Effective Vulnerability Management with Stakeholder Specific Vulnerability Categorization (SSVC) and Qualys TruRisk

Security stakeholders across the globe have long relied on the Common Vulnerability Scoring System (CVSS) to prioritize vulnerabilities and assess their risk posture. The reason why the CVSS has become the standard for many security and vulnerability management teams alike is that this method is easy to understand and seemingly informative. However, the CVSS has many limitations with significant implications.
CVSS = Technical Severity, Not Risk
The original intent of CVSS was to identify the technical severity of vulnerabilities, not the level of risk that each vulnerability posed to an organization. So, while it makes sense to have CVSS as a contributing factor for vulnerability prioritization, it would be unwise to guide targeted and informed vulnerability management programs based on it. For example, using the CVSS approach, large portions of all identified vulnerabilities may be classified are ‘critical’ or ‘high’ when they’re not major risks. According to recent research from Qualys on this topic, more than half of the vulnerabilities (51%) classified by CVSS were either high or critical. This leads to inefficient vulnerability prioritization, decision-making, and suboptimal usage of limited resources to reduce cyber risk.
Security practitioners need a metric beyond CVSS to better digest and remediate vulnerabilities according to their impact on business and relevance to key stakeholders within a specific organization. Of course, with the growing number of vulnerabilities (190K) year-over-year, this is easier said than done.
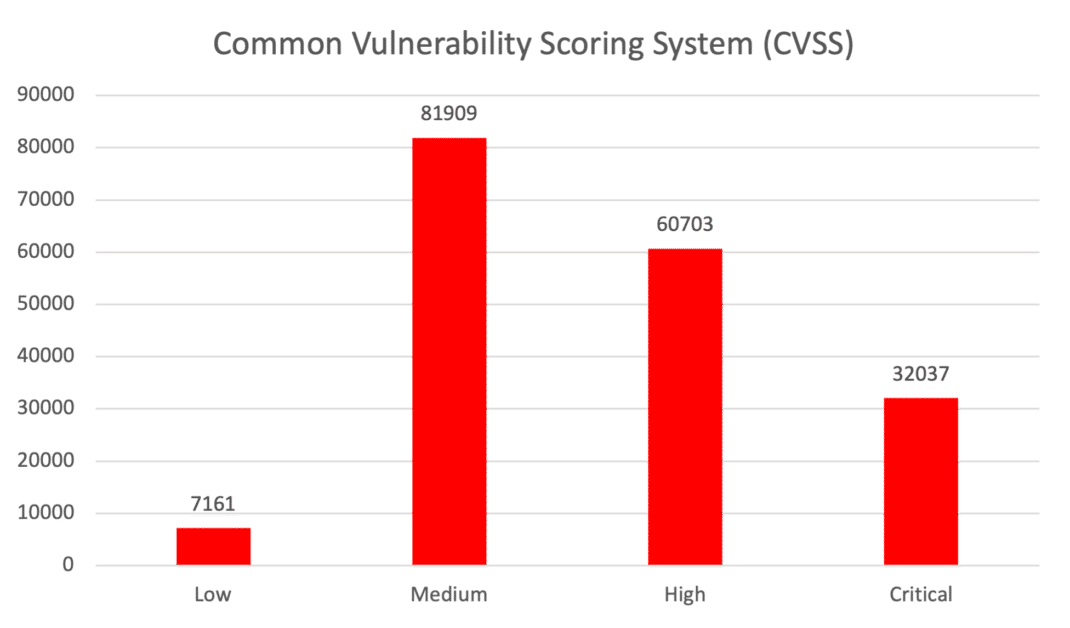
And finally, Vulnerability Management is a stakeholder-centric process. Multiple stakeholders, tools, processes, and priorities need to be accommodated and aligned to achieve one common goal, which is to reduce risk.
Free Trial
Get started with 30-day Free Trial
Stakeholder-Specific Vulnerability Categorization (SSVC)
To address the challenges of the obsolete approach to vulnerability risk scoring, Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with Carnegie Mellon University’s Software Engineering Institute (SEI), recently published a guide for analyzing and prioritizing vulnerabilities. This guide accommodates multiple stakeholders in the vulnerability management lifecycle to improve vulnerability management by framing decisions better using decision trees. The output of the decision tree framework helps organizations determine whether to act immediately on a vulnerability or defer for a later date.
They also published a new Stakeholder-Specific Vulnerability Categorization (SSVC) calculator, which is aimed at helping organizations walk through the decision process referencing each vulnerability’s exploitation status, impact to safety, and prevalence of the affected asset in a singular system.
The CISA SSVC calculator is based on the following five values:
- Exploitation status: Evidence of Active Exploitation of a Vulnerability. This measure determines the present state of exploitation of the vulnerability. There are three decision values: None, Public PoC and Active.
- Technical impact: Technical Impact of Exploiting the Vulnerability. It is similar to the Common Vulnerability Scoring System (CVSS) base score’s concept of “severity”. There are two decision values: Partial and Total.
- Automatable: This represents automating the exploitation events for vulnerability. Automating Steps 1-4 of the Cyber Kill Chain – reconnaissance, weaponization, delivery, and exploitation. There are two decision values: No and Yes.
- Mission prevalence: Impact on assets that provide mission essential functions. Taking into account the criticality of the asset to the organization. There are three decision values: Minimal, Support, and Essential.
- Public well-being impact: Impacts of the affected system compromise the physical, social, emotional, and psychological health of humans. There are three decision values: Minimal, Material, and Irreversible.
Based on the inputs from the above five values, the calculator makes it easier for organizations to determine what to do with them. There are four possible outcomes:
- Track: No action is required. Continue to track within standard update timelines
- Track*: Monitor for changes and remediate within standard update timelines
- Attend: Attention required. Remediate sooner than the standard update timelines
- Act: Attention required. Remediate as soon as possible
Qualys TruRisk: A Risk-Based Approach to Vulnerability Management
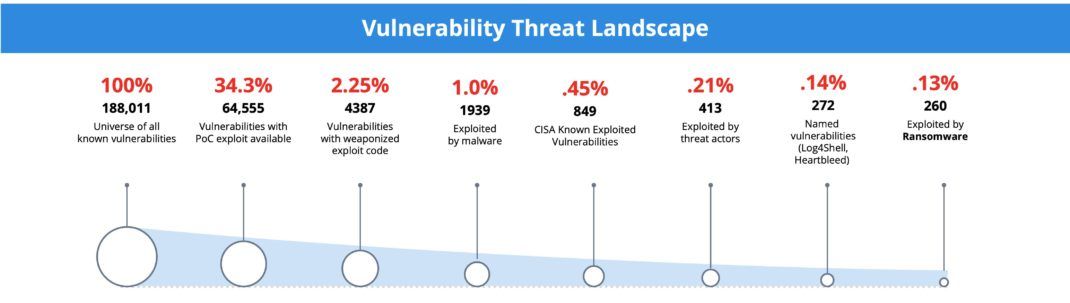
If everything is critical, then nothing is critical. This fact is highlighted when you consider that less than 3% of all vulnerabilities cause the most risk.
In addition, the time of weaponization of vulnerabilities continues to drop, weaponizing on average 2x faster than the time it takes vulnerability management teams to remediate them.
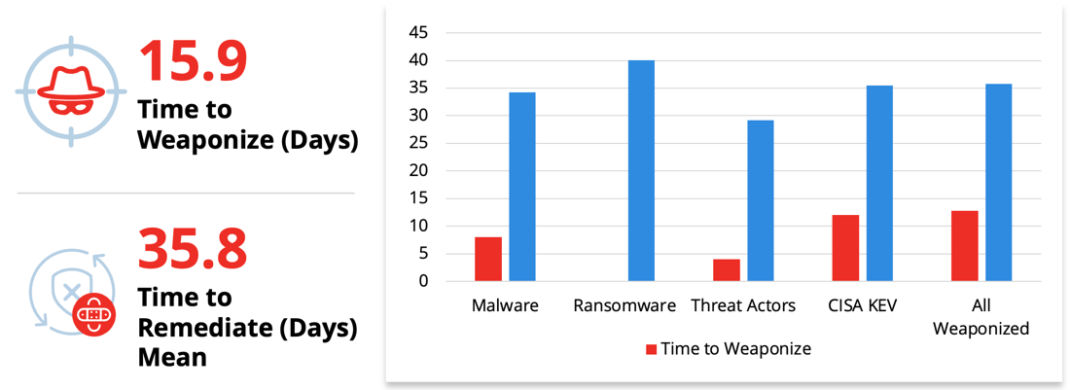
Understanding the business context and risk that a vulnerability poses to an organization is critical for reducing the gap between weaponization and remediation to reduce risk. To make smarter decisions, IT teams must consider multiple data points across vulnerabilities, assets, and other exposures. Complete asset information includes, but is not limited to:
- How critical is the asset?
- Is the asset mission critical to the business?
- Where is the asset located?
- Is the asset internal or internet-facing?
- What is the exploitation status of the vulnerability?
- Is the vulnerability exploited in the wild? – If so, who is exploiting it (ransomware groups/malware)?
- Does exploitation lead to complete system compromise?
- What is the exploit code maturity?
- Can the vulnerability be easily weaponized through automation for mass exploitation?
- Is the system hardened based on best practice guidelines so that the risk of exploitation is reduced?
Aligning Qualys TruRiskTM with SSVC
In mid-2022, Qualys answered these challenges by revolutionizing the VM space by adding a fully transparent risk-based approach to vulnerability assessment with the introduction of Qualys TruRiskTM as part of the unparalleled detection and response capabilities of VMDR.
TruRiskTM automatically assesses asset criticality, its location, the misconfigurations found on the system, and any compensating controls applied to the asset to reduce risk. Additionally, Qualys integrates with 25+ threat and exploit intelligence sources to incorporate a wide array of vulnerability intelligence into the risk assessment capabilities of TruRiskTM.
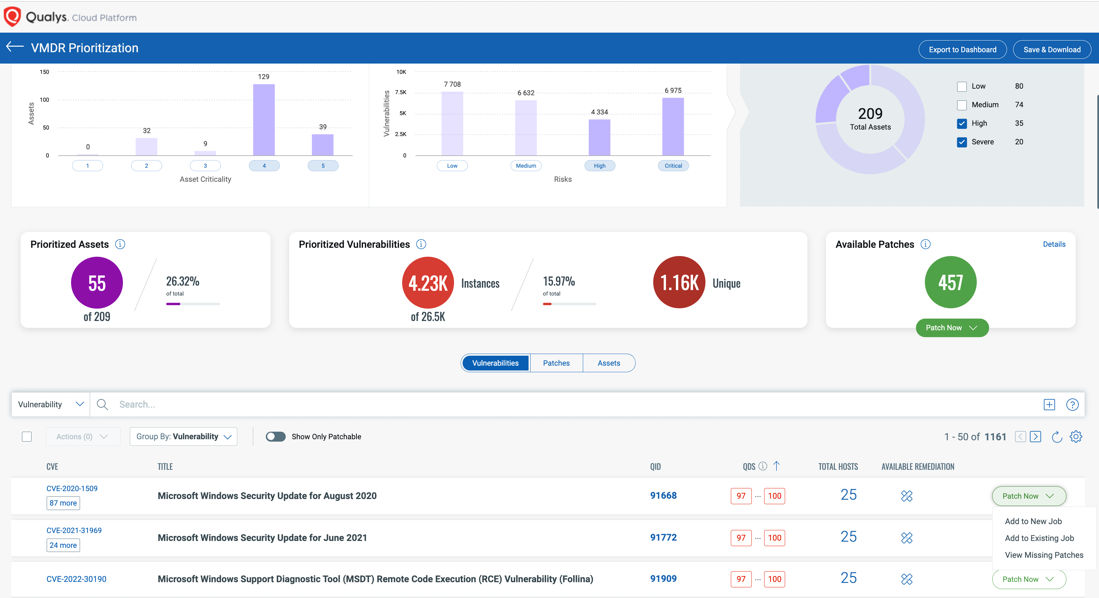
To help with prioritization, TruRiskTM computes two risk scores – Qualys Detection Score (QDS) for vulnerabilities and Asset Risk Score (ARS) for assets. These scores are very easy to understand and are clearly visualized within a unified dashboard.
Similar to the CISA SSVC outcomes, TruRiskTM provides these scores in the 4 categories – Low, Medium, High, and Critical: ranging from 1 to 100 for the QDS and 1 to 1000 for the ARS. SSVC outcomes are Track, Track*, Attend and Act.
Here are some examples of QDS and ARS scores guidance that we give our customers and how they are aligned with the CISA SSVC guidelines:
| QDS Score | QDS Category | Description | Mapping to SSVC |
| 90-100 | Critical | CVSS Critical, exploited in the wild, weaponized exploit available, trending on social media, dark web | Act |
| 70-89 | High | CVSS Critical, exploited in the wild, weaponized exploit available, trending on social media, dark web | Attend |
| 40-69 | Medium | CVSS critical, no exploits available. CVSS High, a Proof of Concept (PoC) exploit is available | Track* |
| 1-39 | Low | CVSS Medium, a PoC exploit is available CVSS Low, no PoC exploit available | Track |
| ARS Score | ARS Category | Description | Mapping to SSVC |
| 850-1000 | Severe | Critical asset with multiple critical or high vulnerabilities | Act |
| 700-849 | High | High value asset with multiple number of critical or high vulnerabilities or is exposed to the internet | Attend |
| 500-699 | Medium | Moderate value asset with critical or high vulnerabilities | Track* |
| 0-499 | Low | Low value asset with multiple vulnerabilities | Track |
Integrated Remediation
One of the biggest challenges for IT teams is finding resources for patching vulnerabilities and misconfigurations. Qualys TruRiskTM allows IT teams to prioritize remediation based on vulnerabilities or the criticality of assets. Qualys Patch Management integrates with TruRiskTM, thus shortening the gap where organizations are exposed to critical vulnerabilities.
By adopting a single unified solution for both vulnerability management and patch management, organizations, both large and small, reduce their Mean time to remediate (MTTR). With this integration, IT teams can create a zero-touch automation job to patch non-mission critical assets that will automatically execute as soon as a new vulnerability with a Qualys Detection Score >90 is detected. This automation instructs Qualys Patch Management to find the right patches and automatically deploy them to the assets. IT teams are now proactive and faster in addressing newly discovered vulnerabilities with the highest risk to their environment.
SSVC and TruRiskTM
In conclusion, the SSVC is an great framework that aims to improve the vulnerability management lifecycle, by accommodating multiple stakeholders through improved decision-making using decision trees. Its ultimate goal is to aid organizations in better prioritization, helping them swiftly identify when to act and when to defer.
Similarly, Qualys TruRisk is designed to drive these outcomes, assisting organizations in better prioritization and risk reduction. The core factors taken into account by the SSVC model, including exploitation status, technical impact, and business criticality, directly align with the key factors used by TruRisk for improved prioritization.
For Qualys customers interested in implementing SSVC in their environments, the framework can be swiftly operationalized by adopting Qualys VMDR with TruRisk.