Managing Security Configuration Risk with the Most Comprehensive Configuration Compliance Solution!

Table of Contents
- Why is Security Configuration Management & Compliance important?
- Reduce your attack surface with Robust System Hardening and Continuous Configuration Monitoring
- Achieving and Maintaining Continuous Compliance with Qualys Policy Compliance
- Qualys Policy Compliances CIS Content
- Contribution to CIS Benchmarks
- Out-of-the-Box Content
- DISA-STIG Compliance
- Automation
- Conclusions
- More Information
- Learn More
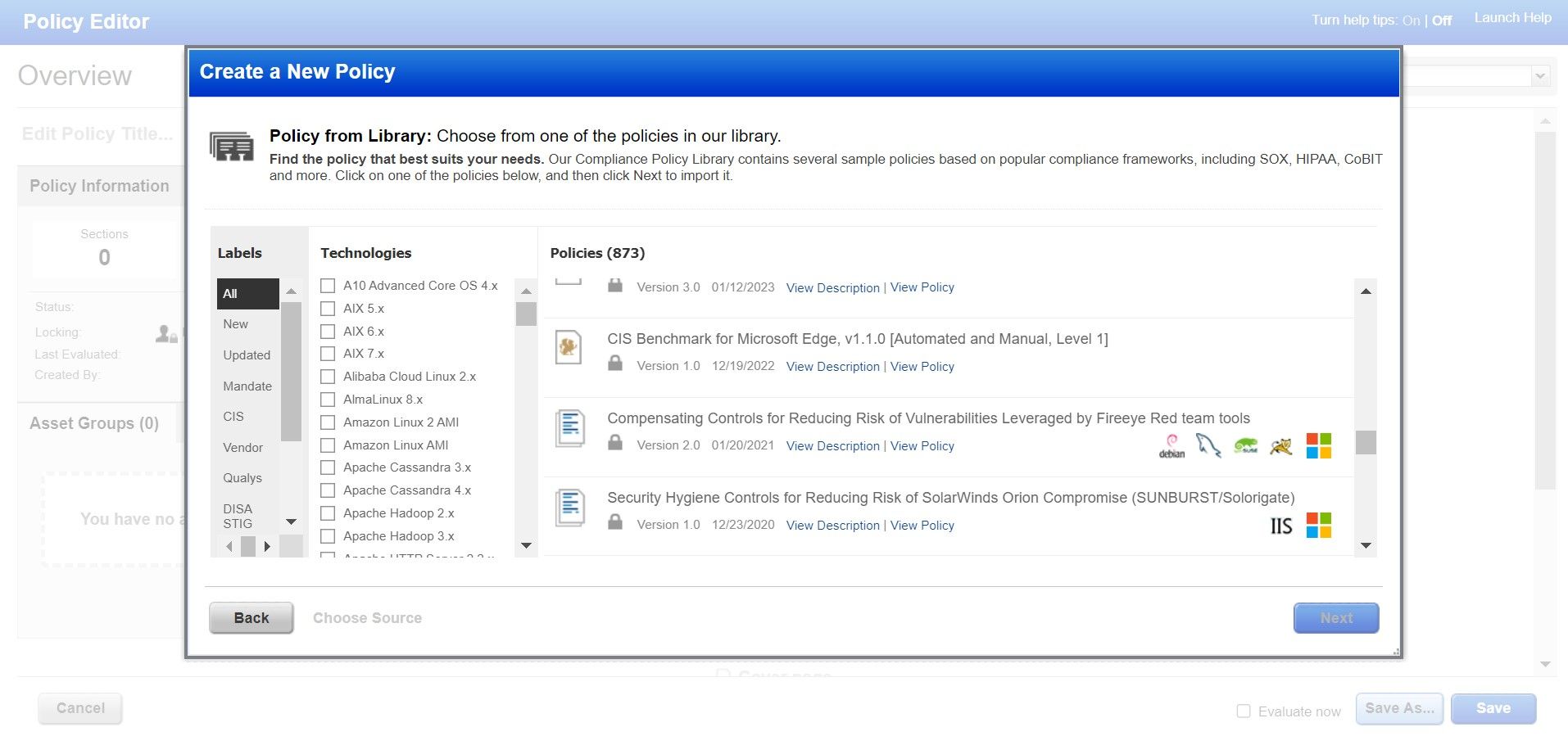
Qualys leads the industry with 850 policies, 19000 controls, 350 technologies, and 100 frameworks
Remote and hybrid work, digital transformation, and customer experience initiatives require rapid and continuous technology additions and changes. This requires continual additions of and deployments for various applications, as well as complex infrastructure changes related to operating systems, servers, containers, databases, web applications, network devices, and firewalls. As such, it’s critical to assess the prevalent risks that exist within an organization’s systems and networks.
Using a solution like Qualys Policy Compliance provides you with an overview of your current security posture by identifying configurations and accessing controls, services, and applications running on critical systems that are unsecure and need security patches. Qualys Policy Compliance can help identify potential vulnerabilities in systems and applications that can be exploited, allowing hackers to access your systems and execute malicious activities.
Why is Security Configuration Management & Compliance important?
In today’s hybrid and modern environment, technologies from AIX, IIS, Oracle to Elasticsearch, MongoDB, middleware, and network devices with misconfiguration risks, such as open RDP or weak access controls, could be exploited, resulting in ransomware or data breach. To manage cyber security risk, Configuration management is essential, as Ransomware attack data shows that RDP misconfiguration is a top three attack vector.
Organizations need to comply and show audit readiness against industry mandates and standards such as NIST/FedRAMP, PCI-DSS, HIPAA, and ISO, and configuration management is a requirement of each mandate. As these standards provide high-level requirements, security & compliance teams leverage industry standards for configuration management like CIS and DISA to help demonstrate compliance.
Reduce your attack surface with Robust System Hardening and Continuous Configuration Monitoring
Cybersecurity has traditionally focused on technologies that prevent threats or assist organizations in recovering from incidents. Firewalls, antiviruses, and endpoint detection and response (EDR) are examples of solutions that protect networks. In today’s world, network security maturity is a constant endeavor and can only happen when you build a secure environment from the ground up.
Regardless of how much you budget for security solutions, if your network or assets aren’t set up securely, they will always be vulnerable. This is where system hardening comes into play.
System hardening reduces an asset’s attack surface – such as a server, operating system, or application. By doing so, an attacker will have fewer ways to gain access to the asset, which is often referred to as reducing your attack surface. Most organizations use existing frameworks and best practices as regulatory requirements or preferred best practices. The National Institute of Standards and Technology (NIST), the Center for Internet Security (CIS), and DISA STIGs offer some of the most popular benchmarks, and Qualys Policy Compliance supports these and many more.
Achieving and Maintaining Continuous Compliance with Qualys Policy Compliance
Qualys Policy Compliance covers more CIS benchmarks as compared to others, including Tenable, Rapid7, Tripwire, and Tanium.
By covering more CIS benchmarks, Qualys Policy Compliance provides visibility into potential risks caused by misconfigurations or insecure default settings in your organization’s infrastructure. According to the experts at CIS, “CIS Benchmarks are best practices for secure configuration of a target system.”
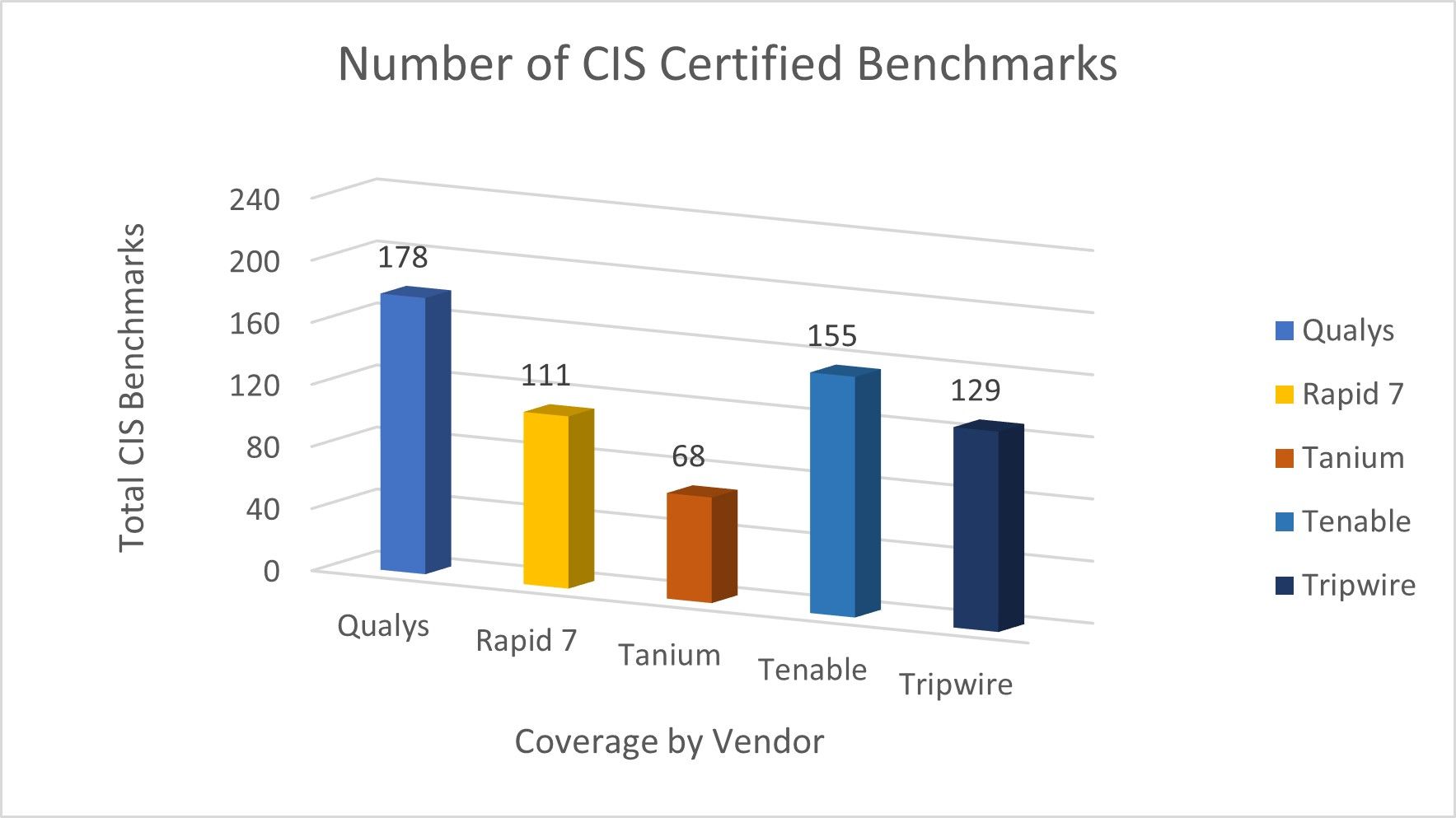
Data for these solutions was obtained from the CIS website, which lists the CIS Benchmarks that each vendor has been certified to use. The CIS Security Software Certification Program has certified Qualys’ products for CIS benchmarks. The Qualys Policy Compliance solution covers most CIS benchmarks, among others.
IT teams and security analysts can map these misconfigurations and identify risks using Qualys’ accurate configuration detections, remediation guidance, and MITRE ATT&CK mappings.
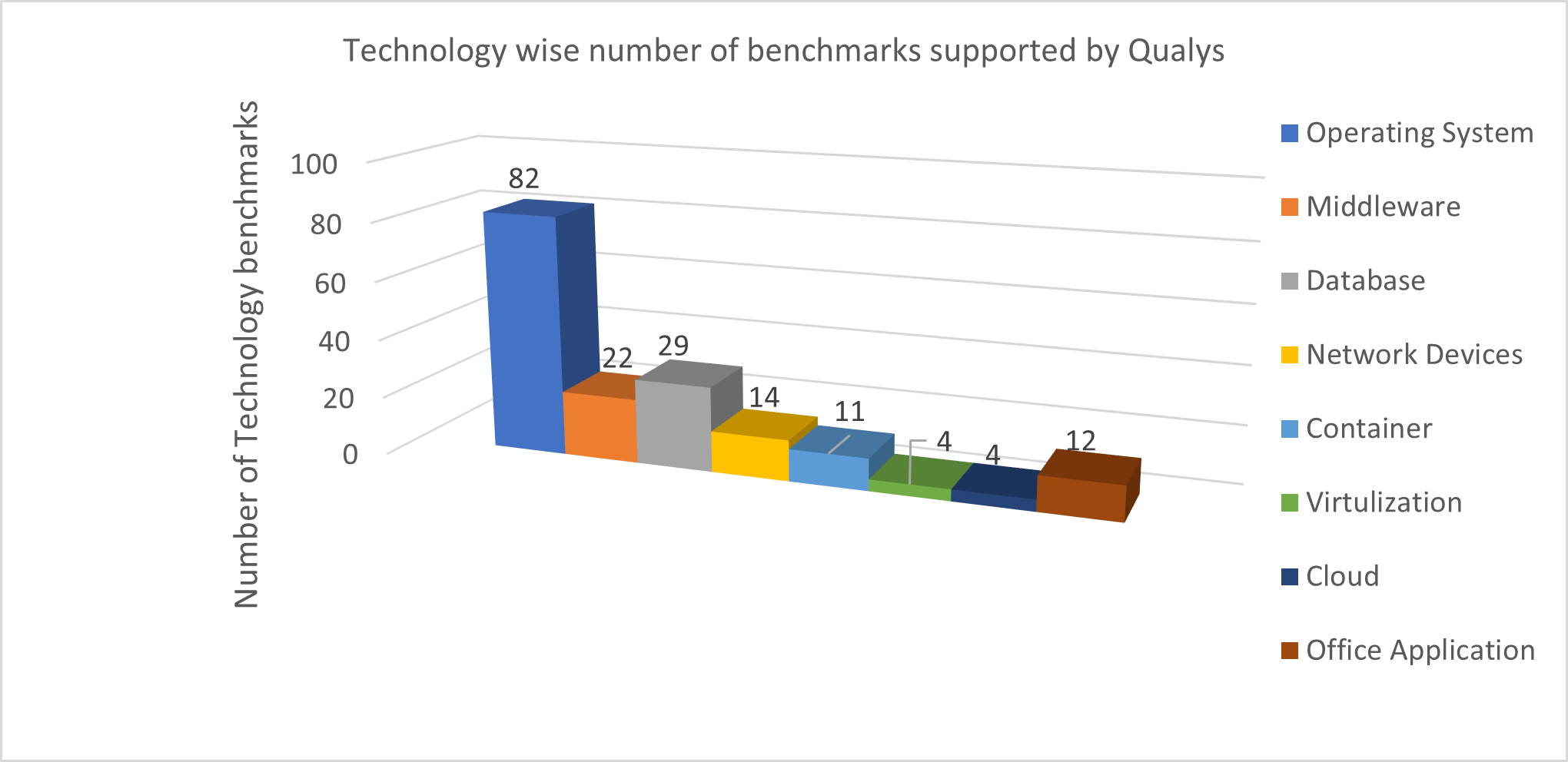
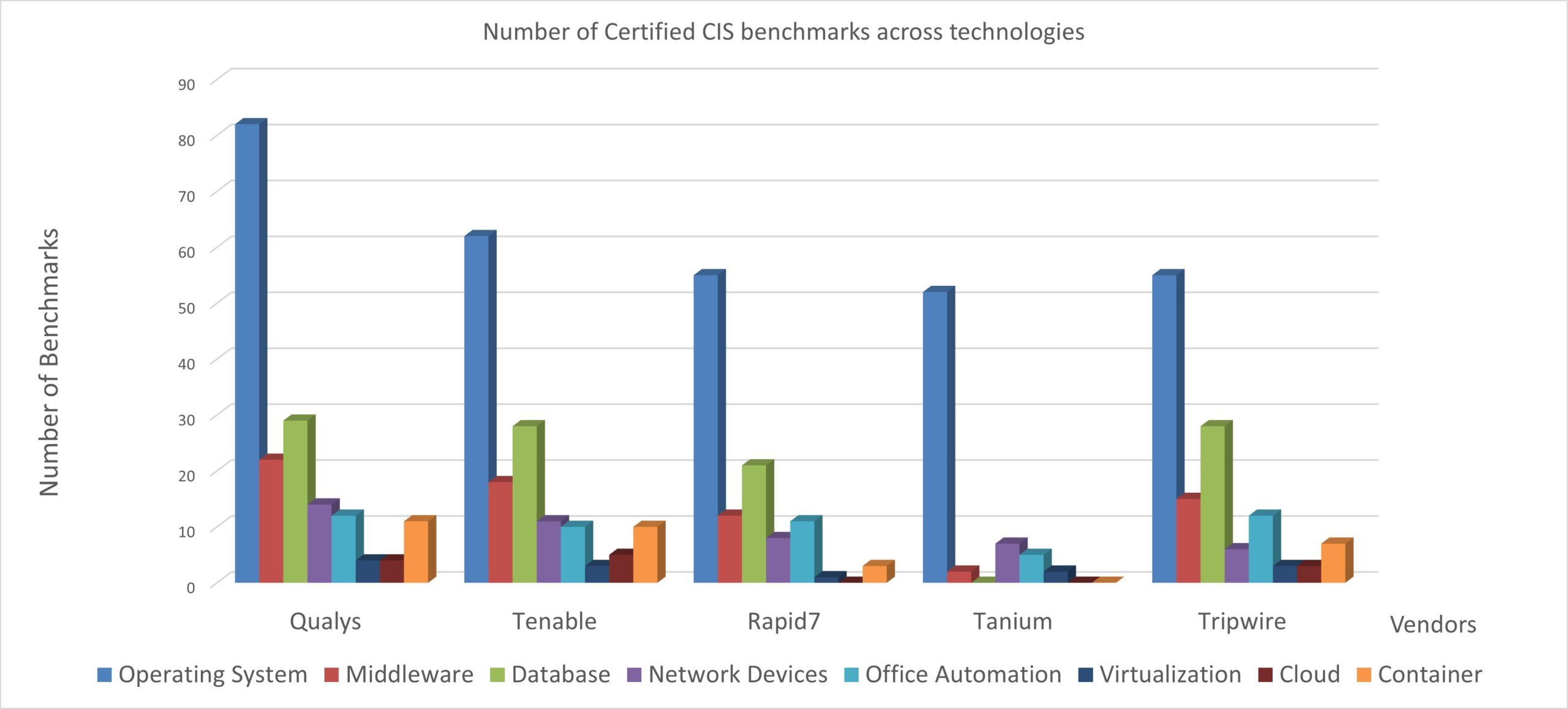
Qualys Policy Compliance’s CIS Content
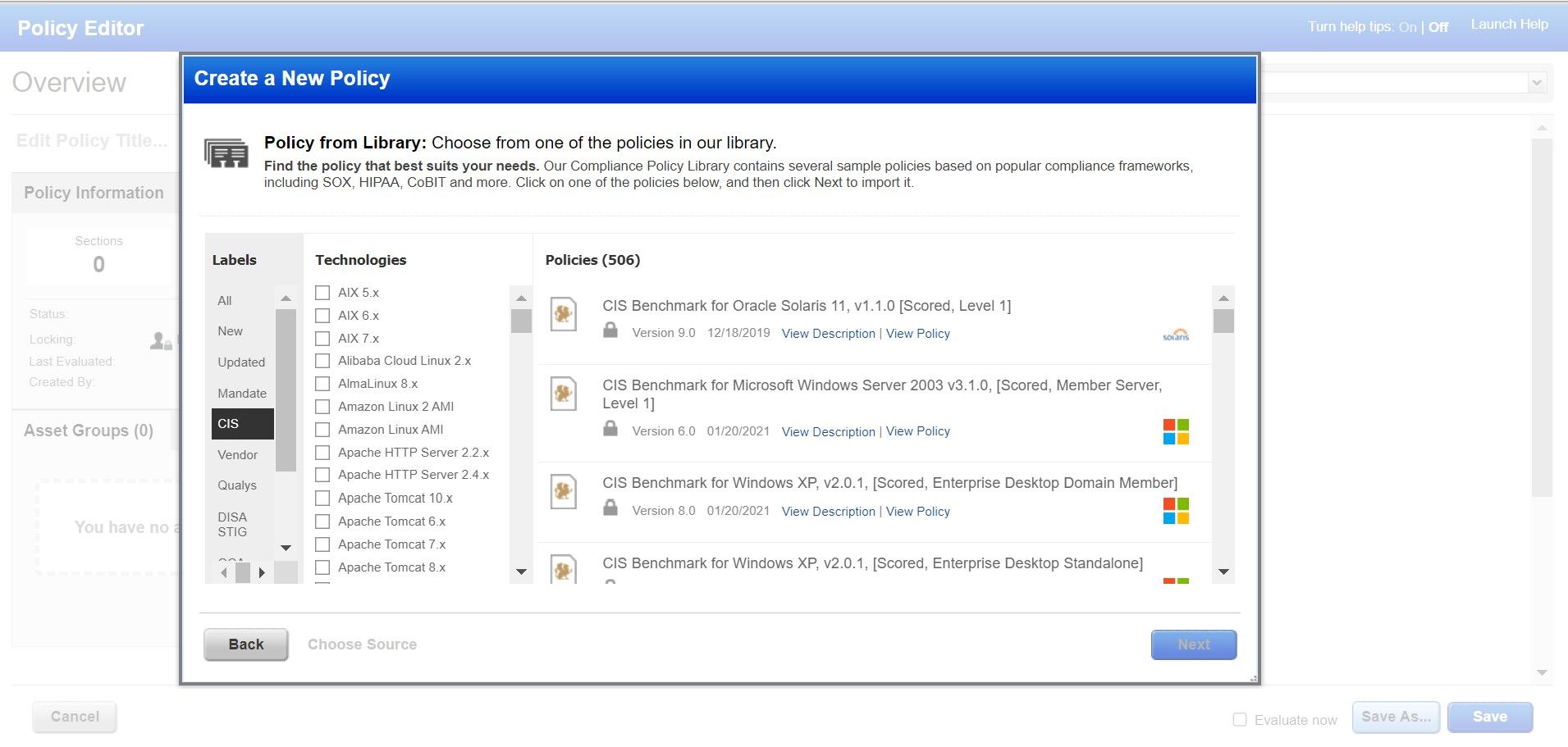
Contribution to CIS Benchmarks
Qualys Policy Compliance researchers contribute far more to the equation than data obtained from CIS; they also contribute to developing these benchmarks by offering security recommendations and improvements for benchmark performance. In addition to benchmarking Checkpoint firewalls and Apache Tomcat, the Qualys Policy Compliance research team has contributed to other benchmarking projects.

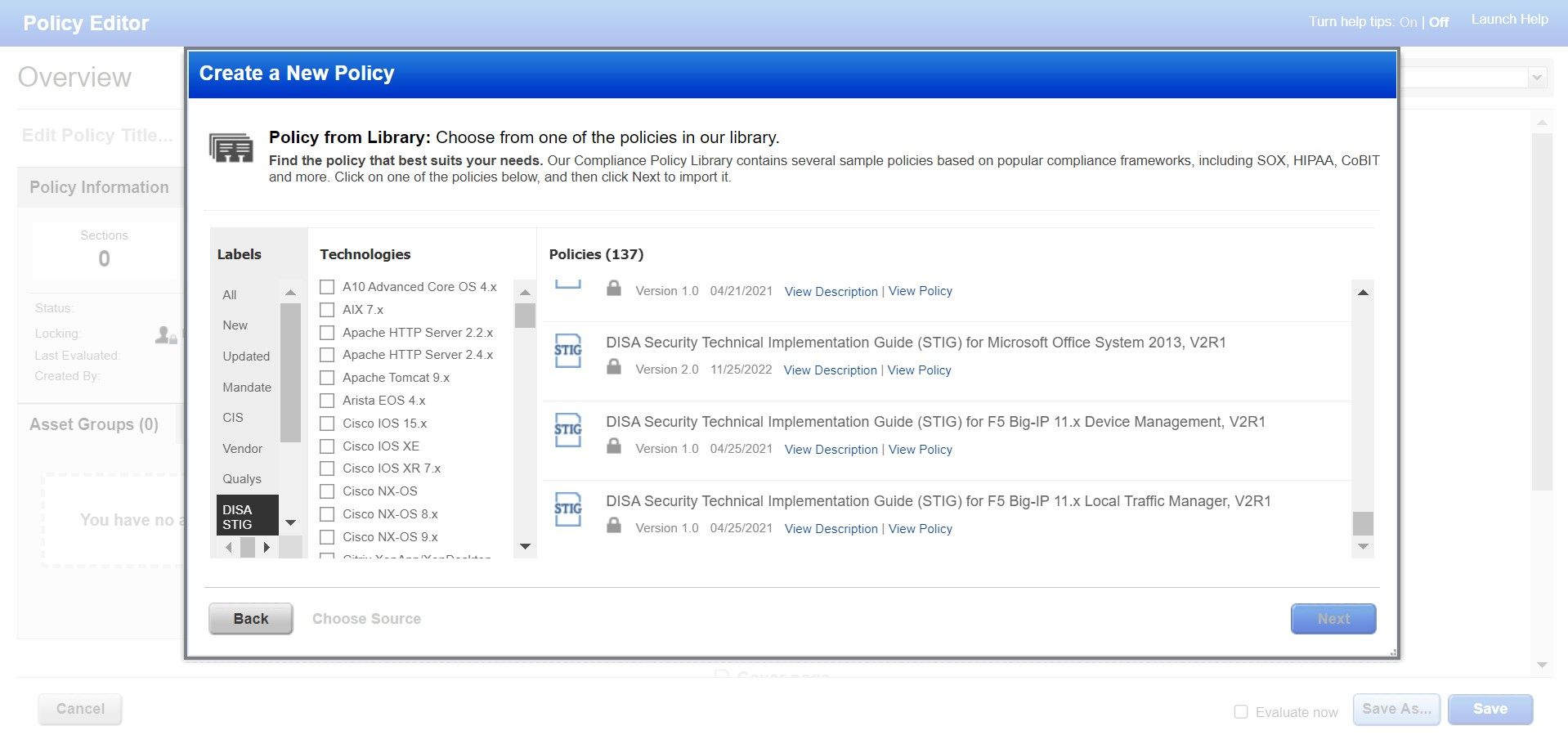
Out-of-the-Box Content
Following industry-standard benchmarks when protecting your network or device is not always enough. Assessing and securing configurations requires a scalable, customized approach. Qualys Policy Compliance provides CIS benchmarks and security templates such as DISA-STIG to offer a holistic approach to network security. Many of these templates are used by federal agencies, as well as for ransomware protection policies and compensatory controls for routinely exploited vulnerabilities.
DISA-STIG Compliance
There are more than 100 DISA-STIG templates supported by Qualys Policy Compliance across multiple technologies, including databases, middleware applications, operating systems, and network devices, etc.
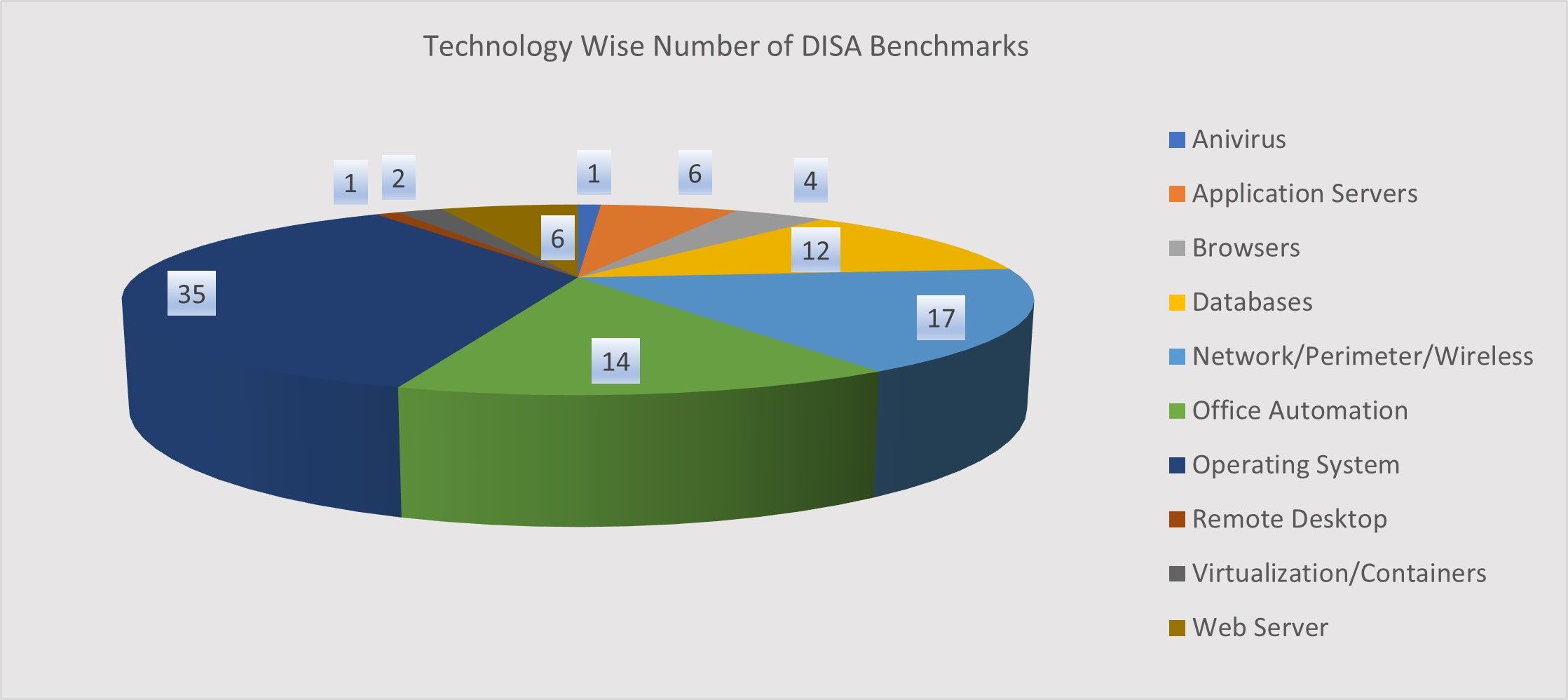
Automation
One of the most important differences between Qualys Policy Compliance and security configuration assessment relates to automation. Organizations have reported a 98% savings in time and effort as compared to manual processes required to remediate misconfigurations and other compliance issues.
Conclusions
Qualys Policy Compliance assesses and hardens your entire technology stack without needing to set up controls from scratch. With Qualys Policy Compliance, your organization will always be audit-ready and reduce the risk of compliance failures, security breaches, brand damage, and litigation.
Qualys leads the industry with 850 policies, 19000 controls, 350 technologies, and 100 frameworks. In addition to the CIS benchmarks, Qualys Policy Compliance ensures that you can pass audits easily for almost any regulation, including PCI-DSS 4.0, HIPAA 2023, GDPR, PSD2, ISO-270001, CCPA, NYDFS, etc. Additionally, Qualys Cloud Platform offers the only FedRAMP High Ready solution in the industry, ensuring you comply with all NIST SP 800-53 requirements.
More Information
We invite you to join us on this journey. Do you want to know how secure your configurations are with Qualys Policy Compliance? Take advantage of Qualys Policy Compliance’s free trial. Alternatively, you can request a demo from one of our technical account representatives.
Learn More
https://blog.qualys.com/vulnerabilities-threat-research/2022/08/23/mitigating-the-risk-of-zero-day-vulnerabilities-by-using-compensating-controls
https://notifications.qualys.com/policy-library/2022/12/22/policy-compliance-library-updates-december-2022