Adopting an Effective and Easy To Implement Zero Trust Architecture
Security professionals employed by a federal agency, supplier, or regulated private sector firm are often challenged by long lists of required cybersecurity rules that can seem endless and unchanging. White House Executive Orders, FedRAMP requirements, CISA Binding Operational Directives, NIST guidelines, FISMA modernization mandates – and Inspector Generals with local, state, or federal agencies stand in line to deliver fines, censures, and penalties for non-compliance.
Security mandates are not created to cause more difficulty, of course, but are instead issued to help organizations avoid serious cybersecurity consequences. President Joseph Biden’s Executive Order 14028 on Improving the Nation’s Cybersecurity succinctly stated:
“It is the policy of my Administration that the prevention, detection, assessment, and remediation of cyber incidents is a top priority and essential to national and economic security. The Federal Government must lead by example.”
Why Zero Trust?
EO 14028 embraces a zero-trust approach as the guiding security model for the federal government, which rolls downhill to agency suppliers and other private sector firms with stringent compliance or security framework requirements. Federal civilian executive branch agencies are all tasked with creating and using a zero-trust architecture (ZTA). According to the Office of Management and Budget, which audits cybersecurity efforts for twenty-three agencies, all grades but two in 2022 were B’s and C’s. The adage, “attackers only need to be right once, while defenders must be right all the time,” suggests there’s room for cybersecurity posture improvement.
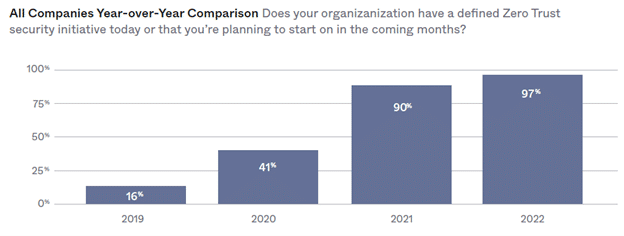
According to The State of Zero Trust 2022 report from Okta, only 16 percent of companies surveyed in 2019 planned to have a zero-trust initiative in place. Today, that number is 97 percent. However, only 55 percent have actually initiated a plan.
It’s no wonder many firms may be confused when trying to adopt a zero trust posture, as there are at least three similar but different models to consider. The National Institute of Standards and Technology (NIST) Zero Trust Architecture (ZTA) special publication (SP) 800-207 hit the streets several years ago. The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency published their Zero Trust Maturity Model Version 2.0 in April 2023 that specifies five pillars to implement. CISA’s best practices aim to provide a simple picture of the challenges adherent with achieving the nation’s strategic objective. Finally, the Department of Defense offers a similar zero trust approach with seven pillars. While no single vendor or tool can address ZTA requirements across all three of these, organizations can connect DoD, CISA, and NIST best practices to a range of security and compliance solutions integrated by the Qualys GovCloud Platform. This approach can prove valuable to both federal agencies and civilian enterprises that are committed to adopting ZTA. Moreover, while many organizations view ZTA as applicable solely to identity access management (IAM), DoD, CISA, and NIST guidelines clearly specify going well beyond IAM to adopt a zero-trust approach for all endpoints and assets.
What Is Zero Trust?
If a relationship between two people devolves to the point of zero trust, it may be time to move on, or at least buy a safe. In the world of information technology and security, a zero-trust relationship is more complicated and the negative consequences could be far more damaging. From an IT security architecture perspective, the essence of zero trust assumes that no user or asset can be implicitly trusted. ZTA assumes that attackers are already inside your environment and pillaging at will. Everything any user, application, or device attempts to do or change within a ZTA environment must be continually verified as authentic and authorized for execution. Ironically, ZTA admonishes conflicting behaviors as compared to international nuclear arms treaties, where the Russian proverb-based doctrine says “trust, but verify.” With ZTA, you must verify first, and then trust.
Zero Trust was coined by a Forrester analyst in 2010, and Google moved the term along during the next few years to enable protected computing by remote workers without using a virtual private network (VPN). The framework was codified in 2018 when NIST issued Special Publication 800-207, Zero Trust Architecture. Core components were updated by NIST in 2020. Forrester and Gartner continued evolving their ZTA models, and in 2021, Microsoft’s Zero Trust Adoption Report documented major traction by 96 percent of 1,200 security decision-makers who stated that zero trust was critical to their organization’s success.
The presidential Executive Order on Improving the Nation’s Cybersecurity issued in 2021, noted earlier, declared ZTA as the fundamental tenet for securing federal systems and critical infrastructure. In January 2022, the Office of Management and Budget (OMB) published more details about the new federal strategy in Memorandum-22-09 (described below), which expanded ZTA beyond its original emphasis on identity and access control. More recently, CISA’s Zero Trust Maturity Model Version 2.0 was published in April 2023 (also described below).
Adopting a Zero Trust Architecture
As an architecture focused on trust, it’s not surprising that the original concept of ZTA was grounded in identity and access management (IAM). Gartner defines IAM as “multiple technologies and business processes to help the right people or machines to access the right assets at the right time for the right reasons, while keeping unauthorized access and fraud at bay.”
On the surface, Gartner’s definition almost sounds like ZTA. The intent is identical, without a doubt. But doubt we must, for ZTA entails a far broader range of integrated controls required to enable a trusted ecosystem. Since concepts related to ZTA emerged thirteen years ago, analysts, security architects, standards organizations, security and IT suppliers, and enterprise security practitioners have pondered, researched, developed, trialed, and road tested what a ZTA ecosystem entails. The conclusion: ZTA extends far beyond only IAM.
The Qualys GovCloud Platform is the most advanced security platform for federal, state, and local agencies, as well as regulated private sector firms that need highly secure zero-trust hybrid IT infrastructures that comply with the Zero Trust Security Model and broader mandates for guidelines in NIST Special Publication 800-53 v5 (see Appendix I). The Qualys GovCloud Platform is the only FedRAMP Ready status vulnerability management platform fulfilling all 421 High Baseline controls out of 1,007 controls in SP 800-53. The Qualys platform is built with the world’s most comprehensive Vulnerability Management (VM) capabilities, including its own asset inventory, threat database, and attack surface management. The apps required for ZTA compliance are delivered via one platform, managed with one dashboard, and deployed with a single agent.
As an integrated solution, the Qualys GovCloud Platform includes four tiers of capabilities that simplify planning, deployment, and continuous ZTA operations for the complex, sophisticated requirements of federal agencies, suppliers, and mature private sector firms.
Comprehensive Application Suite – More than two dozen security and compliance applications are fully integrated within the GovCloud Platform. With a single, centralized interface, security and compliance teams are provided with an agency-wide view. Applications focused on ZTA requirements include Vulnerability Management, Detection, and Response (VMDR); Patch Management; VMDR + CyberSecurity Asset Management (CSAM) with Extended Attack Surface Management (EASM); Policy Compliance; File Integrity Monitoring; and Security Assessment Questionnaire.
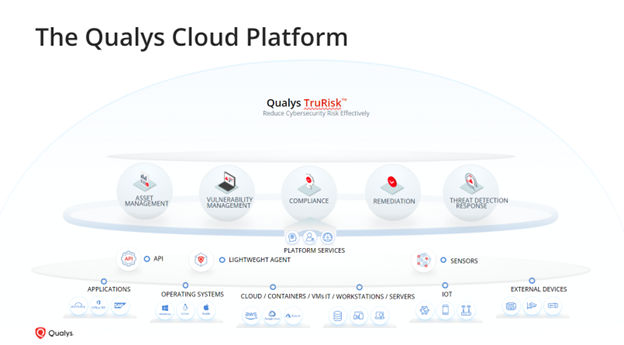
Analytics and Reporting Engines – Modern security and compliance applications depend on intense operational data analytics, so the Qualys GovCloud Platform integrates the use of eight analytics and reporting engines: Apache Kafka, Ceph, Elastic, Redis, Apache Cassandra, Apache Flink, or a cloud microservice.
Distributed Scalable Sensors / Agents – To collect operational data for analytics, the Qualys GovCloud Platform enables the flexible use of six scalable sensors / agents: infrastructure, virtual, cloud, agent, passive, and API.
Flexible Deployments (Cloud and On-Premises) – Federal agencies can deploy the Qualys GovCloud Platform for cloud and on-premises environments from FedRAMP. Non-government enterprises can deploy to virtual environments including Amazon Web Service, Microsoft Azure, or Google Cloud.
Conclusion
Achieving a zero trust architecture as described by the DoD, CISA, NIST, or all three requires a comprehensive suite of technologies, including Identity, Devices, Networks, Applications & Workloads, and Data. As noted, no single solution addresses all these requirements. However, by using the Qualys Cloud Platform, organizations can simplify and achieve compliance across a broad range of ZTA requirements with integrated security and compliance solutions, one centralized control center, and a single agent. Whether your organization is a federal agency, supplier, or civilian enterprise, we encourage you to learn more about the Qualys Cloud Platform and how it can help your organization comply with national policy for cybersecurity by effectively implementing a zero-trust architecture and model.
We also invite you to learn more about how you can use Qualys to achieve Zero Trust Maturity by starting your free trial today.
Contributors:
- Bill Reed, Qualys Product Marketing
- Dave Buerger, Qualys Product Marketing