Qualys Expands Cloud Platform for First-Party Application Risk Detection and Remediation
Table of Contents
- First-Party Application and Open-Source Assessment
- Introducing New Capabilities for First-Party Applications and Open-Source Assessment and Remediation
- Tailoring Risk Assessment for First-Party Applications
- How Custom Assessment Works
- Reducing Supply Chain Risks Automatically with Runtime Software Composition Analysis
- How Runtime Software Composition Analysis Works
- Cloud Platform Enables the Dual Tactic of Custom Assessments and Open-Source Scanning
- Try it in your environment!
- Contributor:
Have you faced the need to identify & respond to open-source package vulnerabilities like log4shell, openSSL, etc, in production from Day Zero?
Are you using first-party, homegrown applications and are worried the risk introduced by those applications is not seen or addressed?
Qualys‘ new capabilities will help you address those challenges.
First-Party Application and Open-Source Assessment
As security leaders grapple with an ever-changing attack surface, ensuring the security of first-party applications looms as a major issue. First-party applications are the software apps developed in house – apps that run the business. Many, if not most, of today’s organizations operate using proprietary or “first-party” software. Analysis by the Qualys Threat Research Unit of more than 13 trillion anonymized data points determined that 79% of servers use open-source components.
Custom, first-party software often contains well-known vulnerabilities and risks since most applications are built with open-source components. For example, the notorious open-source Log4Shell vulnerability continues to plague organizations globally. Scans of more than 50 million cloud assets by the Qualys Cloud Platform found one million instances of Log4Shell – 70% of which are unpatched, according to 2023 Qualys TotalCloud Security Insights. With the clear-and-present danger of open-source risks like Log4Shell, how can organizations proactively secure their first-party applications to limit the risk of exploitation?
Introducing New Capabilities for First-Party Applications and Open-Source Assessment and Remediation
In this blog post, we’ll introduce you to two new product capabilities that you can leverage to bring your own risk assessment logic into the Qualys Cloud Platform and run scans to detect open-source component vulnerabilities. We’ll also show you how the Qualys Cloud Platform can provide you with a unified view of your risk, which can be applied effectively across several critical use cases, including:
- Finding Log4Shell vulnerable JARs in production and ensuring readiness for future Log4Shell events.
- Scanning your entire environment at scale to identify a unique vulnerability that was discovered in one of the libraries being used by a custom application.
- How to review, prioritize, and remediate first-party and open-source vulnerabilities using the same VMDR console you use for third-party applications.
Tailoring Risk Assessment for First-Party Applications
Effective risk assessment is the bedrock of security; this process is especially important for custom, first-party applications and their open-source components. As companies develop their own software to meet specific requirements, the importance of a unified approach to security assessments increases. Unfortunately, risk assessments for first-party applications rarely go through the same lifecycle management of vulnerabilities from discovery to prioritization to remediation – the same process used for third-party applications. When first-party assessments are done, they often rely on disjointed, standalone tools owned and managed by different teams. As a result, effective risk management in such disparate environments becomes an impossible task, which means first-party applications are likely to be exposed to risks that are “unseen” by SecOps teams.
The Qualys Cloud Platform now includes new capabilities for assessing risks in first-party applications. Customers can “bring their own” assessment and remediation logic into Qualys Vulnerability Management, Detection and Response (VMDR) workflows and reporting, providing SecOps teams with a unified view of all first- and third-party applications along with open-source software in their environment.
With the release of this new risk assessment and remediation capability, customers can use many types of scripting languages like PowerShell, Python and many more to define their own assessment and remediation logic. The functionality allows tailoring the logic specifically to assess and remediate vulnerabilities in their first-party, homegrown apps. Implementation is easy with script templates included and a library of pre-defined scripts available as part of the solution.
Here is a scenario of how you would use the solution: Imagine you detected a vulnerable JAR in your home-grown application. The application is deployed on thousands of assets worldwide, so with this new capability you would create a custom assessment to quickly assess all your assets that includes the vulnerable JAR. You would then use your VMDR dashboards and reporting to find the vulnerable assets, prioritize them, and then use a custom remediation script to deploy an updated JAR or apply a configuration change to your vulnerable assets – and thus remediate the risk.
In addition, the new capabilities can help organizations expand their risk-detection logic to unique use cases for their environment, such as:
- Flag as vulnerable assets that do not have a required application or service running. For example, flag assets where EDR/AV is not running.
- Restart services that should be running. In case a required application or service is not running, use custom remediation to start it.
- Flag as vulnerable assets where Chrome or other applications have unauthorized plug-ins/add-ons installed.
- Detect and flag as vulnerable applications that include sensitive information like PII.
How Custom Assessment Works
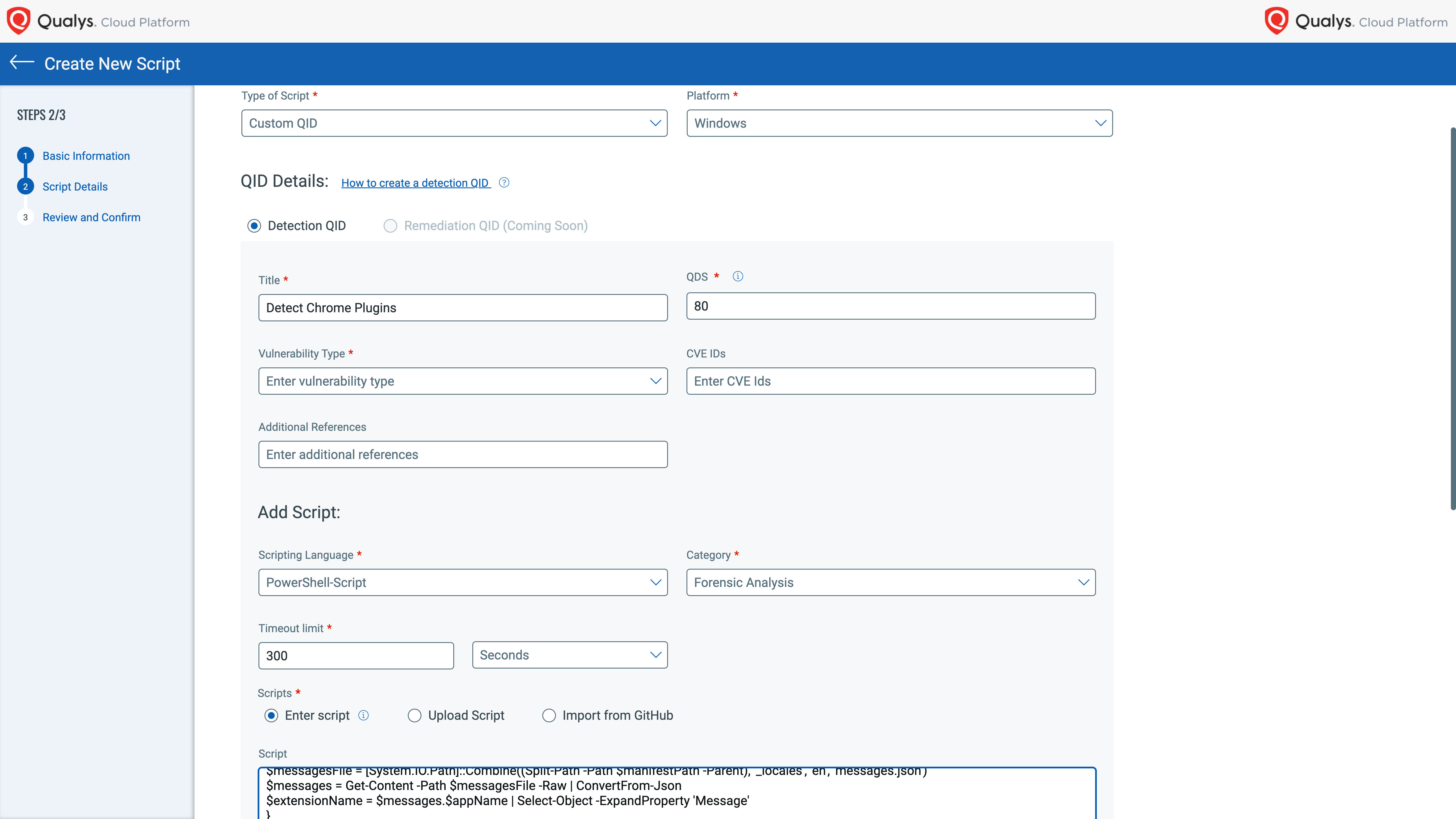
The process of creating custom assessments for first-party applications is straightforward, thanks to the flexibility of the Qualys Cloud Platform and its integration of related apps. With the integration of advanced scripting capabilities in the Custom Assessment and Remediation (CAR) app working in conjunction with VMDR, customers can create a script with one of many supported scripting languages and execute it on a target asset; this determines if the asset is vulnerable to a customer-defined vulnerability.
Custom scripts are treated by the Qualys Cloud Platform as a custom QID – the Qualys ID number assigned to each vulnerability. All custom QIDs are fully integrated into VMDR’s knowledge base and workflows. As a result, every custom QID’s vulnerability information and detection status are shown in VMDR’s dashboard, reports, and workflows; these appear side by side with out-of-the-box detections of other vulnerabilities.
Reducing Supply Chain Risks Automatically with Runtime Software Composition Analysis
The surging use of open-source components during application development has increased the risk of exploitation of vulnerabilities within them. Related risks for the Software Supply Chain are now a significant source of concern, as evidenced by recent attacks on MOVEit, 3CX, Log4j, SolarWinds, and others. In response to this challenge, Qualys has added a new capability for VMDR to detect, manage, and reduce the risk of software supply chain vulnerabilities in the production environment.
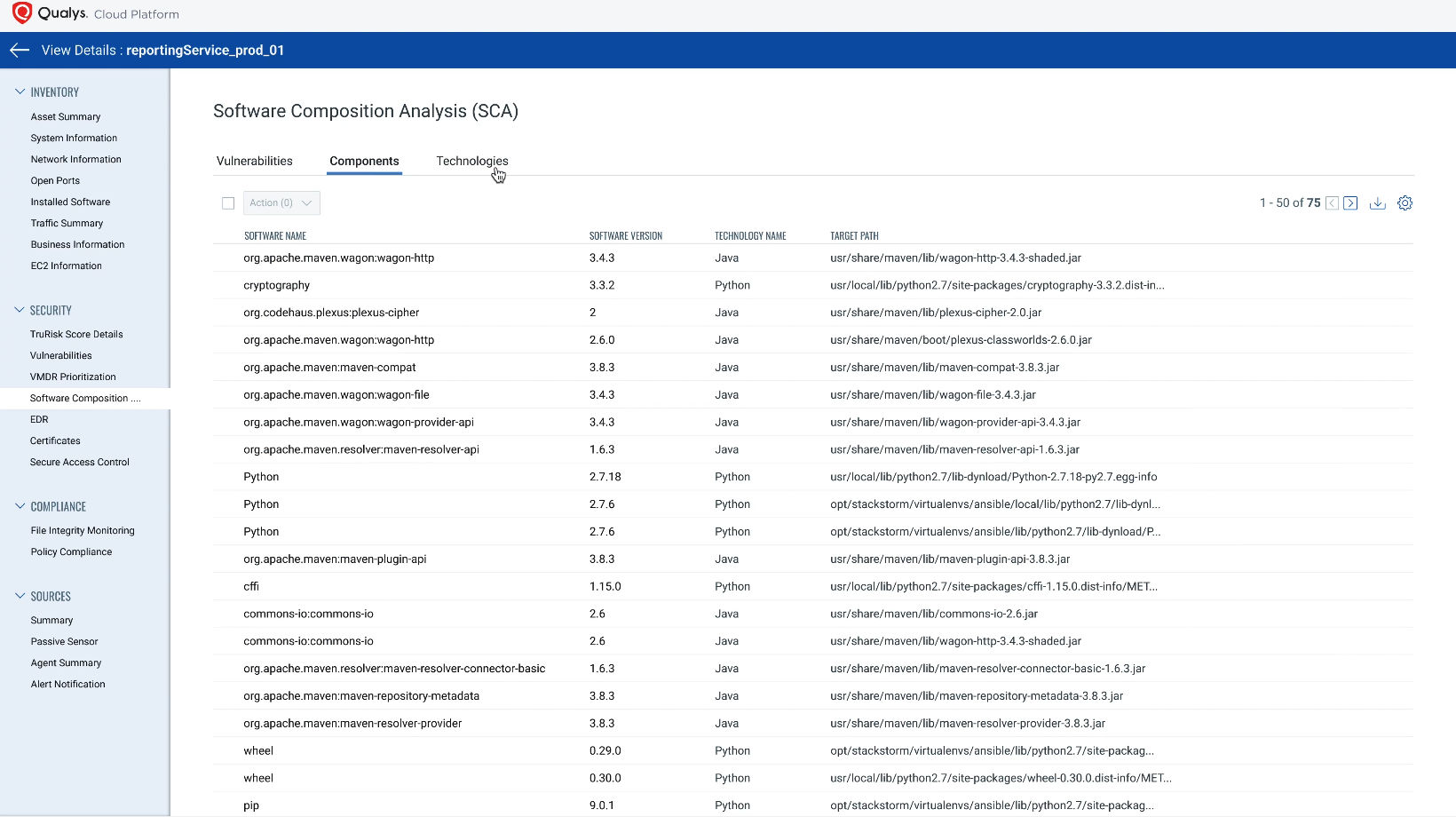
Runtime Software Composition Analysis (SCA) offers continuous and real-time visibility of both open-source and commercial software components present in production of both first-party and third-party applications. SCA determines the associated risk of these applications with innovative threat detection, leveraging the single, powerful Qualys Agent. It opens visibility into a customer’s software supply chain to proactively address potential risks and fortify applications against emerging threats.
SCA scans for vulnerabilities in open-source components developed for Java, Go, .Net, Python, Node JS, Rust, Ruby, PHP and more. The addition of SCA broadens VMDR scanning capability by adding more than 13,000 new signatures, covering more than 11,000 Common Vulnerabilities and Exposures (CVEs).
By incorporating SCA into your security toolkit, your team can bolster the organization’s defenses and safeguard its digital assets from potential threats. The new functionality enables teams to handle Log4j-like outbreaks proactively with confidence and ease. Adding SCA is a substantial enhancement for the Qualys Cloud Platform and underscores our commitment to providing the most comprehensive vulnerability management solution possible.
How Runtime Software Composition Analysis Works
Runtime SCA leverages the same Qualys Cloud Agent used with all Qualys Cloud Platform applications and can be enabled with a single click. The Cloud Agent comes with flexible and granular performance configuration and scanning controls, allowing organizations to tune agent performance and bandwidth usage for specific environmental requirements. You can control a tiny memory footprint and minimal network bandwidth along with the flexibility to either do a full file system crawl or define files and folders to be included and excluded. The Agent would just collect the deltas while continuous evaluation and data enrichment occurs on the Qualys Cloud Platform.
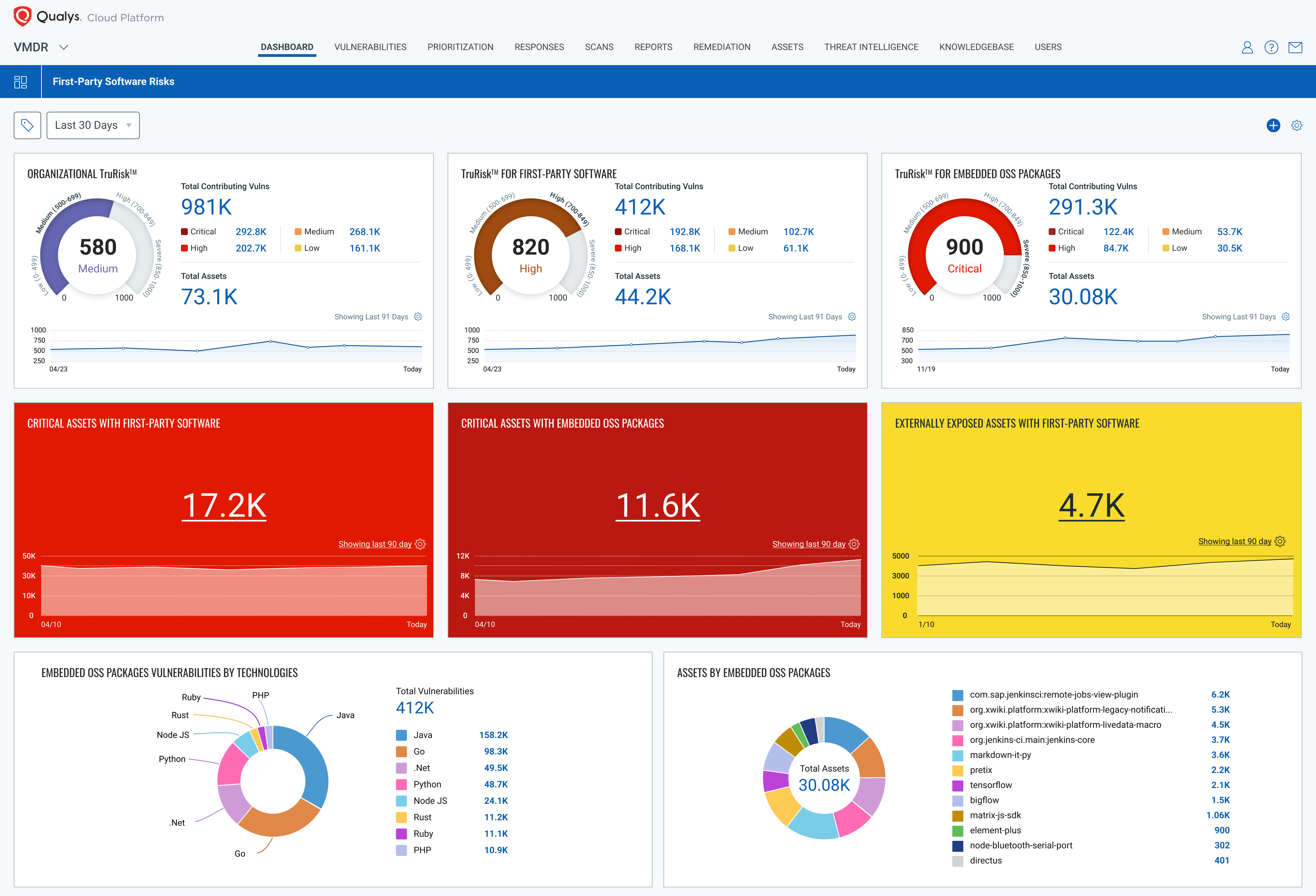
Teams no longer must run any manual scripts or struggle to identify software packages like Log4j. Qualys Cloud Platform and Cloud Agent will continuously provide a unified view of inventory and vulnerabilities associated with the OS, software, and software packages along with the TruRisk score. The solution provides teams with an integrated and centralized reporting and monitoring system, which significantly reduces the mean time to remediate urgent threats to first-party applications.
Cloud Platform Enables the Dual Tactic of Custom Assessments and Open-Source Scanning
The Qualys Cloud Platform enables the power of a dual approach for securing first-party applications. One capability is custom assessments; the other is deeply embedded open-source packages and commercial software components scanning. These two capabilities, while powerful on their own, complement each other in providing a 360-degree view of your cybersecurity landscape. Custom assessments provide insight into the unique aspects of your applications, while open-source scanning uncovers hidden vulnerabilities within the components used in their construction.
This dual approach ensures no stone is left unturned in your quest for robust vulnerability management of all first-party applications with Qualys Cloud Platform.
Try it in your environment!
We invite you to try these features yourself. Sign up for a free trial of Qualys VMDR.
__________________________________
Contributor:
Himanshu Kathpal, Senior Director, Platform and Sensors, Qualys