Elevate Your Security Posture: Implementing CIS Top 18 Controls Through Qualys Cloud Platform
Table of Contents
- What are CIS 18 Controls?
- Why Implement CIS 18 Controls?
- Challenges in Implementing CIS Controls
- How Qualys Can Help
- How Qualys Platform Capabilities Address CIS Top 18 Controls
- Inventory and Control of Enterprise and Software Assets
- Continuous Vulnerability Assessment
- Secure Configuration of Enterprise Assets and Software
- Application Software Security
- Audit Log Management
- Security Awareness and Skills Training
- Conclusion/Summary
- Contributors
The Center for Internet Security (CIS) is a 501(c)(3) nonprofit organization originally formed in October 2000. CIS has created what is considered one of the industry’s “gold standard” security frameworks based on its mission to “help people, businesses, and governments protect themselves against pervasive cyber threats.” To this end, CIS has recently released CIS Controls Version 8. Formerly known as the SANS Critical Security Controls (SANS Top 20), these are now officially called the CIS Critical Security Controls (CIS Controls).
Version 8 combines and consolidates the CIS Controls by activities rather than by who manages specific devices. Physical devices, fixed boundaries, and discrete islands of security implementation now have less importance in a cloud world, and this is reflected in v8 through revised terminology and safeguard groupings.
This blog post explains how the Qualys Cloud Platform can help you implement the CIS v8 top 18 controls to ensure the required cybersecurity hygiene in your environment – including discovery, prevention, detection, and response. It also explains how various cloud apps can help security teams of any size broadly and comprehensively adopt the CIS 18 controls.
What are CIS 18 Controls?
The CIS controls are a recommended and prioritized set of safeguards to mitigate the most prevalent cyberattacks against systems and networks. Multiple legal, regulatory, and policy frameworks map to them and reference them. CIS Controls v8 has been enhanced to keep up with modern systems and software. The movement to cloud-based computing, virtualization, mobility, outsourcing, hybrid work, and evolving threats have prompted the update and helped support enterprise security initiatives, especially when adopting cloud and hybrid environments.
Why Implement CIS 18 Controls?
In today’s world, cybersecurity attacks are increasing and evolving so rapidly that preventing and defending against them is becoming more challenging. Does your organization have an effective cyber defense program in place to detect, prevent, and monitor external and internal threats to prevent security breaches? If not, then the CIS top 18 controls can be a practical cyber defense framework you should consider.
Also, In February 2016, Vice President Kamala Harris (then California Attorney General) recommended that “The 20 (now 18) controls in the Center for Internet Security’s Critical Security Controls identify a minimum level of information security that all organizations that collect or maintain personal information should meet. The failure to implement all the controls that apply to an organization’s environment constitutes a lack of reasonable security.”
CIS 18 controls can help you meet the California Consumer Privacy Act (CCPA) requirements and other difficult U.S. State Civil Codes. Also, similar mandates such as GDPR require the protection of Personally Identifiable Information (PII). Failure to do so can result in significant fines, brand damage, and litigation.
The CIS Controls provide a practical security framework as they are based on actual attacks launched against networks and collaborative input from multiple security researchers. Priority is given to controls that:
- Mitigate known attacks
- Address a wide variety of attacks
- Identify and stop attackers early in the compromise cycle
Challenges in Implementing CIS Controls
CIS controls include multiple areas covering asset inventories, software inventories, secure configurations, malware defense, vulnerability management, network monitoring and defense, incident response management, penetration testing, and more. There are multiple challenges an organization might face during framework implementation, including:
- Maintaining inventory of assets and system components
You can’t protect what you can’t see, opening the door for threat actors. Organizations are adopting new technologies and processes that blur traditional network boundaries, leaving blind spots and making it easy for attackers to leverage them.
- Procuring and maintaining individual tools to achieve security and compliance
To achieve this, an organization must procure separate tools such as vulnerability management, incident response management, security configuration assessment, malware detection and response tools, etc. A lack of integration between these tools can result in security gaps and open multiple doors for security breaches. Furthermore, siloed tools and processes to manage dashboarding, communicating, ticketing, reporting, etc., are inefficient and are not scalable or sustainable. This, in turn, leads to a higher total cost of ownership.
- Lack of Visibility
Another hurdle organizations face is gaining adequate visibility on information assets and associated risks in a global hybrid IT environment.
While all these challenges may seem daunting, what if a single platform and agent could address these and provide clear visibility based on the CIS top 18 controls without the need to manage multiple security tools and vendors?
How Qualys Can Help
The Qualys cloud-native TruRisk platform offers a single solution and agent that provides the capabilities needed to implement and continuously monitor CIS’s top 18 controls in a unified manner. This platform includes apps for asset management, vulnerability management, policy compliance, malware detection and response, security configuration assessment, cloud security assessment, file integrity monitoring, security assessment questionnaire, and more.
Qualys has mapped all the CSCs and related safeguards to specific Qualys apps, making it easier for organizations to adopt and implement the controls. The following table shows how the Qualys platform can help your organization implement an effective cybersecurity strategy with CIS’s top 18 controls.
How Qualys Platform Capabilities Address CIS Top 18 Controls
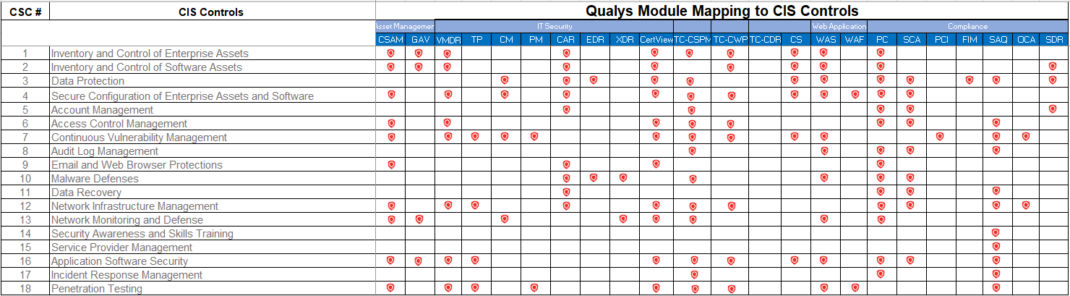
Let’s review a few major CIS controls and see how Qualys helps you implement them.
Inventory and Control of Enterprise and Software Assets
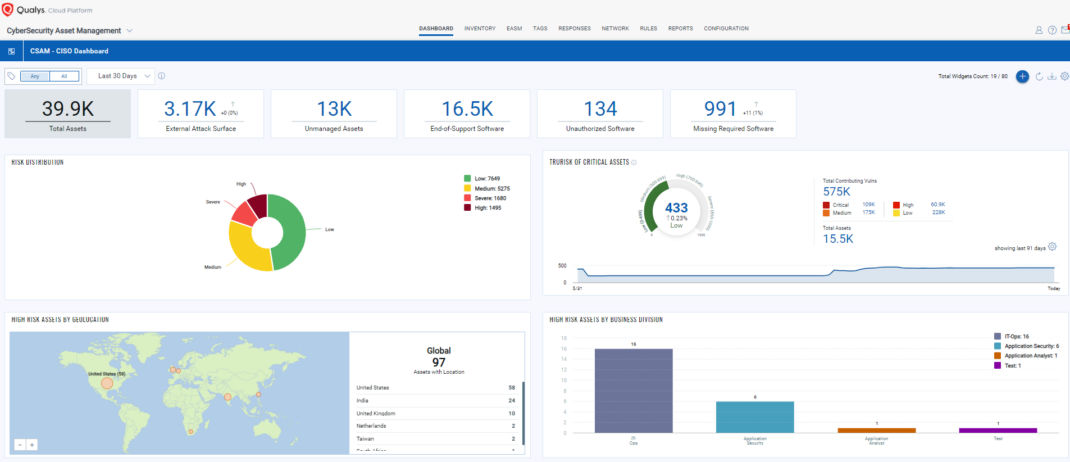
Organizations need to have comprehensive visibility and up-to-date inventory of hardware and Software assets to reduce cyber risk. Qualys CyberSecurity Asset Management (CSAM) continuously discovers and monitors to provide complete visibility of software and assets across distributed hybrid environments. With CyberSecurity Asset Management (CSAM), Security and IT Ops gain both an attackers’ and defenders’ view of their environment for complete, 360-degree visibility of assets, asset groups, domains, subdomains, End-of-Life (EOL) tracking, and more. Together with External Attack Surface Management (EASM), CSAM helps organizations discover, enrich, detect, prioritize, and orchestrate workflows between Security and IT Teams to eliminate workflow friction, improve remediation, and slash cyber risk.
Continuous Vulnerability Assessment
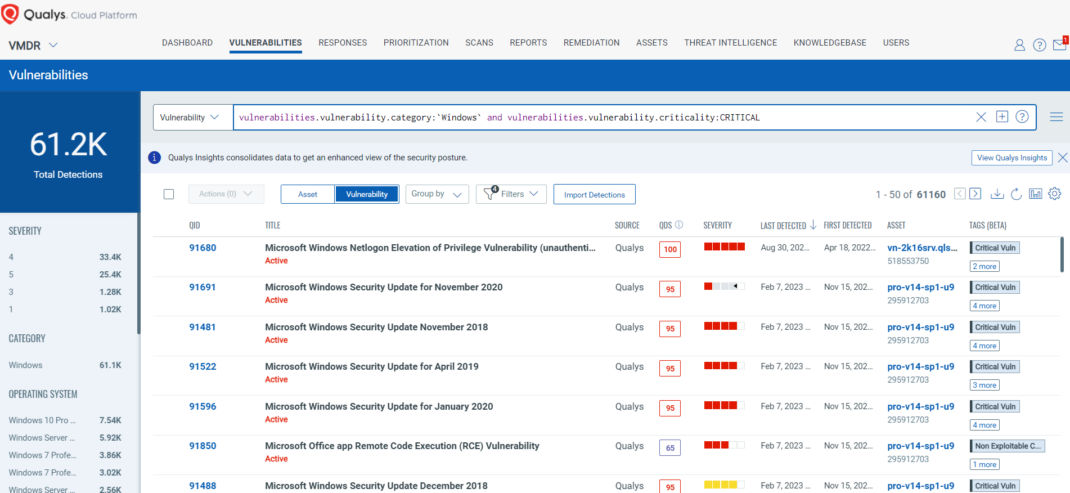
To remediate and minimize the window of opportunity for attackers, organizations need to develop a mechanism to continuously assess and address the vulnerabilities across enterprise assets before attackers can exploit them.
Qualys Vulnerability Management, Detection, and Response (VMDR) enables organizations to automatically discover assets in their hybrid environments and continuously assess them for the latest vulnerabilities. VMDR with TruRisk offers organizations visibility and insights into cyber risk exposure, making prioritizing vulnerabilities and assets based on business risk easy.
Qualys VMDR seamlessly integrates with configuration management databases (CMDB) and Qualys Patch Management (PM) to quickly discover, prioritize, and automatically remediate vulnerabilities at scale to reduce risk. With VMDR, enterprises are empowered with visibility and insight into cyber risk exposure.
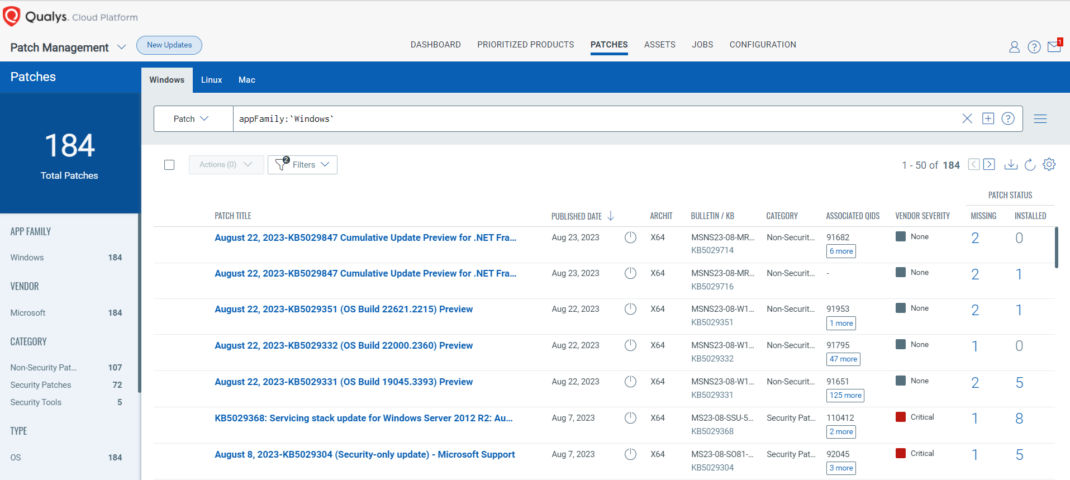
Secure Configuration of Enterprise Assets and Software
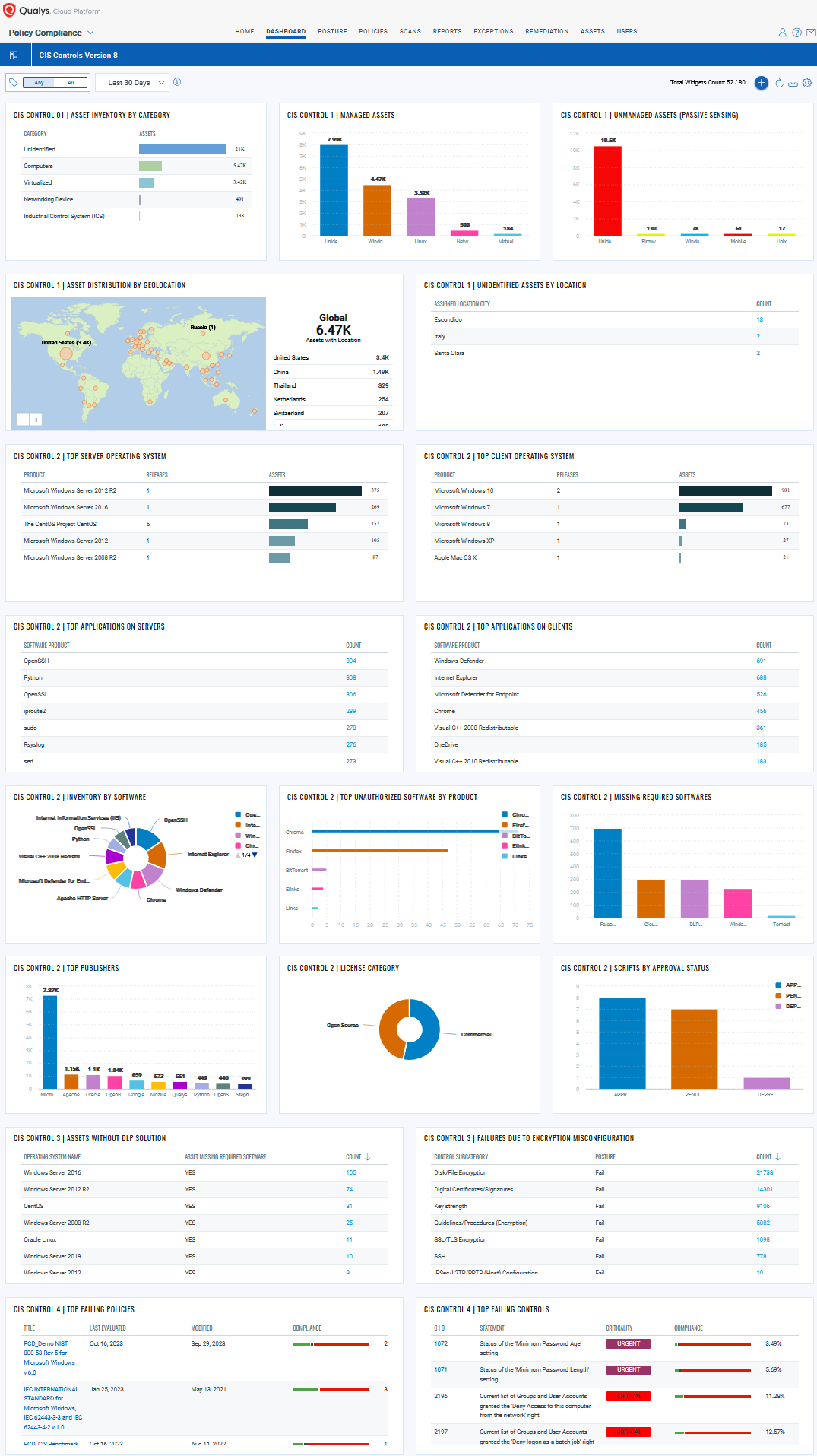
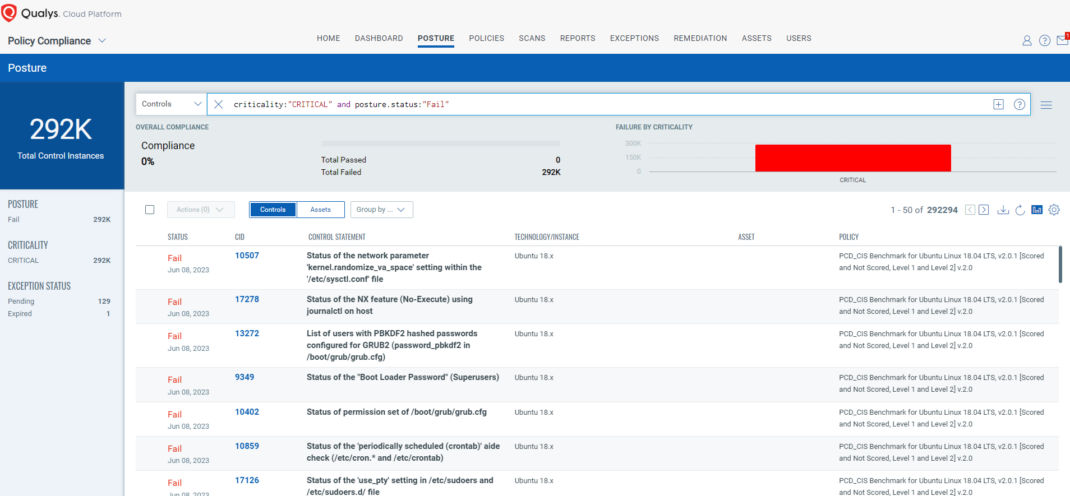
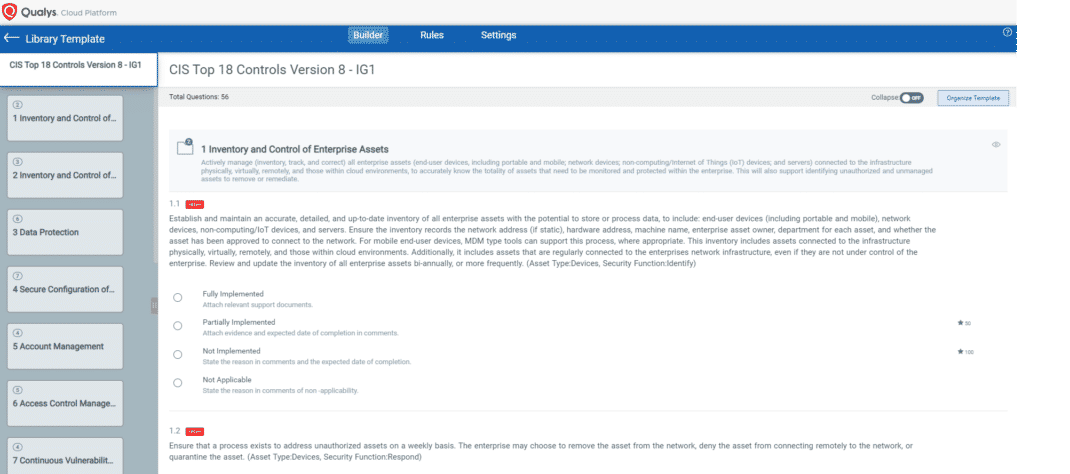
Organizations must establish and maintain a secure configuration of assets and ensure security controls are implemented effectively over time to prevent any loss of data and exposure due to misconfigurations. Qualys Policy Compliance (PC) has an integrated compliance-driven approach and risk management solution that lets you prevent configuration drifts, comply with external regulations and internal policies, prioritize and track remediations, and centrally manage exceptions. Qualys PC enables you to meet regulatory requirements and detect, prioritize, and remediate misconfigurations to mitigate risks and enhance overall security.
With out-of-the-box rich library content based on industry- and vendor-recommended best practices, such as the CIS Benchmarks and the Defense Information Systems Agency’s (DISA) Security Technical Implementation Guides (STIGs), you can fast-track your compliance assessments, or you can customize your control requirements to suit your unique needs.
Qualys Policy Compliance specifically helps you address 15 out of 18 controls, which are mentioned above and which require organizations to establish and ensure the use of standard secure configurations for operating systems and software applications.
Application Software Security
Organizations need to manage the security life cycle of in-house developed, hosted, or acquired software to prevent, detect, and remediate security weaknesses before they can impact the enterprise.
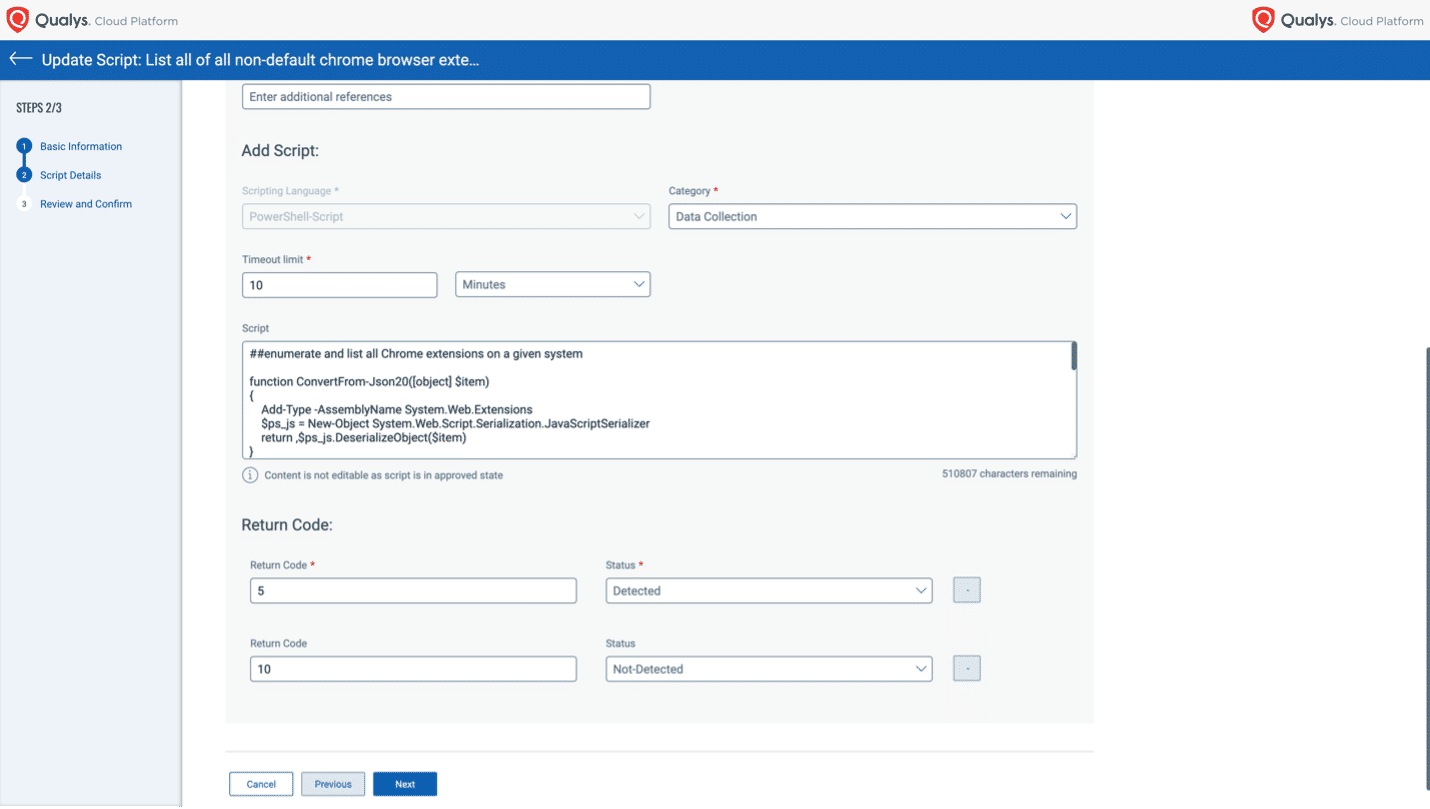
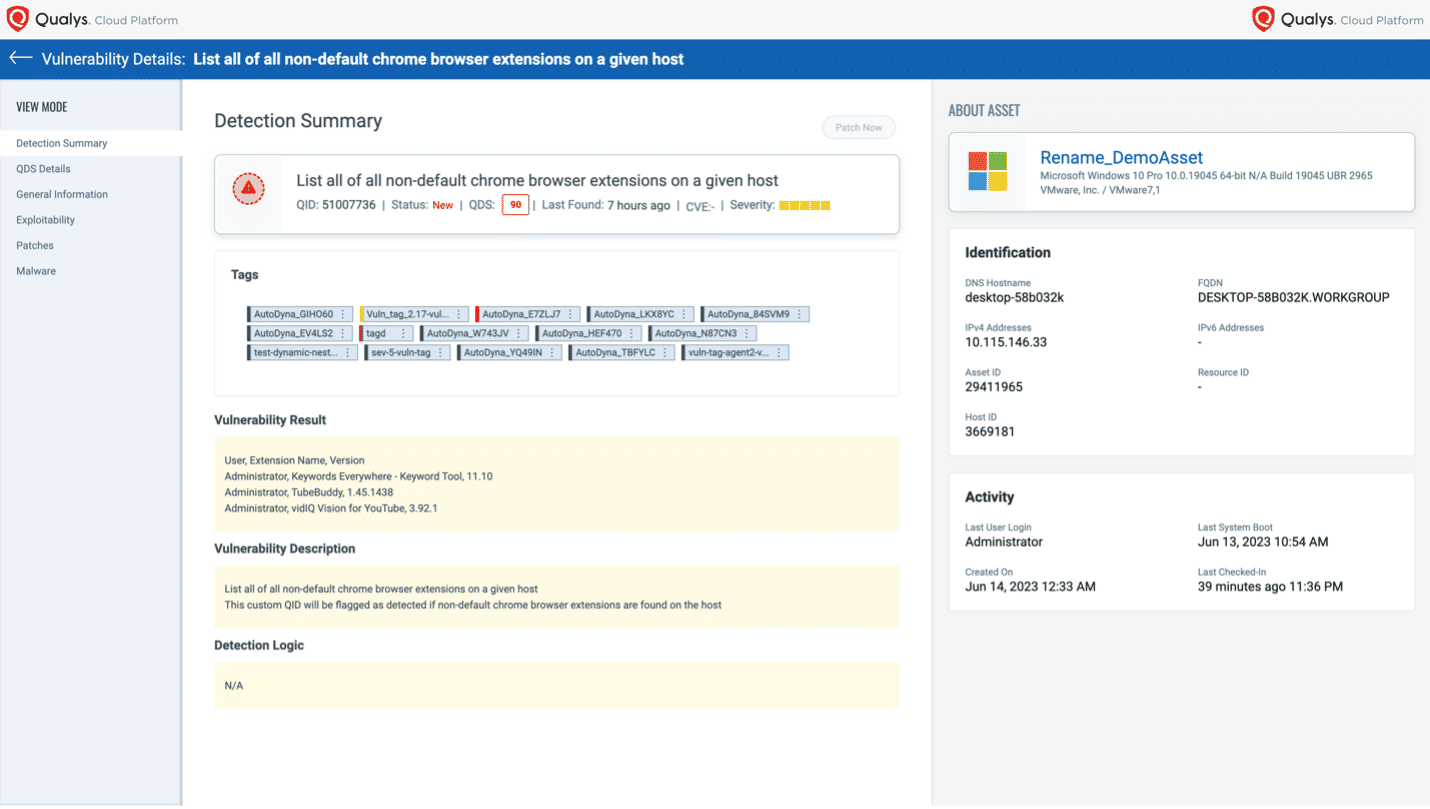
With the integration of advanced scripting capabilities in the Qualys Custom Assessment and Remediation (CAR) app working in conjunction with VMDR, customers can create a script with one of many supported scripting languages and execute it on a target asset; this determines if the asset is vulnerable to a customer-defined vulnerability.
Custom scripts are treated by the Qualys Cloud Platform as a custom QID – the Qualys ID number assigned to each vulnerability. All custom QIDs are fully integrated into VMDR’s knowledge base and workflows. As a result, every custom QID’s vulnerability information and detection status are shown in VMDR’s dashboard, reports, and workflows; these appear side by side with out-of-the-box detections of other vulnerabilities.
Audit Log Management
Organizations need to collect, alert, review, and retain audit logs of events that could help detect, understand, or recover from an attack. Qualys File Integrity Monitoring (FIM) is a lightweight and highly scalable cloud service that provides continuous system monitoring of critical files, folders, and registry objects for changes at scale – unlike any other FIM technology available today. It offers the most efficient alert noise control available in the FIM space. With its unique noise-canceling capabilities, teams can focus only on events that really matter, saving time and reducing complexity. Qualys FIM helps customers adhere to compliance regulations such as PCI-DSS, GDPR, FedRAMP, HIPAA and others.
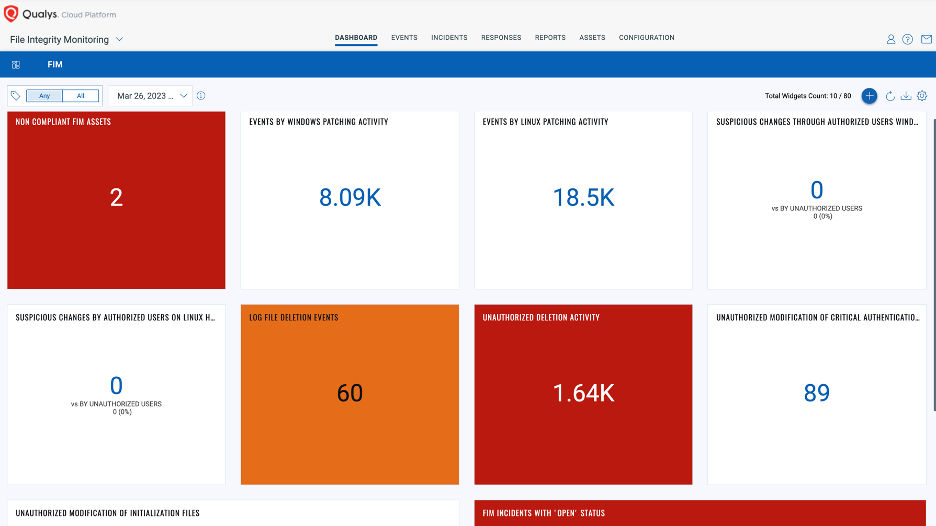
Security Awareness and Skills Training
Qualys Security Assessment Questionnaire (SAQ) helps you design and build questionnaires and automate campaign creation and tracking to quickly identify any security and compliance gaps. It also helps assess business readiness for compliance. Qualys SAQ makes it easier to automate the complex security requirements of the CIS top 18 controls that involve inputs from internal and external parties. With the shared assessment template, you can track the knowledge of internal and external parties on security training and awareness programs.
Conclusion/Summary
Implementing the CIS top 18 controls framework can significantly improve an organization’s security posture, ensure audit readiness, and mitigate risks for security breaches and compliance failures. However, it is not a “set and forget” one-time task. Implementing the controls is a continuous process designed to achieve more robust security and compliance to prevent cyberattacks and regulatory issues. It requires continuous monitoring and evaluation to maintain an effective cyber defense. Qualys solutions such as Policy Compliance, Vulnerability Management Detection and Response (VMDR), Web App Scanning (WAS), CyberSecurity Asset Management, Patch Management, SaaS Detection & Response, and Endpoint Detection & Response (EDR) can help your organization implement CIS controls and strengthen your overall security posture, powered by the revolutionary Qualys Cloud Platform.
Researchers at Qualys are working on a whitepaper that will have in-depth details of how each CIS control and safeguard are mapped to Qualys apps and help you further improve your cybersecurity posture. Watch this space for more updates! For more information or to start a 30-day trial, please contact your TAM or Technical Support.
Contributors
- Jayesh Rajan, Manager, Compliance Analysis, Qualys
- Bill Reed, Product Marketing Manager, Qualys
- Shekhar Rana, Solutions Architect, Qualys