Launching Qualys Cloud Threat Database
We are proud to announce the release of the Qualys Cloud Threat Database which correlates more than 25 different threat intelligence feeds into a single source for all Qualys products to leverage. This comprehensive vulnerability and threat intelligence database pulls from trusted sources such as the CISA Known Exploited Vulnerability Catalog, MITRE ATT&CK Framework, and many other feeds. Combined with the power of machine learning models, this enables products such as Qualys VMDR to provide rich context to the vulnerabilities detected in your environment.
In 2022 more than 25,000 vulnerabilities were published by the National Vulnerability Database (NVD). While at first glance, this seems like a mountain for security practitioners to climb, not all vulnerabilities are created equal. Organizations need help prioritizing and creating remediation plans in today’s threat landscape, where vulnerability management must move beyond just sharing a long list of vulnerabilities. Risk-based vulnerability management gives security / IT teams shared context and the ability to create workflows to quickly align and respond to threats. The Qualys Threat Research Unit (TRU) analyzes vulnerabilities as they are released and continually monitors the threat landscape for evolving risk associated with each of these vulnerabilities. This is measured by assessing the various ways adversaries leverage vulnerabilities.
There are three categories when it comes to measuring vulnerability risk. The first is evidence of a publicly available exploit; second, if the vulnerability abuse can be attributed to a named threat actor; and finally, if malware/ransomware families have leveraged it. Additionally, an organization’s risk score will increase accordingly if a vulnerability is added to the CISA Known Exploited Vulnerabilities catalog. Per these categories of measurement, less than three percent of all known vulnerabilities pose the most severe risk to organizations. Today, there are more than 194k vulnerabilities published by the NVD, broken down into the following categories to measure risk:
- Public Proof of Concept Available: 4480
- Associated with Malware: 1019
- CISA Known Exploited Vulnerability Catalog: 875
- Leveraged by Named Threat Actors: 497
- Associated with Ransomware: 235
While it is critical to know if a vulnerability has been exploited, that alone does not provide the context needed to help an organization prioritize it. For example, additional information around which threat actor or malware family has leveraged the vulnerability can increase or decrease the risk posed to an organization. Qualys TruRisk quantifies an organization’s risk by combining threat intelligence with additional factors such as asset criticality and other compensating controls.
The Qualys Cloud Threat Database
The Qualys Cloud Platform now leverages our new Cloud Threat Database. This unifies all intelligence – vulnerability, malware, and threat actor information – into one centralized location, accessible across all Qualys applications. This enables Qualys customers to view associated malware, threat actors, and exploits when investigating a particular vulnerability.
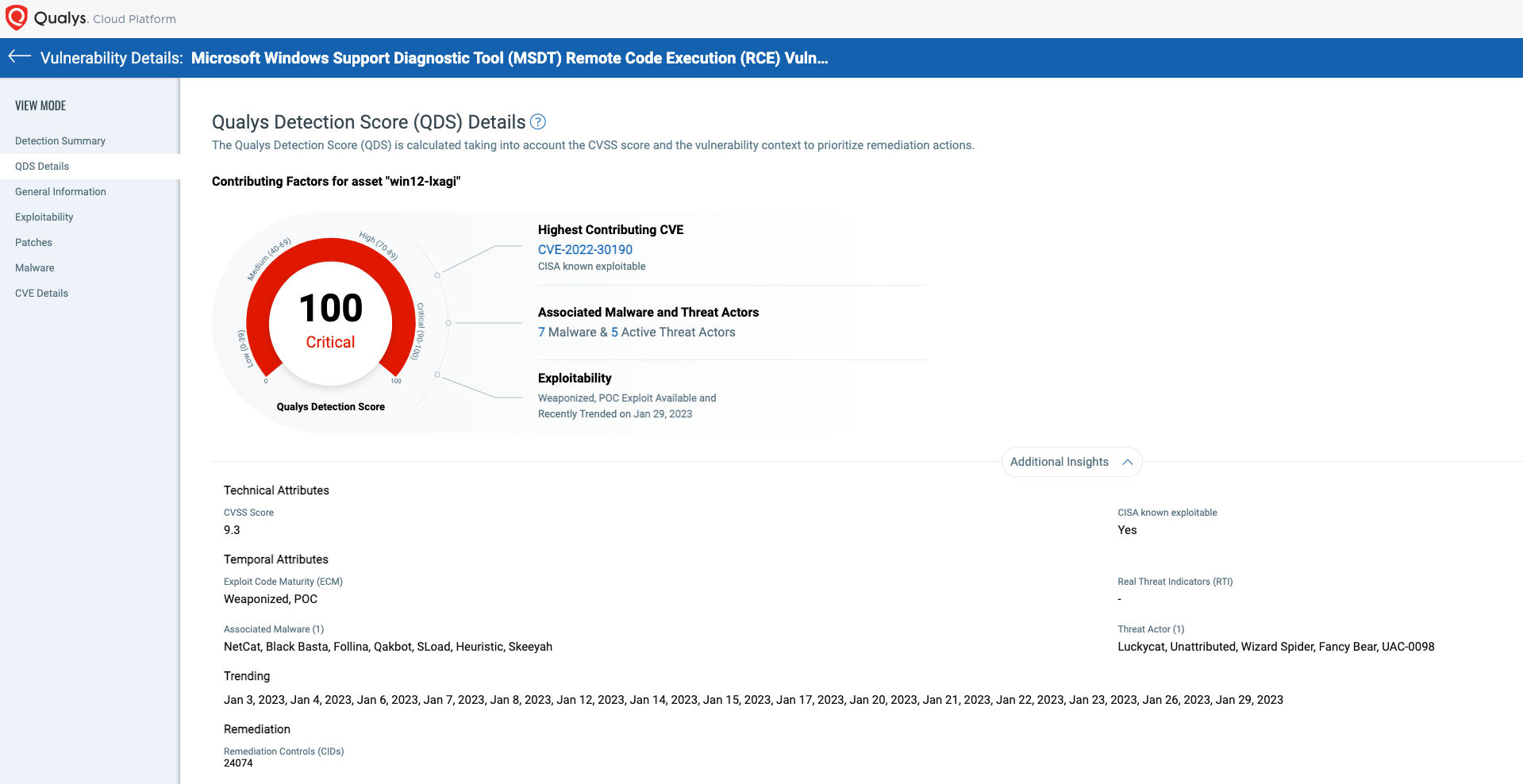
In this example, CVE-2022-30190 –also known as Follina – was tracked under all the various risk categories. It was also added to the CISA Known Exploited Vulnerability catalog, weaponized with a proof of concept available, and associated with seven unique malware families and five named threat actor groups.
Qualys Detection and Response products, such as Multi-Vector EDR, ask a similar question about the verdict of a specific file hash to determine if that file is malicious. The Cloud Threat Database then overlays this with additional intelligence on associations with threat actors that deploy the malware and/or vulnerabilities known to be leveraged by that piece of malware.
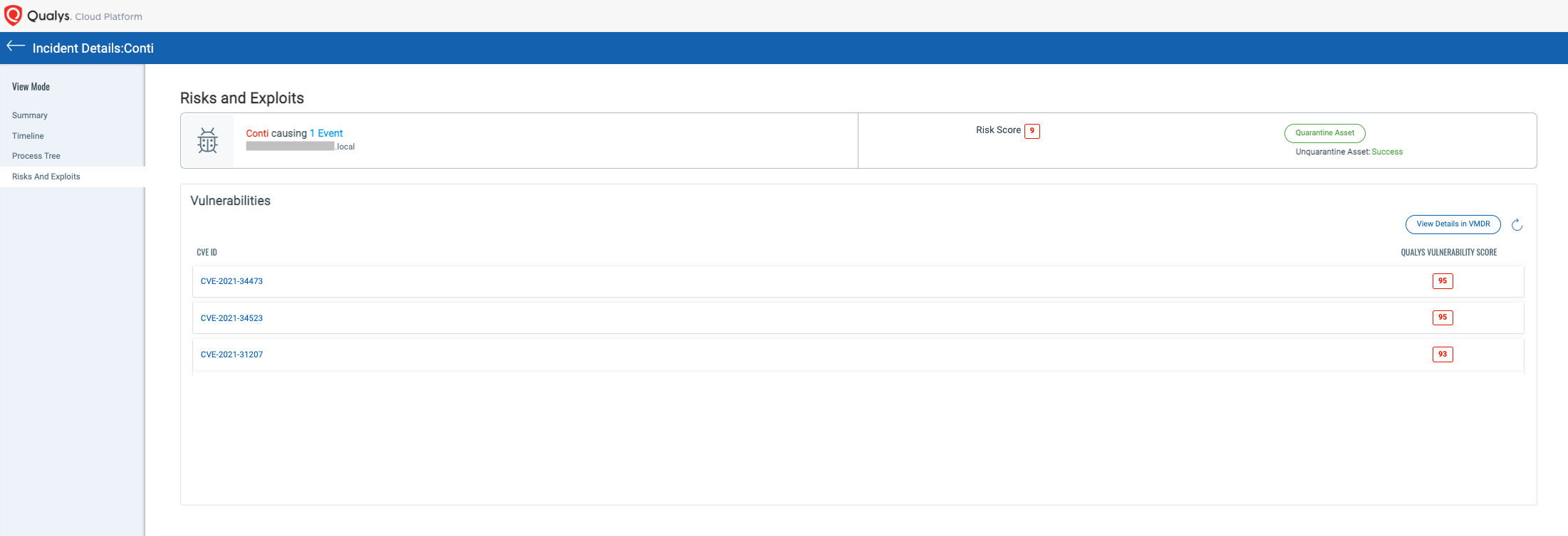
The Qualys Cloud Threat Database is powered by a graph database containing billions of connections between the vulnerabilities, malware, and threat actors that aim to harm organizations. These attributes are interconnected, and an entry point into one often gives way to connections with various other data points. For example, to know a verdict of a file hash tells you the malware family name, threat actors known to leverage that malware, and the vulnerabilities the malware or threat actors are associated with. Alternatively, looking up information about a vulnerability can shed light on the malware and threat actors known to abuse it. Any given entry point provides the context missing from a simple verdict or score.
Powered By Machine Learning
More than 25 different threat intelligence feeds are brought into this service to provide detections and enrich the data Qualys collects. Additionally, TRU inputs the intelligence from original research and analysis of the threat landscape into the platform.
Another significant source of intelligence comes from the ML-based malware detection platform, developed by Blue Hexagon, that feeds into the Cloud Threat Database. This framework leverages advanced deep learning models to analyze and detect malicious samples within a few milliseconds with extremely high efficacy. With this speed, fresh threat intelligence is added to the database the moment a sample is observed, even if it is the first time it has been seen within the threat landscape. The ability to immediately detect and track fresh malicious samples allows the database to receive the verdict, the sample categorization, and the results generated through in-depth analysis of the detected samples.
Detailed analysis of a new file requires significant time and resources, even when using automatic platforms. Due to the lack of resources to analyze freshly observed samples simultaneously, analysis is often delayed. At this point, the sample behavior may have changed due to the takedown of the command and control (C&C or C2) servers or other actions typically taken by threat actors. Using an ML-based detection approach, the sample is selected and forwarded to the analysis platform the moment it is observed allowing the collection of a valuable set of threat intelligence on sample activities – including the C&C resources and lateral movement.
The machine learning models are trained and validated on millions of different samples. Each sample is carefully selected as part of the training dataset to maximize the coverage of the threat landscape. Having an informatically rich dataset allows the machine learning models to generalize beyond the scope of known samples and into the realm of unknown malicious samples– e.g., samples that have not yet been observed.
The models achieve this by processing a representation of each sample (i.e., feature vector) on a high dimensional vector space (i.e., feature space) where each sample is mapped, according to its characteristics, into a different region of the feature space. The model then learns a proper transformation that groups malicious and benign samples into different regions of the target space. While simply put, this highlights how ML-based detection approaches can be applied on samples that are not observed at the training time – called generalizing in ML-based approaches.
More Information
See Qualys TruRisk powered by our Cloud Threat Database in action for yourself with a free trial of Qualys Vulnerability Management Detection and Response (VMDR). or request a demo from one of our technical account representatives.