developed. Therefore, development teams often use readily available frameworks and libraries to speed up the release process. In the modern web world, most applications directly or indirectly depend on underlying components such as application frameworks, content management systems, databases, libraries, proxies, web servers, and operating systems that might be highly vulnerable.
Here’s where fingerprinting comes into play. Identifying these underlying components can significantly enhance an attacker’s ability to footprint the application and its environment. An attacker discovers and collects information about the system covertly. In cybersecurity, this is known as reconnaissance. This technique analyzes headers, cookies, HTML elements, scripts, metadata, directory structures, and other readily accessible data to fingerprint technologies in application request/response pairs. If attackers discover critical application infrastructure information, they have found a gold mine.
Qualys Web Application Scanner (WAS) Approach
Qualys Web Application Scanning (WAS) is a cloud-based service that provides automated crawling and testing of custom web applications and APIs to identify vulnerabilities, including cross-site scripting (XSS), SQL injection, and many more. This automated service enables regular testing that produces consistent results, reduces false positives, and easily scales to cover thousands of websites.
With the recent enhancement of our WAS service, we added an advanced proprietary reconnaissance technique that proactively identifies exposed web application components, thus enabling our customers to identify and reduce attack vectors.
How Qualys WAS Fingerprints Web Applications and APIs
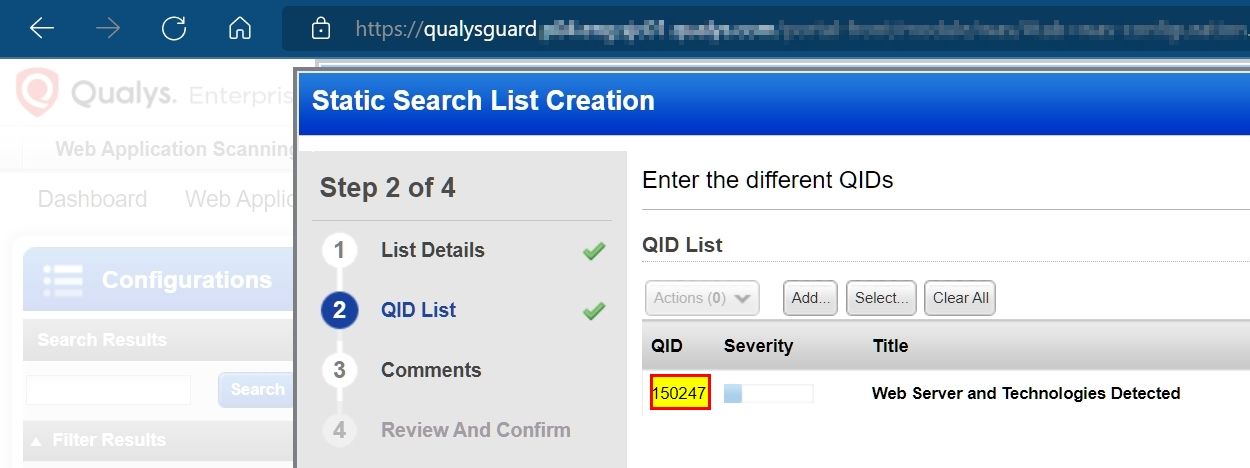
By scanning applications, Qualys WAS identifies and reports the exact versions of popular components and information on the application infrastructure. It passively inspects the application response, including headers, cookies, body, meta, and script tags, using pre-computed regex patterns. QID 150247 – Web Server and Technologies Detected, a unique detection identifier, lists the technologies identified during a scan.
Qualys WAS detects over 120 technologies, including AEM, AngularJS, Apache, Bootstrap, CentOS, Django, Docker, Drupal, Express, Fedora, Flask, FreeBSD, Laravel, Microsoft ASP.NET/IIS/SharePoint, Nginx, Nuxt.js, OpenSSL, PHP, Red Hat, Scientific Linux, Ubuntu, Unix, Windows Server, and more. The list does not end here…we’re always adding new technologies!
With our Out-of-Band Detection methodology, Qualys WAS minimizes false positives and negatives by detecting known vulnerabilities and common misconfigurations.
Here are some detections for Adobe Experience Manager (AEM), a popular content management system:
| QID 150405 | Adobe Experience Manager: Set Preferences Exposed |
| QID 150406 | Adobe Experience Manager: Merge Metadata Exposed |
| QID 150407 | Adobe Experience Manager: Default Get Servlet Exposed |
| QID 150408 | Adobe Experience Manager: Query Builder Servlet Exposed |
| QID 150409 | Adobe Experience Manager: GQL Servlet Exposed |
| QID 150410 | Adobe Experience Manager: Guide Internal Submit Servlet Exposed |
| QID 150411 | Adobe Experience Manager: POST Servlet Exposed |
| QID 150412 | Adobe Experience Manager: Create JCR Nodes |
| QID 150414 | Adobe Experience Manager: Login Status Servlet ExposedQID 150415 |
| QID 150415 | Adobe Experience Manager: Current User Servlet Exposed |
| QID 150416 | Adobe Experience Manager: User Info Servlet Exposed |
| QID 150417 | Adobe Experience Manager: Felix Console Exposed |
| QID 150418 | Adobe Experience Manager: WCM Debug Filter Exposed |
| QID 150419 | Adobe Experience Manager: WCM Suggestions Servlet Exposed |
| QID 150420 | Adobe Experience Manager: CRXDE Lite/CRX Exposed |
| QID 150421 | Adobe Experience Manager: Disk Usage Report Exposed |
| QID 150422 | Adobe Experience Manager: Reflected XSS via SWF |
| QID 150423 | Adobe Experience Manager: WebDAV Exposed |
| QID 150424 | Adobe Experience Manager: Groovy Console Exposed |
| QID 150425 | Adobe Experience Manager: ACS Tools Exposed |
| QID 150426 | Adobe Experience Manager: SSRF via Salesforce Secret Servlet |
| QID 150427 | Adobe Experience Manager: SSRF via Salesforce Secret Servlet |
| QID 150428 | Adobe Experience Manager: SSRF via Site Catalyst Servlet |
| QID 150429 | Adobe Experience Manager: SSRF via Auto Provisioning Servlet |
| QID 150430 | Adobe Experience Manager: SSRF via Open social |
Qualys WAS Scan Configurations
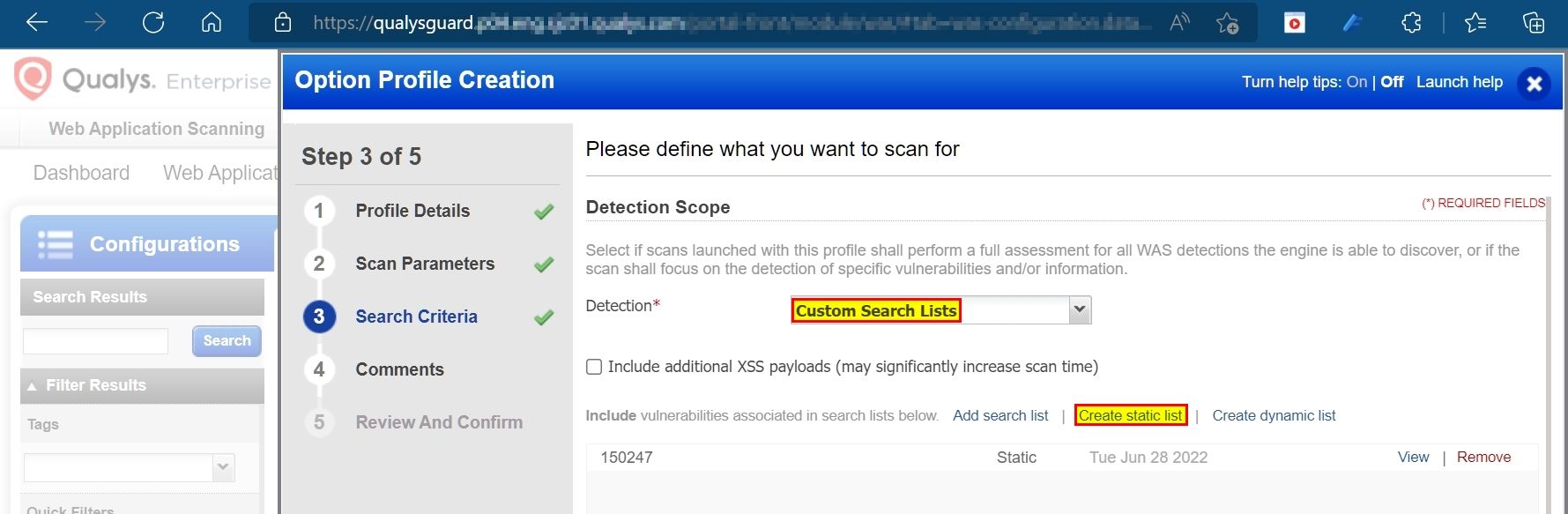
Configuring Qualys WAS Scan is straightforward. In the Search Criteria pane, follow one of the methods below to scan with QID 150247:
Choose Information Disclosure:
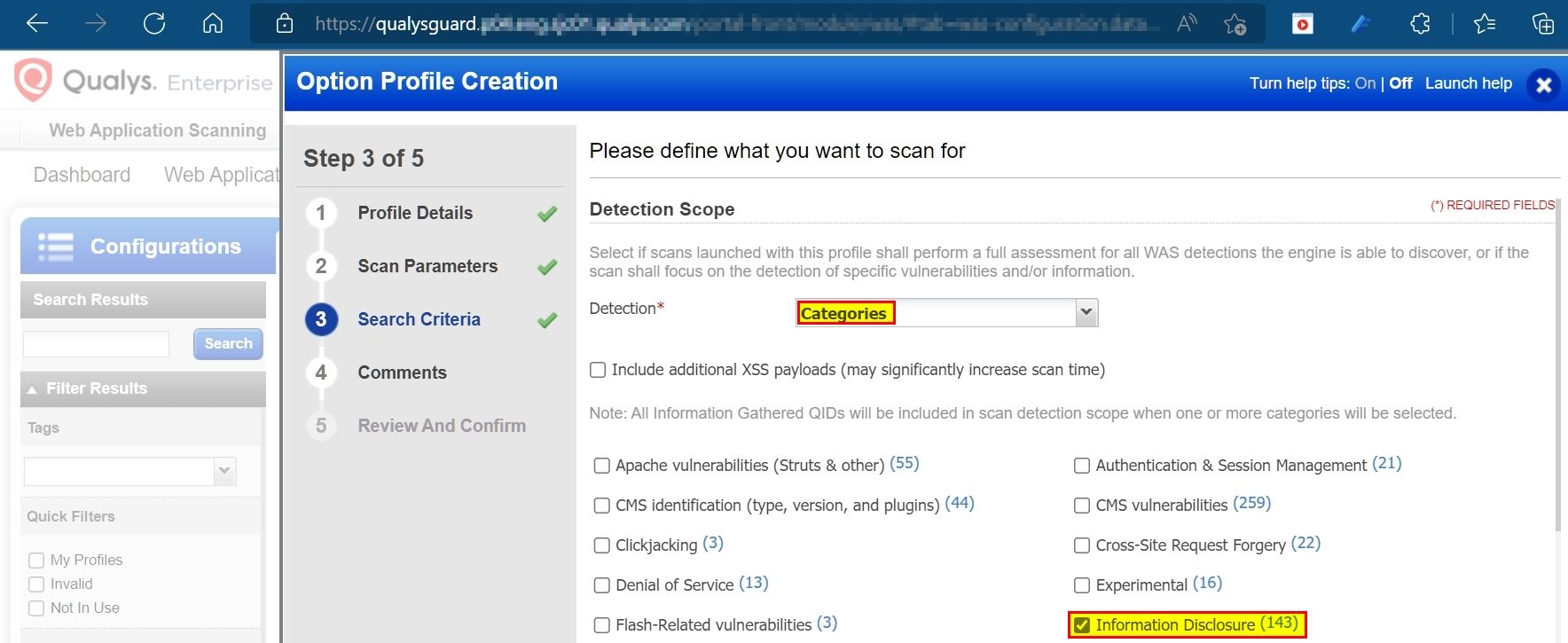
Make a static list of QID 150247:
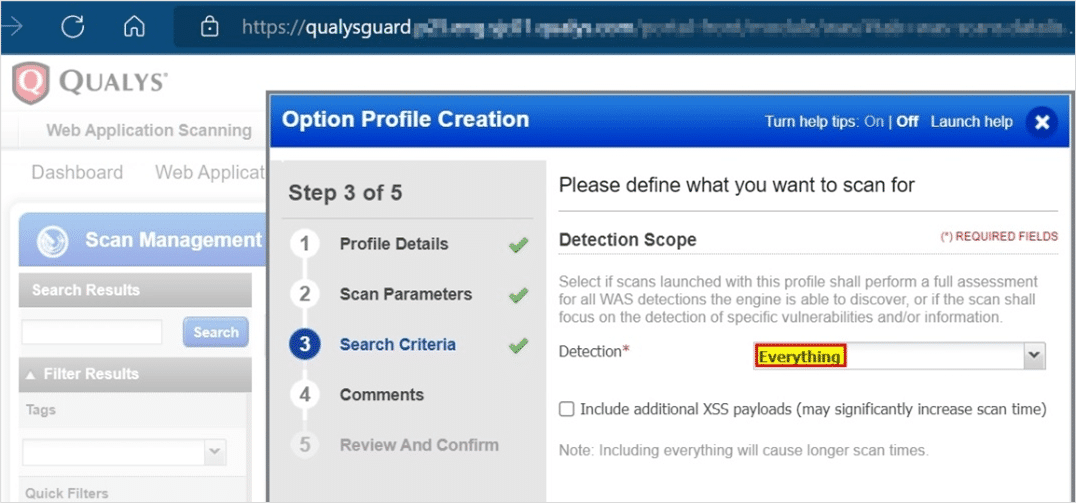
In the Detection Scope configuration, select Everything. During the discovery phase, the scan detects and displays all technologies.
Qualys WAS Scan Report
The Qualys WAS Scan Report section allows you to analyze the report after completing the scan. When here, search for QID 150247 Web Server and Technologies Detected.

Reading the Report
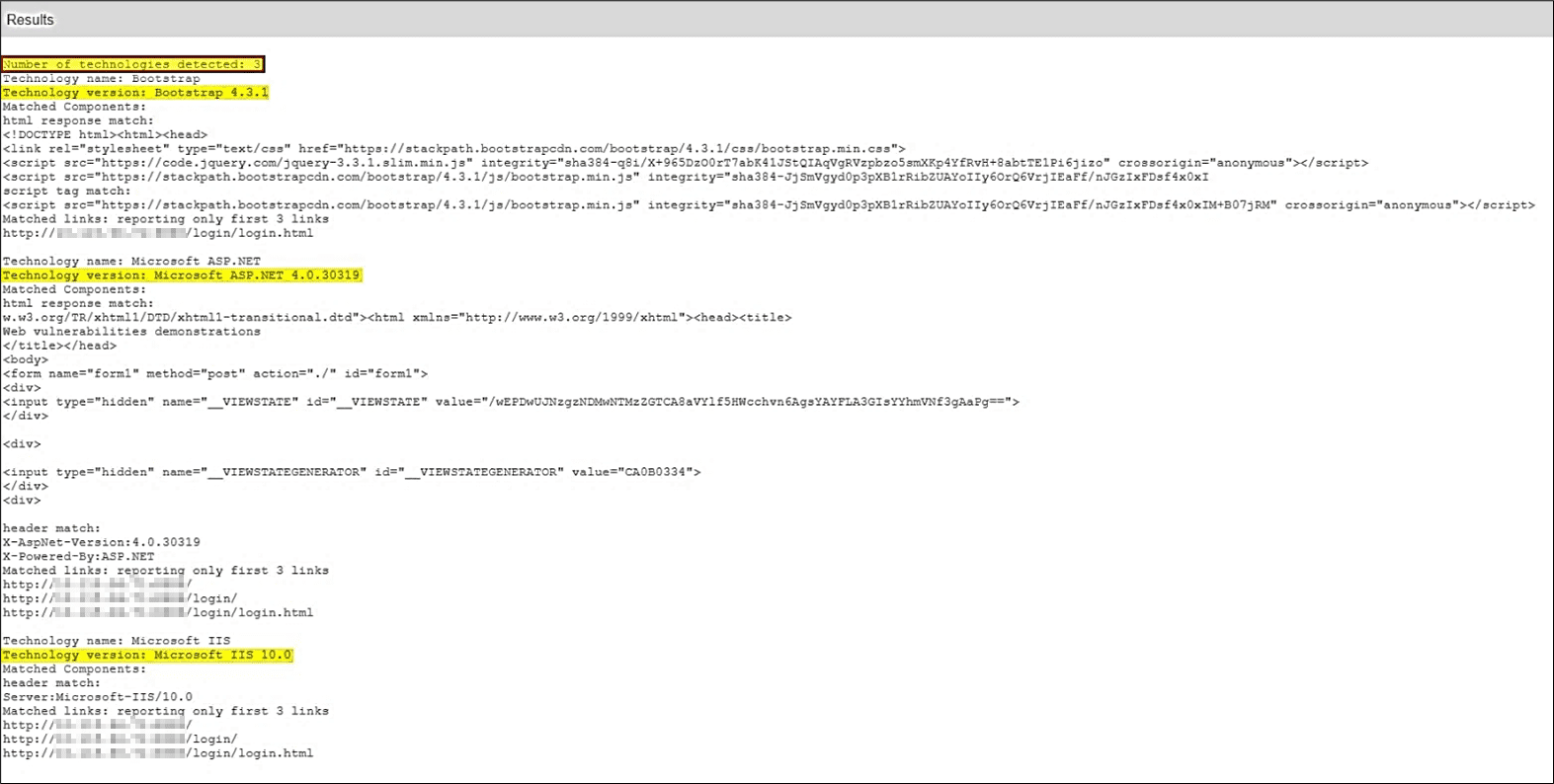
QID 150247 report shows you the following information:
- Total number of detected technologies
- Detected technologies’ names and versions
- For each technology, headers, HTML responses, metadata, scripts, etc., that matched
- Identifying the first few instances of the above information, that is, the links containing the matched technology
Takeaway
As complex environments become more prevalent and organizations increase their use of GTM, attackers have more potential to exploit exposed web application components. As a result of our existing best practices for web application scanners (WAS), vulnerability assessments, and risk management, we provide organizations with an invaluable tool for protecting their infrastructure and reducing attack vectors.
More Information
We invite you to join us on the journey. Are you interested in trying Qualys? Register for a free trial. You can also request a demo from one of our technical account representatives. The Qualys community is also a great place to learn more about Qualys products and share your experiences.
Contributors
- Sheela Sarva, Director, Quality Engineering, Web Application Scanning, Qualys
- Srinivas Dambal, Manager, QA Web Application Scanning, Qualys
- Ed Arnold, Security Solutions Architect, Qualys
- Ambika Singh, Senior Writer, Technical Content Experience, Qualys
Learn More
- https://www.qualys.com/apps/web-app-scanning/
- https://cwe.mitre.org/data/definitions/200.html
- https://capec.mitre.org/data/definitions/224.html
- https://owasp.org/www-project-automated-threats-to-web-applications/assets/oats/EN/OAT-004_Fingerprinting.html
- https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/01-Information_Gathering/
- https://owasp.org/Top10/A05_2021-Security_Misconfiguration/
- https://owasp.org/Top10/A06_2021-Vulnerable_and_Outdated_Components/
- http://projects.webappsec.org/w/page/13246925/Fingerprinting