Is your FIM Solution Cost and Time Efficient?
Table of Contents
Virtually every security professional and corporate executive is painfully aware of recent escalations in cybersecurity threats. No one wants to be a headline or get hit with the typical $4.5 million price tag to remediate an incident (IBM Study). Almost every security team will agree that file integrity monitoring (FIM) is a critical component of any security stack to ensure fast and effective identification of unauthorized changes to critical files that can lead to breaches, data loss, brand damage, audit failures, or litigation. Furthermore, a FIM solution is required to adhere to compliance mandates such as PCI-DSS 4.0, FISMA, HIPAA 2023, GDPR, CCPA, and many others.
The question is not whether an organization should have FIM, but which solution provides the most effective, efficient, and economical alternative for your infrastructure.
All FIM solutions are designed to flag changes and determine if they are authorized. However, a good FIM solution must not require you to work for it, but it should work for you in a simple and efficient way that requires intervention only when a true alert is flagged.
If you already have FIM, here are some questions you should answer to determine if you have an adequate solution:
- Does your team spend too much time managing your FIM solution?
- Does your FIM solution introduce alert fatigue?
- Do you have separate agents for different security needs such as FIM, VM, compliance or remediation?
- Is your FIM solution CPU intensive?
- Does your FIM application seamlessly integrate with your VM or other security stack apps?
- Are the capabilities of your current FIM adequate enough to cover all compliance requirements?
Depending upon the answers to any of these questions, you might want to consider a change.
Qualys File Integrity Monitoring (FIM) is a lightweight and highly scalable cloud application that provides continuous system monitoring of critical files, folders, and registry objects for changes at scale. Unlike any other FIM technology, Qualys noise-canceling technology minimizes events and helps your team focus only on events that matter! By levering the same Qualys agent and platform, there is no need to install and manage a new agent.
The World’s Most Effective Noise-Canceling FIM
Qualys FIM offers the most efficient alert noise control available in the industry to help reduce false positives. Based on our continuous analysis/assessment of event patterns in various production environments, we can say that over 80 percent of change events are permitted and should not trigger an alert or event log. With ‘Trusted Source Status,’ you can easily identify authorized changes due to patches and security updates and whitelist them. Users can also filter change events produced by a combination of known good users and processes and whitelist them.
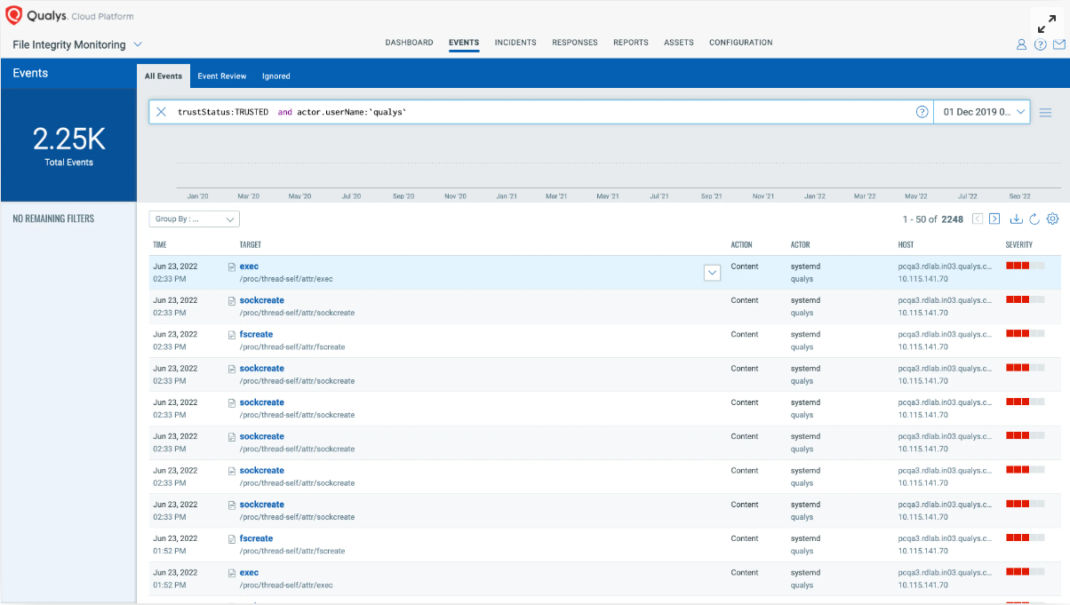
Highlights Unauthorized Changes With Risk Analysis
Unauthorized events are a cause of concern, but given the volume, it is still hard to analyze all such events. The key is to find the unauthorized events which are malicious in nature. For example, a non-privileged user dropping a malicious executable on the host. With Qualys FIM, you can quickly find unauthorized changes and leverage threat intelligence to discern malicious or suspicious events from unauthorized change events.
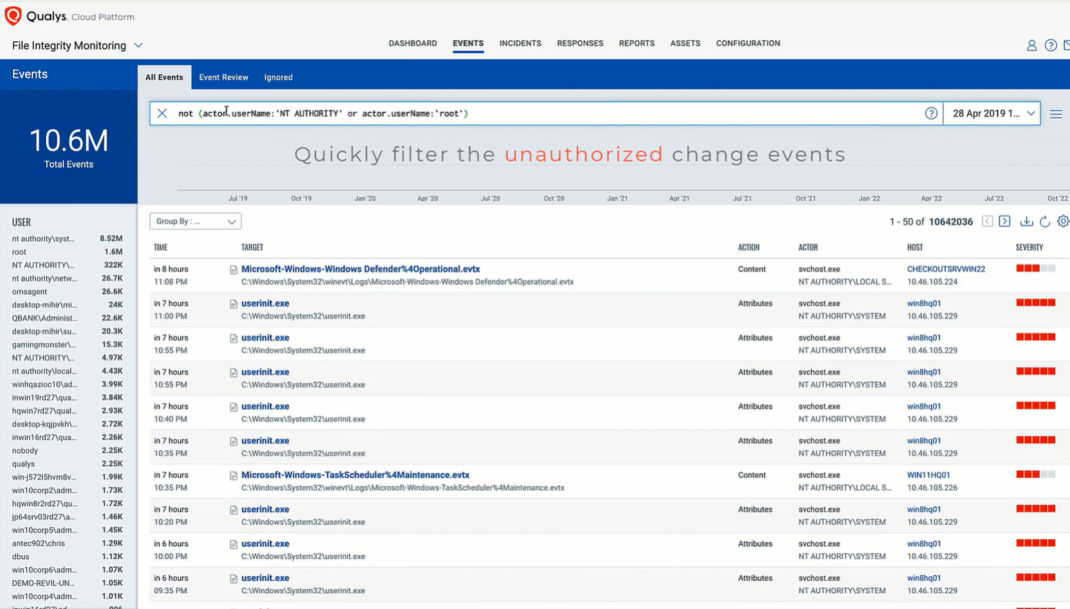
Monitors Dormant and Stale Devices
Based on our analysis, almost 30 percent of assets within any PCI-DSS regulated environment are usually dormant, i.e., these assets have had no change events for an extended duration. With Qualys FIM, you can easily detect assets that should have change events associated with them on a regular basis, but have not had any recent logged events. This might indicate that FIM has been disabled on the host, which is a security and compliance concern.
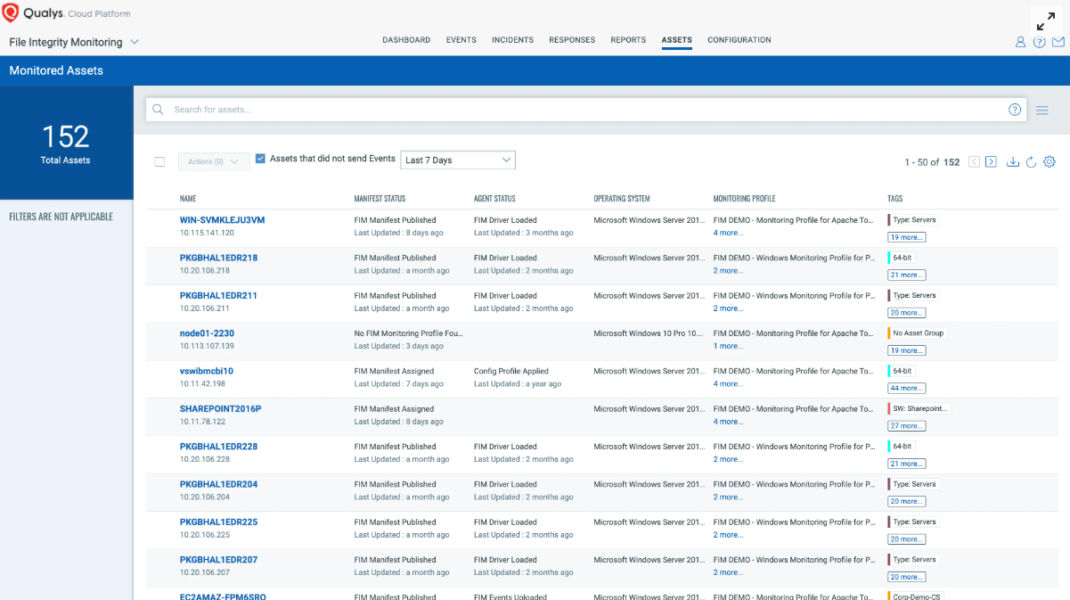
Detects PCI-DSS Non-Compliant Assets
As noted earlier, FIM is listed in Control # SI-7 (7) & (8) of NIST SP 800-53. PCI DSS v4.0, under section 11.5.2, requires FIM to monitor all critical files. Most FIM solutions can cover this, but Qualys goes even further. We not only check if FIM is deployed and activated, we also ensure the integrity of current FIM processes on each host and generate on-demand and scheduled reports for non-compliant assets. Essentially, assets on which FIM was activated but not currently running. This expands your visibility and provides documentation to ensure you’re always audit ready.

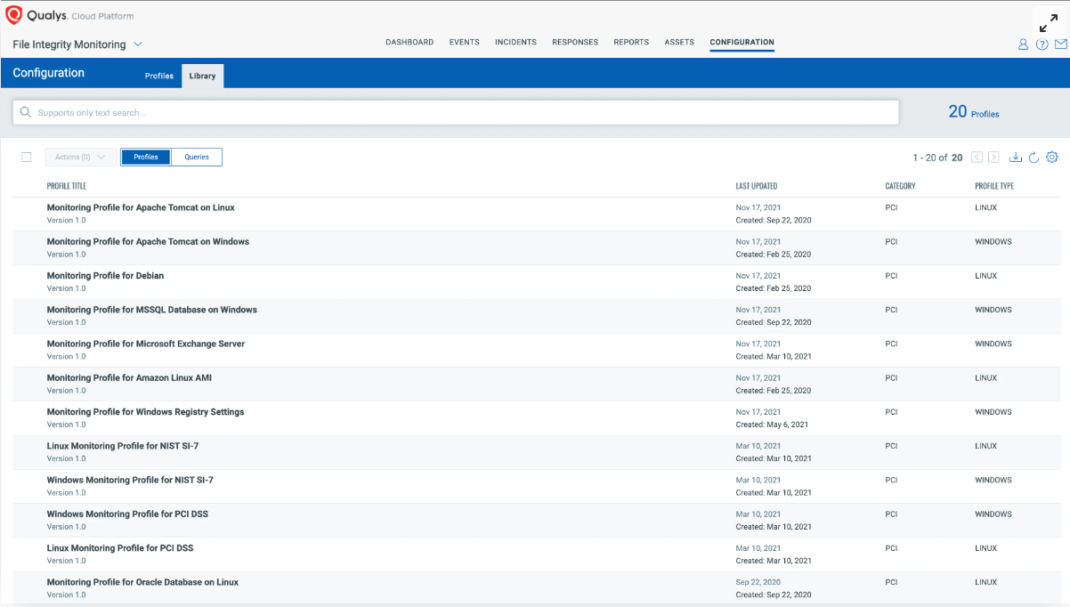
Saves Analyst and SecOps Time
A large percentage of analyst and SecOps staff time is often used to determine which change events to monitor and manage. Qualys FIM contains its own library of out-of-the-box monitoring profiles, which provide analysts with deep insights and pre-configured profiles to determine which highly critical files must be monitored for specific activities. With Qualys FIM, using established profiles that match your monitoring scope with the requirements for each compliance standard can save time and reduce human error.
Conclusion
FIM is obviously not a “nice to have,” but it’s vital to any organization to prevent cybersecurity incidents and compliance failures. Therefore, FIM is not a question of “if” but “which.” Choosing the right FIM application for your firm should include careful consideration and evaluation. We encourage you to compare Qualys FIM with any solution on the market. We’re confident you’ll come to the same conclusion that our current customers have: Qualys offers the best combination of economy, effectivity, and efficiency coupled with the best noise reduction and out-of-the-box tools available to reduce time, effort, and cost.
If you already have a FIM tool, Qualys will also help with the migration making sure the transition is smooth.
Contributors
- Lavish Jhamb, Solution Architect, Compliance Solutions, Qualys
- Bill Reed, Compliance Product Marketing
- Mukesh Choudhary, Compliance Research Analyst, Qualys
- Mohd. Anas Khan, Compliance Research Analyst, Qualys