Nist CSF 2.0: Everything you need to know about
An Overview of NIST CSF 2.0 and Its Expanded Cybersecurity Framework
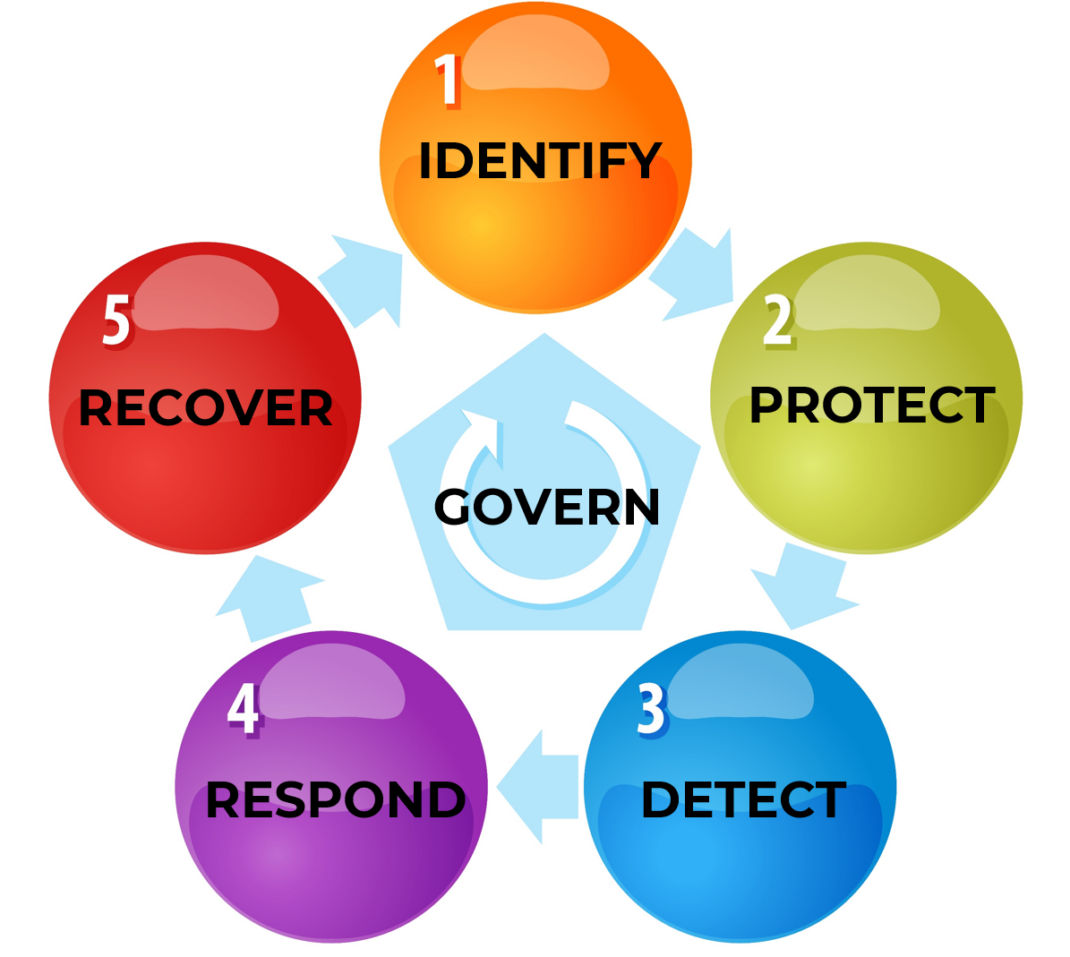
The National Institute of Standards and Technology (NIST) recently updated its popular Cybersecurity Framework (CSF) to version 2.0 to help organizations reduce cybersecurity risks. Designed for virtually all industry sectors, from small to medium businesses (SMBs) to larger enterprises, NIST CSF v2.0 represents the first major update in more than a decade. NIST released CSF v 1.0 in 2014 at the direction of a presidential executive order, with an emphasis on critical infrastructure, to help all firms reduce risks of security breaches. CSF 2.0 expands upon the existing five basic functions of Identify, Protect, Detect, Respond, and Recover and now includes a sixth function called Govern. NIST CSF 2.0 also more fully addresses supply chain risks.
“The CSF has been a vital tool for many organizations, helping them anticipate and deal with cybersecurity threats,” said Under Secretary of Commerce for Standards and Technology and NIST Director Laurie E. Locascio. “CSF 2.0, which builds on previous versions, is not just about one document. It is about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve.”
The CSF 2.0’s expanded scope goes well beyond protecting critical infrastructure, such as hospitals and power plants, and encompasses almost any organization at risk for cyberattacks. The new Govern function focuses on making and carrying out informed decisions on cybersecurity strategy. This component now emphasizes cybersecurity as a major risk factor that executives should prioritize, as it can impact finances, litigation, and brand damage.
“Developed by working closely with stakeholders and reflecting the most recent cybersecurity challenges and management practices,” said Kevin Stine, chief of NIST’s Applied Cybersecurity Division, “this update aims to make the framework even more relevant to a wider swath of users in the United States and abroad.”
A larger percentage of businesses, both in the U.S. and other countries, underscore their Written Information Security Plan (WISP) with the NIST CSF. NIST now prescribes four levels of maturity, or tiers, that characterize the rigor of the firm’s cybersecurity risk governance and management practices. They essentially provide context for how an organization views cybersecurity risks and its processes for managing those risks. The four tiers are Partial, Risk Informed, Repeatable, and Adaptive. NIST recommends that all firms should strive for the Adaptive top tier. To achieve this requires the implementation of best practices alongside the most effective cybersecurity solutions.
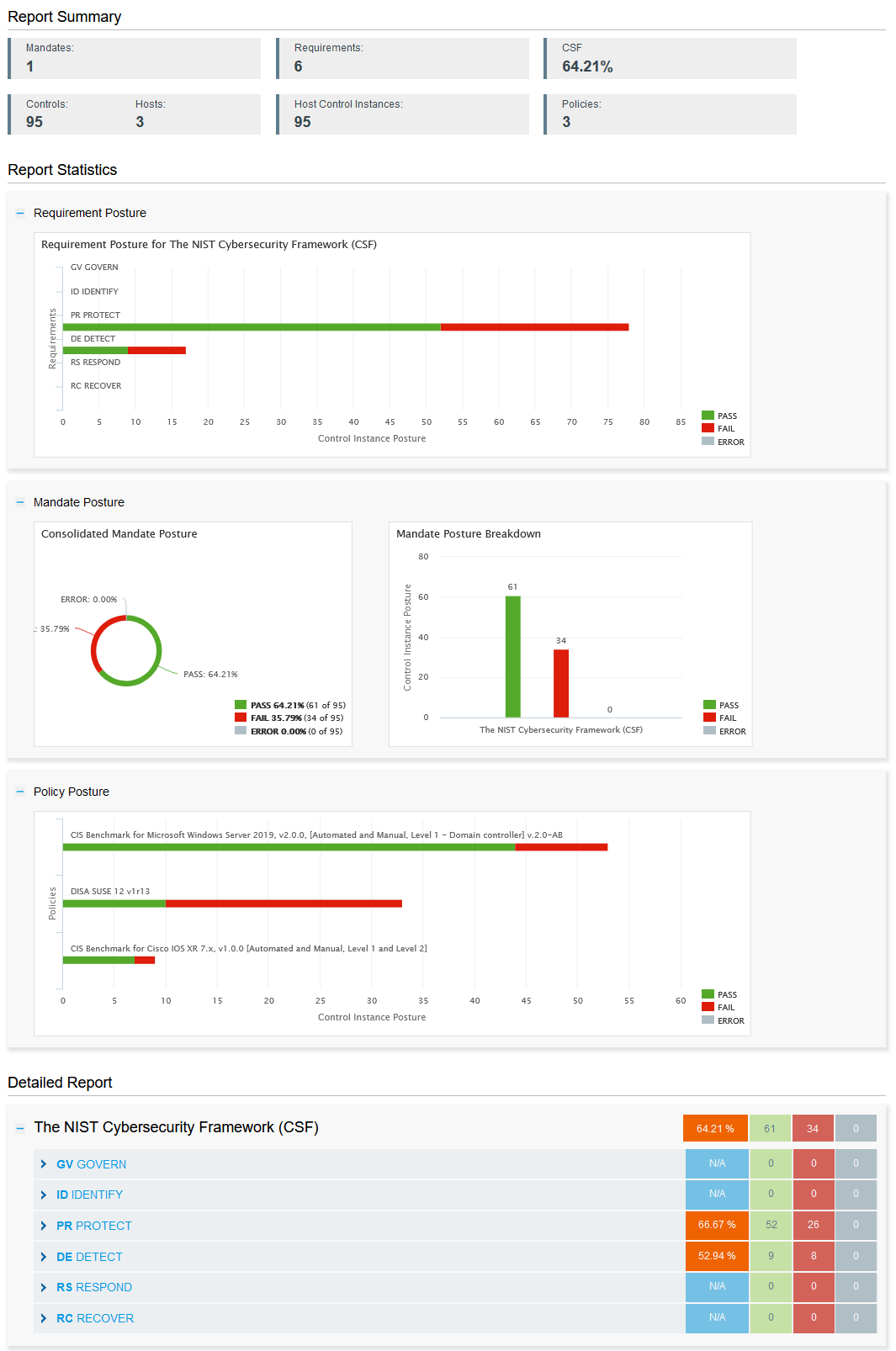
How Qualys Helps Organizations Meet NIST 2.0 Compliance
The Qualys Enterprise TruRisk Platform is built with the world’s most comprehensive vulnerability management (VM) capabilities, including its own asset inventory, threat database, and attack surface management. The apps required for NIST CSF 2.0 compliance are delivered via one platform, managed with one dashboard, and deployed with a single agent.
The following table shows how Qualy’s capabilities can help your organization address all NIST CSF 2.0 requirements.

GOVERN (GV) – Establishing Cybersecurity Strategy and Oversight
The GOVERN function is where your organization’s cybersecurity risk management strategy, expectations, and policies are established, communicated, and monitored. This function provides outcomes to inform what an organization may do to achieve and prioritize the outcomes of the other five functions in the context of its mission and stakeholder expectations. GOVERN addresses an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policy; and the oversight of cybersecurity strategy.
Qualys Policy Compliance (PC) offers a comprehensive NIST CSF 2.0 dashboard with details that outline your posture across all six functions, including mandates, requirements, pass/fail status, and more. Executives can view their overall posture to ensure they are meeting the GOVERN requirements adequately and make adjustments to ensure proper risk management strategy. With Qualys PC, you can go beyond vulnerability management (VM) and security configuration assessment (SCA) to reduce security breach and compliance risks with a single cloud solution, multiple sensors, robust policy library, and seamless integration.
The Qualys PC app includes support for 900 policies, 20,000 controls, 350 technologies, and 100 regulations. This app can also dramatically improve an organization’s security posture by increasing MITRE ATT&CK coverage and overall security postures by up to 79 percent over vulnerability management alone. Gartner says that 99 percent of cloud security breaches are related to mistakes and misconfigurations. Qualys PC allows you to find, prioritize, and automatically remediate misconfigurations that most other solutions miss. The app now integrates with Qualys Endpoint Detection and Response (EDR) to automatically remediate threats discovered by the EDR app. Qualys PC can ensure compliance with numerous mandates such as PCI DSS 4.0, GDPR, PSD2, CCPA, HIPAA 2023, FINRA, ISO, and many others.

IDENTIFY (ID) – Identifying and Assessing Cybersecurity Risks
This function addresses how your current cybersecurity risks are understood. Gaining an understanding of your assets (e.g., data, hardware, software, systems, facilities, services, people), suppliers, and related cybersecurity risks can help you prioritize efforts consistent with your risk management strategy and the mission needs identified under GOVERN.
As this function includes asset management, risk assessments, and improvements to ensure compliance, the Qualys CyberSecurity Asset Management (CSAM) app addresses requirements for asset management, and the Qualys Vulnerability Management Detection and Response (VMDR) app tackles requirements for risk assessment.
Qualys CSAM allows you to create a unified asset inventory with cyber risk and business context to turbocharge vulnerability management and remediation. With CSAM, you can improve asset coverage by 30 percent to turbocharge vulnerability management, proactively manage End of Life or Service by up to twelve months in advance to avoid unpatchable vulnerabilities, and map remediation tickets with 96 percent accuracy with bi-directional CMDB sync to unify IT and security teams.
Qualys VMDR continuously measures known and unknown risks, prioritizes and communicates risks across vulnerabilities, and allows you to patch any device anywhere to remediate, mitigate, and block the attack paths to eliminate risks. With VMDR, you can measure risks six times faster than with competitive VM platforms, communicate risks from over 200,000 vulnerabilities sourced from more than twenty-five threat intelligence feeds, and eliminate critical risks 60 percent faster with a one-click workflow and ITSM integrations.
Peter Drucker once said, “You can’t improve what you don’t measure.” Using CSAM and VMDR to ensure visibility and measure risks can help you cover the improvement requirements for this function.
Qualys TotalCloud offers a unified dashboard for managing cybersecurity across hybrid IT environments. This centralized visibility and control aligns with NIST Identify requirements for effective cybersecurity governance and risk management.
PROTECT (PR) – Ability to secure the assest
This function addresses safeguards used to manage the organization’s cybersecurity risks and how they are used. Once assets and risks are identified and prioritized, PROTECT supports the ability to secure those assets to prevent or lower the likelihood and impact of adverse cybersecurity events, as well as to increase the likelihood and impact of taking advantage of opportunities.
Outcomes covered by this function include identity management, authentication, and access control; awareness and training; data security; platform security, and the resilience of technology infrastructure.
Qualys CSAM and PC can ensure you’re covered for platform security by providing visibility, reporting, dashboards, and remediation so you can attain a top-tier Adaptive NIST CSF 2.0 status.
Qualys TotalCloud can protect cloud infrastructure & SaaS apps up to 85 percent faster with a unified, prioritized view of risks.
DETECT (DE) – Real-Time Threat Detection and Analysis
This function is designed to ensure you can find and analyze possible cybersecurity attacks and compromises. It enables the timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse events that may indicate that cybersecurity attacks and incidents are occurring. This function supports successful incident response and recovery activities.
Qualys Endpoint Security solutions can help you stay covered for this function. Qualys Endpoint Security employs a multi-layered defense to protect your organization’s devices—such as laptops, desktops, and servers—from sophisticated cyber threats, including ransomware, phishing, data theft, and more. As noted earlier, Qualys EDR integrates seamlessly with Qualys PC to automatically remediate threats and misconfigurations, which helps you comply with the RESPOND function.
For continuous monitoring, Qualys File Integrity Monitoring (FIM) can be a critical app. Qualys FIM is a scalable cloud app that enables monitoring for critical files, directories, and registry paths for changes in real time and helps adhere to compliance mandates such as PCI-DSS 4.0, CCPA, GDPR, and others. Unique noise cancellation reduces false alerts by 90%+ to help mitigate audit failures for ignoring low-level alerts. Qualys FIM includes support for non-agent network devices to alert on network configuration deviations, offering enhanced visibility for effective monitoring and response. Also, File Access Monitoring (FAM) triggers alerts when critical host files, not intended for regular use, are accessed.
Qualys TotalCloud measures risk with 360-degree scanning to detect vulnerabilities, and detects malware with up to 99 percent accuracy thanks to AI-powered deep learning threat detection.
RESPOND (RS) – Developing an Effective Response Strategy
This function is about actions taken regarding a detected cybersecurity incident. It covers support for the ability to contain the effects of cybersecurity incidents. Outcomes within this function include incident management, analysis, mitigation, reporting, and communication.
Qualys Endpoint Protection solutions, as noted earlier, can help your analysts stay on top of incident analysis while mitigating false positive alerts that require additional IT support tickets and analyst triage. This can greatly reduce costs and efforts related to supporting this function.
As we discussed previously, Qualys PC helps ensure timely and automated incident management and mitigation, reducing costs and efforts that can overrun resource-constrained teams.
RECOVER (RC) – Ensuring Effective Recovery
This function focuses on assets and operations affected by a cybersecurity incident and how they are restored. It’s all about supporting the timely restoration of normal operations to reduce the effects of cybersecurity incidents and enable appropriate communication during recovery efforts.
Recovery is all about resilience and not just executing your plan but doing so in a timely and efficient manner. Using Qualys Endpoint Protection and PC solutions to RESPOND can go a long way toward ensuring fast and effective recovery by automating manual processes that can result in mistakes and delays.
The Qualys Security Assessment Questionnaire (SAQ) app is a transformative cloud service used to conduct business process control assessments among your external and internal parties. SAQ addresses self-assessments required across all six functions.

Conclusion
NIST CSF 2.0 has taken a decade to get here, but rather than view this as an additional burden and constraint on your organization, covering the requirements in the right way with the right solutions can help bolster your firm’s overall security posture and reduce risks for cybersecurity breaches, brand damage, and litigation.
The Qualys Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys and non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.
The TruRisk Platform integrates and shares data with systems that your organization already uses — such as SIEM, GRC, ITSM, IAM, WAF, and risk management. Accurate vulnerability assessment and network scan data from Qualys can dramatically improve the usefulness and accuracy of many complementary security products such as network management tools, intrusion detection/prevention systems, or firewalls.
The Enterprise TruRisk platform supports dozens of apps, including CSAM, VMDR, PC, Endpoint Security, and many others, that can help you address requirements across all six CSF 2.0 functions. With Qualys, attaining top-tier Adaptive status is not only achievable, but can help you reduce overall costs and efforts along the way. Contact Qualys today to learn more.