Identify and De-risk Unmanaged, Unauthorized Devices With Qualys CyberSecurity Asset Management (CSAM)

Table of Contents
69% of organizations said they experienced at least one cyberattack resulting from an exploit of an unknown or unmanaged asset such as software, cloud-based workloads user accounts, and IoT devices. Ultimately, these attacks stem from visibility gaps in the attack surface. Bringing these assets under management requires flexible discovery methods, including active and passive scans, security agents, API-based discovery, and now—Qualys CyberSecurity Asset Management’s innovative new internal attack surface capability.
CSAM is strengthening internal attack surface coverage by leveraging the already-deployed Qualys Agent to continuously monitor your network to identify unmanaged and unauthorized devices in real time. This passive discovery method is built into the powerful Cloud Agent and, combined with remote scans, external attack surface discovery, and third-party connectors, allows customers to build a comprehensive asset inventory, calculate the TruRisk of every asset, and eliminate risk based on business impact.
Why is This Important?
Some CAASM (Cyber Asset Attack Surface Management) solutions rely solely on API-based integrations to inventory the attack surface. This method is incomplete, relying on data from various point solutions. It also leaves an organization exposed to a specific blind spot: devices and rogue assets connecting to the internal network in real time.
Qualys combines our active scanning and passive discovery with integrations so you see all assets across internal networks and the internet-facing attack surface. The latest release focuses specifically on unmanaged and unauthorized assets connecting to internal networks.
It’s not only about extended visibility of the attack surface, but it also expands actionable risk assessment, including the ability to:
- Manage and control network access with real-time context (the foundation of Zero Trust Security Architecture) by proactively identifying devices connected to the network that are not authenticated, missing security agents, etc.
- Scan rogue devices for vulnerabilities and compliance issues, automatically add them to your CMDB, and prioritize remediation according to TruRisk—all within a single platform.
- Report on rogue, untrusted, unmanaged, or otherwise risky devices along with remediation steps to reduce risk—satisfying compliance frameworks, federal reporting requirements, and on-demand audits.
Since this passive sensing capability is now built in to the Qualys Cloud Agent, there is no need for a deep dive understanding of your network topology for strategic deployment of passive sensors, and no need to incur additional installation costs.
In this post, we’ll explore each of these use cases with examples of how Cloud Agent Passive Sensing helps Qualys customers de-risk their internal attack surface in real time.
To learn more about how Cloud Agent Passive Sensing works, read our previous blog post.
Discover up to 34% more devices on your internal network for VM and compliance scanning
Qualys already has one approach to monitoring the internal network for device activity with the Network Passive Sensor (NPS). Now, passive discovery with Qualys Agent introduces a novel approach to passive discovery that is more efficient, easier to implement, does not require information on network design, and delivers results faster than other solutions on the market. And it doesn’t require any expensive hardware and laborious effort for the deployment of an appliance.
Simply activate your already-deployed Cloud Agent for Passive Sensing.
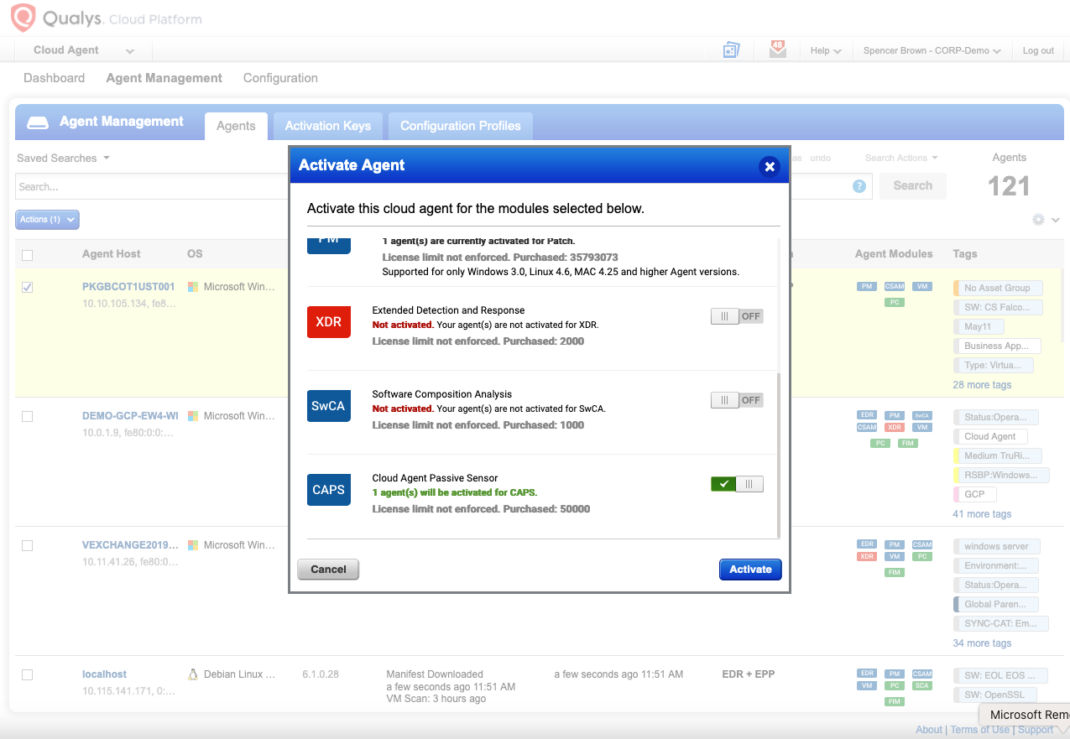
This provides instant visibility of every device communicating in the network, allowing you to assess risk quickly, block access from untrusted devices, and detect compliance issues. By sniffing network traffic, the Cloud Agent will identify new assets such as managed corporate-owned devices, employees’ devices connecting to the network, and IoT devices like Wi-Fi-enabled TVs or IP cameras. Without awareness of a device’s existence, security teams cannot effectively safeguard it.

The Cloud Agent passive sensing capability has already helped Qualys customers discover up to 34% more assets connecting to their networks in real time. That means these assets can be added to their VM programs for TruRisk assessment, scanned for misconfigurations and compliance issues, and blocked from the network if high-priority business risk is detected.
Lay the foundation for Zero Trust Security Architecture
The Zero Trust Security Architecture model defines that no assets (inside or outside the perimeter) should be automatically trusted. In order to enforce this model, organizations need a real-time, comprehensive inventory of IT assets.
Not only is Zero Trust now mandated for US federal agencies, but organizations in all industry segments are moving toward this model to combat the risks associated with remote work and relaxed BYOD policies.
Whether by mandate or by choice, it behooves security teams to identify untrusted devices that connect to the network. By using the already-deployed Qualys Cloud Agent as a passive sensor, organizations can monitor their networks to identify devices, but more importantly, discover user and business data to help enforce Zero Trust policies. Below, we see unmanaged devices discovered with passive sensing.
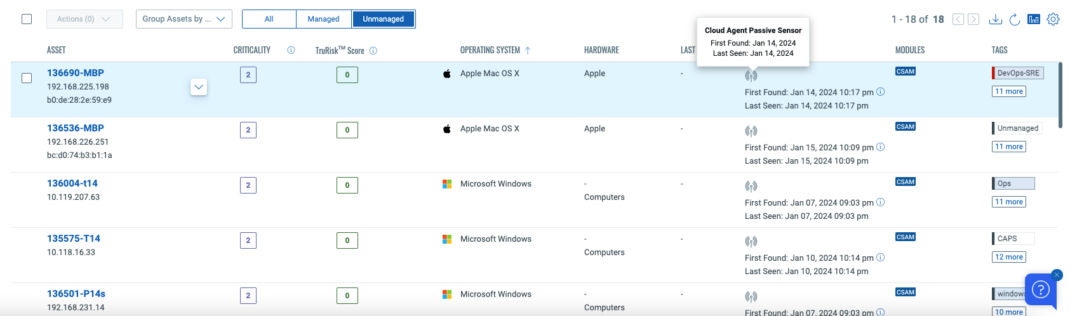
This new capability will identify assets (including IoT/OT devices) connecting to the network, identify high-risk or EoL/EoS software and operating systems (such as Windows XP), and assess TruRisk to help IT/Security teams block access or take remediation actions. Combine that with third-party connectors to device/user management tools (such as Active Directory), and the organization is well-armed to manage which devices and users are authorized to access data within the network.
Provide comprehensive IT visibility of network-connected assets with CMDB sync
According to Enterprise Strategy Group, 79% of organizations have an asset visibility gap, and an incomplete CMDB is a common result. IT environments continue to grow more complex, and enterprise companies have relaxed policies for remote work and BYOD—introducing rogue devices and shadow IT. The result is an increasing number of unmanaged and unauthorized devices attempting to connect with the network—devices that are usually missing from the CMDB.
As CSAM discovers these devices in real time with Cloud Agent passive sensing, they can be synced automatically with CMDBs such as ServiceNow and BMC Helix.
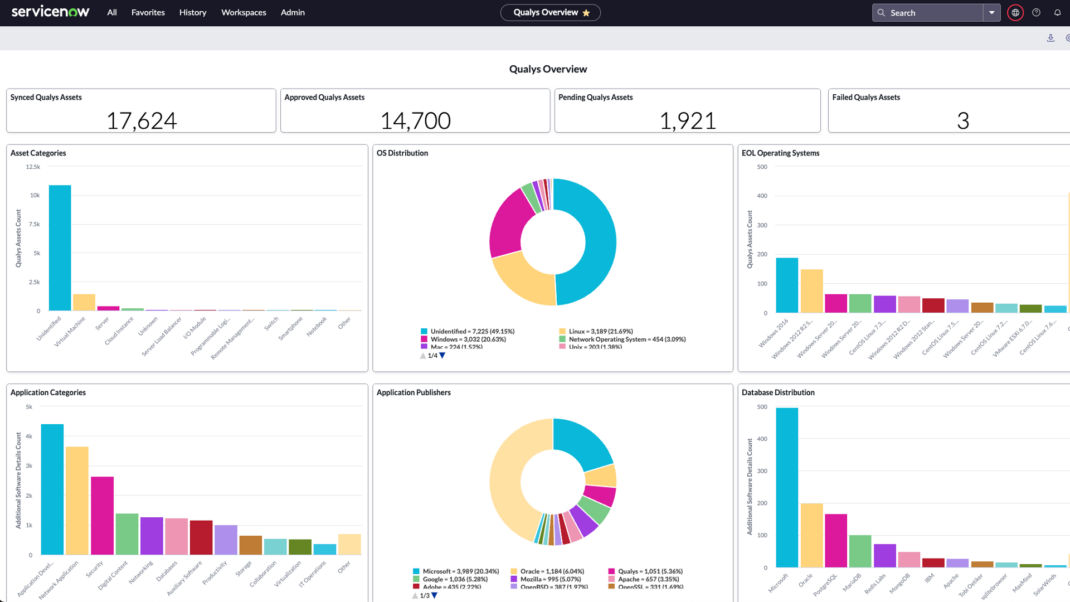
While security teams are responsible for cyber risk, IT teams are often tasked with taking remediation actions. So, when devices connect to the network with EoL/EoS software or other risk factors, Qualys can sync that data with CMDB records, allowing security and IT to collaborate and de-risk these assets quickly.
Solidifying your coverage of the internal attack surface
The release of Cloud Agent passive sensing for CSAM extends coverage of the attack surface for all Qualys customers. Other attack surface management tools fall short—either relying exclusively on API connectors or failing to integrate natively with VM, patching, EDR, and compliance tools required to reduce risk. Qualys customers can get 100% coverage of the attack surface with the same agent they’ve already deployed and the same platform they already use to measure, communicate, and eliminate cyber risk in their business.
Try CSAM for 30 days
Read the press release to learn more about Cloud Agent passive sensing, and go to our webpage to find out more about CMDB sync.