Don’t spend another weekend patching Chrome
As we head into the weekend, Google has released an emergency security update for the Chrome desktop web browser to address a high-severity vulnerability known to be exploited in the wild. This is the seventh Chrome zero-day fixed this year by Google. This security bug (CVE-2022-3723; QID 377721) is a type-confusion flaw in the Chrome V8 JavaScript engine.

Google has not shared details on the nature of attacks in which this vulnerability is exploited but mentioned they are aware of reports that an exploit for this vulnerability exists in the wild.
The vulnerability is a “type confusion” that affects the V8 component of Chrome. Typically, when a piece of code does not verify the type of object given to it and uses it blindly without type-checking, it leads to type confusion.
Type confusion can be extremely dangerous; sometimes, this can lead to code execution. By accessing memory regions that should not be accessible from the context of the application, an attacker could read sensitive information of other apps or cause crashes.
Attacks on the V8 component of Chrome are not typical but are among the most dangerous. Google does not define the level of activity concerning the exploitation that exists in the wild, so whether attacks using CVE-2022-3723 are across-the-board or limited is unknown now.
Zero Day and Third-Party Applications
Zero-day attacks in third-party business applications are a preferred and easy way for threat actors to find their way into your organization. As such, ensuring all end users’ desktops and laptops are patched – as soon as the zero-day fix is released is a critical task for every security and IT person.
However, too many organizations struggle to remediate third-party application vulnerabilities expeditiously and oftentimes, rely on the application’s auto-update mechanism. Unfortunately, auto-update may or may not work in a timely manner, and enforcement and tracking is challenging.
Respond Faster with Zero Touch
It is highly recommended to treat desktop and laptop patching differently than server and production patching. In most cases, the risk of patching a desktop application and breaking core business functionality is lower than causing a severe impact in a production environment. As such applying smart automation to your third-party applications on desktops and laptops will allow organizations to respond faster to new zero-day threats and do it all with little IT intervention or extra work. In other words, once the policy is created, everything else is Zero Touch.
Using Qualys and Zero-Touch Patching to Reduce Risk
As part of Qualys Patch Management, Zero-Touch Patching intelligently identifies the riskiest products in the environment and helps create automation jobs to automatically deploy the proper patches and configuration changes required for remediating vulnerabilities.
Based on Qualys patch prioritization report, applications are ranked based on the number of vulnerabilities they introduced to the environment. Common feedback we hear from our customers is that browsers, including Chrome, are in the top five (5) applications that introduced the most number of vulnerabilities, and therefore risk. Following the recommendation of this report, it is easy for customers to create automated, zero-touch patch jobs to automatically deploy patches to those top third-party applications. As Qualys supports patching these applications right out of the box, once those jobs are deployed, IT teams and security teams do not need any more time with remediation efforts every time a new patch is released. Aren’t you tired of being a weekend remediation warrior?
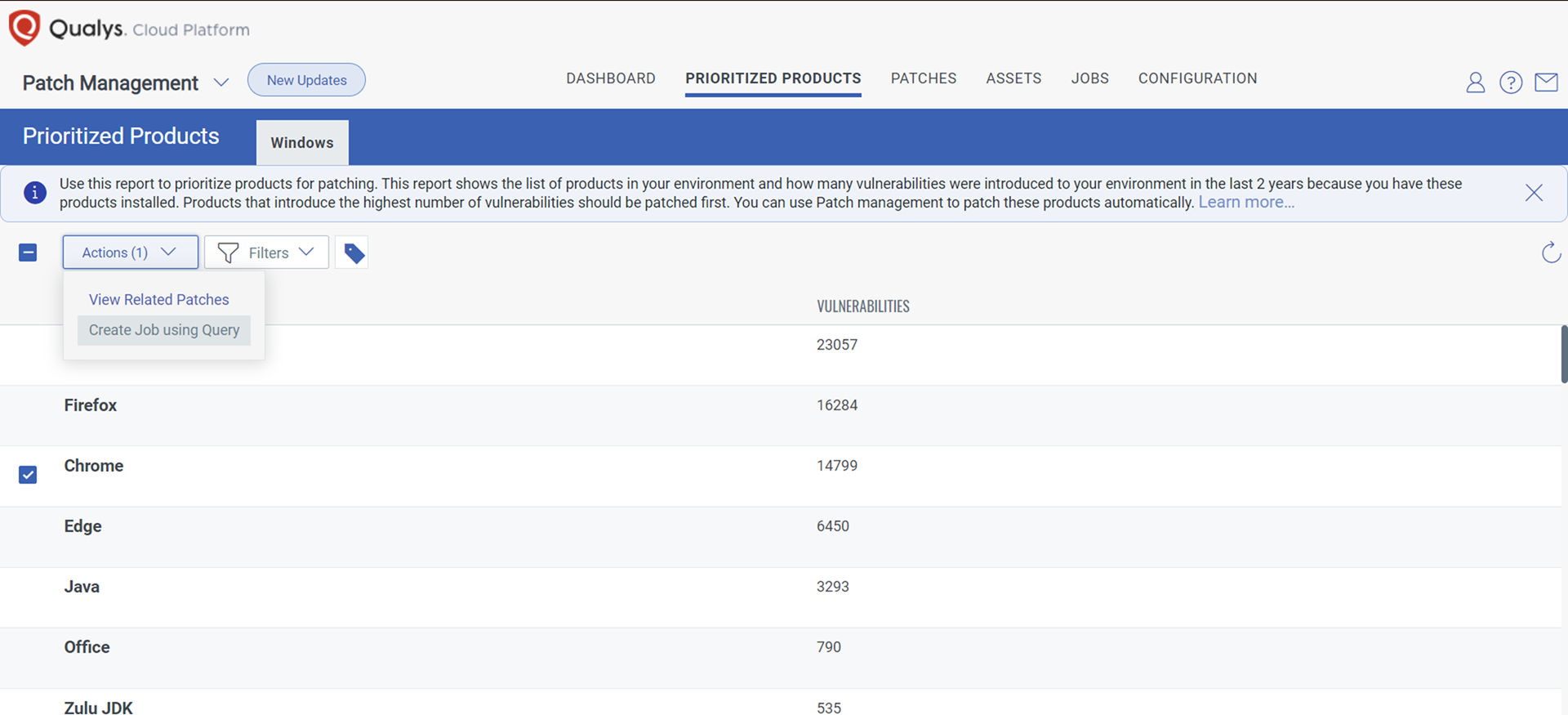
If you are a Qualys customer that does not have Patch enabled, a trial can be enabled quickly – it leverages the same VMDR agent – which will allow you to immediately deploy the Chrome patch to your environment and then create those automation jobs to ensure the next time Google or any other vendor releases a patch, your desktops and laptops are automatically updated.
Contributors
- Saeed Abbasi, Manager, Vulnerability Signatures, Qualys