Qualys FIM Playbook for PCI 4.0
This File Integrity Monitoring (FIM) playbook is your comprehensive guide to establishing and maintaining an effective FIM program aligned with the latest PCI DSS 4.0 standards. By meticulously monitoring and ensuring the integrity of vital files and configurations, your organization can bolster its defenses against unauthorized changes, potential breaches, and data compromises.
Throughout this playbook, you will find strategic insights, best practices, and actionable steps to meet regulatory obligations and fortify your organization’s security posture.
Let’s embark on this journey to elevate your FIM practices and enhance the protection of valuable payment card information.
Setting Up PCI Scope for FIM
The first step in implementing a FIM solution is to identify and define the assets that require activation for FIM monitoring. This process involves recognizing the systems, applications, and data within your organization that are pertinent to FIM. Doing so simplifies the monitoring process and enhances your security posture.
To streamline FIM monitoring, consider assigning specific tags to your identified assets. These tags can be directly used within the FIM solution to initiate monitoring for multiple assets simultaneously. We recommend using a suggestive naming convention for your FIM assets, such as ‘Production PCI Assets_FIM. ‘ This naming convention helps quickly identify and manage assets designated for FIM monitoring.
Setting Up FIM Profiles
Qualys FIM provides the following out-of-the-box FIM profiles for PCI DSS 4.0
- Windows Monitoring Profile for PCI DSS
- Linux Monitoring Profile for PCI DSS
These profiles can be imported from Qualys Library to kick-start your monitoring efforts and comply with PCI DSS.
After import, you can customize these profiles to add more file paths for real-time monitoring.
The assets must be assigned once the FIM profile is set with all critical file paths under the monitoring radar. Assign the asset tag you created to cover your PCI Scope for FIM.
Activate the FIM profile to kickstart your FIM efforts.
Setting Up Correlation Rules for Automated FIM Incidents
FIM events will initiate once any file path within the monitored scope undergoes modification. It is essential to examine these events as they offer insights into the individuals responsible for the change. However, achieving this in practice presents considerable challenges. Analyzing every event might be insurmountable due to the potentially high event volume.
To address this, it becomes imperative to establish correlations among events based on predefined criteria. Doing so enables you to effectively identify and prioritize incidents from a subset of events needing attention.
You can use Qualys Query Language (QQL) to correlate events based on specific criteria for event generation in FIM. Some of the example QQLs you can directly use for Incident creation are as follows:
Spot malicious or suspicious files dropped on the host
reputationStatus:MALICIOUS or reputationStatus:SUSPICIOUS
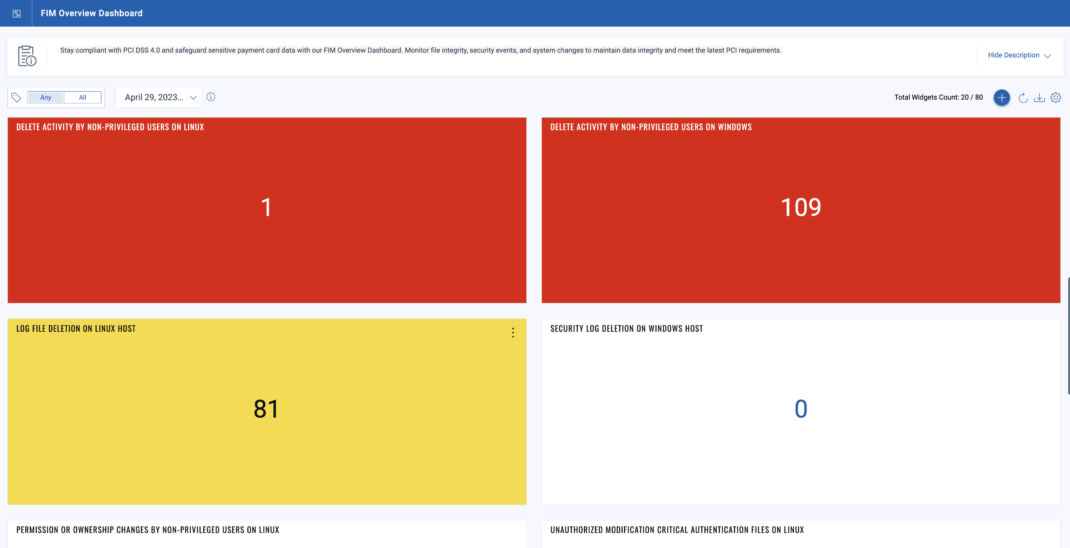
Delete activity by non-privileged users on Windows host
platform:Windows and action:Delete and not (actor.userName:’NT AUTHORITY’ or actor.userName:’Administrator’)
Delete activity by non-privileged users on Linux host
platform:Linux and action:Delete and not (actor.userName:`root`)
Permission or Ownership changes by non-privileged users on Linux
platform:Linux and action:Security and (actor.process:`chmod` or actor.process:`chown`) and not (actor.userName:`root`)
Events indicating unauthorized modification critical authentication files on Linux host
(platform:’Linux’ and (file.name:`passwd` or file.name:`shadow` or file.name:`password-auth` or file.name:`system-auth` and (action:Delete or action:Security or action:Content)) and not actor.userName:`root`)
Events indicating unauthorized modification of initialization files
(platform:’Windows’ and (file.name:win.ini or file.name:system.ini or file.name:boot.ini or file.name:ntuser.dat or file.name:desktop.ini or file.name:hosts or file.name:autoexec.bat or file.name:config.sys or file.name:protocol.ini or file.name: services) and not actor.userName:’NT AUTHORITY\SYSTEM’) or (platform:’Linux’ and (file.name:`lilo.conf` or file.name:`grub` or file.name:`grub.conf` or file.name:`grub.cfg`) and not actor.userName:`root`)
Log file deletion on Linux host
platform:Linux and file.fullPath:’/var/log’ and action: Delete
Security Log deletion on Windows host
platform: Windows and file.fullPath:’C:\Windows\System32\winevt\Logs’ and action: Delete
Setting Up Alert Rules for Automated FIM Alerts
Qualys FIM solution can be configured to send you emails or alerts in various events to ensure the security and integrity of your systems and data. Alerting should be used only for rare but critical events related to unauthorized access and ransomware attacks.
Here are some everyday events or scenarios where you may want your FIM solution to send you emails:
Authentication File Modifications
Unauthorized changes to authentication-related files, such as `/etc/passwd` on Linux or Active Directory database files on Windows, should trigger immediate alerts. Any modification to these files can have a significant impact on system security.
Multiple Deletions in a Short Duration
A sudden and unusually high number of file or directory deletions within a short time frame can strongly indicate a ransomware attack or a rogue process. FIM should generate alerts when this pattern is detected.
Rapid Renaming of Files or Directories
Rapid renaming or renaming of multiple files and directories in a short period can indicate a ransomware attack attempting to obfuscate its actions. Such events should be closely monitored.
Executable File Modifications
Changes to executable files (e.g., .exe, .dll) in critical system directories should be closely monitored. Unauthorized modifications can lead to malware infections or system compromises
Registry Key Changes
Changes to critical registry keys on Windows systems, particularly those related to security and system configuration, should be closely monitored.
Setting Up Report Rules for Automated FIM Reports
Qualys FIM solution includes automated Compliance reports that are pivotal in supporting compliance audits, making them a cornerstone of the FIM system. These reports can be categorized into three key types:
Event-Based Reports
These reports detail specific security events and activities tracked by the FIM system.
Incident-Based Reports
This category documents security incidents and breaches within the monitored environment.
Asset-Based Reports
Asset-based reports offer a comprehensive snapshot of individual assets within the FIM scope. They assess the security posture and compliance of these assets with relevant standards. Using asset-based reports, you can readily identify non-compliant assets vital for maintaining compliance readiness, especially within your PCI scope.
Non-compliant assets encompass two critical categories:
- Assets on Which FIM Was Activated but Not Currently Running – This condition contradicts PCI DSS Requirement 11.5 (v3.2.1) and 11.5.2 (v4.0), emphasizing the necessity of continuous FIM monitoring to maintain compliance and security standards.
- Non-Communicating Assets: These are not communicating with the Qualys platform. Identifying and addressing non-communicating assets is crucial to ensure that all relevant systems are actively monitored and assessed.
Setting Up a Dynamic FIM Dashboard
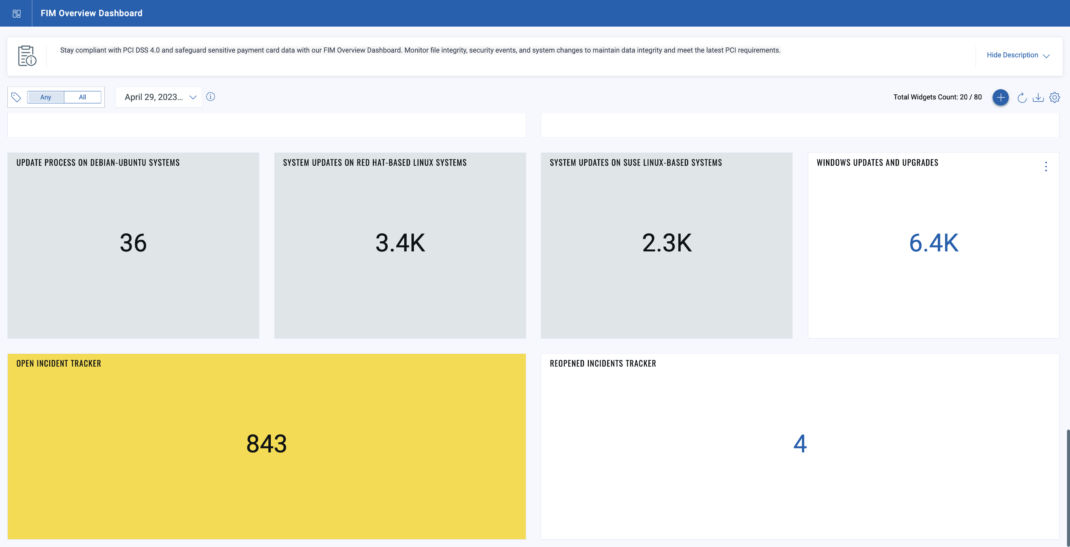
Qualys File Integrity Monitoring (FIM) solution features a dynamic default dashboard that offers a comprehensive summary of environmental change events, focusing on prominently highlighting critical issues that demand immediate attention. It also includes predefined widgets that quickly overview your overall FIM environment. A few dashboard widgets are shown as follows: